We may earn a commission if you make a purchase through the links on our website.
The Best Ransomware File Decryptors

UPDATED: May 31, 2024
The best weapon against ransomware is prevention. But if prevention is too late (you are under fire), or your backups were lost or also encrypted by ransomware, how can you continue with business?
When you are pushed into a corner, a ransomware file decryptor will be your ultimate blow against these deadly threats.
In this post, we will go through how to use a ransomware file decryptor tool and list the best eight decryptor tools in the market to help you get away with your data without paying a ransom.
Here is our list of the best ransomware file decryptors:
- Kaspersky anti-ransomware tools Kaspersky is a member of the NMRP. they provide intelligence and resources with free ransomware file decryptors.
- McAfee ransomware recovery (Tr2) Another member and supporter of the NMRP, McAfee, provides their Tr2— a security framework to develop decryption solutions.
- Emsisoft ransomware decryption tools Emsisoft offers more than 84 different free tools to decrypt popular and dangerous ransomware variants.
- AVG ransomware decryption tool AVG offers seven free ransomware file decryption tools for strong and risky Ransomware variants.
- Trend Micro ransomware file decryptors A leader in cybersecurity solutions, Trend Micro, offers various free decryption tools for dealing with 27 different Ransomware variants.
- Bitdefender anti-ransomware Bitdefender provides various free tools to decrypt ransomware-encrypted files and ransomware recognition software.
- Avast anti-ransomware tools Avast is another leader in ransomware file decryption. They provide 30 free decryption tools to deal with popular and risky Ransomware variants.
- Quick Heal’s free ransomware decryption tool. An easy-to-use set of free ransomware file decryptors. This tool also includes automatic Ransomware-type scanning and backup.
Prevention Goes Before a Ransomware File Decryptor
The best weapon against Ransomware is not a file decryptor but prevention. If you are armed beforehand with the right tools and strategies to deal with a Ransomware attack, you shouldn't really need a Ransomware file decryptor. But still, Ransomware tends to be persistent and relatively successful (especially if you are a direct target), so a Ransomware file decryptor would come in handy when you are already under attack.
A few bullet point steps to help you prevent a Ransomware attack (if you are not already under attack)?
- Training End-users should be cautious and aware of the social tactics used by hackers and attackers. Train yourself or the network users to be suspicious of email attachments, avoid clicking on ads or links, detect phishing scams and shady websites, or open any executable file.
- Update and patch Updating and patching your operating system, applications, and software is key to avoiding vulnerabilities exploited by Malware. Ransomware is Malware that uses a system's vulnerabilities (or weak social link) to enter a system.
- Use security software Use security tools such as anti-virus and anti-malware and configure them to perform scans automatically. Ensure all security software is up-to-date.
- Back up intelligently Perform regular backups of all your data and ensure they are complete and can be restored. Use the 3-2-1 rule of backups: (3) Create at least three copies of your data, (2) save your backups to two different types of media, and (1) create at least one offsite copy. Backups (with full recovery) become the best way to defeat Ransomware, so always secure your backups and ensure they are not connected to the computers being backed up. Offsite backups are key!
Although you might have considered a few of the abovementioned prevention steps, you or your organization still fell victim to a Ransomware attack. So what can you do? How can you ensure business continuity? What will you do if you decide not to pay a ransom or if you do decide to pay, but your data remains locked? How would you manage a crisis and respond to this incident?
Should you (or not) pay the ransom?
According to the ransom note, you will only get access to a decryption key until you pay the ransom. If you refuse to pay, you can technically and permanently say goodbye to your data. But, even though your data is at stake, everybody would advise you not to pay a ransom.
Why shouldn’t you pay?
Remember that this is only the beginning. If you pay, you are compliant in the eyes of these criminals, who will return to extort you even more. Even the FBI would not support paying a ransom in response to a Ransomware attack. The reasons are sound enough: first, there is no guarantee you’ll get your data back (although they might offer proof, such as decrypting one file for free), and second, giving your hard-earned money only gives criminals more funds to innovate and extend their reach.
NOTE: There are cases where payment is the only way. Especially when critical data and infrastructure is at stake, for instance, sensitive information, intellectual property, health patient data, etc., ensuring the services are back on track is paramount so that payment might be the only option.
But yet, whether you pay or not, ransomware generates quite a stressful situation. If you are already under fire and have decided not to pay the ransom (for now), you can try your shot with a ransomware file decryptor.
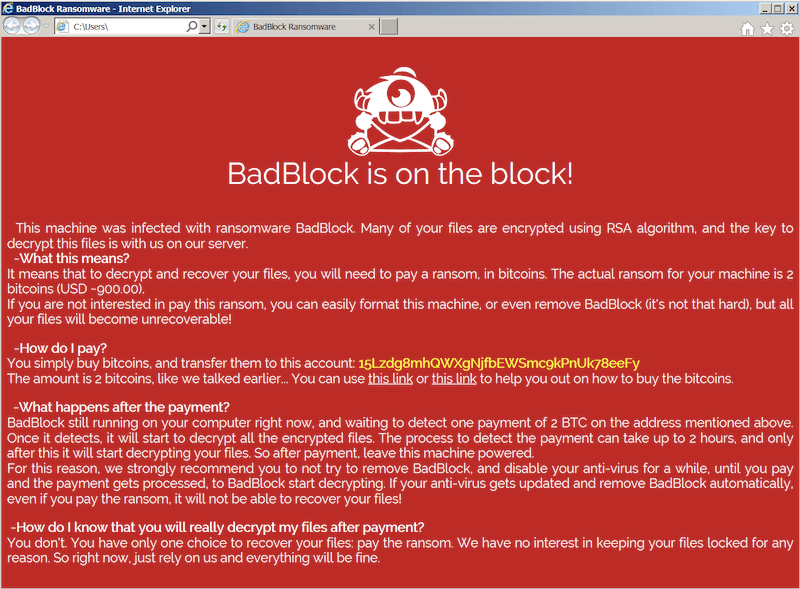
How to use a Ransomware file decryptor?
If you have decided not to pay for a ransom, then it is likely that you either have a backup, don't care about the data at stake, or choose to decrypt ransomware-encrypted files using a file decryptor tool.
Ransomware file decryption tools work: by either solving “weak” encryption algorithms or by getting a master encryption key. As Ransomware variants evolve (i.e., algorithm or key), these tools become pointless.
- There is no guarantee Before using a ransomware file decryptor, keep in mind that not all Ransomware is the same. Ransomware is evolving into more advanced encryption methods and diversifying into thousands of variants. In addition, the criminals know about the existence of Ransomware file decryptors, and they know that you will likely use one, so they are constantly updating their software to make it resistant to these decryptors. Ransomware file decryptor tool developers, “the good guys,” are always looking for zero-day Ransomware malware, attempting to decrypt it, and update their software accordingly. Ransomware file decryptors can't offer any guarantee or success rate.
- Ransomware file decryptors are usually free Because these tools can't provide a guarantee, and some developers support the cause, such as the No More Ransomware Project, the tools are usually free. Some of these tools might belong to complete anti-ransomware solutions.
- Don't be fooled Before getting a Ransomware file decryptor, ensure that you haven't been only infected by Scareware— a fake software that claims you have been infected and directs you to pay for a solution. Some Scareware might look like Ransomware, showing windows or popups wanting to frighten you. Scareware downloads Malware (possibly actual Ransomware) and steals your data. To recover from Scareware, run a full scan with updated antivirus software.
- Identify the Ransomware To know which Ransomware file decryptor tool to use, you'll first need to identify the type of Ransomware locking your files by looking into the details of the warning message (txt, HTML, URL, Bitcoin address, onion, etc.) and the extension of the encrypted file. Usually, Ransomware file decryptor tools target the most common and destructive variants: Crypto ransomware or encryptors. Examples of such Ransomware are Crypto, Petya, Wanna Cry, REvil, NoobCrypt, Cerber, or Locker. Once you have identified the type of Ransomware, you'll need to determine the right Ransomware file decryptor tool.
- Remove or quarantine the Malware Before attempting to decrypt the “encrypted” files” with a Ransomware file decryptor, you'll first have to deal with the Ransomware infection. Use an updated antivirus to remove or quarantine the Malware that got you infected with the Ransomware in the first place. Failure to do so will encrypt your files again.
- Get help! To help you identify the Ransomware and possible solutions, check the No More Ransomware Project (NMRP) — backed by Europol, EC3, Politie, McAfee, and Kaspersky). Additionally, if you see no escape, you can also hire specialists; Ransomware recovery companies, such as Mimecast or DataRecovery, will provide special decryption services at a price.
In the next section, we will review the best Ransomware file decryptors. These tools have defeated some of the current popular Ransomware variants. But as stated above, as Ransomware evolves, these tools will be pointless.
The Best Ransomware File Decryptors
The idea of using these tools is to save your data by circumventing and avoiding having to pay for ransoms. Keep in mind that most of these tools are free and do not offer any guarantee. They work with specific Ransomware variants and may not work with versions of the Ransomware that were released after these products.
1. Kaspersky Anti-Ransomware tools
Kaspersky is a proud member and contributor of the No More Ransomware Project and thus has a good amount of authority when dealing with ransomware. Kaspersky provides various solutions, not only to prevent but also to remove and decrypt ransomware. Kaspersky offers free anti-ransomware (decryptors) software for specific variants like Shade, Rakhni, Rannoh Decryptor, CoinVault, Wildfire, and Xorist.
Another Kaspersky solution to defeat ransomware is the Free Rescue Disk which you can use to boot a Windows machine and then implement the Windows Unlocker tool. For a more comprehensive and unified solution primarily targeted at businesses, you can try Kaspersky Endpoint Security Solution, which prevents and rolls back any malicious activity from ransomware. These tools are used along with Kaspersky's free ransomware file decryptors.
2. Trellix (formerly McAfee Enterprise)
Trellix (formerly McAfee Enterprise) is a key contributor and partner of the No More Ransomware Project, leveraging its extensive resources, intelligence, and technology to combat ransomware. The rebranding of McAfee Ransomware Recover (Mr2) to Trellix Ransomware Recover reflects the broader integration following the merger of McAfee Enterprise and FireEye in October 2021. Trellix Ransomware Recover receives regular updates to incorporate new decryption keys and mechanisms for newly identified ransomware strains.
This framework is designed to unlock all types of encrypted files, applications, databases, or any other objects. It is freely available to anyone who has the decryption key and methodology needed to develop a decryption framework. However, it is important to note that as a free tool, technical and customer support for Trellix Ransomware Recover is limited. Click here to download.
3. Emsisoft Ransomware Decryption Tools
Emsisoft is a world-class developer of home and business computer security software designed to prevent, detect, and mitigate threats. Emsisoft is another associate partner of the popular no-more-ransom project. They provide various Ransomware Decryption Tools to download for free, such as the Maze / Sekhmet / Egregor decryptor, Diavol decryptor, DeadBolt decryptor, Djvu decryptor, or Yashma decryptor.
As of now (06 Dec 2022), there are 84+ Ransomware file decryptor tools provided by Emsisoft, so you have a good chance to find a solution to decrypt your Ransomware. To decrypt a file with Emsisoft, just point to the disk that has been infected (with a specific variant). Keep in mind that technical support for Emsisoft tools is only provided for paid customers.
4. AVG Ransomware Decryption Tool
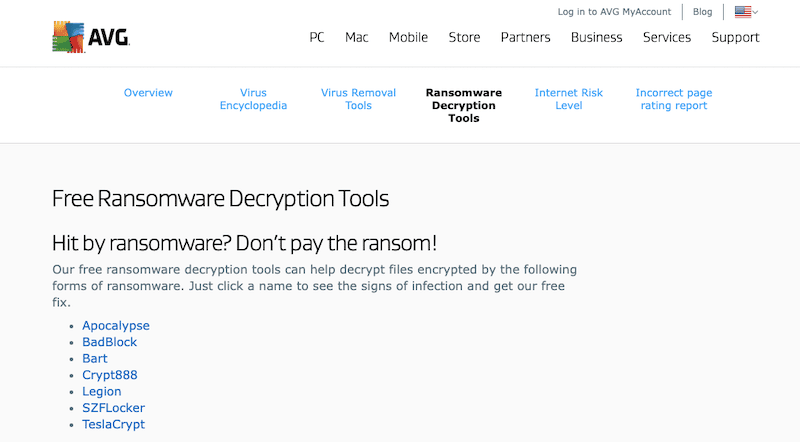
AVG (now part of Avast) is a security software developer powered by a robust cloud-based antivirus engine. AVG provides world-class antivirus, internet security, secure VPN, and protection from ransomware. They currently offer seven free ransomware file decryption tools for the following Ransomware variants, Apocalypse, BadBlock, Bart, Crypt888, Legion, SZFLocker, and TeslaCrypt.
Aside from their free AVG Ransomware decryption tools, AVG also offers commercial AVG Internet Security and AVG Internet Security Business Edition tools. These are two great tools to prevent future ransomware infections.
5. Trend Micro Ransomware File Decryptors
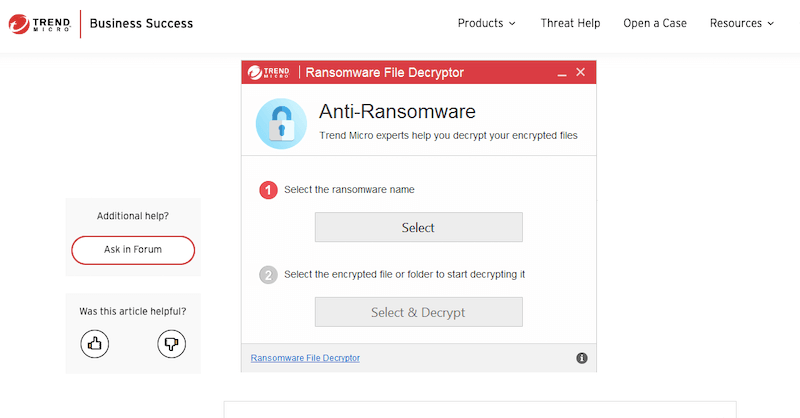
Trend Micro is a global leader in enterprise-level cloud security, XDR (Extended Detection and Response), and endpoint cybersecurity, designed for businesses of all sizes, data centers, and cloud environments. Trend Micro also offers 27 free ransomware decryption tools for dealing with 27 strong Ransomware variants.
You can use the Trend Micro Ransomware file decryptor tool to try to decrypt files encrypted by some of the popular Ransomware variants like Globe / Purge, Xorist, CryptXXX v1,v2,v3,v4,v5, Jigsaw, Globe/Purge, Crysis, and WannaCry.
6. Bitdefender Anti-ransomware
Bitdefender is a global leader in cybersecurity solutions that provide threat prevention, detection, and response. Bitdefender protects individual “home” users and businesses looking for a more robust cybersecurity solution. This cybersecurity leader also provides a couple of Ransomware prevention/detection solutions, including their free Bitdefender Ransomware Recognition (BRR) Tool and the commercial edition Gravityzone Anti-ransomware platform for businesses.
To identify which ransomware and its variants have encrypted your files, such as Darkside, WannaCry, RanHassan, LockerGoga, Fonix, and more, you can use BRR, which will point you into using any of their free ransomware file decryptors. Bitdefender is constantly growing and updating its decryption tools for variants that use weak encryption or when their master encryption keys have leaked.
7. Avast Anti-ransomware Tools
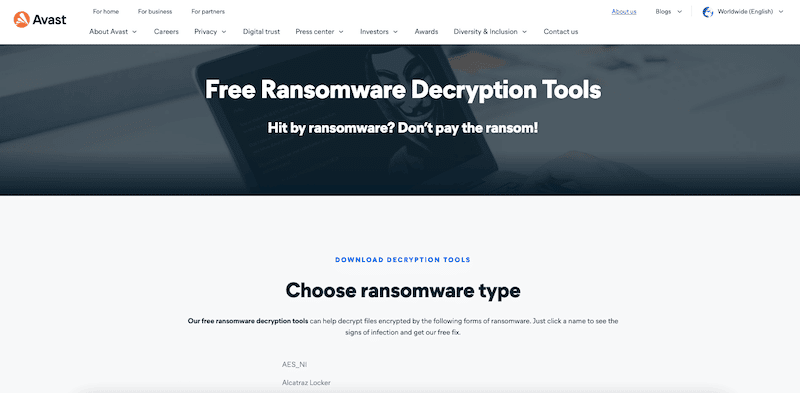
Avast is a leader in cross-platform antivirus and Internet security applications. They include freeware and paid versions of their software. Avast provides Avast One— an all-in-one protection solution including antivirus, VPN, device cleanup, and Ransomware prevention and decryption tool.
Just like the other Ransomware file decryptors, Avast One also offers 30 free decryption tools to deal with different Ransomware variants. These tools include anti-ransomware for variants like Alcatraz Locker, Babuk, Crypt888, Fonix, HermeticRansom, LambdaLocker, NoobCrypt, Prometheus, and more.
Avast One comes in two different editions, Avast One Essential (free) and Avast One (commercial). Both editions include Ransomware file decryptors.
8. Quick Heal’s Free Ransomware Decryption Tool
Quick Heal is an IT security solutions provider for threat detection and prevention, and mitigation of threats in real time. Quick Heal also offers a free ransomware file decryptor tool that will attempt to decrypt files encrypted by Ransomware variants like Troldesh, Crysis, Apocalypse, Globe1 (2 and 3), Opentoyou, Troldesh, Satan DBGer, STOP Djvu, GandCrab, and more.
The Quick Heal’s Ransomware decryption tool is quite easy to install and use. It contains a scanning function to automatically find and detect the type of encryption. When QuickHeal finds an encrypted file that it is capable of decrypting, it will save a backup copy of the encrypted file and attempt to decrypt it.
Ransomware File Decryption FAQs
Ransomware removal vs. Ransomware decryptor?
Ransomware removal tools usually include an antivirus to remove the infection that brought the ransomware to the system and also decryption tools to attempt to recover the locked files. A ransomware file decryptor, on the other hand, just decrypts files— it does not remove the malware.
Does Ransomware file decryptors delete data?
ou might have heard that this Ransomware file decryptors delete files; however, this is just a bluff initiated by Ransomware developers to convince you to pay a ransom. Ransomware file decryptors do not delete data; they just use the decryption key (password or passphrase) to try to make data readable again while also making a backup of the encrypted data.
Will a ransomware file decryptor work?
There are those Ransomware encryption variants that are breakable, those old Ransomware types still roaming around, and those that have been created with flows and weaknesses in the encryption. But keep in mind that the majority of modern Ransomware variants’ encryption is unbreakable. So ransomware file decryption will not always work.
What is the motivation of Ransomware criminals?
These criminals, “Ransomware developers,” are after money. They will sell you precisely that: a file decryption tool with a unique decryption key. You can get away and not pay a ransom by using a free ransomware file decryption tool.