We may earn a commission if you make a purchase through the links on our website.
Threat Intelligence Platforms – Here are the Best TIPS for Managing Security in Your Networks!

UPDATED: April 11, 2024
A Threat Intelligence Platform (TIP) converts collected threat data into actionable intelligence. It empowers a team to defend their network proactively.
“It is only the enlightened ruler and the wise general who will use the highest intelligence of the army for the purposes of spying, and thereby they achieve great results.” – Sun Tzu from the Art of War.
Cyber-attacks are becoming too sophisticated and highly targeted that it can be quite overwhelming for one or two security analysts keeping up the defenses of a network. But understanding adversaries is easier said than done. First, not all companies can hire security analysis talent, and if they do, no analyst can win a war without proper threat intelligence.
Here is our list of the best threat intelligence platforms:
- EventLog Analyzer ManageEngine – FREE TRIAL This is an on-premises package that operates as a log manager as well as a security package, threat intelligence is delivered by ManageEngine to improve threat hunting. Runs on Windows Server and Linux. Start a 30-day free trial.
- CrowdStrike Falcon X This threat intelligence system is offered in three plan levels that add on reporting and expert analysts to the basic feed. This is a cloud platform.
- Anomali Threat Platform This service is a cloud platform that offers system protection. The company also offers a free threat intelligence feed to users of third-party security software.
- LookingGlass Cyber Solutions This cybersecurity company provides subscribers with threat intelligence in human-readable and computer-ingestible formats.
- Trellix Helix This cloud-based platform is a SIEM that gathers log data from your site for threat-hunting source data.
- Datadog Security Monitoring This cloud platform provides security monitoring for all assets on a network and can even unify the security monitoring service for multiple sites plus could resources.
- ThreatConnect This SaaS threat detection system uses security orchestration, automated, and response methods to use the systems already installed on your network as local agents.
- Heimdal Threat Hunting and Action Center This package performs intelligence gathering for a site from its cloud platform. Threat detection and automated responses create a private corporate threat intelligence platform.
- AT&T USM Anywhere A SaaS platform that includes asset tracking, vulnerability management, and a SIEM with a threat intelligence feed from AT&T Alien Labs.
- Recorded Future This TIP works with your existing security tools and a threat intelligence feed supplied by a division called Insikt Group.
- IBM X-Force Exchange This is a cloud-based threat intelligence sharing platform that you could feed into your existing security tools.
- Splunk Enterprise Security This on-premises platform offers a menu of services, including a SIEM for threat hunting. Installs on Windows, macOS, Linux, and Unix, with a cloud version available. To get over attackers, security analysts need to understand how adversaries think, their techniques, and their intentions behind the attacks.
Threat intelligence is like a “spying-the-enemy” strategy. It is obtaining knowledge of the threat ecosystem around us, from logs, website scans, attack signatures, dark web, and even the criminal underground. In this article we’ll take a look at the Best Threat Intelligence Platforms out on the market and how they'll help you defend your perimeter networks from active and passive threats.

What is a Threat Intelligence Platform?
A Threat Intelligence Platform (TIP) automates the collection and dissemination of information about new hacker attacks.
The TIP strategy replaces the old AV provider strategy of maintaining a department of security analysts. By automating threat reporting and creating a central database with regular extracts, the TIP system speeds up the distribution of threat information.
Threat intelligence can be supplied as a human-readable report or as a data feed that can be automatically read-in and integrated by associated cybersecurity packages.
Some TIPs can also help analyze this intelligence with AI/ML techniques and share it with peers. One of the essential features of TIPs is that they let you set up alerts and notifications based on this data. With proper alerting security, analysts can react quickly to any attack.
Two ways to generate threat intelligence
- Machine-Generated Intelligence It can be knowledge gathered by scanning millions of websites on the web, or by finding new types of signature attacks. This data can be generated through AI or ML techniques.
- Human Intelligence Providers Security analysts gather information from different sources and come up with reports and feeds related to ongoing and new cyber threats.
Although some TIPs vendors can internally generate their threat intelligence data, they can also receive it from a large variety of external resources. Some TIPs can rely entirely on third-party providers to get intelligence feeds, so they can focus on managing the data and generating insights. TIPs can also be integrated into other security systems like SIEMs, WAFs (Web-Application-Firewalls), USM platforms, and more.
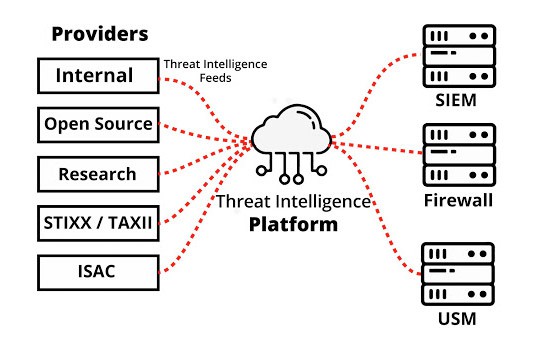
Threat Intelligence feeds
These are one of the most critical elements in TIPs. They are streams of content that provide information on possible security cyber threats. Feeds are made from different indicators like suspicious domains, file hashes, blacklisted IPs, etc.
There are multiple open-source and commercial feeds providers that users can subscribe to. Paid feeds can provide a higher level of threat details because they are usually gathered from closed sources, like the dark web. Open-source feeds, on the other hand, are free but need to be manually selected and curated. Some known feeds are Alien Vaults, ThreatConnect, OSINT, STIX/TAXII, ISACs, etc.
TIPs centralize these threat intelligence feeds generated by different providers and organize them in a single platform. TIPs present threat data in a digestible format, prioritizes the sources, and removes any duplicate entries.
Our methodology for selecting the best threat intelligence platforms:
Threat intelligence is a necessary asset for every business these days to reduce loss and identify vulnerabilities. Below, we have listed some of the important points that you must consider to pick the best Threat Intelligence Platforms for your organization.
- Consider the type and amount of threat sources.
- Make sure it supports automation and orchestration features
- Robust analysis and correlation capabilities
- Integration with Existing Security Infrastructure
- Calculate the total cost of ownership, including licensing, training, and support
- Industry regulations and compliance standards.
The Best Threat Intelligence Platforms
1. EventLog Analyzer ManageEngine – FREE TRIAL
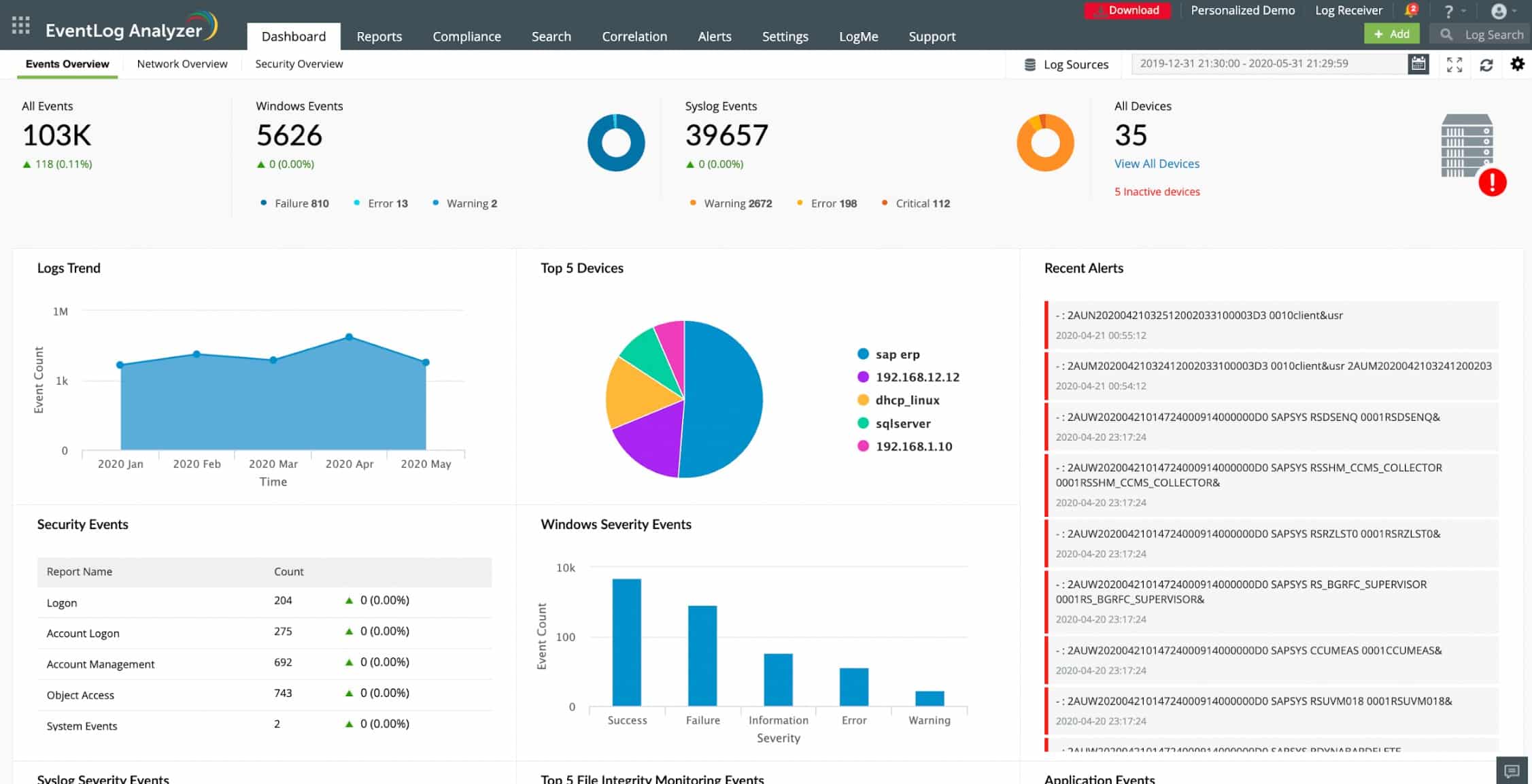
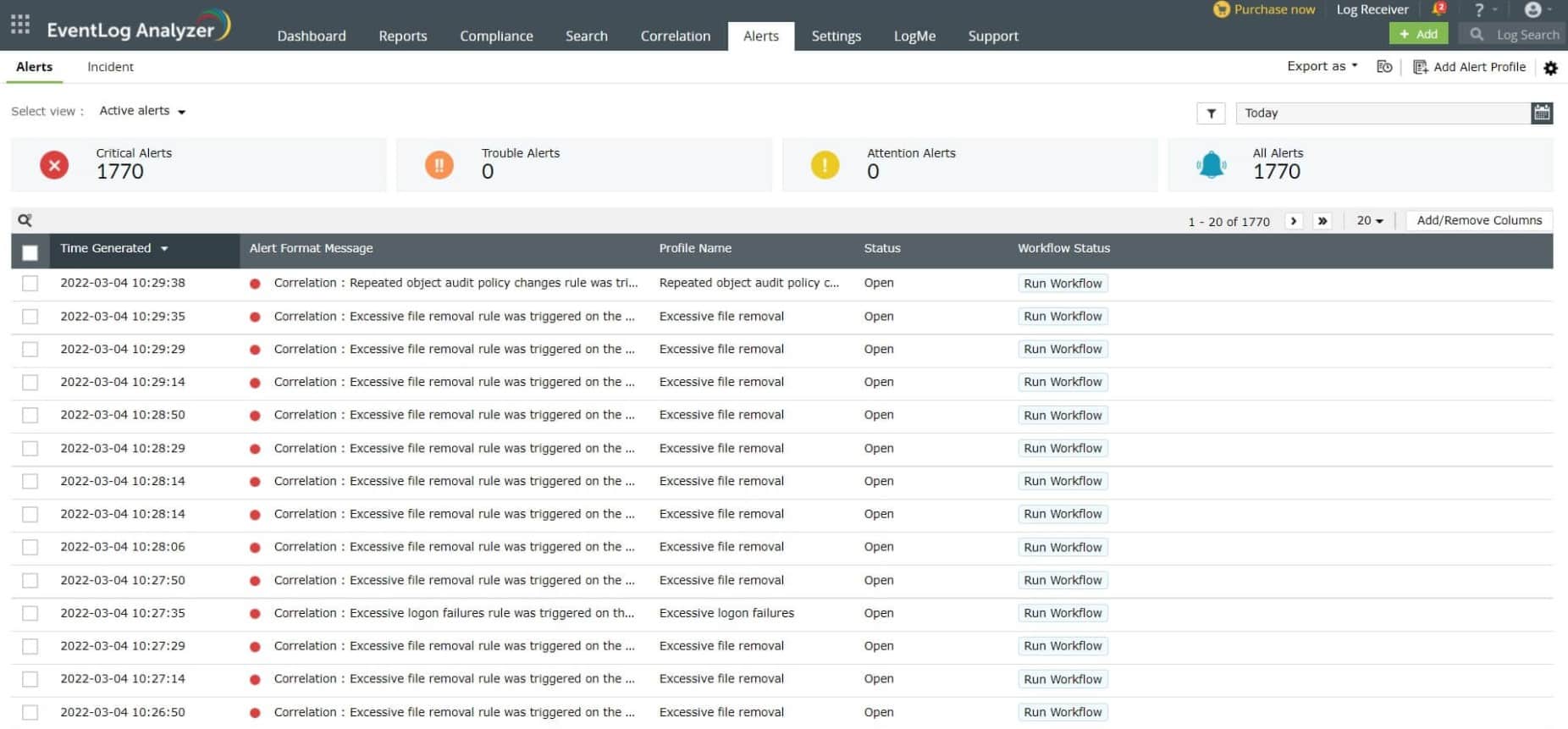
ManageEngine EventLog Analyzer is a web-based comprehensive log manager, auditing, and compliance solution. As the name implies, Event Log Analyzer is a log analysis software that collects, analyzes, and creates reports from a wide range of event logs.
Key Features:
- Log management
- Threat detection
- Takes a threat intelligence feed
- Compliance reporting
Why do we recommend it?
We recommend EventLog Analyzer by ManageEngine for its versatile log analysis capabilities. With custom log parsers, it effortlessly analyzes human-readable log formats, automatically extracting fields and enabling the marking of additional fields. This feature enhances analysis, particularly for unsupported or third-party application log formats, providing comprehensive insights for effective log management.
The tool is also widely used for auditing and report generation purposes. With the Event Log Analyzer, you can run from network device, server, and application audits and create compliance audit reports. The software also offers an integrated SIEM platform with threat intelligence capabilities.
You can view and share intelligence through popular feeds like STIX, TAXII, and AlienVault. The tool also correlates with a global blacklist of IPs to protect you from potentially harmful sources.
Event Log Analyzer alerts you via email or SMS when malicious sources and threats attempt to attack your network.
Who is it recommended for?
This tool is commonly used by cybersecurity experts and professionals in industries prioritizing data security. EventLog Analyzer is ideal for real-time file integrity monitoring and a perfect pick for businesses handling confidential data; the tool tracks changes to files and folders, enabling swift detection of security incidents and ensuring data integrity. It also conducts in-depth analysis on Windows and Linux servers.
Pros:
- Customizable dashboards that work great for network operation centers
- Multiple alert channels ensure teams are notified across SMS, email, or app integration
- Uses anomaly detection to assist technicians in their day-to-day operations
- Supports files integrity monitoring that can act as an early warning system for ransomware, data theft, and permission access issues
- Forensic log audit features enable admins to create reports for legal cases or investigations
Cons:
- Is fairly detailed and requires time to fully explore the platform
Price and License: EventLog Analyzers comes in three different editions, Free, Premium, and Distributed.
Download: Free edition of Event Log Analyzer (maximum of five log sources) or download a fully featured and unlimited Premium Edition on a 30-day free trial which automatically converts to the Free Edition after the trial is up.
2. CrowdStrike Falcon X
CrowdStrike Falcon X is a threat intelligence feed that is designed for use with other CrowdStrike cybersecurity products. The system delivers Indicators of Compromise (IoCs) for use with CrowdStrike Falcon Insight or CrowdStrike Falcon XDR. This service speeds up the threat-hunting processes of CrowdStrike products by providing factors to look for when searching through log data uploaded to the Falcon cloud platform.
Key Features:
- Hybrid solution
- Centralized threat detection
- Local responses
- Threat intelligence feed option
Why do we recommend it?
We recommend CrowdStrike Falcon X as the world's leading AI-native platform for automated threat intelligence. It can automatically investigate incidents and expedite alert triage and response. Other than this, it is integrated into the Falcon platform for faster operation and efficient threat detection and mitigation.
The base package gets you the IoC feed but there are two higher plans. The first of these is Falcon X Premium. That adds on readable reports for guidance that are tailored to the specific sector and location of your business. This advises security technicians of the latest hacker activity and it is supplied by the research team of CrowdStrike. You also get rules to add to Snort and Yara data search tools.
The top plan is called Falcon X Elite. That gets the advice of a security specialist from the CrowdStrike cybersecurity consultancy team. You can get the security of your system assessed by the analyst and then you also get the right to call that specialist for advice when the information that your security systems are difficult to interpret.
Who is it recommended for?
CrowdStrike Falcon X integrates malware sandbox analysis, malware search, and threat intelligence into a unified solution. It is recommended for cybersecurity professionals and industries prioritizing robust endpoint protection, perfect for reducing time and skills required for manual incident investigations.
Pros:
- Doesn’t rely on only log files to threat detection, uses process scanning to find threats right away
- Acts as a HIDS and endpoint protection tool all in one
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Can install either on-premise or directly into a cloud-based architecture
- Lightweight agents won’t slow down servers or end-user devices
Cons:
- Would benefit from a longer trial period
Price: The Falcon PRO platform pricing starts at $8.99 per endpoint/month, Enterprise for $15.99 per endpoint/month. You can inquire about pricing for the Elite and Complete packages.
Download: CrowdStrike Falcon X is a cloud service, so there is nothing to download. You can access a 15-day free trial.
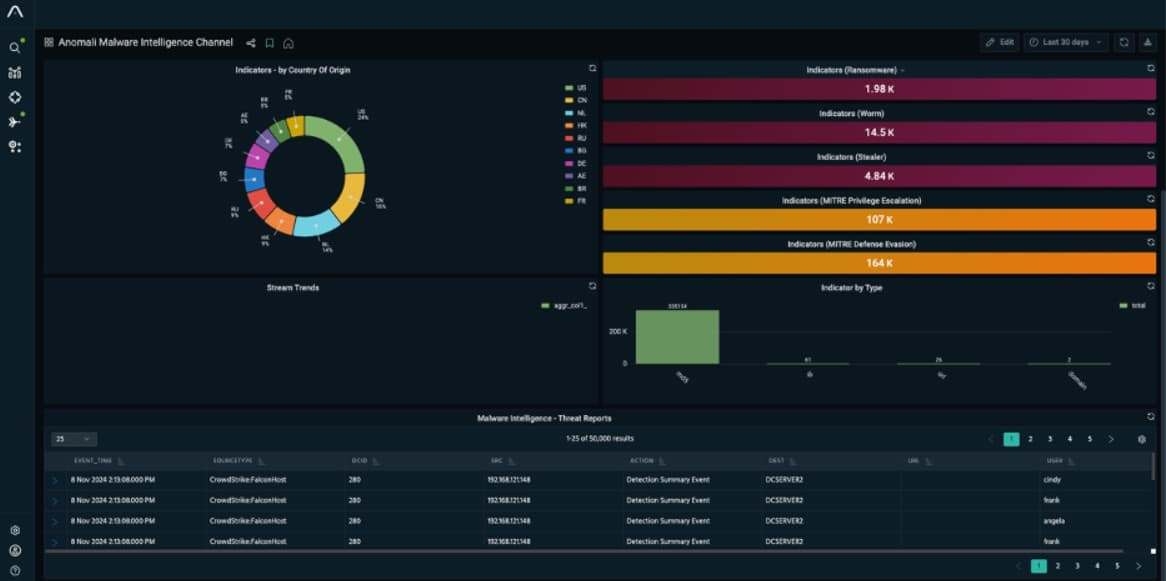
3. Anomali Threat Platform
Anomali Threat Platform is a TIP powered by Machine Learning (ML). It is designed to detect active threats and prioritize them using ML algorithms. The tool normalizes all feed sources into a single platform and enhances the data by adding threat context.
Key Features:
- AI-based threat hunting
- Integrate threat intelligence standards
- Choose a third-party threat intelligence service
- Proprietary threat intelligence
Why do we recommend it?
We recommend the Anomali Threat Platform for its AI-driven approach. It significantly boosts analyst productivity by using petabytes of historical security data. It uses integrated security analytics and AI to autonomously detect, hunt, and enrich threats with contextual information.
Anomali helps security managers identify new attacks and avoid false positives by combining threat intelligence with existing and historical events. It collects intelligence feeds from premium providers like OSINT, STIX/TAXII, and ISACs.
Anomali also offers the Anomali Preferred Partner Store which is a one-of-a-kind cyber-security marketplace for threat intelligence and integrations. Through this store, you can have access to a catalog of threat intelligence providers, evaluate them, and buy intelligence feeds.
Anomali also offers Limo, a free Threat Intelligence Feed that contributes to cyber-threat intelligence. They also provide STAXX, the free STIX/TAXII Solution, to help you collect and analyze more threat intelligence.
Who is it recommended for?
The Anomali Threat Platform streamlines critical intel collection and distribution into security operations workflows. It is widely used by cyber professionals across the globe for seamless integration of machine-readable intel with security controls coupled with integrated dashboards. This tool makes decision-making easier with real-time insights into prioritized and relevant threats.
Pros:
- Highly flexible platform
- Offers a free cloud-based intelligence feed
- Offers threat detection as a service
Cons:
- Better suited for medium to large-sized companies
Price: Get a quote.
Download STAXX free client that gives you access to STIX–TAXII feeds. There is no free trial for the Anomali Threat Platform, but you can request a demo.
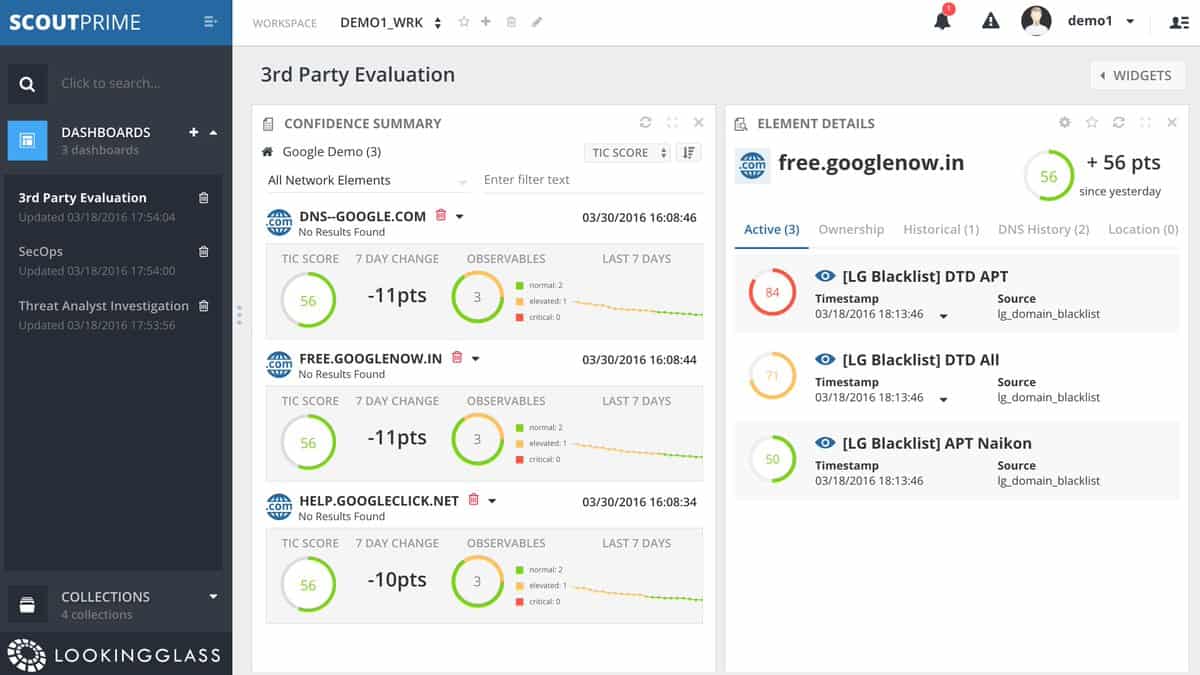
4. LookingGlass Cyber Solutions
LookingGlass offers diverse cyber-security products and services for different stages of an attack life-cycle. Their portfolio ranges from managed services, two threat intelligence platforms, data feeds, and automated threat response software.
Key Features:
- Threat Modeling
- Analyst Workbench
- Risk Scoring
- Data Consumption Model
- Threat Intelligence Investigation
Why do we recommend it?
We recommend LookingGlass Cyber Solutions for its comprehensive approach to cyber risk management. By monitoring your attack surface with enriched threat intelligence, it provides a robust framework to assess and address vulnerabilities. It also creates customized threat actor models for proper detection and response, ensuring a tailored and proactive cybersecurity strategy.
Their two TIPs are ScoutTHREAT and ScoutPrime. ScoutTHREAT is an advanced proactive threat monitoring solution. It tool allows security analysts to link atomic indicators, like IPs or file hashes to higher-level Tactics, Techniques, and Procedures (TTPs) frequently used by hackers.
ScoutPRIME, on the other hand, is considered a cyber-situational awareness platform. It helps you visualize the entire external threat landscape and all your IT assets. It centralizes all the collected, and normalized data feeds into one platform.
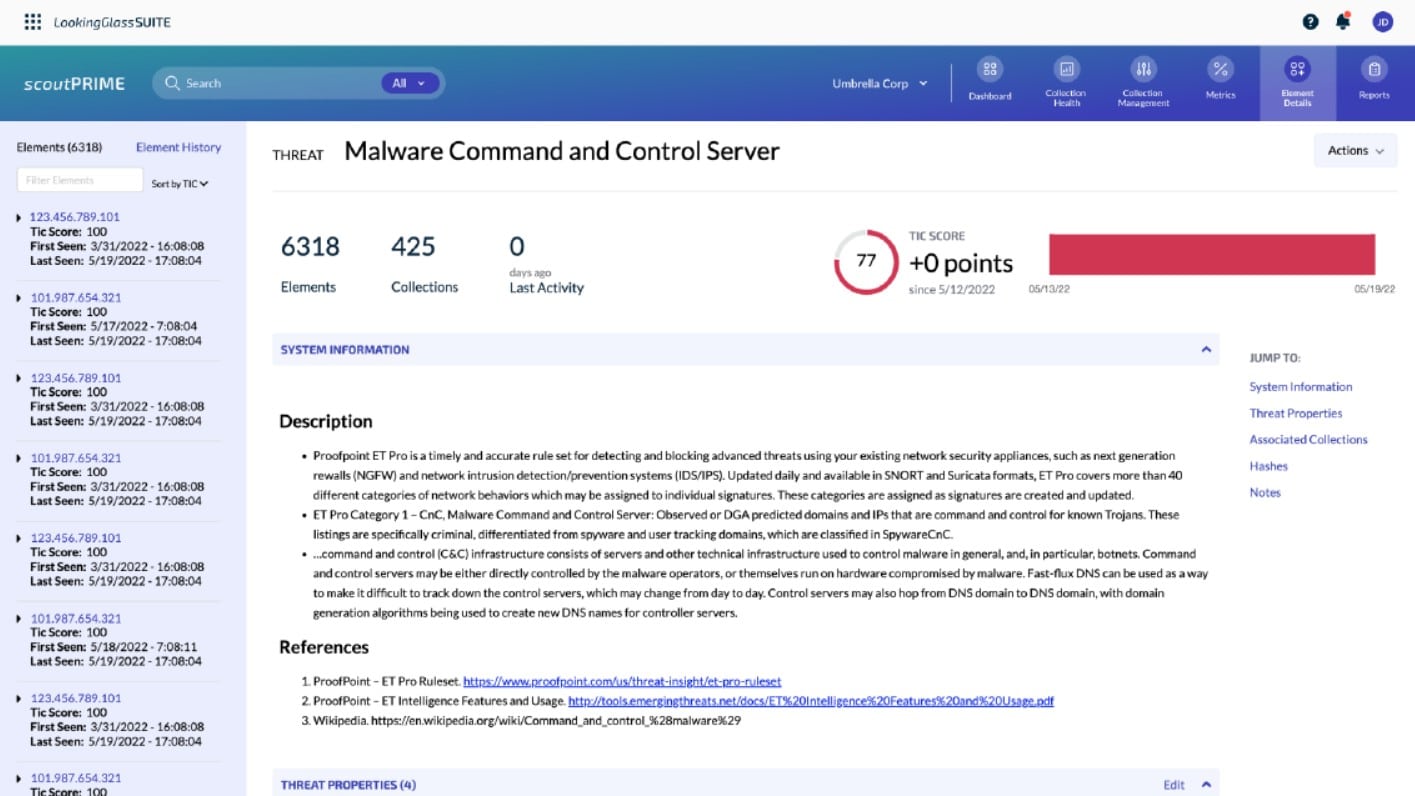
Who is it recommended for?
Cybersecurity experts and professionals in diverse industries use this tool. LookingGlass Cyber Solutions is a combination of AI, full-spectrum intelligence services, and a robust response portfolio. The tool is ideal for those seeking automated threat indicators and entity extraction, efficiently extracting key attack indicators from structured and unstructured threat intelligence for rapid correlation and processing.
Pros:
- Offers cyber security as a service
- Offers SIEM services
- Can produce technical and C-level overview reporting
Cons:
- Is best for companies who want a more hands-off approach to their security
Price: Contact sales.
Download: to try the platform for free, contact sales first.
5. Trellix Helix
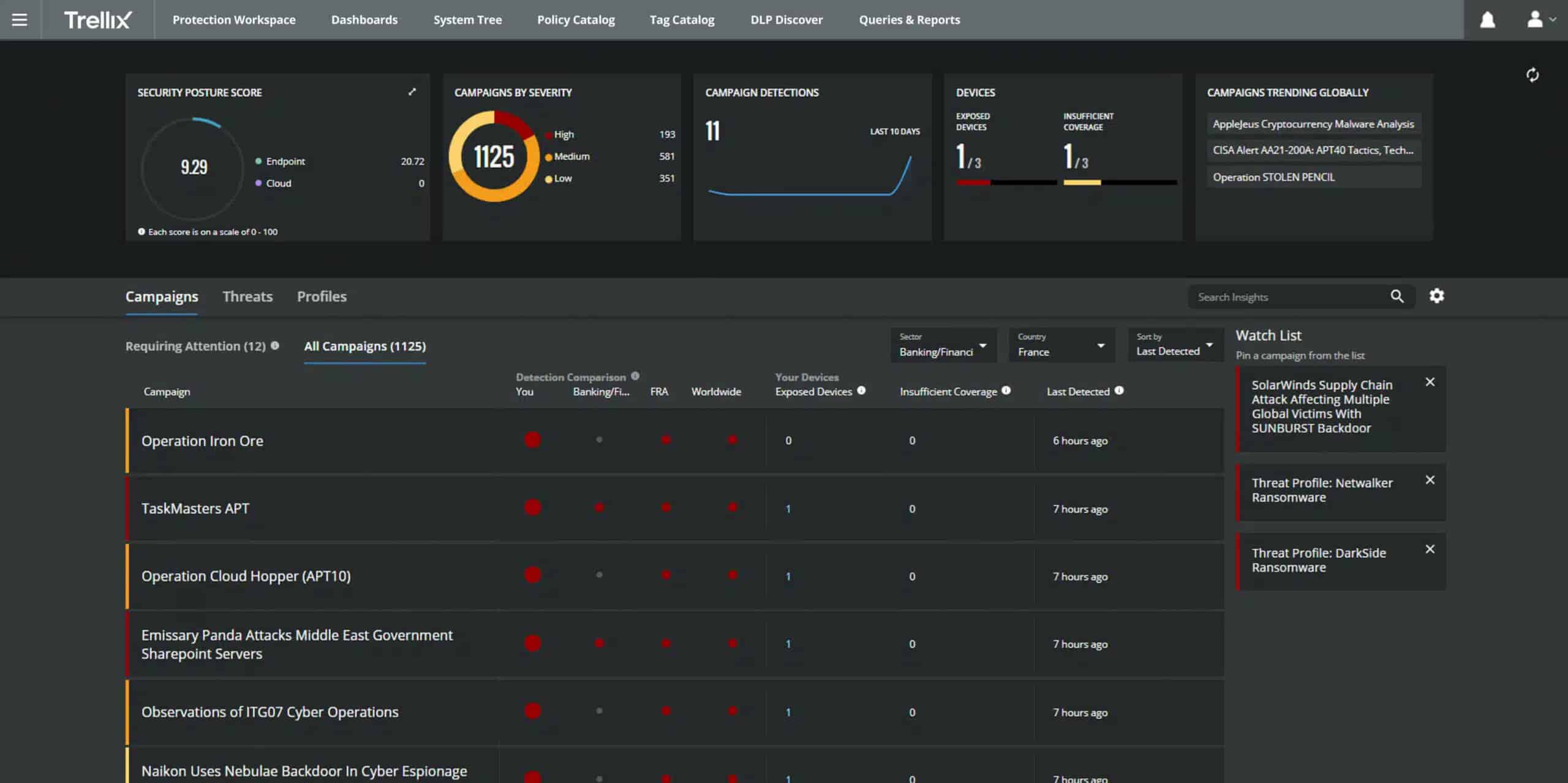
Trellix Helix is the new name for FireEye Helix. This is a cloud-based security platform that triggers alerts for detected threats and provides automated and manual threat remediation. The solution is based on SIEM analytics and powered by Trellix human analysts experts.
Key Features:
- Data gathering
- SIEM
- Third-party cybersecurity coordination
- Threat intelligence feed
Why do we recommend it?
Experts prefer the Trellix Helix for its advanced threat detection, and it is powered by machine learning, AI, and real-time cyber intelligence. It provides crucial insights into threat actors and their motives. The intelligent and adaptive platform enables the prediction and prevention of emerging threats. You can quickly identify root causes and respond in real-time for a proactive cybersecurity approach.
Trellix Helix also integrates different tools and threat intelligence capabilities to protect you from the latest threats. The FireEye system is compatible with a threat intelligence feed from Mandiant. The two companies recently split and the feed was a FireEye service during the period that the Helix system was written. You can also take advantage of this intelligence by integrating alerts and events data.
The software leverages ML and AI to analyze behavior and create alerts when there are anomalies. With Threat Intelligence and advanced analytics, Trellix Helix can detect a wide range of multi-vector threats.
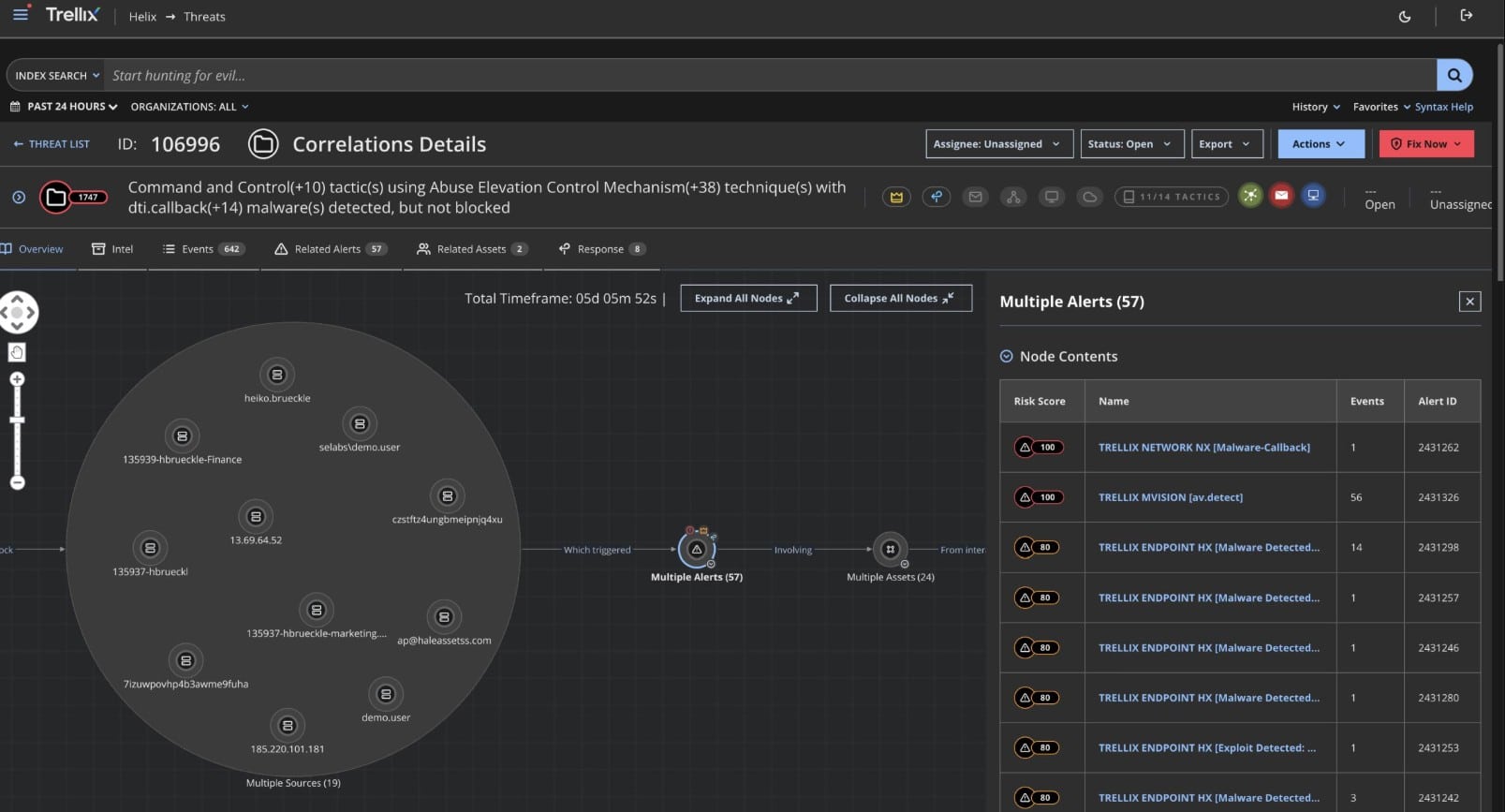
Trellix Helix detects security events by comparing and normalizing data from multiple integrated tools:
- Next-gen SIEM.
- Security Analytics.
- Threat Intelligence.
- Security Orchestration and Automation (SOAR).
- User and Entity Behavior Analytics (UEBA).
- Compliance Reporting.
Who is it recommended for?
Recommended for cybersecurity experts and enterprises seeking comprehensive threat awareness, Trellix Helix offers visibility and control across the entire organization. It has various security functions, and it helps you collect, correlate, and analyze critical data. You must choose this tool if you prioritize efficiency and contextual threat intelligence for effective cybersecurity management.
Pros:
- Great interface, the dark theme is great for long-term monitoring in NOCs
- Subscription-model keeps your database updated with the most recent threats and bad-actors
- Provides insights for remediation and preventive actions based on recent events
- Playbooks offer remediation workflows to automatically fix issues
Cons:
- Configuration can be challenging
- Reporting can be cumbersome and difficult to customize
Price and License: Trellix doesn’t publish a price list so you need to contact sales to get a quote.
Download: There is no downloadable free trial. You can access a free demo to see how Trellix Helix works.
6. Datadog Security Monitoring
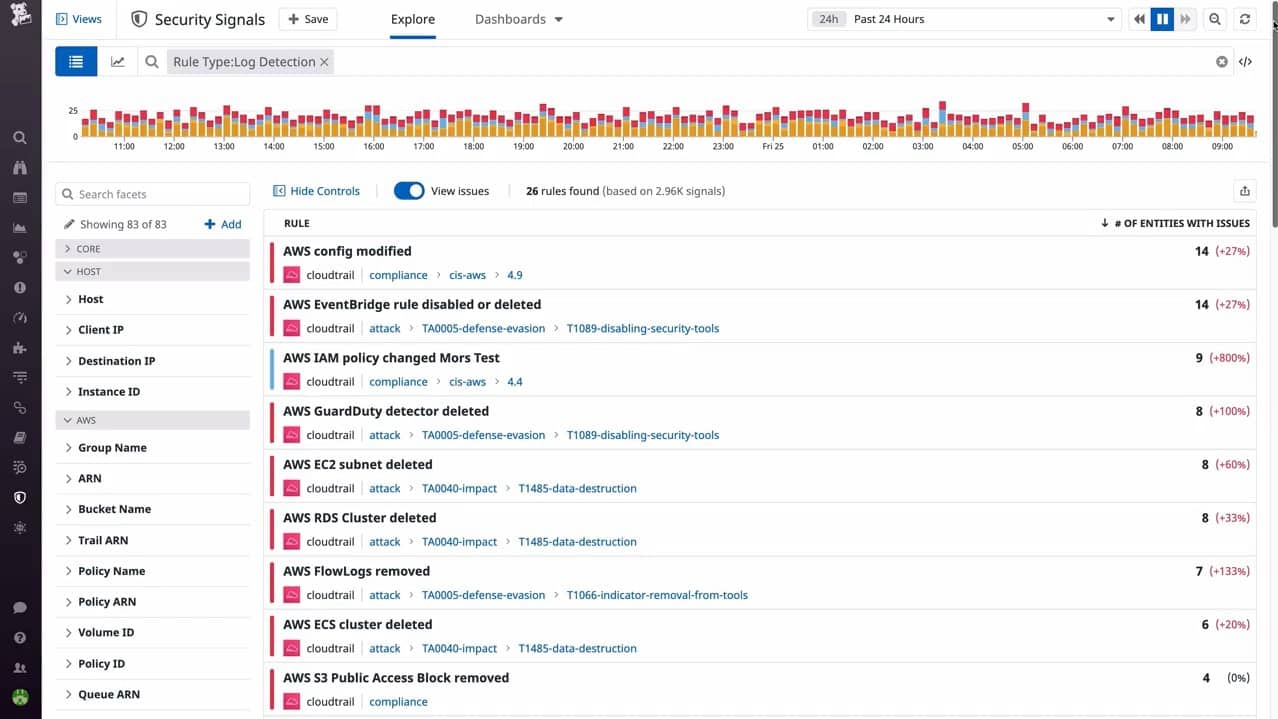
Datadog Security Monitoring is one of the services offered by this SaaS platform of system monitoring and management tools.
Key Features:
- Intrusion detection
- Log consolidation
- Integrate security alerts from other security packages
- Alerts that can be forwarded as notifications
- Automated threat hunting
- Instant proprietary threat intelligence
- Option to include external threat intelligence feeds
- DevOps security testing options
Why do we recommend it?
Datadog Security Monitoring has great real-time threat detection capabilities. With automatic identification of attacker techniques and misconfigurations, Datadog enables organizations to detect threats across applications, networks, and infrastructure swiftly. You can achieve enhanced security with rapid, efficient monitoring that begins safeguarding your assets within minutes of implementation.
The Security Monitoring service is a SIEM system that gathers event data from protected systems and consolidates that data on the cloud. Your account can merge the monitoring of many sites and resources – you just need to install an agent on each location.
Threat intelligence is provided by the grouped experience of all Datadog customers. The threat hunting system applies that intelligence to the pool of log messages that were gathered from all locations.
Extra services on the Security Platform can be added on to the Security Monitoring plan. These other services are designed to test applications under development and perform vulnerability scanning on cloud assets.
Who is it recommended for?
It is recommended for cloud-focused industries and professionals to get comprehensive analysis across cloud environments. It is ideal for both DevOps and Security teams and facilitates seamless navigation through visualizations and telemetry. With a unified platform, it easily aligns development and security efforts, providing full observability and ease of use.
Pros:
- Highly scalable cloud-based monitoring that can applications across multiple WANs
- Flexible à la carte pricing and feature options
- Vast amount of integrations, great for large networks utilizing numerous third-party applications
- Templates work extremely well out of the box, customization is possible but not always necessary
Cons:
- Could benefit from having a longer 30-day trial period
Price: This service is priced per GB of processed log data with a rate of $0.20 per GB when paid annually or $0.30 when accessed in an on-demand account. You can register for a 14-day free trial.
7. ThreatConnect
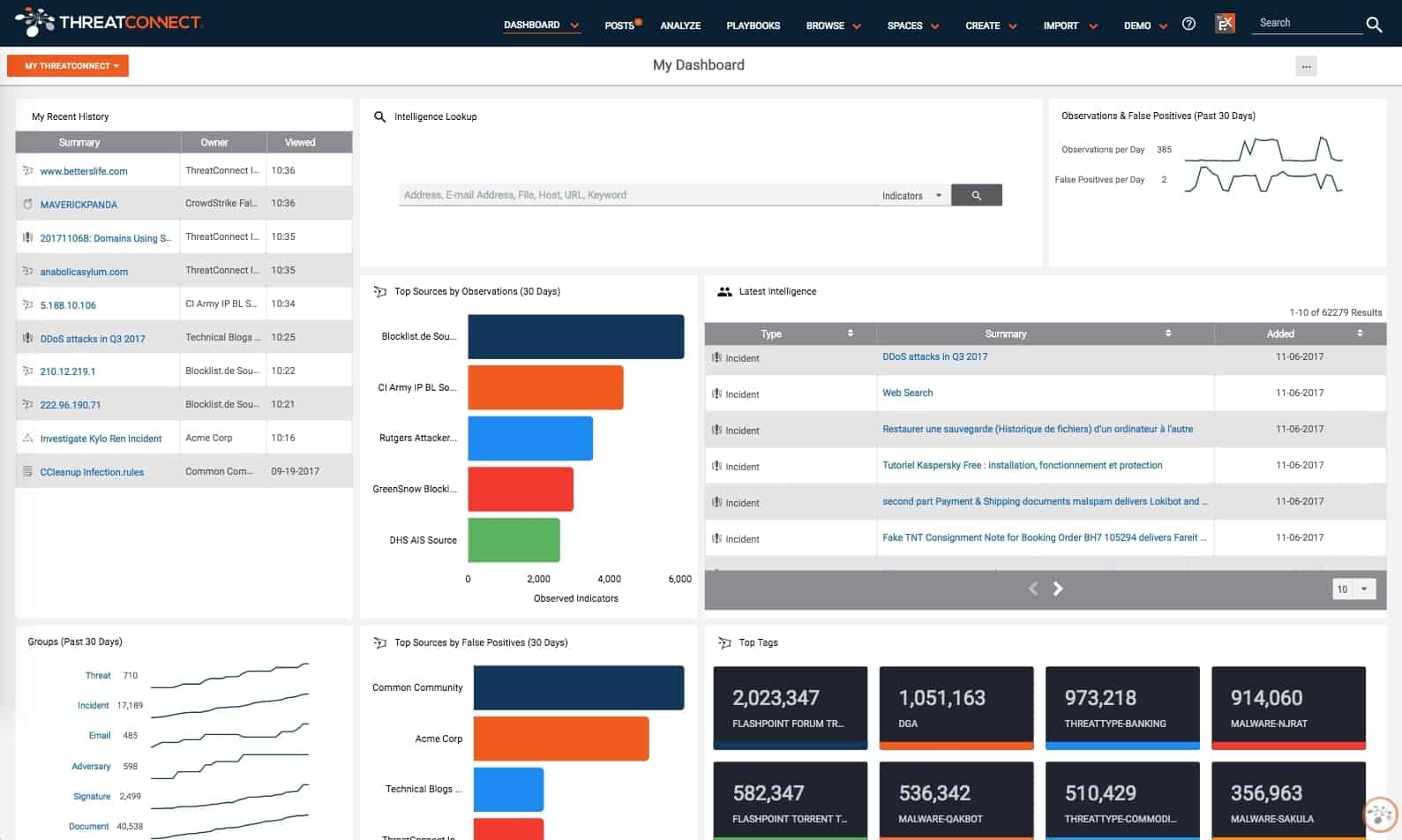
ThreatConnect is a SaaS-based security solutions provider. Their Threat Intelligence Platform enables users to aggregate and act based on threat intelligence data. ThreatConnect can take external or internal threat data and convert them into digestible and actionable intelligence that helps analysts make informed decisions.
Key Features:
- Internal threat intelligence
- External threat intelligence feed
- Threat prioritization
- Automated response orchestration
Why do we recommend it?
We recommend ThreatConnect as a leading SaaS-based security solutions provider. It uses robust techniques like analytics, automation, and machine learning to improve the organization's security. It helps to mitigate critical vulnerabilities and reduce the mean time to detect and respond.
ThreatConnect combines intelligence, automation, orchestration, and response in a single platform to help companies be more proactive in their security.
- Intelligence: Helps you prioritize threats and understand their impact. With ThreatConnect, you can operationalize and aggregate intelligence, convert artifacts into intelligence, correlate data, and more.
- Automation: The platform was designed to help users understand abnormal behaviors, automate workflows, and solve threats efficiently using intelligence data. With ThreatConnect, you can automate triage and phishing reporting to get a faster response.
- Orchestration: ThreatConnect allows you to orchestrate workflows so that you can respond faster to threats. For example, you can orchestrate processes at the time of an incident.
- Response: With ThreatConnect, you can manage team collaboration before, during, and after an incident to improve response times.
Who is it recommended for?
ThreatConnect is commonly used by cyber professionals as it follows a modern approach to Threat Intelligence Operations. It is suitable for those seeking an evolved Threat Intel Lifecycle and aiming to enhance cybersecurity strategies through a progressive and comprehensive threat intelligence framework.
Pros:
- Offers threat detection as a service
- Leverages automation for better threat response
- Uses response methods based on tools present in your network
Cons:
- Better for larger companies
Price: Request a quote.
Download: You can start using ThreatConnect for free by opening an account.
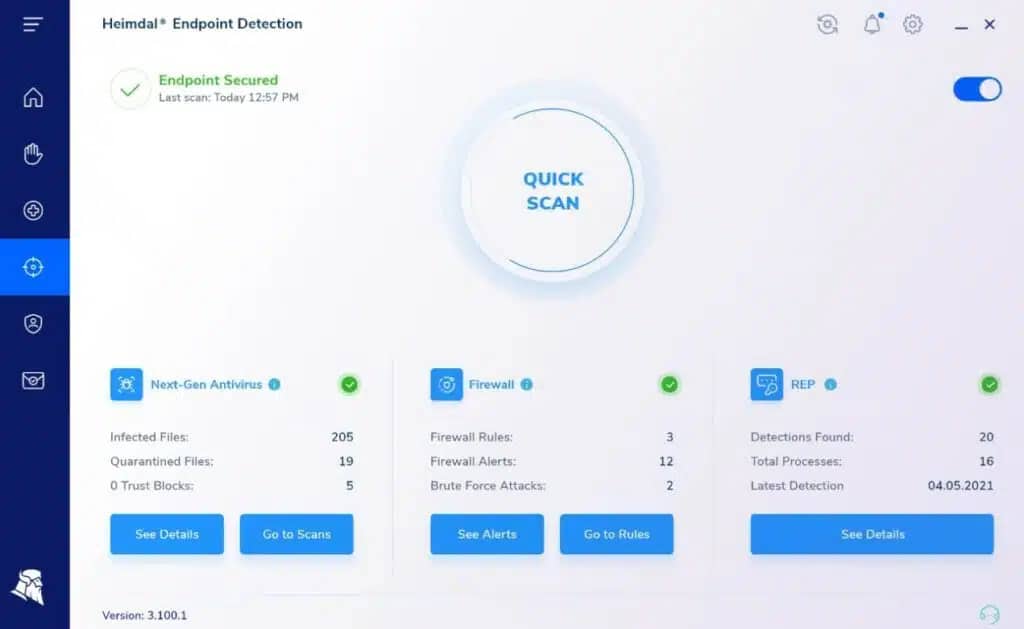
8. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center is a cloud-based platform that gathers data from on-premises cybersecurity packages, scans it for threats, and then disseminates threat data and response instructions.
Key Features:
- Interacts with on-site cybersecurity
- Common data pool
- Centralized threat hunting
- Response instructions
Why do we recommend it?
We recommend Heimdal Threat Hunting and Action Center for its consolidated approach to managing alerts, data, and security responses in real time. With a single pane of glass, it offers context-rich, assisted action at every level, providing security teams with an advanced threat and risk-centric view of their entire IT landscape. This tool improves decision-making with granular telemetry across endpoints and networks.
The platform requires that a customer is already using at least three Heimdal security packages on-site. These are the front-line agents for the threat intelligence platform.
One of the three on-premises packages that support the Threat Hunting and Action Center is the Heimdal Next-Gen Anti-Virus system, which installs on Windows, macOS, and Linux. The NGAV package includes a mobile device management (MDM) system that operates on devices running Android, and iOS.
The two other supporting packages should be selected from Network Security, Email Security, Patching & Asset Management, and Endpoint Security.
The Threat Hunting module is called the XTP Engine, which means Extended Threat Protection. This is a SIEM, which mines uploaded activity reports for threats. The Action Center triggers security advice and response instructions to on-device tools if a threat is detected.
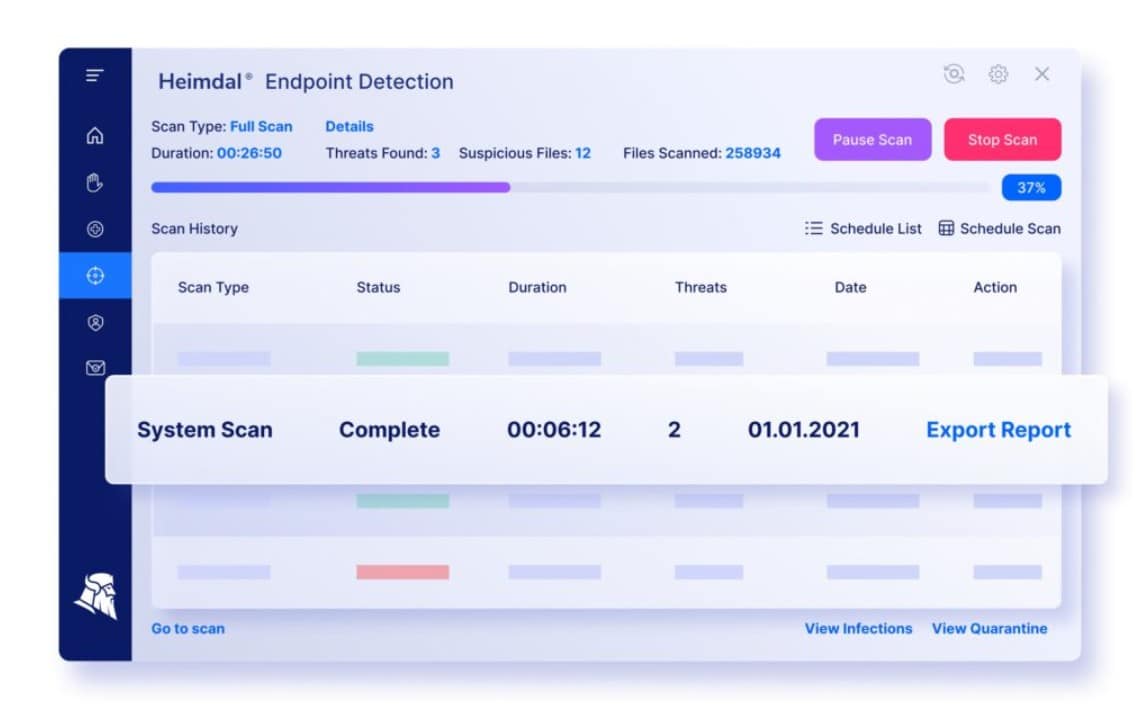
Who is it recommended for?
It is recommended for cybersecurity professionals and IT experts. Heimdal Threat Hunting and Action Center allows security teams to make smart decisions. It has a one-click execution of commands like scanning, quarantine, and isolation. Overall, it is the best choice for professionals investigating incidents or threats, offering detailed information for comprehensive analysis.
Pros:
- Gathers activity records from Heimdal cybersecurity tools
- Includes a vulnerability scanner and system hardening measures
- Searches activity records for threats
- Implements automated responses
- Provides a hybrid cybersecurity solution with on-premises and cloud elements
Cons:
- No free trial
Price and License: Heimdal doesn’t publish a price list.
Download: There is no free trial for the Threat Hunting and Action Center platform. However, you can request a demo.
9. AT&T USM Anywhere
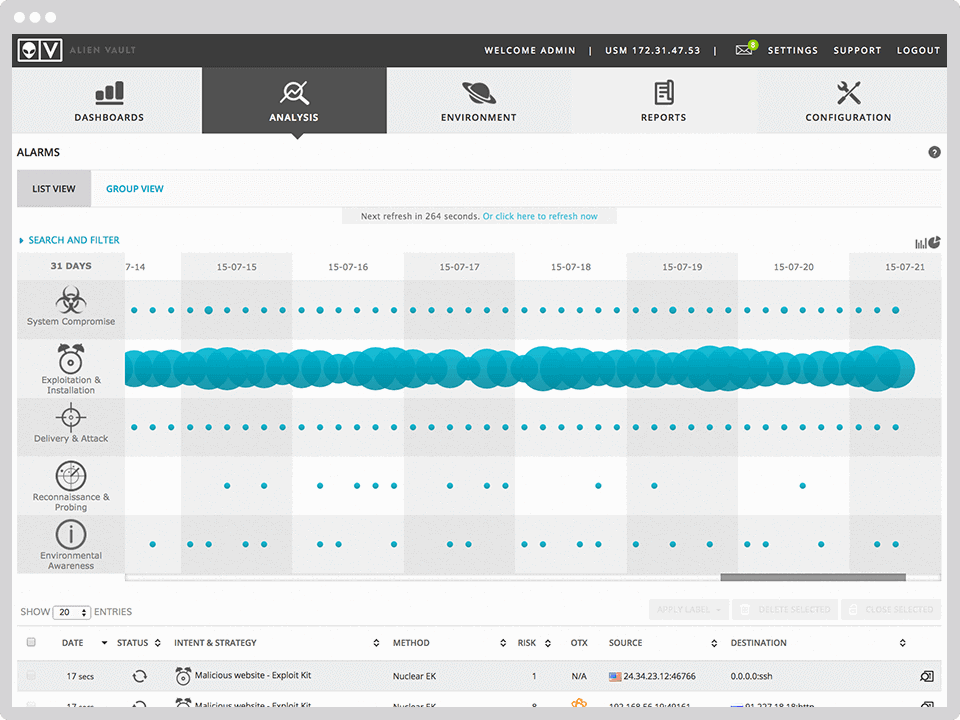
AT&T acquired USM Anywhere when it bought AlienVault in 2019. This cloud platform includes an asset discovery service, a threat detection system, and a vulnerability scanner. As the name of this service explains, it is able to monitor any IT asset no matter where it is located.
The USM is composed of
- Asset Discovery.
- Threat Detection (NIDS and HIDS)
- Assessment and analysis
- Incident Response.
- Compliance Management.
AT&T USM Anywhere gives you quick and centralized visibility into the entire threat ecosystem.
Key Features:
- Known as AlientVault
- Stablemate of Open Threat Exchange
- External threat intelligence options
- Vulnerability scanning
Why do we recommend it?
We recommend AT&T USM Anywhere for its comprehensive Risk Advisory services. It suits requirements for almost all business sizes. It helps in identifying and mitigating cyber and compliance risks, fortifying cyber resilience. This tool uses cutting-edge security technology for fast-track security operations.
The security system receives a threat intelligence feed that is curated by AT&T Alien Labs. That update arrives every 30 minutes and directly updates the threat-hunting rules of the USM service.
Who is it recommended for?
It is recommended for cybersecurity experts and professionals in diverse industries. AT&T USM Anywhere is ideal for defending endpoints against sophisticated cyber threats. With autonomous detection and response capabilities at machine speed, it's a robust solution for proactive threat hunting if you strive for complete security.
Pros:
- Available for Mac and Windows
- Can scan log files as well as provide vulnerability assessment reports based on devices and applications scanned on the network
- User powered portal allows customers to share their threat data to improve the system
- Uses artificial intelligence to aid administrators in hunting down threats
Cons:
- Would like to see a longer trial period
- Would like to see more integration options into other security tools
Price and License: AT&T USM comes in three different editions with different pricing, Essentials ($1075 /mo.), Standard ($1695 /mo), and Premium ($2595 /mo).
Download: Get a fully functional free trial of USM Anywhere for 14 days.
10. Recorded Future
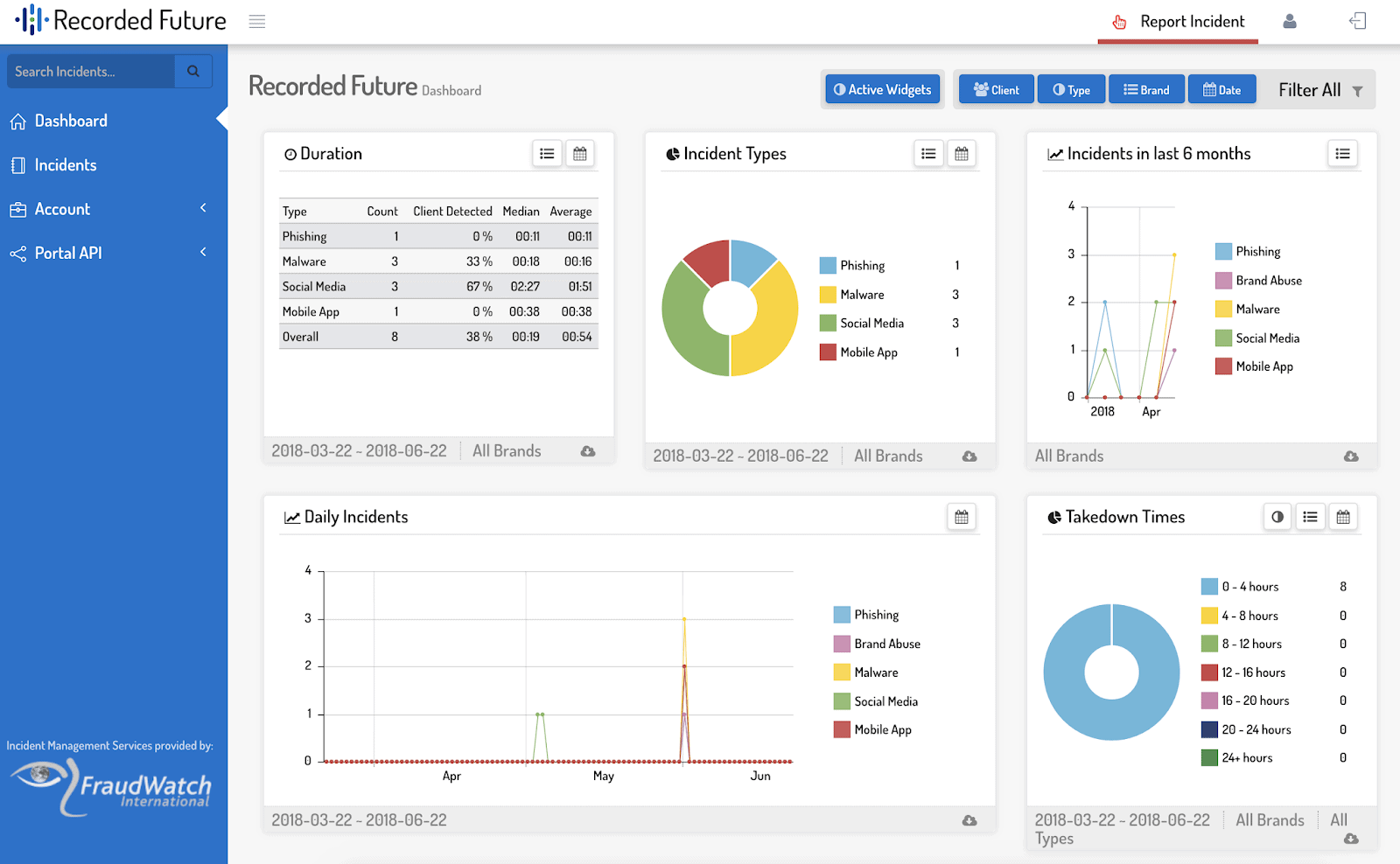
Recorded Future is an all-in-one threat intelligence solution.
Key Features:
- Centralize and contextualize any data feed.
- Collaborate with a team on threat analysis.
- Integrate with third-party solutions.
- Powerful alerting system.
Why do we recommend it?
We recommend Recorded Future as the most comprehensive and independent threat intelligence cloud platform. It offers real-time, unbiased, and actionable intelligence to identify and mitigate threats spanning cyber, supply-chain, physical, and fraud domains. Recorded Future stands as a trusted resource for holistic threat intelligence, ensuring robust security measures.
It collects and analyzes massive amounts of threat data in real-time and converts it into valuable insights using NLP (Natural Language Processing) and ML technology. Recorded Future makes integration with your current security platforms such as SIEMs, or firewalls easy to implement.
It can aggregate internal intelligence data with external sources and contextualize it into a central platform. Insikt Group a human-based research and analysis team that works with Recorded Future to hunt down Malware and look for emerging threats.
It provides the Recorded Future platform with new and unique intelligence. Recorded Future solution works as a Threat Intelligence Platform.
It has all the functionalities as a TIP and even includes its own threat intelligence. You can use it to analyze the collected data and get a holistic view of the entire threat landscape.
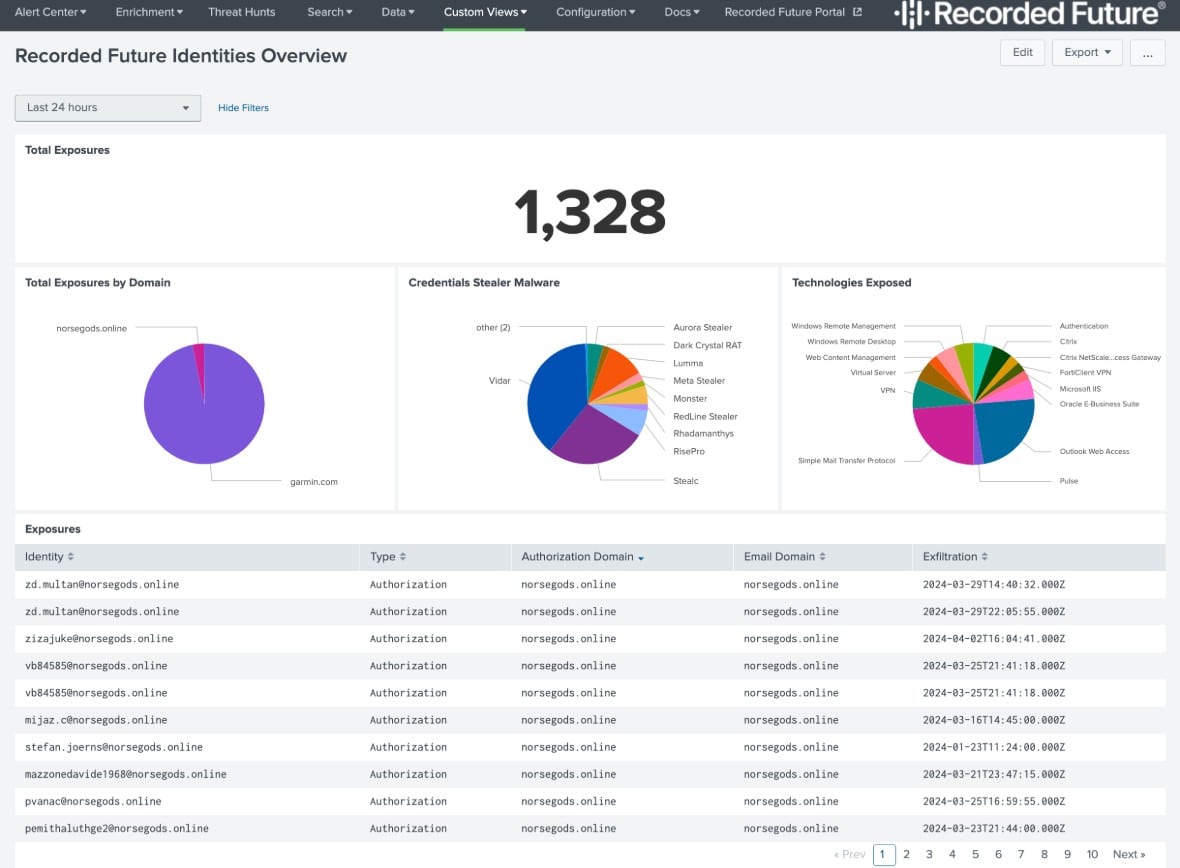
Who is it recommended for?
Recorded Future is widely used in cyber industries to reduce risk. Whether in various IT and security stacks or at different maturity levels, organizations can use valuable insights to respond to and mitigate cyber-attacks quickly. Add this as a valuable resource to your business for comprehensive threat intelligence.
Pros:
- Simple yet intuitive user interface
- Modular widgets allow for easy dashboard customizations
- Can analyze collected threat data or publically available information online
Cons:
- Must contact for pricing
- Steeper learning curve due to their use of machine learning
Price and License: Recorded Future comes in three different editions, Express, Core, and Advanced. To learn more about license and price, contact Recorded Future.
Download: Request a demo.
11. IBM X-Force Exchange
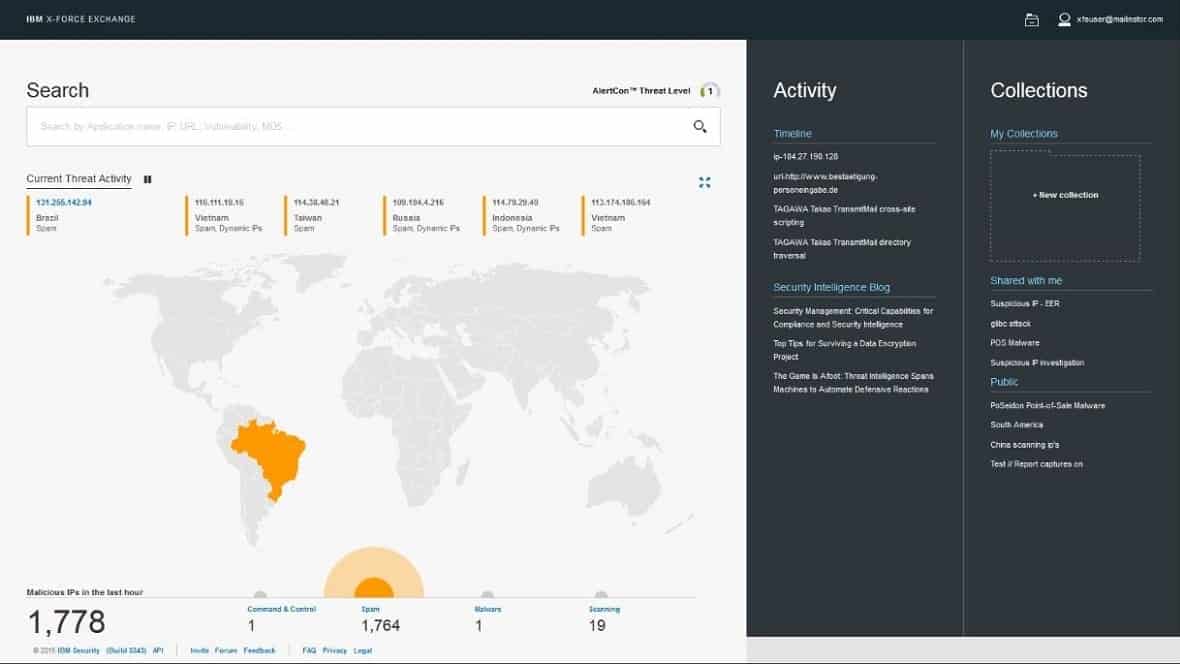
IBM X-Force Exchange is a cloud-based collaborative Threat Intelligence Platform.
Key Features:
- Access to human-generated threat intelligence data
- Collaborate and share threat intelligence.
- Central platform for organizing data.
- Configure watchlists for continuous monitoring.
- Integrate third-party intelligence.
Why do we recommend it?
We recommend IBM X-Force Exchange for its IBM Security Guardium Vulnerability Assessment capabilities. This tool scans data infrastructure across databases, data warehouses, and cloud environments to detect vulnerabilities. It suggests remedial actions based on benchmarks from standards like STIG, CIS, and CVE, ensuring a robust approach to vulnerability management.
It helps security analysts research, aggregate sources of intelligence, and share data with their peers. The platform is supported by machine-generated data and by the IBM X-Force Research team that provides human-generated intelligence.
The research team and the software monitor over 25 billion websites looking for threats. The platform is also supported by a large database of more than 96,000 risks, including attacks, blacklisted IPs, etc.
Who is it recommended for?
Recommended for cybersecurity professionals and experts across diverse industries, IBM X-Force Exchange caters to those seeking efficient threat intelligence. It is perfect for searching or submitting files for scanning. It allows checking for Indicators of Compromise (IOCs), keywords, and malware intelligence. You can also collaborate through groups and share and discuss issues about threat intelligence collections.
Pros:
- Based on a flexible cloud platform
- Offers man integrations to share threat intelligence into your existing technology
- Better suited for enterprises
Cons:
- Must contact for pricing
Price and license: For more information on pricing and license, contact sales.
Download: You can try IBM X-Force Exchange by signing up for a free guest account.
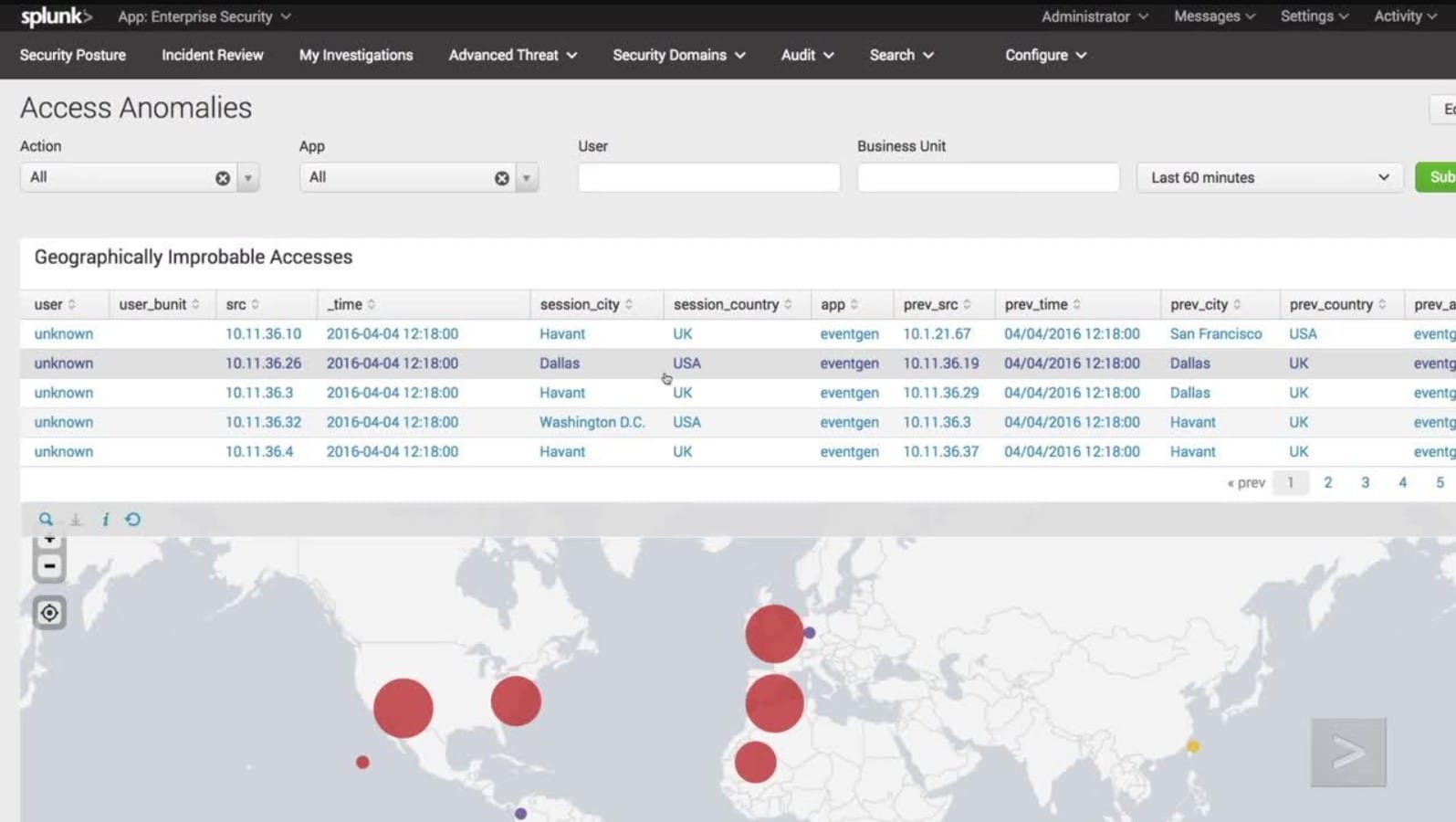
12. Splunk Enterprise Security
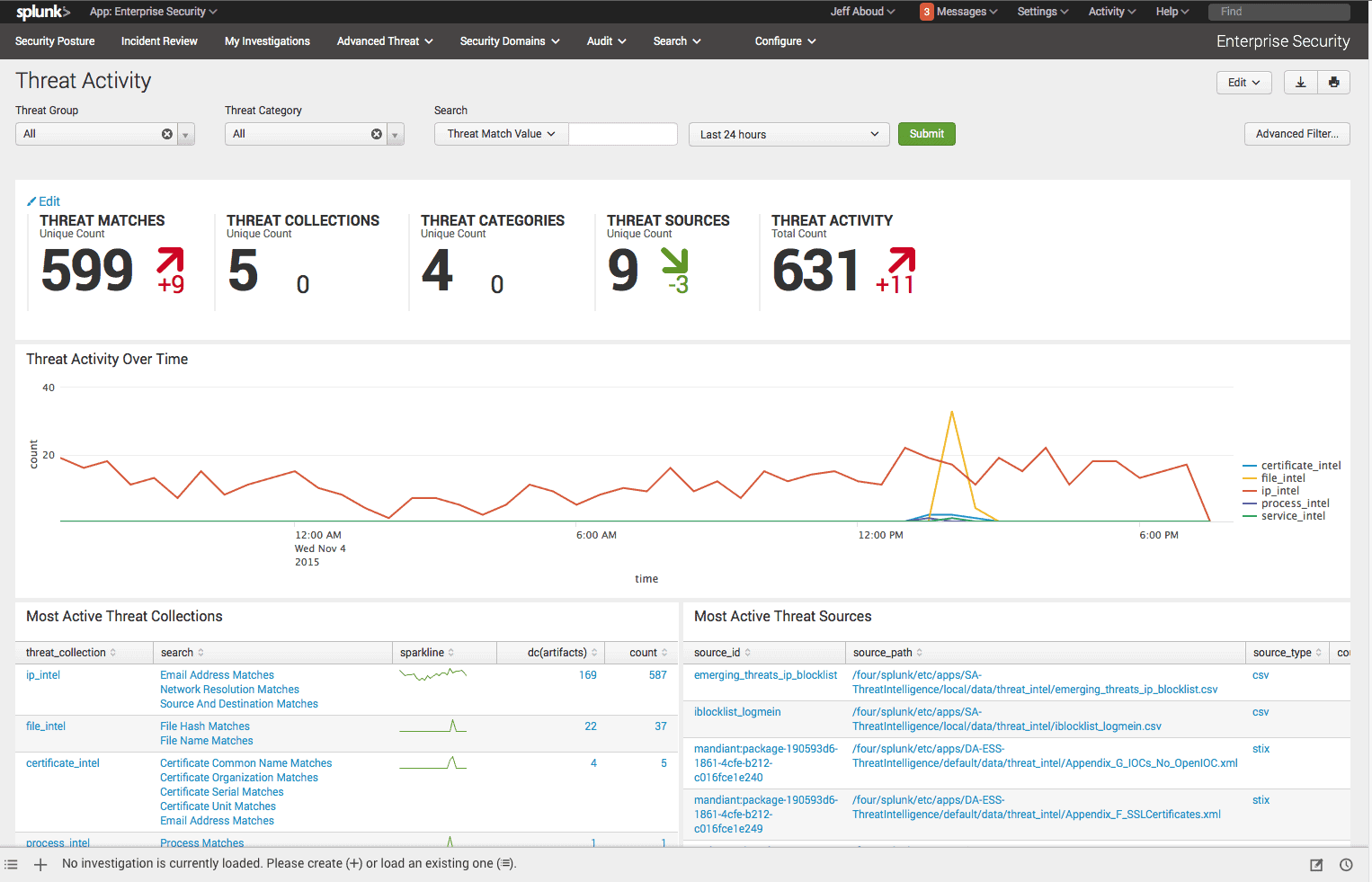
Splunk develops web-based software for searching, monitoring, and analyzing machine-generated data. They provide security through SIEM, AIOPs, Machine Learning, Application and log management, and IT compliance software
Key Features:
- Ingest threat data from the cloud or on-premises
- A central dashboard to streamline threat analysis.
- Automated actions and workflows.
- Alert management.
- Risk scores.
Why do we recommend it?
We recommend Splunk Enterprise Security for breaking down data silos and obtaining actionable intelligence. It can quickly ingest data from multi-cloud and on-premises deployments to have full visibility. It lets organizations detect malicious threats in their environment, making it an essential tool for robust cybersecurity and threat detection.
Splunk Enterprise Security is an analytics-driven SIEM solution that uses actionable intelligence to protect enterprises from threats. The software can integrate with the Threat Intelligence Framework to receive and manage threat feeds and generate alerts. This framework collects and normalizes all threat intelligence data. It also provides a searching and correlation mechanism to improve attack detections.
The Splunk Enterprise Security framework also comes with audit dashboards that help you retrieve, normalize, and analyze threat intelligence.
Who is it recommended for?
Recommended for IT and cybersecurity professionals in diverse industries, Splunk is built on an open and scalable data platform. It is perfect for dynamic business needs that use multiple cloud platforms. Overall, Splunk is an essential solution for adaptable and comprehensive data-driven insights.
Pros:
- Can utilize behavior analysis to detect threats that aren’t discovered through logs
- Excellent user interface, highly visual with easy customization options
- Easy prioritization of events
- Offers features to create operational and business intelligence from your data
- Available for Linux and Windows
Cons:
- Better suited for large enterprises
Price and license: Contact Spunk for pricing information.
Download: Get seven days of a free Splunk Enterprise Security sandbox environment, so you can start testing the product.
Final Words
Threat Intelligence Platforms (TIPs) depend on threat intelligence providers, whether commercial or open-source. Some TIPs vendors generate their internal intelligence through machine-generated data or human analysts and ingest it to the platform. These vendors also sell their intelligence feeds to other TIPs.
Although threat intelligence feeds are very useful, without context, it is difficult to gain real insights to hunt down threats proactively. TIPs can aggregate, normalize, curate, organize, send alerts, and even perform actions from all this data. They give the context that the analyst needs to understand the threats at hand.
Some of the ten best Threat Intelligence Platforms shown above have free trials so that you can start protecting your networks. Tools such as Event Log Analyzer, IBM X-Force Exchange, N-able Threat Monitor, and Datadog Security Monitoring will give you a chance to dive into this amazing space.
Threat Intelligence Platforms FAQs
What is the difference between a threat intelligence platform and a security information and event management (SIEM) solution?
A threat intelligence platform is a specialized solution that focuses on collecting, analyzing, and disseminating threat information, while a SIEM solution provides a broader range of security management and analysis capabilities, including log management and security event correlation.
How do I choose a threat intelligence platform?
When choosing a threat intelligence platform, you should consider factors such as the platform's capabilities, scalability, integration with other security solutions, and ease of use. Additionally, you should evaluate the vendor's reputation and track record, and consider the cost and resources required to implement and maintain the platform.
How do I integrate a threat intelligence platform with my existing security solutions?
To integrate a threat intelligence platform with your existing security solutions, you may need to use APIs or other integration tools provided by the platform vendor. Additionally, you may need to modify your security policies and procedures to align with the platform's capabilities.
What is an intelligence feed?
An intelligence feed is a stream of threat intelligence data that is provided by a vendor or other source. Intelligence feeds can be used by threat intelligence platforms to provide real-time threat information and support proactive threat detection.
What is open-source intelligence (OSINT)?
Open-source intelligence (OSINT) is information that is publicly available and can be used to support threat intelligence activities. OSINT sources can include websites, social media, and other publicly available information.
How do I use a threat intelligence platform to improve incident response?
A threat intelligence platform can improve incident response by providing actionable intelligence that can be used to more quickly and effectively respond to security incidents. Additionally, the platform can help automate certain incident response tasks, such as threat triage and remediation.
How do I measure the effectiveness of a threat intelligence platform?
To measure the effectiveness of a threat intelligence platform, you can track metrics such as the number of threats detected, the time to detect threats, and the number of successful remediation actions. Additionally, you can measure the platform's impact on overall security posture and the reduction in the number of security incidents.