We may earn a commission if you make a purchase through the links on our website.
Varonis Alternatives & Competitors for File & Permissions Analysis
UPDATED: March 22, 2024
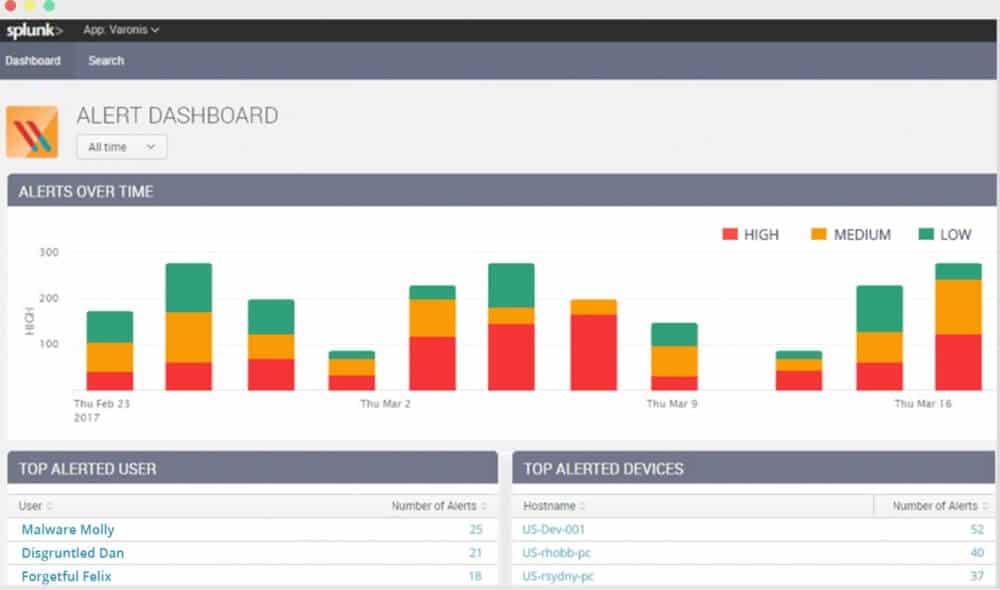
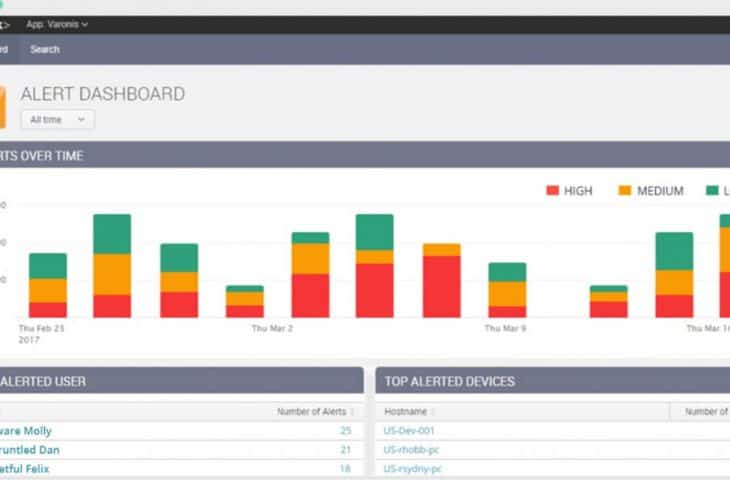
Varonis is a data security platform designed to protect your data from inside threats and prevent it from breaches. It will identify and inspect unusual behavior, privilege escalations, and unauthorized access to Active Directory, file servers and email systems. When Varonis finds vulnerabilities, such as inconsistent permissions or global access to sensitive files, it fixes them automatically. This software can also help you prepare for compliance audits.
Varonis looks at the state of a file, finds signs of compromise, and identifies suspicious behavior. It achieves this by using machine learning and user behavior analytics.
Their product suite, includes Datadvantage for data audit and protection and Datalert for User Behavior Analytics.
Key and interesting Features?
- Actionable Alerts with Who, What, Where, and When Detailed in the dashboard. Varonis is able to send alerts to your email.
- Full audit trail and powerful sorting and filtering capabilities. With Varonis it is easy to investigate where an attacker modified data, changed permissions, read emails or marked messages as unread.
- Determine data ownership: Veronis is able to determine who is the owner of the data based on access frequency.
Pricing Information.
Public pricing is unavailable for Varonis. But they have a 30-day unlimited free trial and a continual user license model. For more information, you can get a Price Quote from Varonis official site.
According to CyberSecurity Pricing, the license for DatAdvantage starts at $17,000 DatAdvantage with IDU Classification Framework for 100 Users for about $8,000.
Here's the Top Varonis Alternatives
1. ManageEngine ADAudit Plus – FREE TRIAL
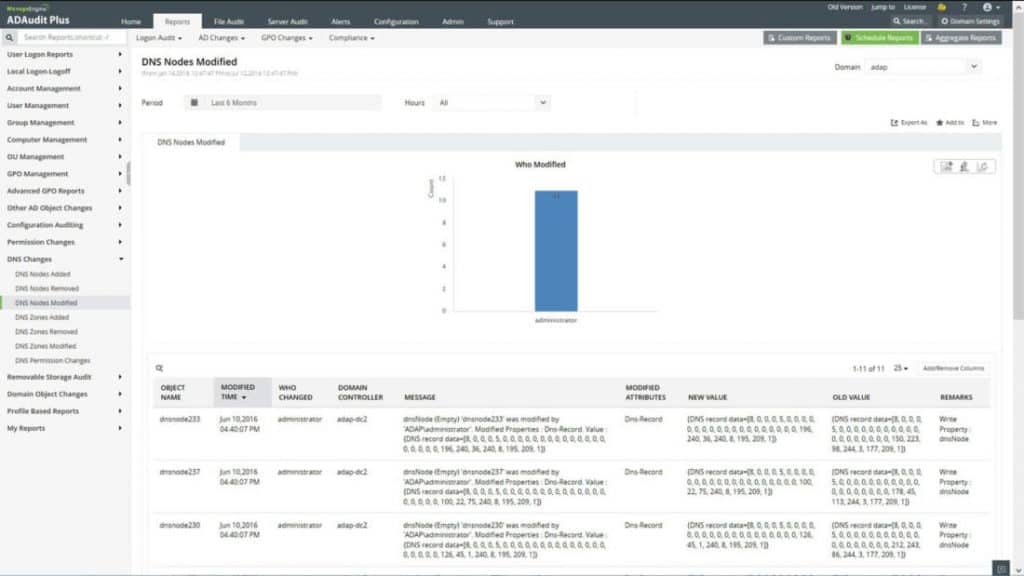
ADAudit Plus is a real-time, web-based Active Directory “AD” change auditing software from ManageEngine. It provides complete reports on almost all changes that occur in your Windows AD. The who, when, and where questions, from ADAudit Plus help identify any normal or abnormal activity and get complete knowledge of what is happening in the AD.
The software helps a manager to gain knowledge through their rich reports. ADAudit Plus comes with over pre-configured reports to make the process faster. It also comes with 24/7 monitoring capabilities and email alerting.
Some Key Features and Capabilities include:
- Real-time Windows Active Directory Auditing.
- Auditing of Windows Log-on and log-off.
- File Servers Auditing.
- Auditing of Windows Servers:
- Compliance Audit Reports.
Just like Varonis, ADAudit Plus, can collect metadata from the Active Directory and File Systems to monitor them. Both solutions can find, how, when, and where users were authenticated to AD.
Pros:
- Focused heavily on compliance requirements, making it a good option for maintaining industry compliance
- Preconfigured compliance reports allow you to see where you stand in just a few clicks
- Features insider threat detection – can detect snooping staff members or blatant malicious actors who have infiltrated the LAN
- Supports automation and scripting
- Great user interface
Cons:
- Upgrading can often break features and cause issues
- Custom reporting has a steep learning curve
The price is not published on ManageEngine official site, but you can request a price quote. Get a fully functional 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top pick for a Varonis alternative because this system provides user behavior analytics to implement insider threat and account takeover detection, just like Varonis. This system has extensive Active Directory protection systems. It records any change made to records in Active Directory, logging the administrator account involved and the previous record values. That makes the change reversible. The tool will also alert for each change, making it possible to spot a compromised administrator account. The system operates protection for any resource that uses Active Directory as an access rights management service; it also applies to Azure AD. The service examines all login attempts, looking for stolen credentials that might be used outside of the company. It also highlights multiple failed login attempts, which occur in password cracking attempts.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/active-directory-audit/download.html
OS: Windows Server, AWS, and Azure
2. SolarWinds Access Right Manager – FREE TRIAL
Access Right Manager “ARM” from SolarWinds (formerly known as 8Man) is a solution that allows you to manage and audit user rights of your IT environment. ARM optimizes all the security processes within your company. It helps answer the following questions, who has access? what they have access to? and, who should have access to what?
With this information, Access Right Manager can classify users and prevent unauthorized ones from accessing sensitive data. The software is based on the following principles:
- User Permission Analysis.
- Documentation and Reporting.
- Security Monitoring.
- Role and Process Optimization.
- User Provisioning and management.
Aside from the basic functionalities, ARM can monitor Active Directory, audit Windows File Share, monitor Microsoft Exchange, and monitor SharePoint access.
Features for file and permissions analysis?
- ARM Allows User Permission Analysis:
Check user access to file servers and services. Extend your visibility into privileged accounts and memberships. - Create, activate, Deactivate, Modify, or Delete User Access To Files and Services.
With ARM you can set up and manage user accounts and provide access to files servers.
Pros:
- Provides a clear look into permission and file structures through automatic mapping and visualizations
- Preconfigured reports make it easy to demonstrate compliance
- Any compliance issues are outlined after the scan and paired with remediation actions
- Sysadmins can customize access rights and control in Windows and other applications
Cons:
- SolarWinds Access Rights Manager is an in-depth platform designed for sysadmin which may take time to fully learn
Download a 30-day Free Trial to Test the Software in your Network, Download Below to Get Started!!
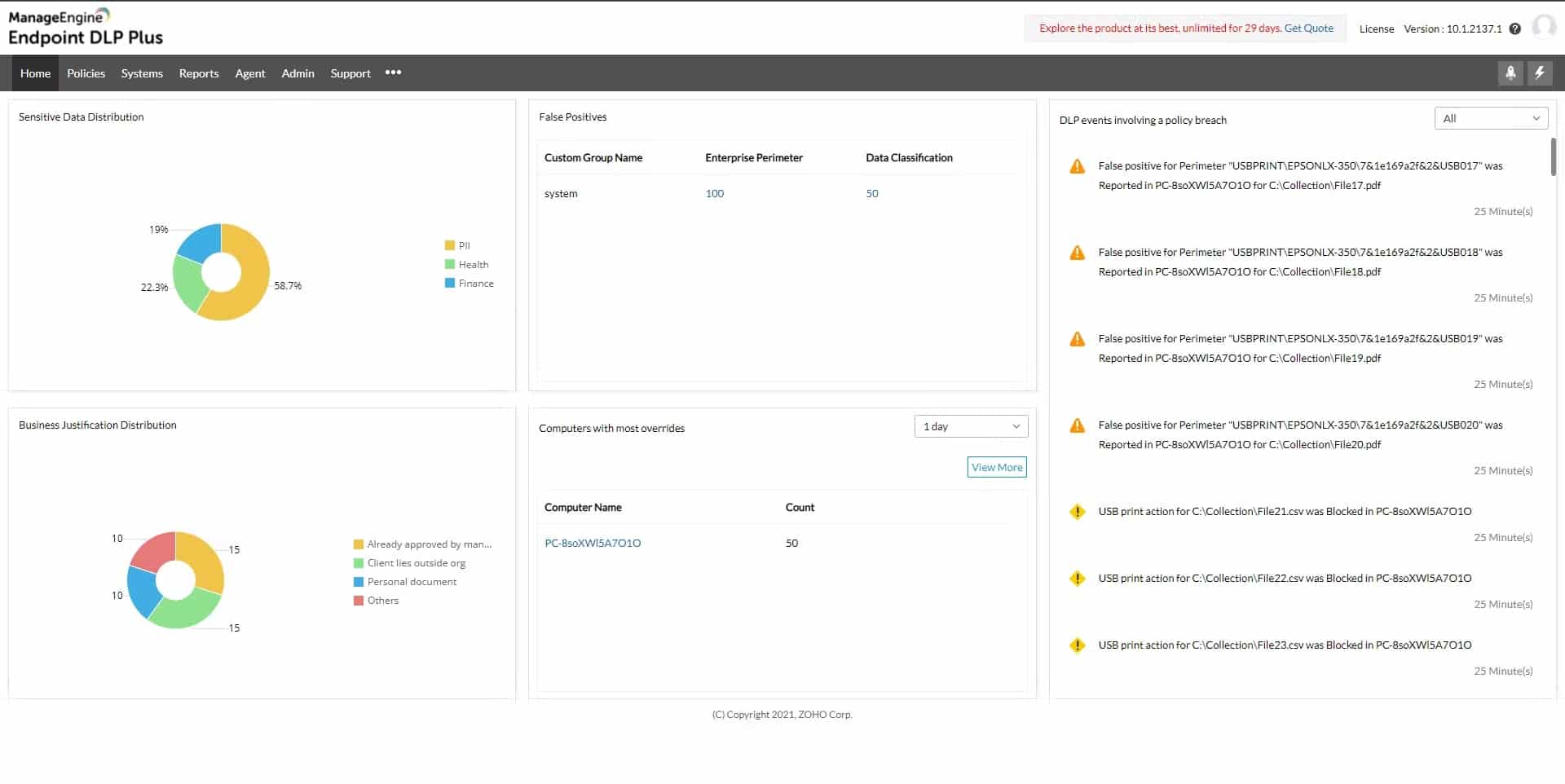
3. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP Plus is an enterprise-focused tool that protects data across various mediums and network environments.
Key Features
- Monitors network traffic for the transmission of sensitive data, and sends alerts when unauthorized data transmission is detected
- Scans the network and devices for sensitive data, such as credit card numbers or personally identifiable information, and provides detailed reports on the results
- Encrypts sensitive data to prevent unauthorized access or transmission, and provides secure channels for authorized users to access the data
ManageEngine Endpoint DLP Plus (Data Loss Prevention) is a security tool that helps organizations prevent the unauthorized transmission of sensitive data from their network. It includes features such as content-aware monitoring, data discovery, and data encryption to protect sensitive information from being accessed or transmitted without permission. Endpoint DLP Plus can be used to prevent the unauthorized sharing of sensitive information through email, instant messaging, cloud storage, and other channels. It can also help organizations comply with industry regulations and standards related to data security. Overall, Endpoint DLP Plus can help organizations to protect their sensitive data and prevent data breaches.
Pros:
- Flexible deployment options across multiple platforms
- It can be installed on both Windows and Linux platforms, making it more flexible than other on-premise options
- Offers in-depth reporting, ideal for enterprise management or MSPs
- Integrated into more applications than most patch management solutions
Cons:
- ManageEngine is a feature-rich platform that takes time to explore and learn fully
Get a fully functional 30-day free trial.
4. Netwrix Auditor
This software is a good alternative to Varonis, but it does not offer as much features and functionality as Varonis. Netwrix Auditor is a platform that provides visibility for user behavior analysis and risk mitigation. It helps protect sensitive data by allowing control over access, configuration, and changes, in the cloud, on-premises, or in hybrid IT environments.
Netwrix visibility platform provides amazing security by identifying vulnerabilities, detecting unusual user behavior and going deep into threat patterns.
What Netwrix does for File and Permissions analysis?
- Netwrix can find high-risk configurations, such as universal access permissions for sensitive files. When there are excessive permissions to everyone in group or many directly assigned permissions.
- The software displays all effective user permissions in File Servers and Active Directory. With a complete picture of this data you can block overexposed data and give access to only the necessary users.
- Improve security in sensitive data shares. Find file share points and folders that have sensitive information and make sure only authorized users have access to it.
Pros:
- Offers detailed auditing and reporting that helps maintain chain of custody for sensitive files
- Offers hardware and device monitoring to track device health alongside security
- Allows sysadmin to implement automated remediation via scripts
- Integrates with popular help desk platforms for automatic ticket creation
Cons:
- The trial could be a bit longer for testing
The price of license is not public on their site. Request pricing and licensing information from Netwrix official site. Get a free 20-day trial from Netwrix official site.
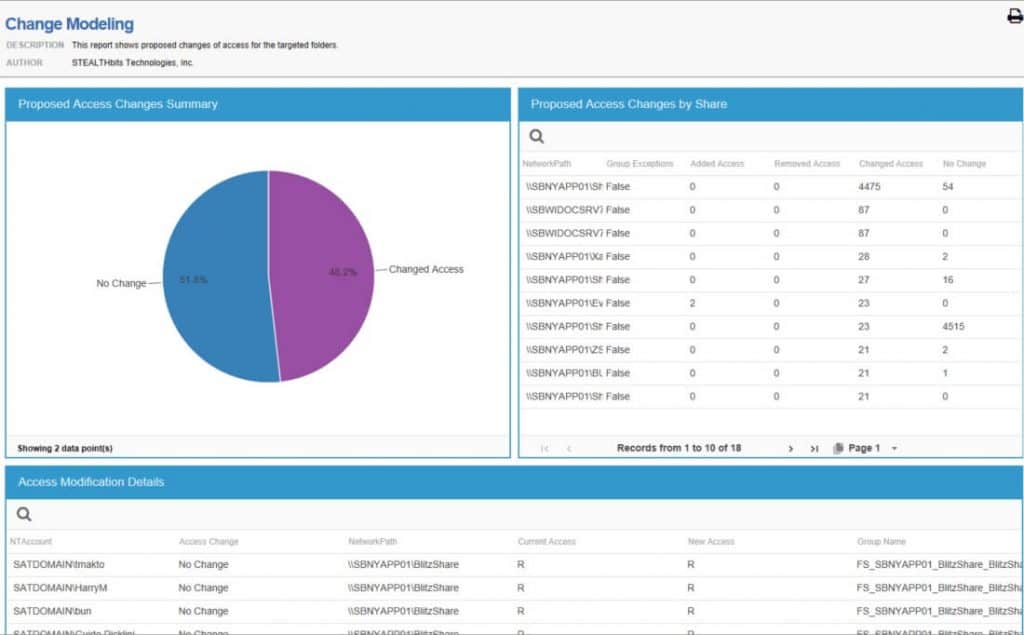
5. STEALTHbits
STEALTHbits is another alternative to Varonis. They are very similar in functionality and both are considered Data Access Governance software. This software is focused on protecting credentials and sensitive data. It accomplishes this by deleting unnecessary access, enforcing security policies, and identifying complex threats.
Some key features of STEALTHbits:
- Sensitive Data Discovery
- Access & Permissions Auditing
- Activity Monitoring
- Threat Analytics
- Sensitive Data Reviews
Just like Varonis, STEALTHbits is capable of automating endless manual tasks that take employees valuable time. It also works with the help of an agent and does not depend on auditing from Windows file-system.
Some Features for File and Permissions analysis?
- The Sensitive Data Review:
This powerful feature allows owners to mark “hits” as false-positives. It also analyzes the files that have sensitive information and decides whether they need remediation. - The File System Activity Threats:
A threat model that includes, Ransomware, Sensitive Data Activity, State File Activity, User Share Activity, Peer Group Activity, and Modified Binaries. With these reports, the users can be alerted whether there is abnormal behavior. They also indicate advanced and inside threats to the data in the file system.
Pros:
- Simple lightweight dashboard and reporting
- Ideal for small to medium-sized companies
- Uses simple reporting to help sysadmins control access easier
Cons:
- Must contact sales for pricing
The price is not published on their site. Request a free trial, and their sales team will get in contact with you within 24 hours. Request a free trial from STEALTHbits official site.
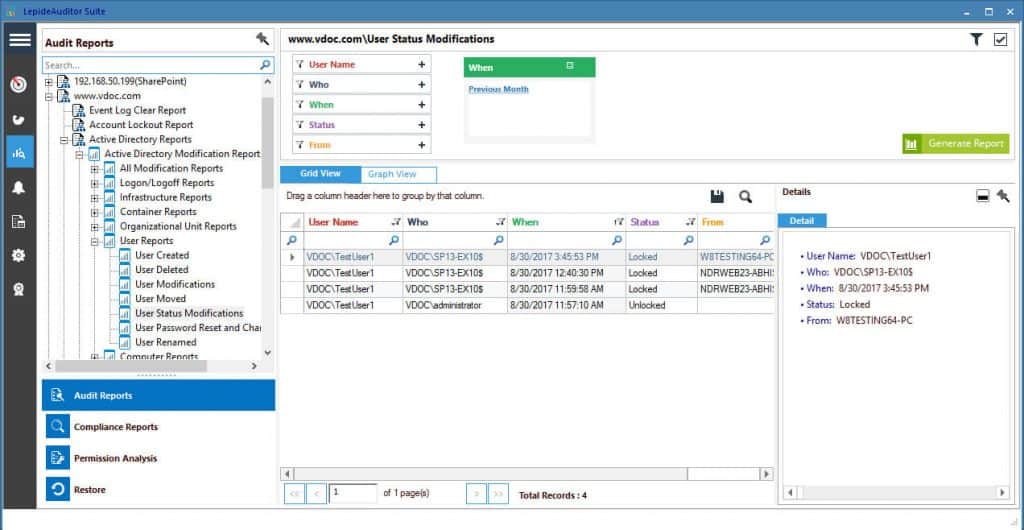
6. Lepide Auditor
Lepide Auditor is a security data-centric audit and protection solution aimed for the enterprise level. The software provides insight of the data and systems, whether they are located on the cloud, on premises or in hybrid environments.
The main function of Lepide Auditor is to change auditing. With this centralized platform, administrators can audit 5 different systems, Active Directory, Exchange Server, SharePoint, SQL Server and Group Policy Objects. LepideAuditor is also really helpful to enforce and meet security compliances, like PCI, FISMA, HIPAA, and GLBA.
Lepide Auditor Features:
- Real Time log collection:
LepideAuditor is able to perform real-time change configuration auditing.
- In-depth Reporting:
The solution comes with over 270 predefined Audit Reports.
- Object Backup and Restoration:
The tool can take Backup Snapshots and Restore the state of Active Directory and Group Policy objects. - Server Health Check:
Monitor the health of Active Directory, Exchange Server, and SQL Server.
Pros:
- A simple way to see last login, name and CN path of multiple accounts at once
- Can quickly create CSVs or HTML format reports
- A simple wizard makes it easy to set custom threshold-based alerts
Cons:
- Similar tools allow for more functionality like bulk password changes and unlocks
The price is not published in Lapide Auditor’s official site. Register, download a free trial, and you will get a price quote after 15 days. LepideAuditor offers a 15-day free trial. Download it at their official site.
Summary
A company’s most sensitive information is not always safe. It is continuously spreading out, growing, and getting harder to protect.
We are most vulnerable to attacks to our data from inside our networks. Using multiple tools and difficult-to-integrate solutions leaves you more vulnerable to data breaches.
But how do we protect our data?
A file and permissions analysis tool is the right platform to avoid inside threats. They are meant to protect your data, information, and knowledge within the network. A data security solution, that can audit and report credentials, permissions and other valuable information in the network is critical.
Software like Varonis, SolarWinds ARM, NetWrix, STEALTHbits, LepideAuditor, and ADAudit Plus can analyse how users work with the data, they can determine roles of the user, and fix unnecessary permissions.