We may earn a commission if you make a purchase through the links on our website.
The Best Multi-Factor Authentication Tools

UPDATED: September 10, 2024
Searching for the best multi-factor authentication tools? We put all the most popular tools to the test to find what works best for organizations of all sizes. Below are our top choices.
Here is our list of the best multi-factor authentication tools:
- ManageEngine ADSelfService Plus – EDITOR’S CHOICE This package provides a Web interface that offers a way for users to reset passwords and unlock accounts. The system also includes mechanisms for single sign-on and multi-factor. Runs on Windows Server, AWS, and Azure. Get a 30-day free trial.
- Authy Offers a range of authentication methods, including biometrics, SMS, and push notifications.
- OneLogin Authorization solutions for workforce, customer, and partner accounts from a cloud-based platform.
- Google Authenticator A free mobile app that provides multi-factor authentication for third-party systems.
- Okta Provides user account management for workforce and customers with integrated SSO and MFA.
- LastPass A cloud-based password vault system that provides credentials synching across devices.
- Auth0 This package provides a single sign-on system and application-level protection for cloud-based applications.
- Microsoft Entra ID Offers multifactor authentication with a range of verification methods to secure account access. This is the new name for Azure AD.
Methods of Multi-Factor Authentication
- SMS or Email Codes SMS or email codes send a one-time code to your mobile phone or email. When logging in, you enter this code along with your password. These codes are typically short-lived, expiring after a few minutes. This method relies on your mobile carrier or email provider's security.
- Authenticator Apps Authenticator apps, like Google Authenticator or Authy, generate time-based one-time passwords (TOTP). These codes refresh every 30 seconds and are synced with your account. You scan a QR code during setup to link the app to your account. This method works even without an internet connection.
- Biometric Authentication Biometric authentication uses unique physical traits, such as fingerprints, facial recognition, or retina scans. Your biometric data is scanned and matched against the stored template. This method is highly secure because biometric traits are unique and hard to replicate. Devices with built-in biometric scanners, like smartphones and laptops, commonly use this method.
- Security Keys Security keys are physical devices that connect via USB, NFC, or Bluetooth. They use cryptographic protocols to verify your identity. You plug in or tap the key when prompted during login. YubiKey and Titan Security Key are popular examples of this method.
- Push Notifications Push notifications are sent to your registered mobile device when you attempt to log in. You simply approve or deny the login attempt through the notification. This method is quick and convenient, requiring just a tap on your phone. Duo Mobile and Microsoft Authenticator offer this feature.
- Hardware Tokens Hardware tokens generate one-time codes displayed on a small device screen. You enter the code along with your password to log in. These tokens are usually standalone and don't require an internet connection. RSA SecurID is a well-known example of a hardware token.
- Smart Cards Smart cards store authentication data on an embedded microchip. You insert the card into a reader and enter a PIN to authenticate. This method is commonly used in corporate and government environments. Smart cards can also store certificates for digital signatures.
- Software Tokens Software tokens are digital versions of hardware tokens, often integrated into devices or applications. They generate time-based or event-based codes for authentication. You install the token software on your device and use it similarly to a hardware token. This method provides flexibility and ease of use.
The Best Multi-Factor Authentication Tools
How to Pick the Best MFA Tool For You
- Assess Data Sensitivity Identify the type of data you are protecting to determine the appropriate MFA strength. For critical data, such as financial records or sensitive personal information, opt for hardware-based MFA options like security keys or biometric authentication. These methods provide higher security levels due to their reliance on physical devices or unique biological traits. For less critical data, software tokens or authenticator apps might suffice, offering a balance of security and usability.
- Evaluate Ease of Use Examine how the MFA tool integrates into your existing workflows. Authenticator apps and push notifications are user-friendly, providing quick authentication with minimal disruption. Biometric methods, though requiring specific hardware, offer seamless and rapid access once set up. Consider the technical proficiency of the users and the frequency of authentication required to ensure the chosen method does not hinder productivity.
- Check Compatibility Verify that the MFA tool is compatible with your current systems and applications. Ensure it supports all operating systems in use, such as Windows, macOS, iOS, and Android. Check for integration capabilities with your enterprise software, email clients, VPNs, and other critical services. Compatibility issues can lead to implementation delays and additional costs, so thorough testing in your environment is crucial.
- Analyze Costs Calculate the total cost of ownership for each MFA tool. SMS-based authentication might incur per-message charges, while authenticator apps generally have no ongoing costs. Hardware tokens and biometric systems involve initial investments in devices and potential maintenance expenses. Factor in the cost of deployment, user training, and any necessary infrastructure upgrades to make an informed financial decision.
- Review Security Features Investigate the security features and reputation of each MFA tool. Look for tools with robust encryption standards, such as AES-256, and multi-layered authentication protocols. Examine the tool's history for any security breaches or vulnerabilities. Choose tools that have undergone rigorous testing and certification by independent security organizations. Reading detailed user reviews and expert analyses can provide insights into the tool’s reliability and effectiveness in real-world scenarios.
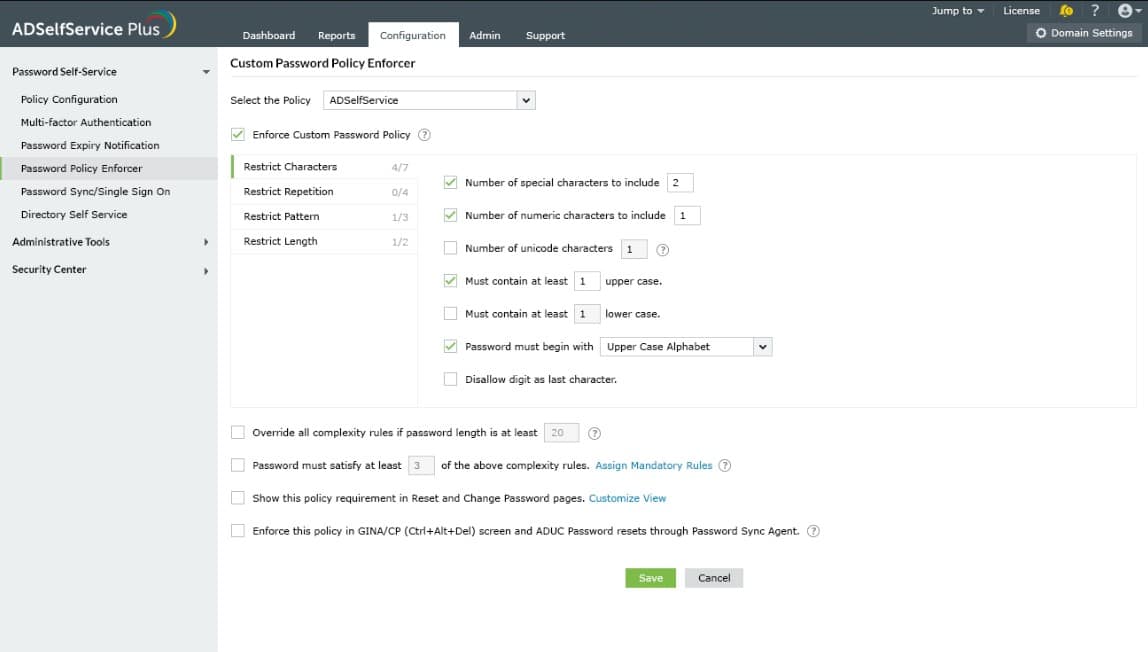
1. ManageEngine ADSelfService Plus – FREE TRIAL
ManageEngine ADSelfService Plus stands out for its comprehensive multi-factor authentication options and ease of integration with various applications. Its user-friendly interface simplifies the setup and management of authentication policies, making it accessible for both administrators and users.
Key Features:
- Multi-Factor Authentication (MFA): Ensures secure access through various authentication methods like biometrics, OTPs, and push notifications.
- Customizable Authentication Policies: Allows tailoring of MFA policies to fit different user roles and requirements.
- Integration with Various Applications: Seamlessly integrates with popular applications and platforms to extend MFA protection.
- Self-Service Password Reset: Empowers users to reset their passwords securely using MFA, reducing helpdesk calls.
- Adaptive Authentication: Adjusts the level of authentication based on risk assessment, ensuring enhanced security without compromising user experience.
The tool’s ability to significantly reduce helpdesk calls through self-service password resets enhances its value in any organization. Its adaptive authentication feature also ensures a balance between security and user experience, making it an excellent choice for organizations seeking robust security solutions.
Pros:
- Enhanced Security: Multiple authentication factors significantly increase account protection against unauthorized access.
- User-Friendly Setup: Easy to configure and manage MFA settings, making it accessible for administrators and users alike.
- Wide Integration: Supports integration with numerous applications, enhancing overall security infrastructure.
- Reduced Helpdesk Load: Self-service password reset feature decreases the number of helpdesk tickets, saving time and resources.
- Customizable Policies: Allows the creation of specific MFA policies to meet diverse security needs across different user groups.
Cons:
- Complexity for Non-Tech Users: Users unfamiliar with advanced security measures might find the MFA setup process challenging.
Get Started with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADSelfService Plus is our top choice for multi-factor authentication due to its robust security features and user-friendly setup. It offers multiple authentication methods, including biometrics and OTPs, ensuring comprehensive protection against unauthorized access. The customizable authentication policies and seamless integration with various applications make it a versatile solution for different organizational needs. Additionally, the self-service password reset feature not only enhances security but also significantly reduces helpdesk workload. Overall, its combination of security, ease of use, and integration capabilities sets it apart as a leading option in multi-factor authentication.
Download: Start a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/self-service-password/sem/active-directory-multi-factor-authentication.html
OS: Windows, Linux, Cloud-based
2. Authy
Authy offers a wide range of authentication methods, including biometrics, SMS, and push notifications, ensuring robust protection for users. Its seamless integration with various platforms and applications makes it a versatile choice for businesses of all sizes.
Key Features:
- Versatile Authentication Methods: Supports various methods like biometrics, SMS, and push notifications for enhanced security.
- Customizable Policies: Allows tailoring of authentication policies to meet specific organizational needs.
- Seamless Integration: Easily integrates with multiple platforms and applications for consistent security across the board.
- User-Friendly Dashboard: Simplifies the management of authentication policies and provides detailed analytics.
- Adaptive MFA: Adjusts security measures based on user behavior and risk levels for optimal protection.
The user-friendly dashboard and detailed analytics provide administrators with valuable insights and easy management of authentication policies. Overall, Auth0’s flexibility, security, and ease of use make it a tried and true solution for multi-factor authentication.
Pros:
- Flexible Authentication: Offers a wide range of methods, ensuring robust security and user convenience.
- Easy Integration: Seamlessly integrates with numerous platforms, making it versatile for different applications.
- User-Friendly Interface: The intuitive dashboard simplifies policy management and provides valuable insights.
- Scalable Solution: Easily adapts to the needs of growing businesses, offering scalability without compromising security.
- Adaptive Security: Enhances protection by adjusting authentication measures based on user behavior and risk assessment.
Cons:
- Dependency on Internet: Relies on a stable internet connection for seamless authentication, which can be a limitation in some environments.
- Learning Curve: Administrators may face a learning curve when customizing and managing advanced features.
3. OneLogin

OneLogin provides a range of authentication methods, including biometrics, OTPs, and smart cards, providing comprehensive protection. The platform integrates smoothly with various applications and services, making it highly versatile.
Key Features:
- Versatile Authentication Methods: Supports biometrics, OTPs, smart cards, and more for comprehensive security.
- Seamless Integration: Easily integrates with numerous applications and services, providing consistent protection.
- User-Friendly Interface: Simplifies the management of authentication policies with an intuitive interface.
- Detailed Reporting: Offers in-depth analytics and reporting tools for better security management.
- Adaptive Authentication: Adjusts security measures based on user behavior and risk assessment.
Its user-friendly interface and detailed reporting tools enhance the overall management of authentication policies. Overall, OneLogin's robust security, ease of use, and integration capabilities make it an excellent solution for multi-factor authentication.
Pros:
- Comprehensive Security: Provides a wide range of authentication methods, ensuring robust protection.
- Easy Integration: Integrates smoothly with various applications and services, enhancing overall security infrastructure.
- User-Friendly Management: The intuitive interface makes it easy for administrators to manage and monitor authentication policies.
- Advanced Reporting: Detailed analytics and reporting tools aid in monitoring and improving security measures.
- Adaptive Measures: Adjusts authentication based on risk levels, balancing security and user convenience.
Cons:
- Complex Initial Setup: Setting up and configuring the system can be challenging, particularly for larger organizations.
- Cost Considerations: The pricing may be high for smaller businesses or those with limited budgets.
- Learning Curve: Administrators may face a learning curve when navigating advanced features and customization options.
4. Google Authenticator
Google Authenticator provides time-based one-time passwords (TOTPs), adding an extra layer of security to user accounts without requiring an internet connection. Its straightforward setup and compatibility with a wide range of services make it accessible for both individuals and businesses. Despite its simplicity, Google Authenticator offers robust security features, ensuring that sensitive data remains protected. Its combination of simplicity, reliability, and security makes it an excellent choice for multi-factor authentication.
Key Features:
- Time-Based One-Time Passwords (TOTPs): Generates secure one-time passwords that change every 30 seconds.
- Offline Functionality: Operates without the need for an internet connection, ensuring access at all times.
- Wide Compatibility: Works with a multitude of services and applications for versatile use.
- Simple Setup: Easy to install and configure, making it accessible for all users.
- Secure Authentication: Enhances account security with an additional layer of protection.
Pros:
- User-Friendly: The straightforward interface makes it easy for users to set up and manage multi-factor authentication.
- Reliable Security: Provides robust security with time-based one-time passwords that change frequently.
- Offline Access: Functions without an internet connection, ensuring authentication is always available.
- Wide Compatibility: Supports numerous services and applications, offering flexibility for users.
- No Cost: The app is free to use, making it an economical choice for secure authentication.
Cons:
- Lacks Advanced Features: Does not offer advanced features like push notifications or biometric authentication.
- Single Device Limitation: Only works on the device it is installed on, limiting flexibility for multi-device users.
- Manual Setup Required: Each service must be manually added, which can be time-consuming for users with many accounts.
- Limited Support: There is minimal support available for troubleshooting or user assistance.
5. Okta
Okta offers a wide array of authentication methods, including biometrics, push notifications, and hardware tokens, ensuring a robust security framework. The intuitive user interface and detailed analytics make it easy for administrators to manage and monitor authentication policies.
Key Features:
- Diverse Authentication Methods: Offers biometrics, push notifications, hardware tokens, and more for robust security.
- Seamless Integration: Easily integrates with various applications and services, enhancing overall security infrastructure.
- Intuitive User Interface: Simplifies the management and monitoring of authentication policies with a user-friendly interface.
- Detailed Analytics: Provides in-depth analytics and reporting for better security oversight.
- Adaptive Authentication: Adjusts security measures based on user behavior and risk levels to enhance protection.
Its ability to integrate effortlessly with various applications and services further enhances its appeal. Overall, Okta’s extensive features, ease of use, and integration flexibility make it an exceptional solution for multi-factor authentication.
Pros:
- Comprehensive Security: Offers a wide range of authentication methods, ensuring robust and flexible security.
- Easy Integration: Seamlessly integrates with numerous applications and services, providing a consistent security framework.
- User-Friendly: The intuitive interface makes it easy for administrators to manage and monitor authentication policies.
- Advanced Analytics: Detailed analytics and reporting help in monitoring and enhancing security measures.
- Adaptive Measures: Adjusts authentication based on risk assessment, balancing security and user experience.
Cons:
- Complex Setup: Initial setup and configuration can be complex, particularly for large organizations.
- High Cost: Pricing can be a concern for smaller businesses or those on a tight budget.
- Dependency on Internet: Requires a stable internet connection for seamless operation, which can be a limitation in some environments.
6. LastPass

LastPass offers a variety of authentication methods, including biometrics, OTPs, and push notifications, ensuring that user accounts are well-protected. The platform integrates effortlessly with a wide range of applications and services, making it a versatile solution for businesses of all sizes.
Key Features:
- Multiple Authentication Methods: Offers biometrics, OTPs, and push notifications for robust security.
- Seamless Integration: Integrates easily with a wide range of applications and services.
- User-Friendly Interface: Provides an intuitive interface for easy management of authentication policies.
- Comprehensive Reporting: Offers detailed reporting tools for better security management.
- Adaptive Authentication: Adjusts security measures based on user behavior and risk assessment.
Its intuitive interface and comprehensive reporting tools make it easy for administrators to manage and monitor authentication policies. LastPass's combination of robust security, user-friendliness, and integration capabilities make it an outstanding choice for multi-factor authentication.
Pros:
- Strong Security: Offers a variety of authentication methods, ensuring robust account protection.
- Easy Integration: Integrates seamlessly with numerous applications and services, enhancing overall security.
- User-Friendly: The intuitive interface simplifies the management and monitoring of authentication policies.
- Detailed Reporting: Provides comprehensive reporting tools to help monitor and improve security measures.
- Adaptive Measures: Adjusts authentication based on risk levels, balancing security and user convenience.
Cons:
- Initial Setup Complexity: The initial setup and configuration can be complex, especially for larger organizations.
- Cost Concerns: Pricing may be high for smaller businesses or those with limited budgets.
- Internet Dependence: Requires a reliable internet connection for seamless operation, which can be a limitation in some environments.
7. Auth0
Auth0 supports a wide range of authentication methods, including biometrics, SMS, and push notifications, ensuring comprehensive user protection. The platform’s seamless integration with numerous applications and services makes it highly versatile for various business needs. Its intuitive interface and detailed analytics enable administrators to manage and monitor authentication policies effectively. Auth0’s robust security, ease of use, and integration capabilities make it an excellent solution for multi-factor authentication.
Key Features:
- Versatile Authentication Methods: Supports biometrics, SMS, push notifications, and more for enhanced security.
- Customizable Policies: Allows tailoring of authentication policies to meet specific organizational needs.
- Seamless Integration: Easily integrates with multiple platforms and applications for consistent security across the board.
- User-Friendly Dashboard: Simplifies the management of authentication policies and provides detailed analytics.
- Adaptive MFA: Adjusts security measures based on user behavior and risk levels for optimal protection.
Pros:
- Comprehensive Security: Provides robust protection with a variety of authentication methods, including biometrics and hardware tokens.
- Developer-Friendly: Extensive documentation and SDKs make it easy for developers to integrate and customize the solution.
- Scalable Infrastructure: Designed to support growing businesses with its scalable architecture, accommodating increasing user bases effortlessly.
- Global Reach: Supports multiple languages and complies with various international security standards, making it suitable for global organizations.
- Customizable Login Experience: Allows businesses to customize the login interface to align with their brand identity.
Cons:
- Complex Initial Setup: The initial setup and configuration process can be complex and time-consuming for organizations with limited technical expertise.
- Pricing Model: The tiered pricing model can become expensive as additional features and users are added, which might be a concern for smaller businesses.
- Occasional Downtime: Some users have reported occasional downtime and service interruptions, which can impact critical authentication processes
8. Microsoft Entra ID
Microsoft Entra ID is our top choice for multi-factor authentication due to its advanced security features and seamless integration with a wide range of applications. This solution supports numerous authentication methods, including biometrics, SMS, push notifications, and hardware tokens, providing comprehensive user protection.
Key Features:
- Diverse Authentication Methods: Supports biometrics, SMS, push notifications, hardware tokens, and more for enhanced security.
- Adaptive Security Policies: Adjusts security measures based on user behavior and risk levels, providing optimal protection.
- Seamless Integration: Integrates effortlessly with Microsoft 365, Azure, and various third-party applications for consistent security.
- User-Friendly Dashboard: Simplifies the management of authentication policies and provides detailed analytics.
- Unified Identity Management: Manages identities and access to applications in a central location, improving visibility and control.
Its intuitive interface and detailed analytics enable efficient management and monitoring of authentication policies. Furthermore, its robust adaptive access policies and seamless user experience make it a highly effective solution for businesses of all sizes. Overall, Microsoft Entra ID’s combination of security, flexibility, and ease of use makes it an outstanding choice for multi-factor authentication.
Pros:
- Comprehensive Security: Provides robust protection through various authentication methods, including advanced options like FIDO2 security keys and biometric verification.
- Seamless Integration: Integrates smoothly with a wide range of Microsoft and third-party applications, enhancing overall security infrastructure.
- Adaptive Access: Implements risk-based adaptive access policies that adjust security measures dynamically based on user behavior.
- User-Friendly Experience: Offers an easy sign-in experience across multiple environments, reducing the burden of password management and increasing productivity.
- Centralized Management: Centralizes the management of identities and access, improving visibility and control over user activities.
Cons:
- Pricing Model: The tiered pricing can become expensive as more features and users are added, which may be a concern for smaller businesses.
- Learning Curve: Administrators may experience a learning curve when navigating the platform’s extensive features and customizations.
- Occasional Downtime: Some users have reported occasional downtime and service interruptions, which can impact critical authentication processes