We may earn a commission if you make a purchase through the links on our website.
The Definitive Guide to Audit Logs

UPDATED: February 6, 2024
Take steps to understand and utilize your log data with this handy guide.
As you run and interact with systems on your network, they store a history of their actions called a log. Most software and hardware products generate this log in a way that can be viewed and extracted to be properly read by an end-user. These logs provide an enhanced insight under the hood of your systems, meaning you can identify exact behavior and time signatures for everything your systems do.
What’s more, because the log data lists specific actions that your systems are doing, they can be extracted and fed into other systems through APIs to create integrations between systems where they would otherwise not exist. For example, hardware might log temperature information—this data might then be fed into a cooling system that automatically switches on when the log data shows an increase in temperature.
With deep research and analysis, below are the three top-most audit logs tools that we found useful and worth trying:
SolarWinds Loggly – FREE TRIAL This tool is easy to use and provides a faster troubleshooting solution by tracing the issues from roots. It is an undeniable tool for every organization to monitor application and infrastructure issues for maintaining secure networks.
ManageEngine EventLog Analyzer – FREE TRIAL It has a report builder that allows you to customize the log analysis reports according to the business needs, or you can also use its pre-built reports as needed.
Datadog Log Management You can search by filter and analyze logs to understand the complex query and log patterns. You can simply drag and drop the visualizations.
However, this aspect of log data usage doesn’t necessarily fall under audit logging, so won’t be explored in much depth within this article. Instead, we’ll be focussing on using log data as recorded information that helps you to find out what is happening on your systems, and what users are involved.
Why Utilize Audit Logs?
There are several benefits that audit logs can provide, and we can break down these benefits into three broad categories: Proof, Insight, and Security.
Audit Logs as Proof
Because logs are drawn directly from systems, they can be depended on as valid proof. Log data presents trustable data that can be pulled from your systems quickly and easily; making it perfect for converting into graphs, reports, and presentations.
You can use audit log data for compliance reports, and many regulators specifically request audit logs to aid in their own evidence gathering. The data can also be abstracted and then shown to investors, and customers, or displayed as part of marketing.
Audit Logs as Insight
Audit logs provide a level of detail about your systems that is otherwise unavailable through regular interfaces. This means that logs can be used to collect and collate stats that are useful for other functions.
One of the most popular uses for audit log data is for performance monitoring. Since the information can be broken down into more minute data and is collected at regular intervals, you can effectively produce performance graphs that can track the trends of your data. This method can also be used to spot anomalous data—which ties into Security below—but can be extremely useful in detecting issues.
Audit Logs as Security
Because data pulled from logs includes user interactions, with the associated user information, audit logs are especially useful for detecting security issues. As mentioned above, this might tie into finding anomalous data that is connected to a potential security breach. If the anomaly is the result of user interaction, audit logs will identify which user account created the anomaly.
This also ties into using audit logs as proof. In these circumstances, the audit log effectively acts as evidence that can be used against malicious user activity. This reason is why so many compliancy mandates request log data—because it is extremely useful evidence in finding user-related infractions.
Managing Audit Logs
Audit logs present data extracted from systems in a “human-readable” form—but while the information is technically human-readable, it can often look like complete nonsense unless you know what to look for. Most log data, especially when it relates to system faults, include strings of error codes that can be relayed to technical support desks (or more likely just googled).
When reading through the data, you’ll want to scan for identifiable information. These might be usernames or UUID if it relates to security or specific user faults. Related object identifiers, serverIDs, etc. might help with other faults. Sometimes, logs include their own descriptions which can help you to better understand exactly what a log message means.
Another important thing to note is log security. Log files contain especially useful information to malicious parties and are often the target of hacking attempts. Good software systems will encrypt things like passwords and critical user data within log files, but the information that can be gathered can still likely be used against you. Therefore, security access to your log files through things like user permissions is vitally important.
Audit Log Tools
Two distinct problems come with log data: the first is the sheer amount that each system on your network generates; the other is the fact that log data is very rarely delivered in a human-readable fashion—fortunately, there are solutions to both of these problems: log parsing software.
There is a vast amount of log auditing and management solutions available on the market. Simple log auditing tools provide you with a means of collecting and displaying log data in a more readable format. More complex solutions can allow you to automate responses to flagged log data entries, which can massively speed up your remediation speed.
Our methodology for selecting an audit log tool
Choosing the best audit log tools for your organization involves careful consideration of several factors to ensure they meet your specific requirements. Here are pro tips to help you make an informed decision:
- Clearly outline your organization's audit log requirements
- Consider tool compatibility with your current system and infrastructure
- Scalability- should handle an increasing volume of logs
- capabilities for storing and retaining logs
- real-time alerts and notifications
- Automation and Customization:
- Check for reviews, testimonials, and the level of customer support offered
- Consider Compliance Reporting
- Cost and other security features
Here, we’ve presented a look at three of the best audit logging tools that should help you to better understand and utilize your log data:
1. SolarWinds Loggly – FREE TRIAL
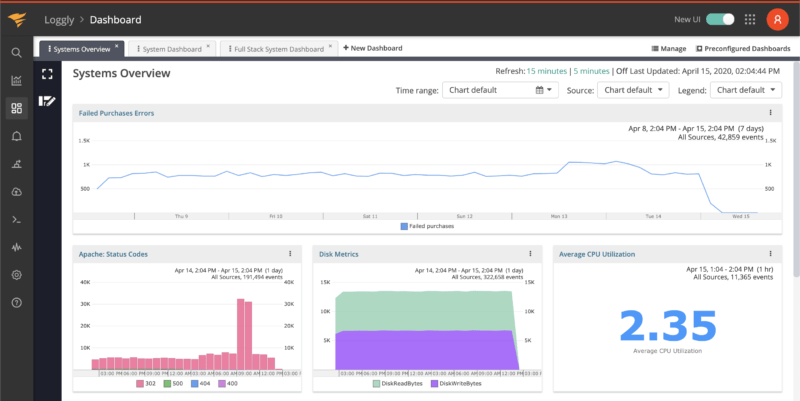
SolarWinds Loggly is a log parsing and analysis solution based on APM (Application Performance Management) that integrates with a variety of sources. Loggly is ideal for your performance analysis needs since it can gather data from a wide range of sources and scan log data to examine a wide range of performance parameters.
Key Features:
- APM integrated log analysis
- Customizable dashboard
- Scalable full-stack log management
- Automated log summaries
- Built-in email alerting
Why do we recommend it?
The SolarWinds Loggly tool has a user-friendly dashboard and allows users to create custom dashboards quickly for monitoring application health, behavior, and trends. In addition, you can also use prebuilt dashboards to track performance data(KPI) and other useful statistics, providing a comprehensive and intuitive approach to log analysis and application monitoring.
You can compare performance data rapidly using the offered charts and system overview while the data sources are live on your systems. As a result, this method is ideal for log analysis that focuses on performance. Nonetheless, it lacks the automation found in other solutions. However, it outperforms every other product in terms of specific performance analysis.
SolarWinds provide a 30-day free trial of the product available on the website. What’s more, SolarWinds has several log-based products that can be found. We’ve only mentioned one in this article, but there’s also SolarWinds Security Event Manager, and SolarWinds Papertrail — both take a different approach to log parsing and analysis.
Who is it recommended for?
SolarWinds Loggly is particularly recommended for log management experts, system administrators, and IT professionals who seek an advanced tool for organizing log data in real time. You can gain valuable insights without requiring intricate query setups. Loggly is especially beneficial for experts who need to identify unusual event counts or outliers promptly and delve into relevant data with ease.
Pros:
- It supports powerful and Interactive Search
- It is an affordable solution to meet multiple business needs
- Integrated workflow for faster results
- It supports continuous monitoring for instant solution
- Centralized logging and anomaly detection
Cons:
- Limited options for setting up alerts
EDITOR'S CHOICE
SolarWinds Loggly is our top choice due to its exceptional ability to aggregate logs from various integrations into a unified platform. With Loggly, you can effortlessly filter through the logs, ensuring swift identification of relevant information. Additionally, it also has robust notification features, promptly alerting you when specific logs of interest occur.
Download: Start 30-Day Free Trial
OS: Cloud-based
Download: https://www.loggly.com/
2. ManageEngine EventLog Analyzer – FREE TRIAL
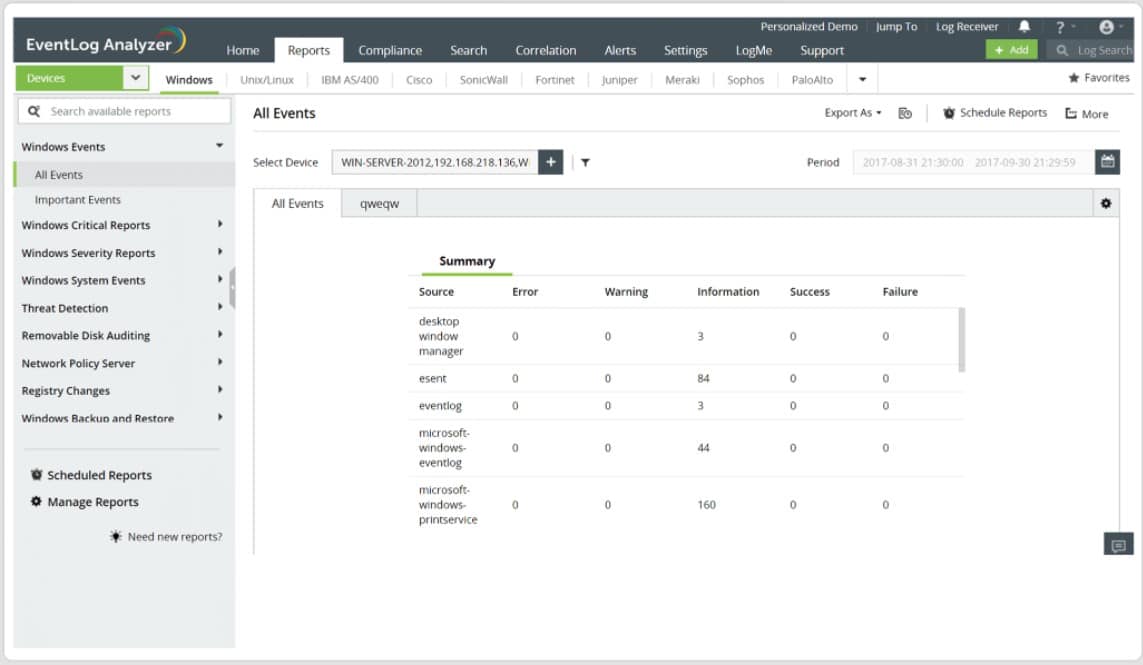
The ManageEngine EventLog Analyzer is an enterprise-level log parsing and analysis tool. The software solution focuses on merging logs from both hardware and application logs, such as switches and firewalls. This is particularly handy for network administrators who are responsible for a large number of network devices on the premises.
Key Features:
- In-depth auditing capabilities
- High-speed log processing
- Built-in incident management
- A wide variety of log sources included
- Custom data sources
Why do we recommend it?
The ManageEngine EventLog Analyzer tool is known for its widespread trust, as it is used by over reputed 10,000 organizations relying due to its robust network security. The tool offers instant alerts in case of critical changes to confidential files and folders, this helps to monitor and fix the issue to security incidents before damage happens.
The solution's scalable features and various buying choices make it ideal for a wide range of business sizes. The program has an inbuilt ticketing system that interfaces with a small number of helpdesk solutions, but it doesn't have much automation capability otherwise. The software's main focus is monitoring and analysis, with exceptional auditing and compliance reporting thrown in for good measure.
This solution is purely for the enterprise businesses who need the absolute best in audit logging capabilities across a massive array of both hardware and software. The API and customizability provide a lot of integration options that put this solution ahead of several others if coverage for a broad range of systems is a priority for your business. Access the 30-day free trial.
Who is it recommended for?
The ManageEngine EventLog Analyzer tool is the best choice for cybersecurity experts and IT professionals who want log management solutions. It allows identifying the root cause of security breaches. With advanced data visualization tools and intuitive dashboards, experts can conduct in-depth log analysis, gaining valuable insights from network logs for effective cybersecurity management.
Pros:
- This tool has a straightforward setup and is easy to use
- Perfect choice for centralizing Windows system
- It gives a detailed report
- It has a fantastic GUI and interface
Cons:
- Limited scalability for handling a huge number of log volumes
Download: https://www.manageengine.com/products/eventlog/log-management-tool.html
3. Datadog Log Management
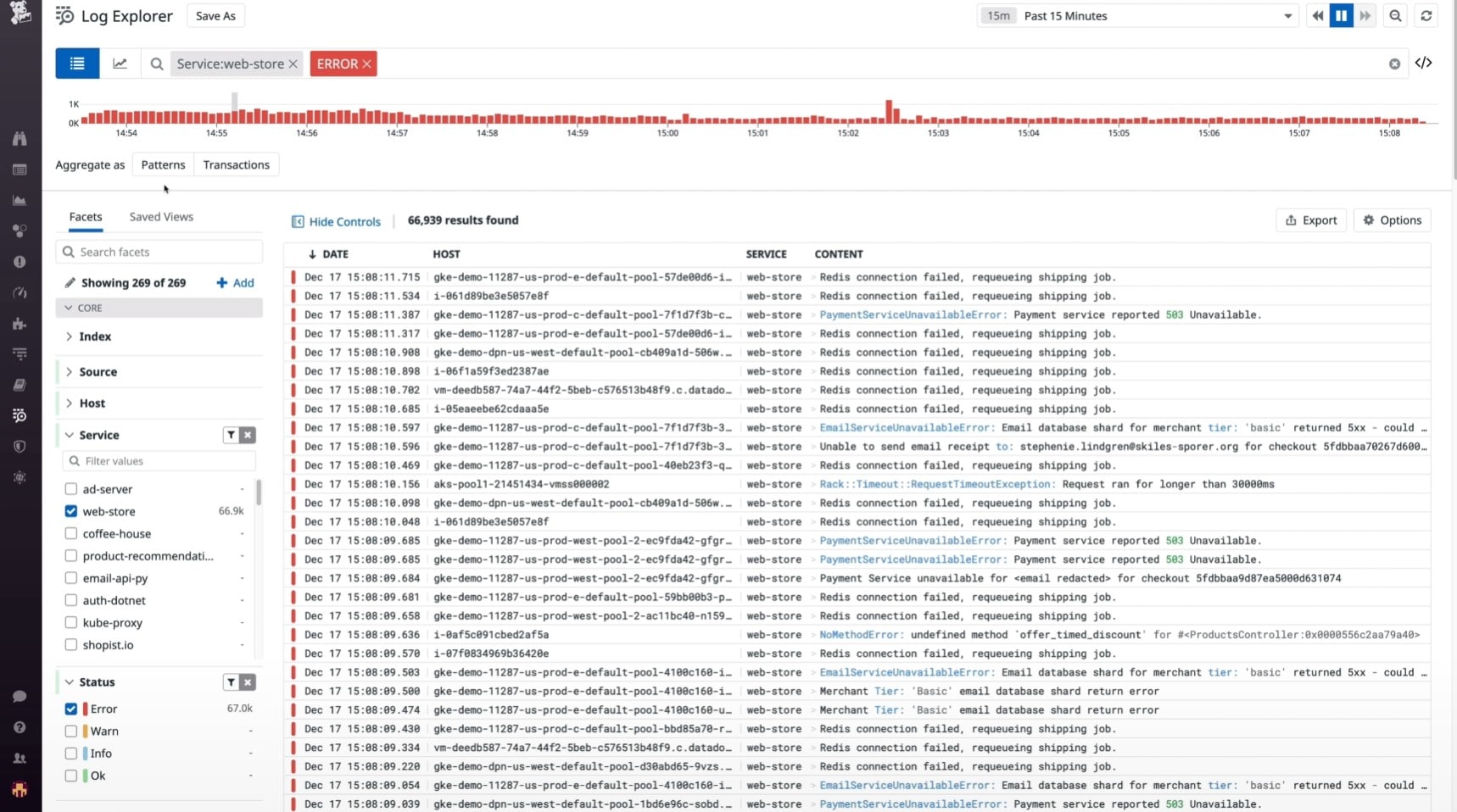
Datadog Log Management combines a huge proportion of log data into a single software solution. By displaying precise information about your logs from the primary control panel. The log patterns tool, for example, finds trends in your data to help identify potential abnormalities and improve long-term performance. Simultaneously, visual summaries on a configurable dashboard allow for accurate data monitoring.
Key Features:
- Large-scale log processing
- Central monitoring dashboard
- Pattern detection for troubleshooting
- Unlimited supported data sources
- Archive and compress log data for storage
Why do we recommend it?
The Datadog Log Management allows the centralized routing of processed logs to third-party destinations, including data lakes or SIEM vendors, through Log Forwarding. This feature helps in easy integration with external systems to access the data quickly.
With an amazingly smooth and professional interface, this solution goes above and beyond to aid in the parsing and analysis of log data. The software is built for scalability, and it can handle millions of log data sources per minute. If you want to use a log parsing and analysis tool to increase your network's general troubleshooting and expansion capabilities—you can't go wrong with this option in that circumstance.
Datadog Log Management is the most scalable of the solutions listed in this article but is built primarily for medium-to-enterprise size businesses. Where it excels is the expanded options for monitoring and remediation through the pattern detection systems.
Who is it recommended for?
Datadog Log Management is a must-have network monitoring tool for seasoned log management experts who prioritize versatility. This helps in ingesting, Live Tail, and archiving diverse logs, deciding on the most valuable ones for retention. The tool's ability to rehydrate logs from compressed archives allows seamless access during audits or investigations, making it ideal for professionals.
Pros:
- It supports DB monitoring and Serverless stack monitoring.
- Easy third-party integrations
- Efficient logging and alerts
- It has excellent data and behavior analysis feature
Cons:
- Removing resources from the data dog tool is a little complex and hard process.