We may earn a commission if you make a purchase through the links on our website.
The Best CSPM Tools

UPDATED: May 29, 2024
Cloud computing and cloud storage are quickly becoming an organization's most important pillars. They are put to use and improved upon so that the customers' data can remain safe and intact.
This not only eliminates the requirement for the company's urgent need to have data backed up in hard drives but also contributes to extending the life of the data by reducing the amount of data that is lost over time. As a result, technologies for managing cloud security posture play an important part in the whole picture.
Here is our list of the best CSPM tools:
- Aikido This SaaS platform provides security testing for applications under development that continues through to their release. Assurance mechanisms before a system goes live involve checking the intended host and delivery mechanisms for security vulnerabilities and that’s where the CSPM comes in.
- CrowdStrike Falcon Horizon This CSPM tool will detect misconfigurations as they happen, allowing you to lessen the impact they have on your network's security. In addition to this, it assures compliance, gets rid of blind spots, and functions well across a variety of cloud platforms.
- Datadog The Cloud Security and Policy Manager (CSPM) from Datadog performs persistent scans of the settings across cloud accounts, hosts, and containers to locate any holes or vulnerabilities. The deployment process is streamlined as a result, and the overall security of your cloud infrastructure is improved.
- CloudGuard Posture Management A package that combines CSPM and workload protection, and can be used for live system monitoring in addition to the development process.
- Fugue This enterprise CSPM solution handles cloud security from the angle of software engineering and assists engineers in building security into environments that are hosted in the cloud.
- Trend Micro Conformity This platform performs real-time monitoring of your cloud infrastructure and automatically remediates any measures that need to be taken to ensure compliance, security, and governance of your cloud assets.
- Ermetic This CSPM solution emphasizes identification first and offers safety across many clouds for your cloud environment. This simple-to-deploy SaaS solution makes it possible for security and DevOps to collaborate without any problems.
- BMC Helix Cloud Security It automates cloud setup security checks and remediation without requiring any sort of coding, making it possible for services such as Infrastructure as a Service to be provided (IaaS).
- Palo Alto Prisma Cloud This service provides logging for compliance purposes in addition to specializing in cloud storage systems and the access permissions that operate on those systems.
- Threat Stack Cloud Security Platform You get continuous security monitoring as well as analyses of your system's vulnerabilities when you use this platform of security systems.
As a result, the vital data belonging to the company are now vulnerable to attack. To protect a company's data, solutions for cloud security management do scans to look for data breaches and misconfigurations. The following is a list of the best CSPM (Cloud Security Posture Management) Tools that are now on the market for your selection.
The Best CSPM Tools
Our methodology for selecting these free Wake-on-LAN clients
It's important to identify critical cloud vulnerabilities and other misconfigurations. Hence, you should consider the things below to pick the right CSPM tool to make the most out of it.
- Consider Infrastructure as Code (IaC) during development and deployment.
- Check for Cloud Platform Support such as AWS, Azure, and Google Cloud.
- Evaluate the tool's capability to provide comprehensive coverage.
- Look for Automated Compliance Checks.
- Look for continuous monitoring and rapid response capabilities.
- Ease of Use and Deployment.
- Consider scalability, flexibility, and customization.
- Consider Incident Response and Remediation.
- Consider both initial costs and ongoing expenses.
- Must go for trial versions or demos offered by CSPM vendors.
1. Aikido
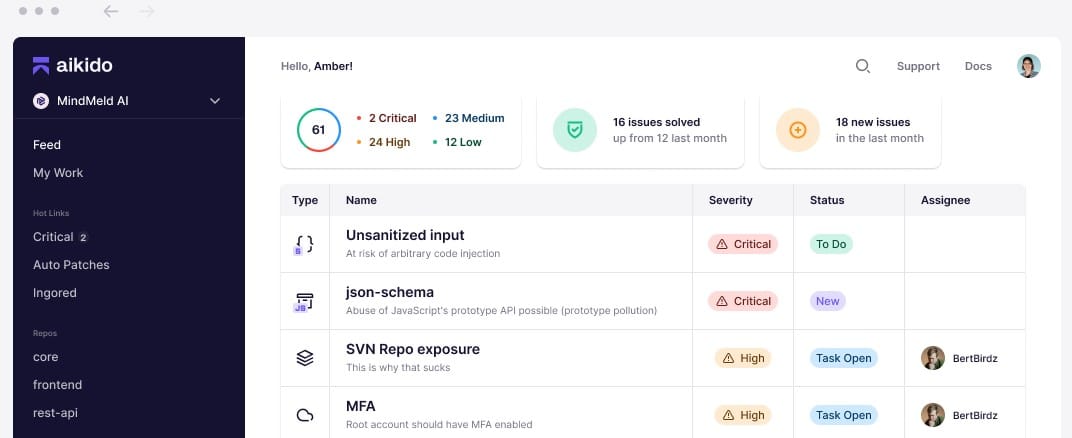
Aikido provides application security testing and it is aimed at DevOps teams. The package is particularly strong at verifying APIs and third-party components and it provides both dynamic and static application security testing. The platform doesn’t go to all of that effort to ensure that applications are secure only to let those systems get released onto insecure platforms. So, the Aikido platform also includes a CSPM that checks hosting systems and platform services to make sure they don’t weaken security.
Key Features:
- Verifies application security
- Accesses code repositories automatically when new code is checked in
- Infrastructure-as-code scanning checks containers and Kubernetes
- Cloud infrastructure verification through a CSPM
- Assesses the configurations of cloud accounts
- Scans platform services for risks
- Looks within containers to identify outdated runtimes
Why do we recommend it?
The Aikido platform ensures that applications for SaaS or the Web are not vulnerable to attack. That diligence goes right down to the cloud systems that underpin those applications when they go live. This is where the CSPM of the package performs its work. A final check of all elements working in concert can reveal secret disclosure or cohesion weaknesses.
Who is it recommended for?
This package is designed for those companies that create and manage SaaS products and Web applications. The service isn’t really aimed at those businesses that subscribe to SaAS packages. The company provides a Free edition, which includes all of the functions of the paid options but with limited capacity.
Pros:
- Automated testing that forms part of a CI/CD release process
- Assigns a severity score to discovered issues
- Consolidates related errors through deduplication to prevent reporting overload
- Some problems can be fixed automatically by the Aikido service
- Integrates with project management and bug tracking services
Cons:
- Operates as part of an application development and release testing process, not as a standalone CSPM
The Aikido service starts by examining any third-party code that is marked for inclusion in an application development project. The next service is a continuous testing system that can launch tests automatically when code is checked into a repository. These tests perform both dynamic and static application security testing.
The package includes scans for the infrastructure-as-code, containers, and cloud platforms that will host, protect, deliver, and segment instances of the application as they run. This is where the CSPM is implemented. The consideration of cloud services can also be tested in conjunction with the running application during release testing to ensure that there is no secret disclosure between modules.
The Aikido platform is a subscription SaaS package with four plans and the first of these is free to use. There is no free trial for the service but the company recommends that potential buyers sign up for the free plan in order to test the system.
EDITOR'S CHOICE
Aikido is our top pick for a CSPM tool because this system puts cloud security posture management into a specific context. The cloud security testing is implemented in conjunction with scanning of the applications that they are going to serve. This strategy can reveal security weaknesses that might exist in the interactions between the application and its supporting infrastructure. These are factors that testing the application in isolation and the cloud services by themselves would not reveal. The tool is able to examine infrastructure-as-code, Kubernetes, and containers along with their hosts and the software that they contain.
Download: Access the FREE Trial
OS: Cloud-based
2. CrowdStrike Falcon Horizon
The elimination of security blind spots is accomplished through the use of agentless cloud-native protection that performs continuous analysis of your environment for misconfigurations. You will have complete visibility into your multi-cloud environment with the help of CrowdStrike Falcon Horizon, which offers a single source of truth for cloud resources.
Key Features:
- Ongoing and intelligent monitoring of cloud resources.
- Deployment of cloud applications that are safe and offer enhanced speed and effectiveness.
- Unified visibility and control across all of the different cloud environments.
- Address any concerns regarding the network's security.
- Assist developers in preventing them from making expensive mistakes.
- A reduction in alert fatigue is one of the goals of threat detection.
- There is no disruption caused by the integration with SIEM solutions.
Why do we recommend it?
We recommend CrowdStrike Falcon Horizon for its cutting-edge antivirus protection, effectively guarding against malware threats. The platform simplifies host firewall management, streamlining security processes. Additionally, users benefit from real-time insights through automated threat intelligence, enhancing overall cybersecurity by staying ahead of potential risks and attacks.
Who is it recommended for?
CrowdStrike Falcon Horizon is recommended for security experts and professionals who require advanced threat detection capabilities. When it identifies a security weakness, the system promptly raises an alert, offering insights into potential vulnerabilities. This tool is particularly beneficial for experts managing access rights and evaluating account structures in Azure AD. Moreover, the support team of security experts at CrowdStrike is readily available to provide guidance and advice on necessary tasks.
Pros:
- It helps to detect cloud misconfigurations
- Monitors entire virtual network and other assets
- Observability and log management
- Targeted threat detection
- Experts provide remedies and guides
Cons:
- It can be difficult to set up on Mac due to other extensions.
You will not only gain helpful information and insights into your overall security posture, but you will also receive guidance on how to avoid future security difficulties. This is a significant benefit. This tool's most notable function is that it gives you full insight into all cloud-native assets across your whole cloud architecture, even if those assets are dispersed across more than one cloud environment.
This is the tool's most notable feature. This not only provides broad context and insight into your security decisions but also assists you in taking the required actions to ensure the security of your cloud. This CSPM program will automatically find devices that are not being protected by it and will notify you to take immediate action. Falcon Horizon's automated discovery helps to ensure that there are no unmonitored devices or blind spots in your cloud architecture. This is accomplished by ensuring that there are no unmonitored devices.
3. Datadog
The Datadog monitoring software is offered both as an on-premises installation and as a service hosted in the cloud (SaaS). Windows, Linux, and macOS X are all supported operating systems by Datadog. Several cloud service providers, including Amazon Web Services, Microsoft Azure, Red Hat OpenShift, and Google Cloud Platform, are supported.
Key Features:
- Delivers a consolidated perspective of an IT/DevOps team's underlying infrastructure.
- Dashboards that are modifiable to the user's specifications.
- In reaction to significant issues, alerts are disseminated to the appropriate parties.
- There is support for over 250 different product integrations.
- Logs, error rates, and latency measurements are all automatically gathered and examined.
- Gives you access to use the API.
- Software written in Java, Python, PHP,.NET, Go, Node, and Ruby, among other languages, is supported.
Why do we recommend it?
Datadog Cloud Security Posture Management is recommended for its robust features, conducting continuous configuration scans on cloud accounts, hosts, and containers. With comprehensive checks, it ensures adherence to industry benchmarks. The tool's continuous scanning and executive reporting deliver valuable insights for tracking and maintaining strong security postures in dynamic cloud environments.
The user interface consists of dashboards that can be personalized to provide graphs that are constructed from a variety of data sources in real-time. Consumers may also be notified by Datadog whenever there are performance issues with any collection of metrics, such as compute rates, if the situation warrants it.
Who is it recommended for?
Datadog Cloud Security Posture Management is useful for security experts and IT professionals who need to manage complex cloud infrastructures. This tool provides security posture scores across the entire infrastructure, enabling them to trace each score back to specific benchmark or framework criteria. In addition, this helps in the precise identification and remediation of security vulnerabilities, ensuring a resilient and compliant cloud environment.
Pros:
- Supports cross-platform cloud compatibility
- You can connect it to data dog security system
- Supports session replay and error tracking
- Workflow automation
- Incident management
Cons:
- It doesn't provide automated solutions
This configuration security patch management tool gives you full visibility of your settings at any moment. With this access, you will be able to answer some important questions such as the configuration of your S3 bucket over the past month, the status of your Kubernetes containers, and many more. In addition to this, it offers a more accurate context for your arrangement.
Only in the event of significant configuration errors will Datadog's CSPM allow you to send individualized notifications to the relevant teams. If it is necessary, you can even adjust its settings to cause it to issue alerts at the account or service level.
4. CloudGuard Posture Management
Your security posture can be seen with the assistance of CloudGuard Posture Management, which also automates governance and compliance across several cloud services. It is an additional reliable security tool that assists in locating misconfigurations, vulnerabilities, and threats in a system. In addition, it protects the sensitive data you have by enforcing the best security practices and rules across all of the numerous projects, accounts, and virtual networks you have.
Key Features:
- Conducts audits to find an improper activity.
- Cloud intrusion detection.
- Defends against dangers that come from within.
- Offers notifications in real-time.
- Provides safety for the workload as well as application security.
Why do we recommend it?
CloudGuard Posture Management follows a comprehensive approach to cloud security and compliance in native environments like AWS, Azure, Google Cloud, and Kubernetes. It has many great features, such as automated security, governance, and compliance features, that help with high-fidelity visibility and control.
Users are also able to scale across many cloud platforms with CloudGuard Dome9, including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). It is a cutting-edge service that guards the information of your firm from any risks posed by employees from within.
Who is it recommended for?
CloudGuard Posture Management is an important tool for security professionals, cloud architects, and IT specialists who deal with operational and developmental aspects. It can easily be integrated across various cloud platforms to manage workload protection and dynamic cloud environments.
Pros:
- It takes instant actions on alerts
- Supports central firewall administrator
- Real-time cloud compliance monitoring
- Allows to create custom rules across infrastructure
- It offers detailed information about the entire environment
Cons:
- It might mess up remediation when you change the rules
Another justification for including the CSPM tool on the list is that CloudGuard Dome9 is a quick and efficient cloud security platform that makes compliance and governance a breeze. Control is provided over IAM users and roles by CloudGuard Posture Management. As a result, granular permissions in multi-cloud settings may be easily managed by administrators.
5. Fugue
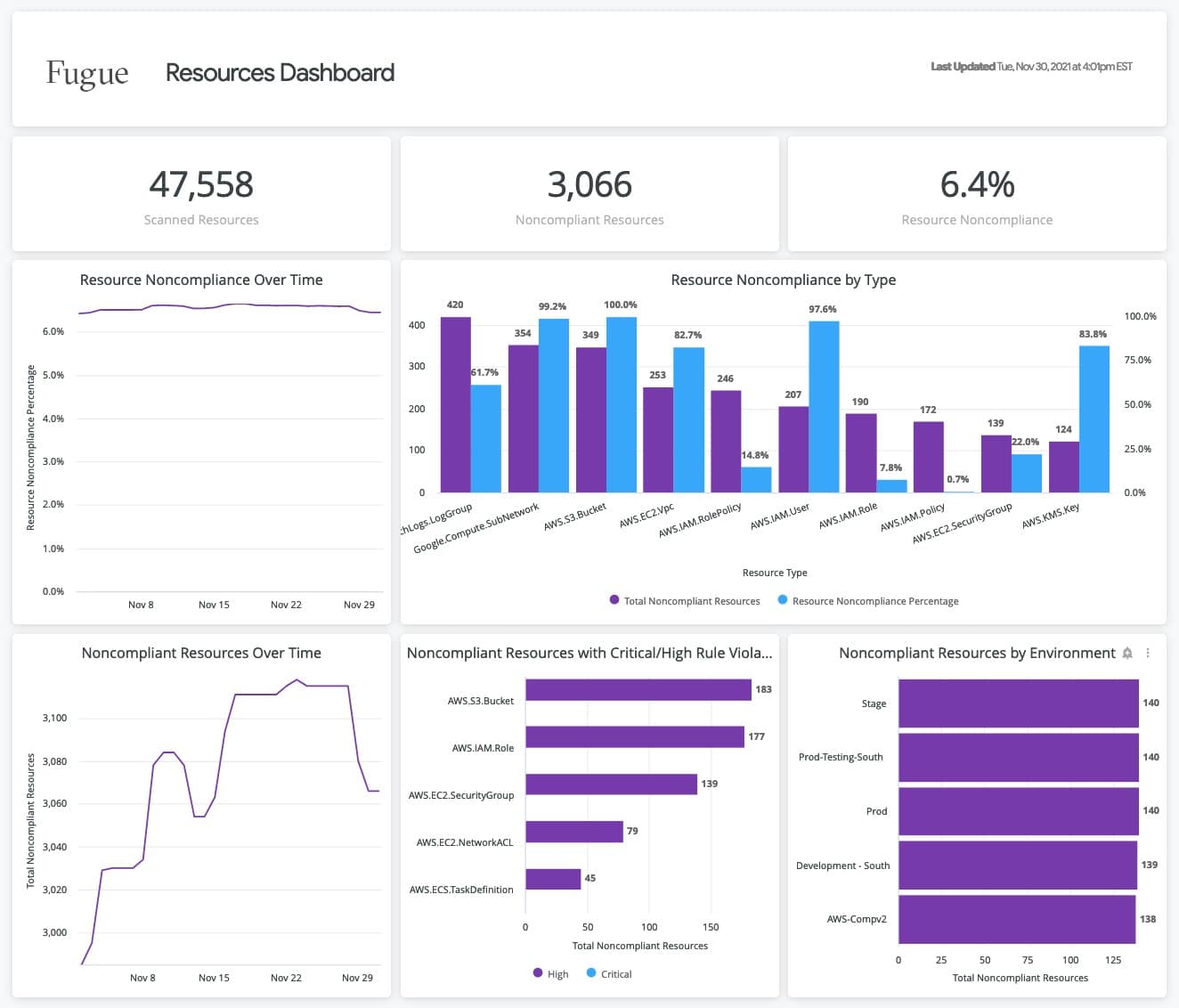
Cloud security and compliance platform Fugue uses a uniform policy engine that is powered by the Open Policy Agent to protect all stages of the software development lifecycle (OPA). The security and cloud engineering teams can work more efficiently thanks to Fugue since it increases their level of trust in the cloud's security. Users can use Fugue to perform pre-deployment security checks on CloudFormation, AWS, Kubernetes manifests, and docker files, and receive actionable remedial feedback via developer-friendly tools. Fugue is available to users on Windows, macOS, and Linux platforms.
Key Features:
- Enables customers to safeguard CloudFormation throughout the entirety of the improvement process.
- Is governed by a centralized policy framework.
- Organizations can reliably employ compliance and security measures.
- It gives consumers advanced tools for both visualizing data and reporting on it.
- Customers can better protect their CloudFormation thanks to the Regula policy engine in Fugue.
Why do we recommend it?
Fugue is one of the reputed CSPM tools that provides tools to integrate security measures from the initial development stages through deployment, enabling robust and continuous security practices across cloud environments. These tools scan your cloud infrastructure against predefined regulatory standards and security best practices, quickly identifying compliance gaps.
Several industry-leading platforms, including Slack, Jira, OpsGenie, and ServiceNow, are among those that interface effectively with Fugue. Ticketing and messaging throughout the company are streamlined as a result.
Who is it recommended for?
This tool is recommended for cloud security experts, DevOps professionals, and IT specialists. It helps to detect infrastructure misconfigurations, enforce policies, and automate cloud lifecycle management to make workflows smooth for DevOps teams. With customized reporting and analytics, security experts can gain valuable insights into the compliance status and take informed actions to enhance cloud security measures.
Pros:
- It has a centralized policy framework
- It supports cloud account management
- It provides deeper visibility and accurate reports
- Supports drift detection
- Automated threat remediation
Cons:
- It might be expensive for small or medium business
This platform performs continuous monitoring of your platform and keeps track of any configuration changes as well as potential vulnerabilities. It even uses guardrails to protect critical resources, preventing unwanted access to information and data. In addition, Fugue continuously compares its performance to previously defined baselines to spot any potential vulnerabilities.
6. Trend Micro Conformity
The Trend Micro Conformity CSPM tool is all-encompassing cloud security and policy management solution that continuously monitors your cloud environment to ensure regulatory compliance and good governance for your cloud infrastructure. It comes equipped with a plethora of capabilities that can cater to the requirements of various groups operating inside your corporation.
Key Features:
- Complete and all-encompassing visibility.
- Completely Computerized compliance audits.
- Encourages the adoption of a DevOps culture.
- Remediates misconfigurations.
Why do we recommend it?
Trend Micro Conformity has the amazing capability to quickly assess security, governance, and compliance risks in cloud environments. Its automated cloud risk assessment feature provides organizations with a rapid understanding of their risk levels. It goes through a complimentary session where their cloud engineers conduct this assessment for AWS and Azure for proper evaluation of potential vulnerabilities.
Correcting incorrect setups is the area of expertise of Trend Micro Conformity. It performs ongoing monitoring of your infrastructure and, if there are any misconfigurations, it delivers real-time notifications together with information providing context about the issue. All of this makes it easier for the different teams to address the problems as quickly as possible.
Who is it recommended for?
Trend Micro Conformity is recommended for cybersecurity professionals, cloud architects, and IT experts responsible for ensuring the security of workloads across diverse environments, including virtual, physical, cloud, and containers. This tool is best at providing runtime protection for workloads and offers cloud network layer Intrusion Prevention System (IPS) security; hence, it's a valuable asset for organizations with layered security strategies.
Pros:
- Great visibility and behavior analysis
- Intrusion detection and prevention
- Anti-malware functionalities
- Easy and simple dashboard
- It is multi-cloud support
Cons:
- Might face issues in granular control and deployment
Overall, Trend Micro Conformity is equipped with a wide variety of cutting-edge capabilities that make it possible to enforce security, governance, and compliance throughout the entirety of your cloud architecture. Even the reports required for compliance and internal auditing are produced by it automatically.
7. Ermetic
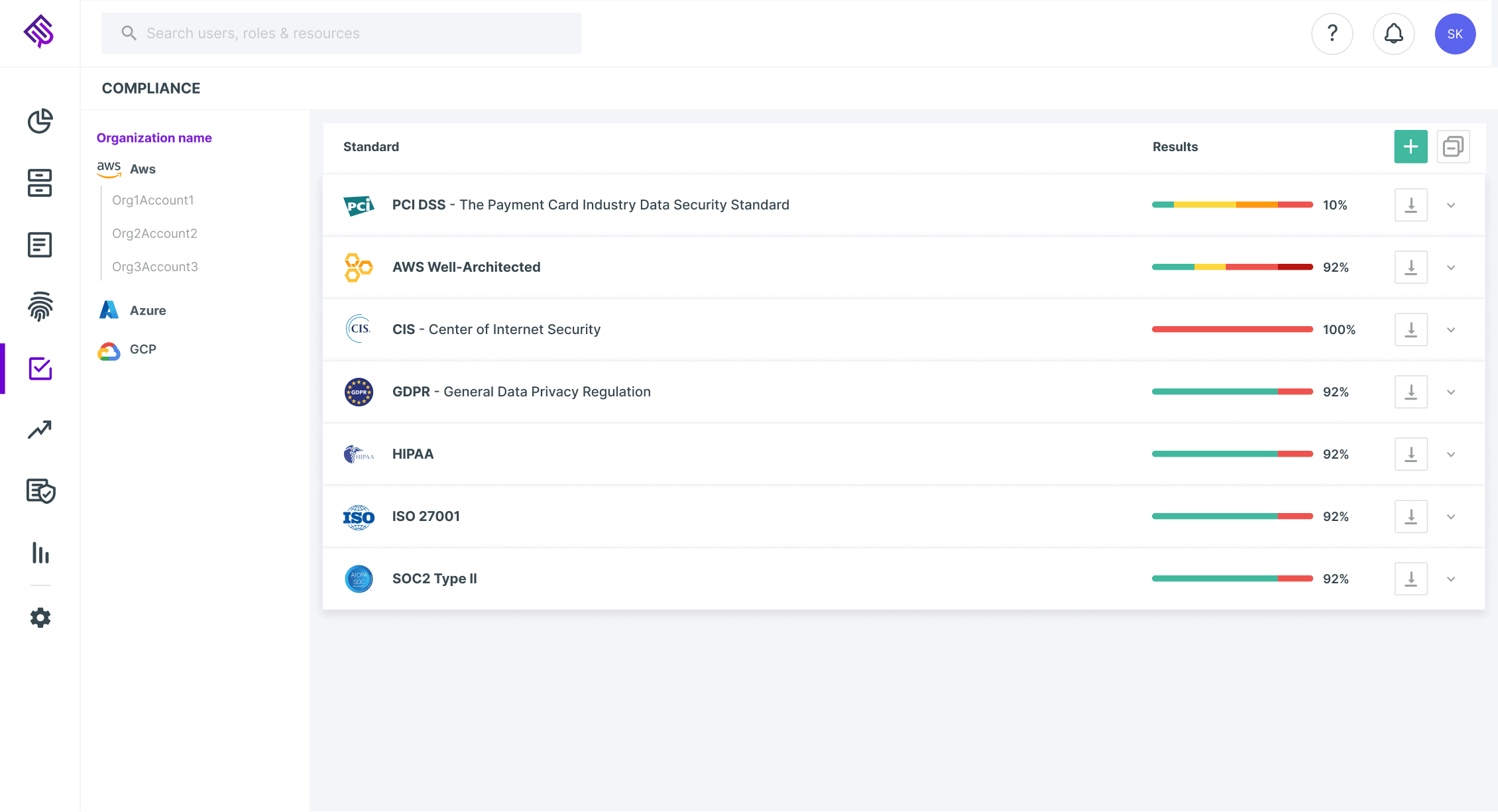
Ermetic is a Cloud Security Policy Manager (CSPM) that puts identity first and offers protection for multi-cloud environments. This software as a service solution controls your cloud assets, finds abnormalities and misconfigurations, ensures compliance, and lets the security and DevOps teams collaborate more effectively.
Key Features:
- Allows for the automation of cloud compliance.
- Combines CIEM and CSPM into a single system.
- Identity-centric.
Why do we recommend it?
This tool allows organizations to identify and understand the entities with network access to specific resources. By providing visibility and control, Ermetic helps mitigate security risks arising from network misconfigurations, making it an essential solution for safeguarding cloud environments.
Who is it recommended for?
Ermetic is recommended for security professionals, Kubernetes administrators, and DevSecOps experts responsible for the security and compliance of Kubernetes clusters across diverse cloud infrastructures. This tool has the capability to reveal, prioritize, and remediate security gaps, which streamlines the process of automating compliance measures.
Pros:
- Improved security scan
- You can access pre-built reports and dashboards
- Helps streamline IT workflow
- Provides Administration tools/console
- Helps with routine maintenance tasks
Cons:
- You might face a lack of integration options
Overall, Ermetic is a powerful cloud security and privacy management application that offers thorough protection for your cloud assets and identities. It does this by combining the functionalities of CIEM and CSPM, which enables it to deliver novel insights regarding security and governance.
This one-of-a-kind piece of software provides comprehensive cloud security by integrating both the CIEM and the CSPM programs. These two tools each tackle the issue of security from a unique perspective.
8. BMC BMC AMI Cloud
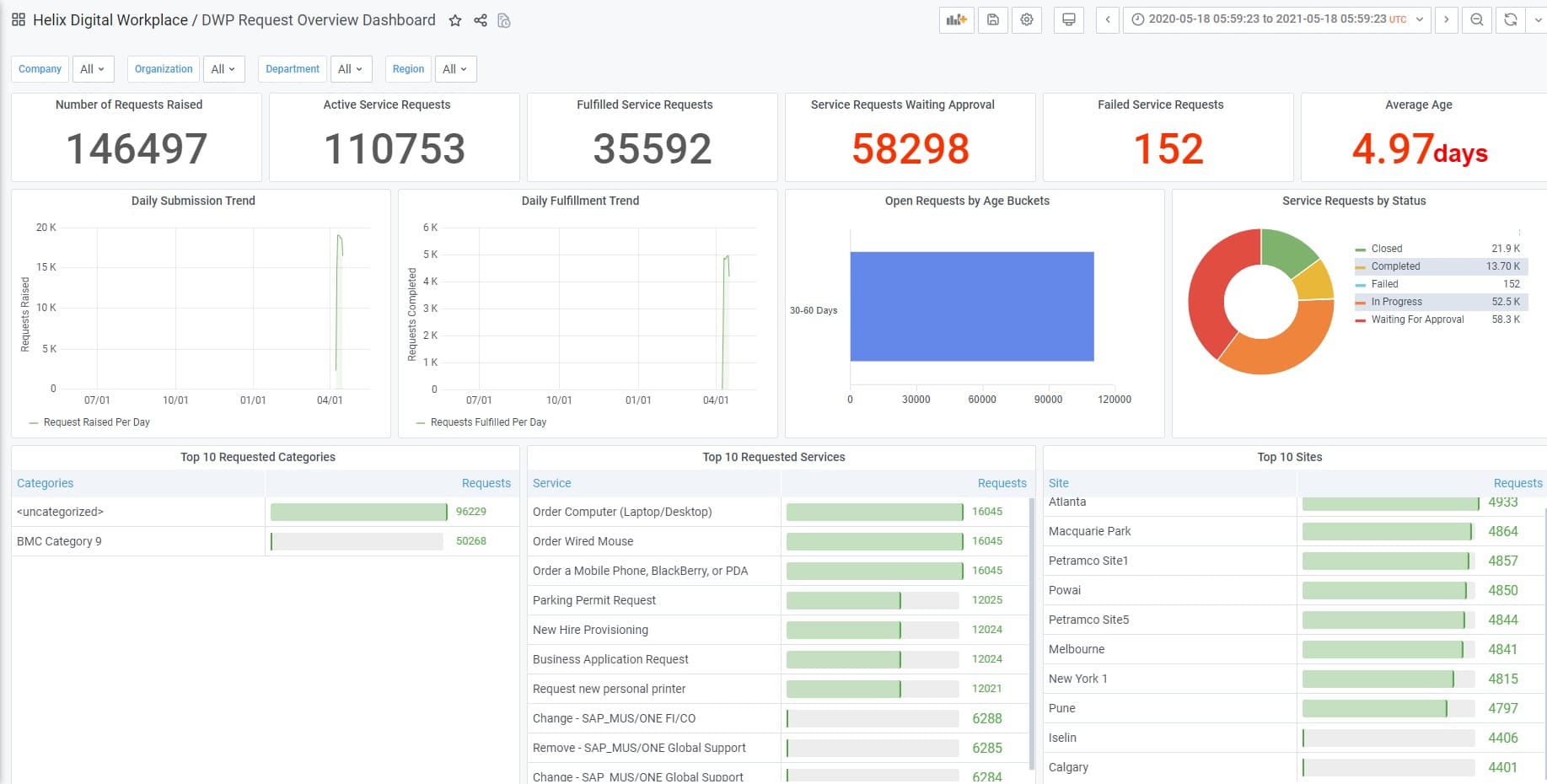
BMC AMI Cloud can automate cloud configuration security checks and remediation without requiring any coding on the part of the user. This makes it possible for services such as Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) to have a secure and consistent set up along with an audit trail.
Key Features:
- BMC AMI Cloud streamlines the process of managing the cloud's security posture.
- Self-driving remediation, automatic remediation with an easy user interface, and self-driving remediation.
- Support for customized remediation is all features included in the software.
- BMC AMI Cloud has policies available for use.
Why do we recommend it?
Experts prefer BMC AMI Cloud due to its robust features, including cloud security scoring and remediation. You don't need any coding as it has automated remediation capabilities, which will look at security issues in cloud environments.
BMC AMI Cloud can improve governance while simultaneously lowering risk since it integrates compliance and security testing into service delivery and cloud operations.
Who is it recommended for?
BMC AMI Cloud is widely used by cloud security professionals and DevSecOps teams to manage the security of cloud environments. Experts use this tool for automated security checks and remediation features to suit AWS, Azure, and GCP IaaS and PaaS services.
Pros:
- It supports role-based security
- It has a top-notch support team
- You can customize it according to your organization's security needs
- Configuration and incident management
Cons:
- It is expensive as compared to other CSPM tool
Integrating incident and change management in a closed-loop not only ensures that everything runs well but also makes it possible for scrum teams to simply manage their security posture while adhering to governance guidelines. Facilitate agility rather than obstruct it. If you have access to a large amount of content, you can start safeguarding your cloud footprint in as little as five minutes.
9. Prisma Cloud
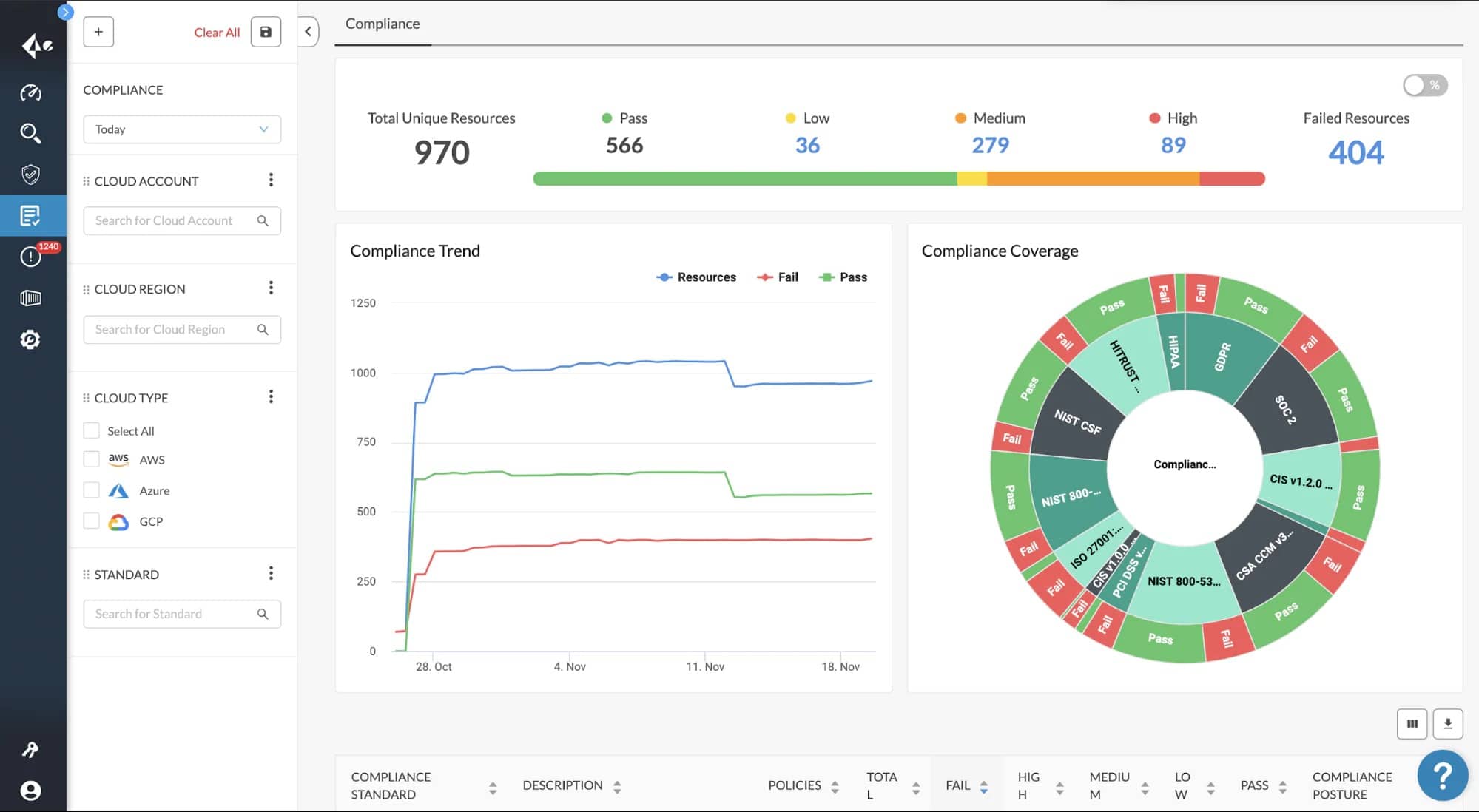
Prisma Cloud is an industry-leading cloud-native security technology that provides unparalleled visibility and protection across many cloud computing environments, including Google Cloud and Microsoft Azure. Additionally, with the utilization of its superior functionality, it offers protection against unwelcome dangers. Container image sandboxing is a new function that has been added to the industry-leading CSPM tool. This feature aids in the detection of potential security risks by evaluating all of the files, processes, and pre-deployments of network activity.
Key Features:
- Preserves the natural growth of cloud-based systems.
- Detection of the exfiltration of data from networks.
- The application of policies governing governance.
- Conducts scans for malicious software on shared cloud storage.
- Offers comprehensive runtime protection for the entire stack.
- Guards the workload in the cloud, the network, and the security posture.
Why do we recommend it?
Prisma Cloud allows organizations to monitor posture, detect and remediate risks, and maintain compliance in a multi-cloud environment. If you have a wider user base, then you must have this tool; it provides effective control over permissions across diverse cloud platforms to effectively manage permissions and access control.
Using Prisma cloud, developers can locate and eradicate cloud blind spots in their applications. In addition, with the assistance of the Prisma cloud, the load of alert weariness is also significantly decreased.
With its single-agent structure, Prisma Cloud provides full control over public cloud environments, hosts, containers, and other platforms, making it an ideal solution for all of your cloud security requirements. It delivers full-stack runtime protection, full network visibility, and support for API security as well as container security.
Who is it recommended for?
Cybersecurity experts, cloud security professionals, and IT administrators find this tool useful for safeguarding cloud environments. This tool is particularly valuable for experts focused on identifying sensitive data and scanning for malware within public cloud storage. Additionally, it helps in securing virtual machines (VMs) across various public or private cloud platforms, to provide robust protection for sensitive information.
Pros:
- Compliance and Alerts with extreme detail
- Allows to add custom queries using RQL language
- CI/CD pipeline to identify any security issue before deployment
- Simple integration and supports multi-cloud
Cons:
- It can be hard to set up for new users or non-tech person
Prisma Cloud is a good option to go with if you are seeking a CSPM tool that can maintain compliance across multi-cloud and hybrid-cloud settings.
10. Threat Stack Cloud Security Platform
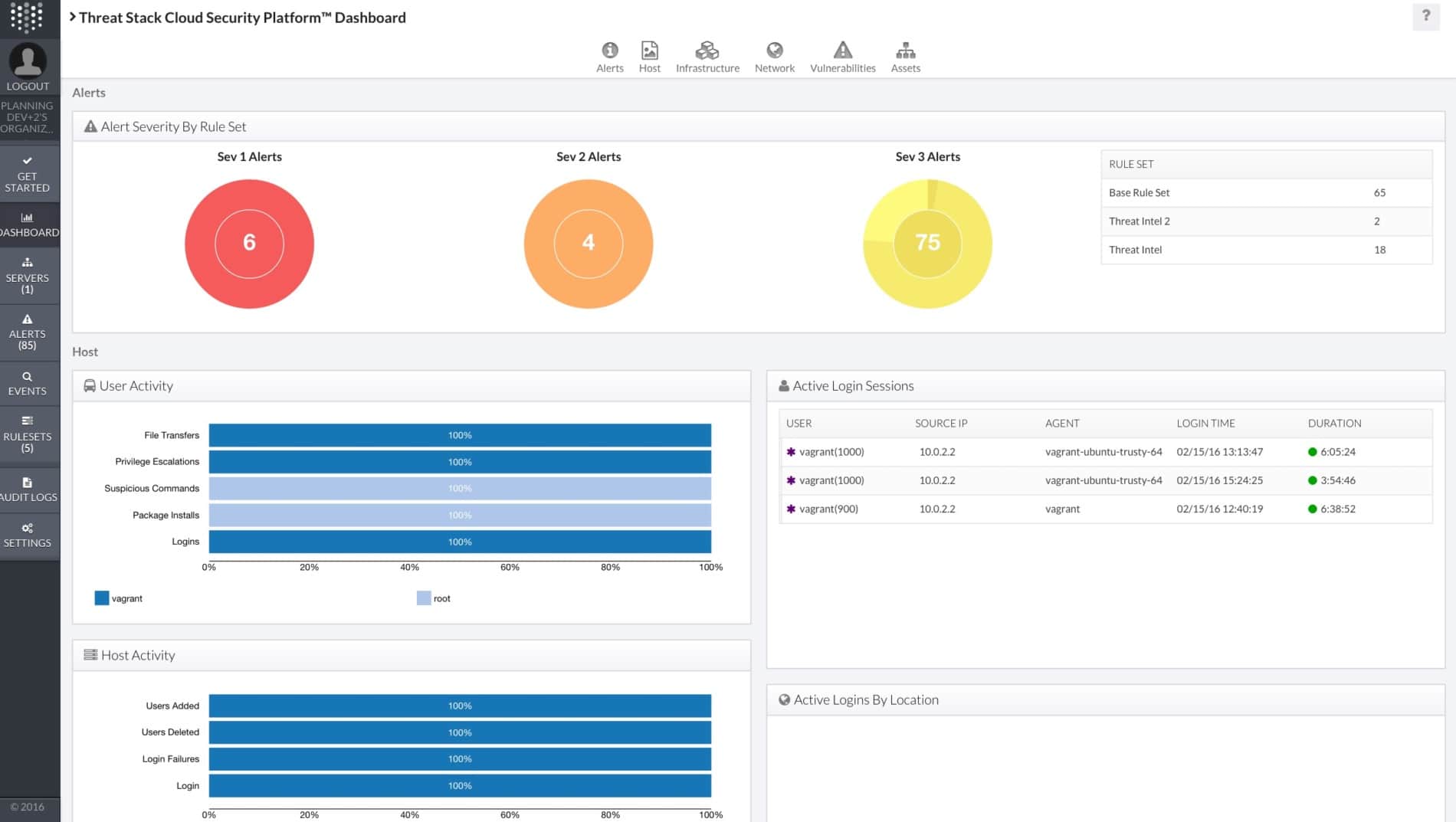
Threat Stack is a cloud service provider management (CSPM) platform that enables visibility across cloud management consoles, apps, and infrastructure. It was developed for current applications and cloud-native architecture. It is a widely used platform that operates in the cloud and provides assistance to businesses in identifying, prioritizing, and reacting to both real-time and unforeseen threats.
Key Features:
- Security for the application and infrastructure.
- Encourages compliance with IAM policies.
- Accessibility to both on-premises and cloud-based instances.
- Guarantees complete safety and adherence to regulations across the whole cloud infrastructure.
- Compatible with a variety of third-party security operations tools.
- Offers protection for both containerized applications and Kubernetes.
Why do we recommend it?
Threat Stack specializes in mitigating application-based and volumetric distributed denial of service (DDoS) attacks. This tool stands out for its ability to protect web applications using advanced threat detection and artificial intelligence/machine learning (AI/ML) intelligence. It provides a robust defense against a range of cyber threats.
In addition, it offers improved outcomes for customers through its essential capabilities and sophisticated features, which include, amongst others, Vulnerability Assessment, Policy Management, Configuration Auditing, and Incident Management.
Machine learning, rules, and the integration of full-stack telemetry are the foundation of Threat Stack's one-of-a-kind strategy for securing cloud environments. It is also capable of supporting CloudTrail monitoring and IAM controls, making it one of the most effective solutions for protecting application infrastructure.
Who is it recommended for?
Threat Stack helps cybersecurity professionals, threat hunters, and IT experts in real-time detection and mitigation of malicious bot attacks. It is particularly valuable for experts who want to protect customer credentials, financial details, and Personally Identifiable Information (PII) against threats such as Magecart, Formjacking, and other client-side supply chain attacks.
Pros:
- Proactive monitoring
- Offers real-time protections
- Vulnerability assessment
- Built-in and configurable rules
- Supports Integrations with third-party SecOps tools
Cons:
- It sends lots of alerts that are not critical or malicious
Threat Stack is an excellent choice for your company if you are searching for a CSPM tool that can respond to known as well as unknown vulnerabilities and threats. If this describes what you need, read on.
The Best CSPM Tools: Editor’s Choice
The CSPM tool that is greatest for you is going to depend on the unique needs you have in contrast to the tool that handles these pain areas the best. After you have narrowed your choices down to a few instruments that have capabilities that are comparable to one another, the price will be the decisive factor.
CrowdStrike Falcon Horizon is our top choice as it is meant to maximize client visibility into real-time and historical endpoint security events by capturing event data necessary to identify, understand, and respond to threats. This is accomplished through the use of event data collection.