We may earn a commission if you make a purchase through the links on our website.
The Best Botnet Detection Software

UPDATED: August 2, 2024
In the constantly changing landscape of cybersecurity, botnets have emerged as one of the most powerful and covert dangers. Cybercriminals can use these harmful networks of compromised machines to carry out several illegal actions, such as DDoS attacks, spam distribution, data theft, and other crimes. Organizations use botnet detection software, a crucial cybersecurity technology created to recognize and block botnet activities before they can wreak havoc on networks and systems, to tackle this sneaky threat.
Here is our list of the best botnet detection software:
- Cisco Secure Network Analytics (formerly Cisco Stealthwatch) Offers advanced threat detection using behavioral analysis, machine learning, and anomaly detection to identify botnet activities and other security threats across the network.
- SolarWinds Security Event Manager (SEM) Provides real-time monitoring and correlation of network events to detect and respond to botnet intrusions and other malicious activities effectively.
- Broadcom Endpoint Security (formerly Symantec Endpoint Protection) A comprehensive security suite that includes botnet detection and prevention capabilities, utilizing advanced heuristics and signature-based methods.
- Trellix Network Security Platform (formerly McAfee Network Security Platform) Employs advanced intrusion detection and prevention techniques to identify and block botnet traffic and other security threats in real-time.
- Trend Micro Deep Discovery Inspector Utilizes specialized network inspection to identify and mitigate botnet activities and other advanced threats on the network.
Botnet detection software is a specialized class of cybersecurity solutions designed to identify, evaluate, and mitigate botnet threats. It is often referred to as botnet monitoring software or botnet prevention tools. To spot signs of botnet infections, Command and Control (C2) communications, and other suspicious behaviors connected with botnets, these software solutions are designed to carefully examine network traffic, endpoints, and system activity. Botnet detection software gives businesses a multi-layered defense against botnet attacks by utilizing a variety of detection approaches, including signature-based identification, behavior analysis, and machine learning algorithms.
Key Considerations When Evaluating Botnet Detection Software
Organizations should carefully evaluate many significant variables as they seek to select the best botnet detection software for their cybersecurity requirements.
- Comprehensive Detection Techniques Effective botnet detection software employs a diverse range of detection techniques to maximize its ability to identify both known and emerging botnet threats. Signature-based detection is one of the fundamental methods used in botnet detection software. This technique involves comparing incoming network traffic and file signatures against a database of known botnet patterns. When a match is found, it indicates the presence of a known botnet, allowing the software to take appropriate action. While signature-based detection is reliable for identifying known botnets, it may struggle to detect new or modified botnet variants, limiting its efficacy in dealing with evolving threats. To address this limitation, botnet detection software integrates behavior analysis and machine learning algorithms. Behavior analysis monitors network activities and endpoints for deviations from typical behavior. For instance, botnets often exhibit abnormal communication patterns, excessive network connections, or suspicious data transfers, which can trigger behavior-based alerts. Machine learning algorithms play a pivotal role in adapting the software's detection capabilities over time. By continuously learning from historical data and new threats, the software can identify previously unknown botnet behaviors and adjust its detection rules accordingly. This adaptability enhances the software's ability to identify emerging botnet threats and reduces the risk of false negatives.
- Real-Time Monitoring and Analysis Real-time monitoring is a crucial aspect of botnet detection software that enables security teams to detect and respond promptly to botnet activities. The software continuously monitors network traffic, examining data packets and endpoint activities in real-time. As botnets are designed to propagate quickly and avoid, detection, timely identification is vital to prevent further infection and mitigate potential damage. With real-time monitoring, the software can promptly trigger alerts and automated responses as soon as suspicious behavior or botnet-related activities are detected. The software can analyze network traffic patterns and spot unusual network activity that can point to the presence of a botnet thanks to real-time analysis. Monitoring odd network traffic spikes, frequent connections to shady IP addresses, and unwanted communication attempts are all part of this procedure. Botnet detection software can quickly identify these behaviors and take fast action to stop or isolate infected devices, lessening the botnet's influence on the network.
- Scalability and Performance For businesses looking for a botnet detection system that can expand along with their network infrastructure, scalability is a crucial factor. The botnet detection software must be able to handle the additional strain without compromising performance as networks grow and handle higher volumes of data. As the organization's network changes, scalable solutions guarantee that the software will continue to be effective and responsive, ensuring ideal detection and reaction times. Scalability and performance are closely related, as high-performing botnet detection software should be able to process and analyze network traffic without significantly slowing down the system. This is especially important in settings where major enterprises operate since efficient operations depend on reliable and fast networks. Security teams can respond rapidly to new botnet threats because of high-performance botnet detection software's ability to quickly evaluate large amounts of data and send out real-time alarms.
The Best Botnet Detection Software
1. Cisco Secure Network Analytics (formerly Cisco Stealthwatch)
At its core, Cisco Secure Network Analytics (formerly Cisco Stealthwatch) is designed to provide real-time monitoring and analysis of network traffic, allowing security teams to gain valuable insights into network behavior and identify potential botnet activities. What sets Stealthwatch apart from other botnet detection tools is its emphasis on behavioral analysis and machine learning. Instead of solely relying on traditional signature-based methods, Stealthwatch leverages machine learning algorithms to understand and baseline normal network behavior, thus enabling it to detect anomalous activities that could indicate botnet infections.
Key Features:
- Behavioral analysis for anomalies.
- Machine learning-based detection.
- Utilizes NetFlow for monitoring.
- Proactive against emerging threats.
- Seamless security ecosystem integration.
Cisco Secure Network Analytics capacity to conduct continuous network monitoring without introducing any additional overhead is one of its primary distinguishing characteristics. This is accomplished by utilizing NetFlow, a network protocol that gathers and stores information on network traffic and is already built-in to many network devices. Cisco Secure Network Analytics can monitor network activity in real-time while maintaining network performance by employing NetFlow.
Because Cisco Secure Network Analytics places a strong emphasis on behavioral analysis, it can also spot botnet activity that conventional security solutions would overlook. Botnets frequently employ sophisticated evasion strategies to escape detection, but Cisco Secure Network Analytics can spot minute changes from the usual that can point to the presence of a botnet. Cisco Secure Network Analytics, for instance, can spot botnets trying to establish Command and Control (C2) links or moving laterally in the network.
Cisco Secure Network Analytics is also noted for its scalability, making it appropriate for both small and large businesses. The solution's capacity to process enormous amounts of network traffic data allows it to provide thorough botnet identification across intricate and dispersed networks. Secure Network Analytics, Cisco's threat detection system, continually looks for new threats and zero-day assaults rather than just identifying established botnet signatures. With time, sophisticated machine learning models get better at detecting threats as they adapt and learn from new ones. By taking a proactive strategy, enterprises may keep ahead of the growing threat posed by botnets.
Security teams can see network activities and produce useful insights thanks to Cisco Secure Network Analytics's powerful reporting and analytics features. These reports support compliance audits, general network performance monitoring, and not just the identification of botnet-related activity. Cisco Secure Network Analytics is always being updated with the most recent threat intelligence because of Cisco's dedication to continuing research and development. The solution stays current with the constantly shifting threat landscape thanks to routine software upgrades and access to Cisco Talos threat intelligence feeds, making it a trustworthy and long-term option for botnet detection.
2. SolarWinds Security Event Manager (SEM)
Due to its unified approach to threat monitoring and response, SolarWinds Security Event Manager (SEM) is a comprehensive and cutting-edge botnet detection tool that stands out in the field of cybersecurity. SEM offers a distinctive collection of characteristics that distinguish it from other botnet detection systems. It was created to meet the needs of enterprises of various sizes.
Key Features:
- Centralized log correlation and analysis.
- Real-time proactive monitoring.
- User-friendly customizable interface.
- Advanced pattern recognition algorithms.
- Scalable for diverse infrastructures.
As a security information and event management (SIEM) system at its core, SEM gathers and assesses security event data from diverse sources across the network. The capacity of SEM to centralize and correlate log data from many systems, devices, applications, and endpoints sets it apart from other botnet detection technologies. Security personnel are better able to identify patterns and potential botnet-related behavior that may be distributed throughout the network thanks to this centralized method, which gives them a comprehensive view of network activity.
SEM's real-time monitoring capabilities are its strongest suit. It constantly checks incoming log data for indications of botnet activity and other security concerns to make sure that any possible problems are found and addressed right away. Organizations can respond quickly to new botnet threats thanks to this proactive approach, averting possible harm before it worsens.
Another distinguishing trait that sets SEM different from other botnet detection tools is the product's user-friendly interface. It provides simple dashboards and adaptable reports, enabling security personnel to quickly acquire useful insights into the security posture of the network. This simplicity of use improves the overall effectiveness of efforts to detect and respond to botnets and enables security analysts to make effective decisions.
In addition, SEM makes use of sophisticated correlation and pattern recognition algorithms to spot suspicious activity linked to botnets. SEM can identify behavioral patterns suggestive of botnet infections or botnet-related communications by analyzing enormous amounts of log data and events. This degree of analysis contributes to a decrease in false positives and increases the precision of botnet identification, two key components of any effective cybersecurity approach. SEM's scalability and flexibility are further strong points. It is useful for companies of all sizes and complexity levels since it can handle large-scale networks with varying infrastructures. SEM can adjust to the specific needs and develop along with the organization's growing network, whether it's a tiny firm or an enterprise-level structure.
3. Broadcom Endpoint Security (formerly Symantec Endpoint Protection)
Broadcom Endpoint Security (formerly Symantec Endpoint Protection) combines several cutting-edge technologies to successfully counter attacks from botnets. This product's combination of modern heuristics and behavior-based analysis with established signature-based detection techniques is one of its distinctive features. Broadcom Endpoint Security is extremely effective at detecting both known botnet signatures and previously unknown botnet-related actions by integrating these several strategies.
Key Features:
- Multi-layered threat detection approach.
- Cloud-based threat intelligence integration.
- Proactive real-time monitoring.
- Defense against multi-vector attacks.
- Centralized management and reporting.
The solution's proactive approach to botnet detection is another key differentiator. It continuously monitors and analyzes endpoint activities in real-time, swiftly detecting any suspicious behaviors associated with botnets. This proactive stance enables Broadcom Endpoint Security to stop botnet infections before they can spread and cause significant harm to the network.
Integration of cloud-based threat intelligence is one of Broadcom Endpoint Security's unique characteristics. Through this interface, the software may quickly deliver updated threat definitions to endpoints and obtain the most recent information on known botnet activity. To remain ahead of emerging threats, Broadcom Endpoint Security makes use of the cloud to keep its botnet detection capabilities up-to-date and flexible.
The Broadcom Global Intelligence Network (GIN), a sizable global threat intelligence network, also plays a significant role in increasing the product's capabilities. Broadcom Endpoint Security can recognize and respond to botnet activities using this network's huge volumes of threat data that are collected and analyzed from millions of endpoints around the world.
Broadcom Endpoint Security further provides unified management and reporting options. From a single, user-friendly panel, security administrators can manage and keep an eye on the security status of endpoints and networks. This unified strategy makes it easier to maintain security policies and provides useful information about the organization's overall security situation. Symantec Endpoint Protection's capacity to fend off multi-vector attacks is another one of its primary advantages. To enter networks and spread, botnets frequently use a variety of attack routes. Beyond merely botnet detection, Broadcom Endpoint Security's provides defense against a variety of attack vectors, such as malware, ransomware, zero-day exploits, and more.
Symantec Endpoint Protection underwent a branding transition after Broadcom Inc. acquired Symantec's enterprise security business in November 2019. The product is now marketed under the name “Broadcom Endpoint Security”. This change reflects Broadcom's integration of Symantec's cybersecurity solutions into its broader portfolio, ensuring enhanced security capabilities for enterprise users. The core features and technologies of Symantec Endpoint Protection, as described above, continue to be available and supported under the new branding. For further information please click here.
4. Trellix Network Security Platform (formerly McAfee Network Security Platform)
Trellix Network Security Platform is a prominent botnet detection software that sets itself apart from others with its strong emphasis on network-based intrusion detection and prevention. Designed to protect against sophisticated cyber threats, including botnet infections, the platform offers a comprehensive set of features that make it a valuable asset in any organization's cybersecurity arsenal. The Trellix Network Security Platform makes use of both behavior-based and signature-based detection techniques. It can recognize well-known malware signatures and recognize unusual network activity linked to botnets thanks to this special blend. The software can quickly identify and stop botnet activity by analyzing network data in real time, thereby reducing the impact of possible infections.
Key Features:
- Network-based intrusion prevention.
- Blended signature and behavior-based detection.
- Extensive customization and flexibility.
- Real-time threat intelligence integration.
- High scalability for large networks.
Focusing on network-based protection is one of Trellix Network Security Platform's unique features. This platform focuses on network traffic monitoring to identify and inhibit botnet activity at the network perimeter, in contrast to certain other botnet detection solutions that largely rely on endpoint protection. Organizations benefit from an extra layer of defense from this network-centric strategy, which protects the entire network from potential botnet attacks.
Additionally, the Trellix Network Security Platform offers a high degree of customization and flexibility, making it appropriate for businesses of various sizes and industries. Security administrators can modify rules and settings to meet the particular requirements of their network environments thanks to the comprehensive policy management capabilities of this product. No matter how complicated the organization is, the platform will continue to be successful and efficient thanks to its flexibility in adapting to different infrastructures.
Integration of threat intelligence is one of Trellix Network Security Platform's other important strengths. The platform maintains current information on botnet activities and other emerging threats by utilizing threat intelligence feeds and working with McAfee's Global Threat Intelligence network. Through the sharing of real-time threat intelligence, the platform is better able to detect new botnet signs and patterns.
Additionally, the high level of scalability offered by the Trellix Network Security Platform enables it to handle massive volumes of network traffic without sacrificing speed. For businesses with large network infrastructures, this scalability is essential to maintaining the effectiveness of botnet detection and prevention as the network grows.
The Trellix Network Security Platform emerged from a significant branding transition following the merger of McAfee Enterprise and FireEye in October 2021. This merger led to the establishment of Trellix in January 2022, with a renewed focus on delivering extended detection and response (XDR) capabilities. The platform now integrates advanced threat detection technologies, combining automation, machine learning, and threat intelligence to offer robust protection against evolving cybersecurity threats.
5. Trend Micro Deep Discovery Inspector
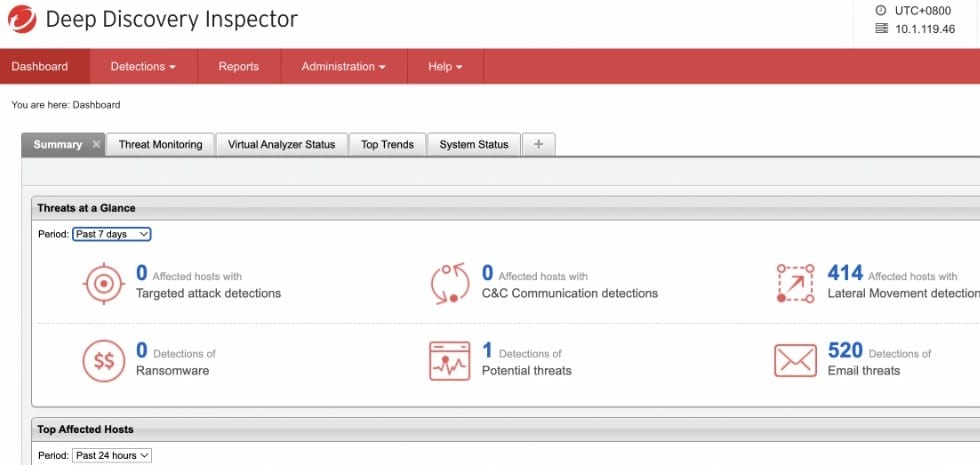
Deep Discovery Inspector thoroughly examines network traffic using deep packet inspection (DPI) and bespoke sandboxing. Using this method, the program can recognize and assess network communication behavior in real-time, giving a thorough insight into suspected botnet operations. Deep Discovery Inspector's DPI capabilities enable it to effectively discover new and unidentified botnet variants, in contrast to some other solutions that largely use signature-based techniques.
Key Features:
- Deep packet inspection for analysis.
- Adaptive machine learning capabilities.
- Real-time global threat intelligence.
- Focus on lateral movement detection.
- Seamless collaboration with other solutions.
Deep Discovery Inspector's adaptive machine-learning skills are one of its distinguishing qualities. The software continuously adapts to new threats and botnet activities using machine learning techniques. Because of its versatility, the software can keep up with new cyber threats and botnet strategies, giving enterprises a proactive line of protection against complex assaults.
Deep Discovery Inspector also uses data from Trend Micro's Smart Protection Network and specific threat intelligence feeds. This integration makes sure that the platform has access to the most recent information on the actions of botnets and attack methods in real-time. By utilizing this worldwide threat knowledge, the platform can quickly recognize and stop communications and suspicious activity associated with botnets.
Deep Discovery Inspector's emphasis on lateral movement detection within the network is another distinguishing feature. To have the most impact, botnets frequently try to spread laterally across the network. Deep Discovery Inspector can quickly and effectively contain potential botnet infections because of its thorough network inspection, which lowers the possibility of extensive damage.
Additionally, the platform's compatibility with additional Trend Micro products, like the Deep Discovery Analyzer and Trend Micro Apex One, gives businesses a comprehensive and multi-layered security strategy. Deep Discovery Inspector strengthens the organization's overall security posture and boosts botnet detection and response capabilities by exchanging threat intelligence and working with other security solutions.