We may earn a commission if you make a purchase through the links on our website.
Active Directory: Guide to Terminology, Definitions & Fundamentals!
UPDATED: September 29, 2022
Before Active Directory existed, if you needed to get a shared file in a network, you had to know the name or IP of the server, the path of the file, and its name.
Although this solution works for small networks, it is not scalable as the network grows.
A directory service helps solve this problem by mapping all the names of network resources such as shared files, folders, printers, servers, etc., to their particular address.
Today, a directory service like Active Directory (AD) is of paramount importance to an organization’s network, especially the large ones.
AD supports almost all of the mission-critical processes and applications like resource provisioning, capacity planning, security, network services, resource management, and more.
In this article, we made a list of the essential terms and concepts in the Active Directory world.
If you are a beginner in Active Directory, this list can help you get a good foundation on the key concepts.

Active Directory Fundamentals
Directory Service
A Directory Service is an information store built on a hierarchical structure.
It allows easy and quick storage, search, and management of resources within a network.
Each network resource is considered an object.
What is not?
It is important to notice that a directory service is more than a database.
It is a “service,” as the name implies.
Whereas the database is the physical data store accessed and stored in a computer system, the directory service uses the database to request and get the objects’ information.
Active Directory (AD)
Active Directory (AD) is a directory service for Windows domain networks.
It comes with any Windows Server that has the Active Directory Domain Services role (AD DS) installed.
AD is primarily used to store, give permissions, and manage information about users and their resources.
AD can store information as objects. An object is a resource within a network such as user accounts, passwords, computers, applications, printers, file/folder shares, security groups, and their permissions.
The Windows Domain Controller (DC), which is the server running the AD DS role, is the software/hardware that provides the AD set of services.
The primary function of a domain controller is to authenticate and authorize all users and their resources into a Windows domain network.
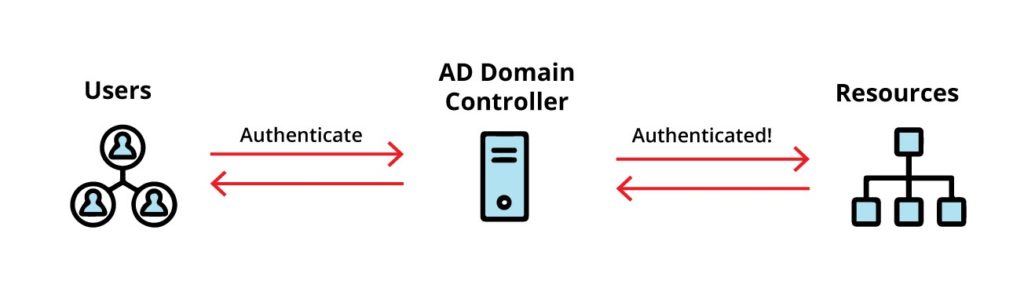
The best example of AD is when a user signs in to a computer that is part of a Windows domain.
AD checks the credentials against a database, if the username and password are valid, the user can log into the computer.
Related Post: Best Active Directory Monitoring Tools and Software
Lightweight Directory Access Protocol (LDAP)
Lightweight Directory Access Protocol (LDAP) is an open and multi-vendor protocol used for accessing and authenticating directory services.
It provides the syntax for applications and systems to interact with the directory services.
In other words, LDAP provides a way to communicate with a directory service. Active Directory uses LDAP version 2 and version 3 as access protocols.
To provide authentication, LDAP works with a client/server model and runs over the TCP/IP stack.
It supports Kerberos authentication, Simple Authentication Security Layer (SASL), and Secure Sockets Layer (SSL).
Active Directory Web Services (ADWS)
The Active Directory Web Services (ADWS) was introduced with Windows 2008 R2.
It allows remote management of any local Active Directory domains, Active Directory Lightweight Directory Services (ADLDS) instances, and Active Directory Database Mounting Tool instances.
ADWS uses the WS protocol over port 9389, and it is not bounded to HTTP ports such as 80 or 443.
Directory System Agent (DSA)
An Active Directory instance is made up of its database and a program known as the Directory System Agent (DSA).
This program, which is a collection of services and processes, gives access to the data store and services that the LDAP requests.
The DSA is the one that provides access to a portion of a directory requested by a Directory User Agent.
Active Directory Structure
Active Directory organizes all your networked resources in a logical structure.
This logical model is independent of the physical structure of the network.
In other words, AD is not concerned about the network topology or the number of domain controllers; it just structures resources logically.
So rather than finding a resource by its physical location, AD allows users to find it by its name.
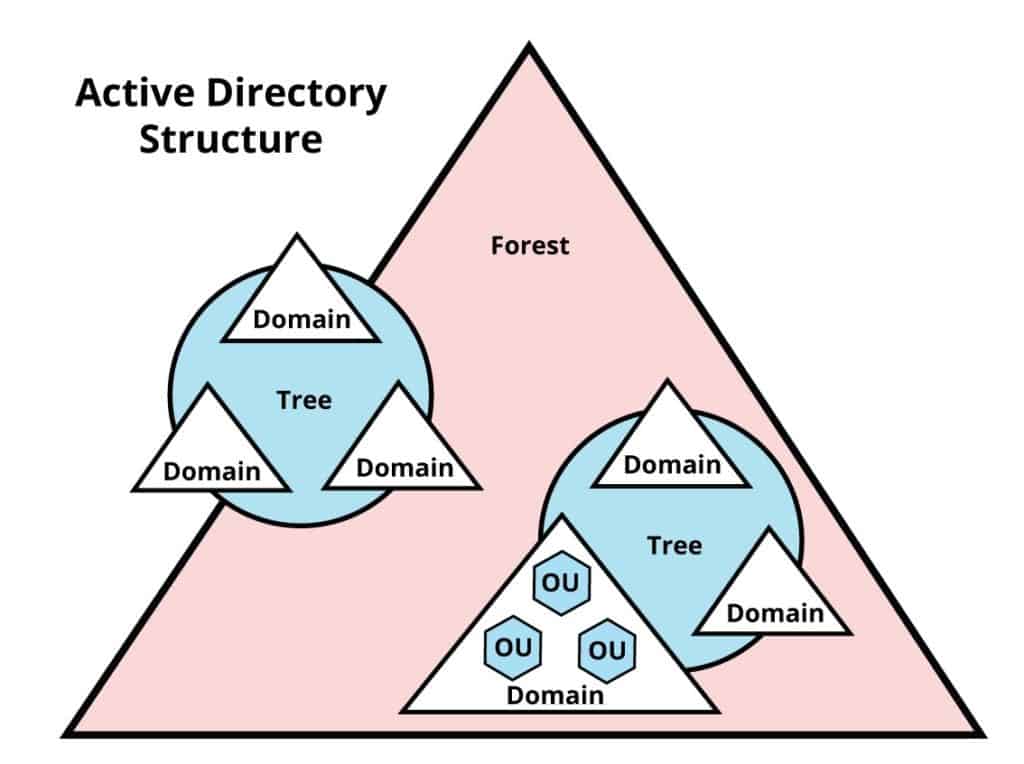
Active Directory allows you to organize network elements like users or computers into the hierarchical logical structure.
At the top of the hierarchy is the Forest, followed by Trees, which hold one or more domains.
Within a domain are the Organizational Units (OU).
Active Directory Objects
The Active Directory structure is formed by groupings of information, also referred to as objects.
Each object represents a unique network entity such as a user or computer, and it is described by a set of attributes.
For example, a user object can be specified by name, ID, address, telephone, and more.
Objects fall into two different categories:
- Resources
- Security Principals
The objects within the resources category can be printers, computers, or other shared devices.
Objects within the security principals category are users, passwords, groups, etc., or any object that needs to be authenticated, or that can be given permissions.
AD allocates a unique Security Identifier (SID) to each of these security principals objects.
The SID is used to allow or deny access to the object to the resources within a domain.
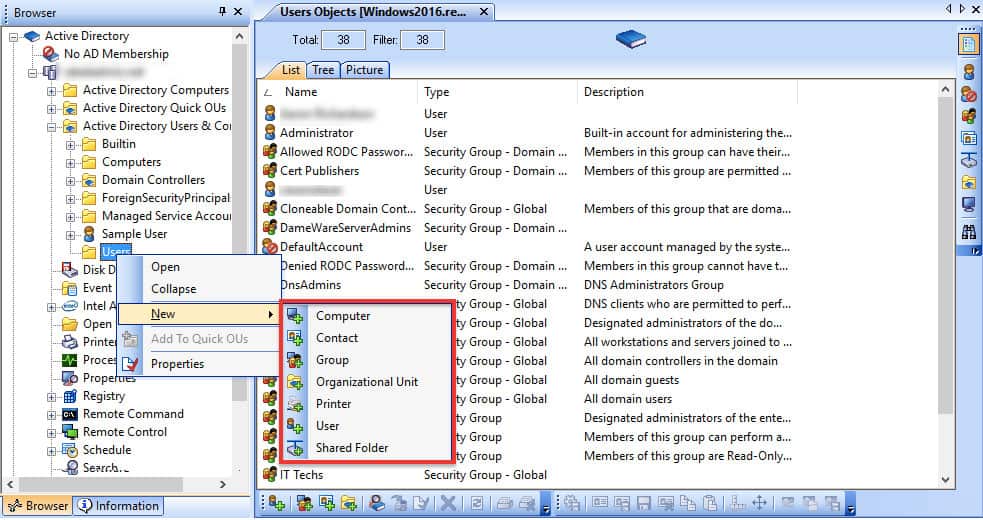
The Objects Supported by default by Active Directory:
- Users These are the objects assigned to individuals who need access to the domain resources. A user account has a user name and a password.
- Computers It represents a workstation or server within the domain.
- Contacts It contains information about third-party contacts. This object does not have a SID, so it doesn’t belong to the domain.
- Groups These objects represent a collection of user accounts, computers, or contacts. There are two types: Security and Distribution groups. Groups ease the management of many objects into a single unit.
- Shared folder This object is mapped to a server share and is used to share files throughout the entire network.
- Printer This object corresponds to a shared printer within the domain.
- Organizational Unit (OU) This type of object is a container that can include other objects like users, computers, or groups from the same domain. An OU is used to store similar objects and make their management easier. It is also used to apply group policy settings and permissions to the entire container.
Organizational Units vs Groups
It is important to highlight the differences between Object Groups and Organizational Units (OUs).
Groups were designed to Allow or Deny access to a resource while an OU is intended for object control, mainly through Group Policy (GPO) or permissions.
Another distinction is that groups use SIDs, while OUs don’t use SIDs (they can’t be placed into a group).
User Naming Attributes
Security in Active Directory can be improved using a set of user naming attributes to help identify user objects like logon name or ID.
The following are important Naming Attributes in AD:
- UserPrincipalName (UPN) It is the primary logon name for the user. By convention, the UPN uses the email address of the user.
- ObjectGUID It is a unique identifier of the user. In AD, the ObjectGUID attribute name never changes and remains unique even if the user is removed.
- SAMAccountName It is a logon name that supports the previous version of Windows clients and servers.
- ObjectSID This is the Security Identifier (SID) of the user. This attribute is used to identify a user and its group membership during security interactions with the server.
- SIDHistory This is the previous SIDs for the user object.
Domains
Domains are the core structural units of Active Directory. They are a collection of objects formed by a database using the object ID information. An AD domain can have several sub-domains, also referred to as child domains.
A domain uses the client-server communication model. This model allows security as you can assign permissions from the domain (server) to different users or groups (clients). The domain controller uses security services that provide authentication and authorization to specific resources.
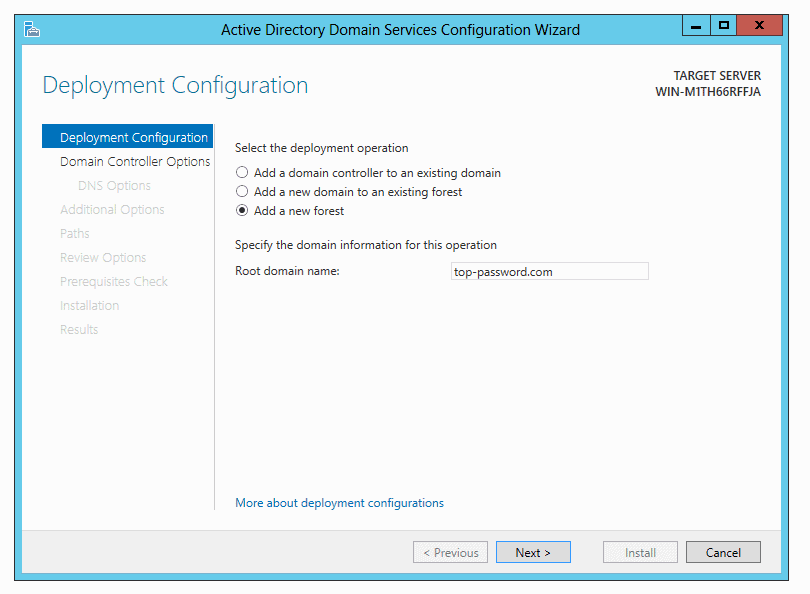
Common Characteristics of an AD domain:
- A Group of Domains makes up a Tree.
- A Group Policy can be configured for an entire domain, but it is more common to apply it to an OU.
- An AD domain can be identified with a Domain Name Server (DNS) name or a sub-domain.
When configuring AD for the first time, you would need to create a root domain name.
An example of an Active Directory domain name would be “ad-internal.company.com,” where “ad-internal” is the name you are using for your internal AD domain, and “company.com” is the name of your external resources.
Fully Qualified Domain Name (FQDN)
To name an object within a domain, you can use the Fully Qualified Domain Name (FQDN), which is the unique name of a host or computer on the entire domain.
The FQDN consists of the hostname and the domain name.
For example, the FQDN for a computer in the domain “sales-internal.company.com,” with the name “WORKSTATION-040,” would be “WORKSTATION-040.sales-internal.company.com.
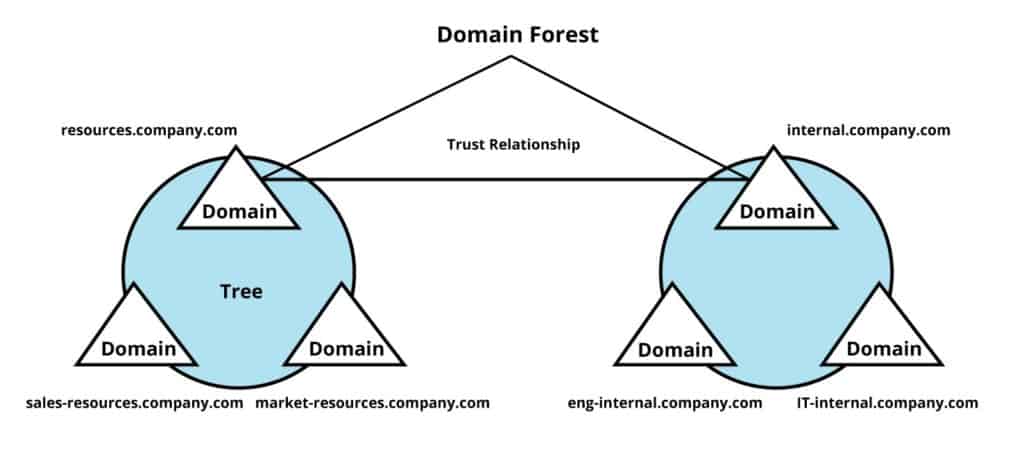
Trees
An AD Tree is a group of domains within the Active Directory network that share a common DNS naming structure.
The tree creates a logical boundary between multiple domains.
The “word” tree is used because each domain has precisely one parent, which creates a structure with a form of a hierarchical tree.
A collection of these trees form a forest.
Forests
An AD forest is the collection of one or more AD trees.
It is the top container in the hierarchical structure and creates a logical separation between trees.
It can consist of a single tree with one domain or several trees with multiple domains.
By default, the first domain created in AD will automatically generate a forest.
Trees within the forest share the same schema.
That means that all the contents within objects will be the same in all domains in the forest.
Another characteristic of a forest is that its domains trust each other by default.
Groups
An Active Directory Group is a collection of objects, such as users, computers, or contacts.
Groups allow easy administration and better security.
Instead of managing every single object individually, a manager can control all of them as a whole.
Groups are frequently used for assigning permissions to objects within a domain.
There are two types of groups in AD:
- Security Group: It is used to give or deny access to specific resources within a domain.
- Distribution Group: It is used to distribute emails and messages to the entire group. This group is not designed for providing access to resources.
Group Scopes
Either security or distribution object groups can fall into three different group scopes, Universal, Global, or Domain Local.
The group scope defines the location within the network where the group can be used.
The scope is the level at which the group will be reaching throughout the domain, tree, or forest. It can also help assign group members.
- Global Groups: Contains objects such as user and computer accounts in the local domain. These groups can be used to grant access to local objects to another domain, tree, or forest.
- Domain Local Groups: Can contain objects from any domain. The group members can only access resources in the local domain.
- Universal Groups: It has objects from other group scopes and any domain in the tree or forest as group members. The members of this group can access resources in any domain.
Active Directory Schema
The AD Schema describes the rules about the type of object class with certain attributes that can be stored in AD.
The schema is like a layout that defines the content and structure for these object classes.
Every object created in Active Directory is an instance of an object class. For example, the “User Object” is an instance of the “User Class.”
When a new user is created, it falls into the object class “User,” and it will require mandatory or optional attributes, according to the schema.
The AD schema is composed of various Elements:
- Schema Object Classes
- Schema Attributes
- Syntaxes
- Control Access Rights
Functional Levels
Active Directory Functional Levels are controls that determine which Active Directory Domain Services features can be used in the domain or forest.
These levels can also specify the version of Windows Server OS that can run on domain controllers.
As a best practice, when deploying the AD DS, set the functional levels for the domain and forest to the maximum value to allow the latest and best features available in Active Directory.
FSMO Roles
The Flexible Single Master Operation (FSMO) roles allow Domain Controllers (DC) to keep authenticating users and giving permissions without any interruption.
In other words, the responsibilities like authorization and authentication of a DC are separated into different roles and distributed across multiple DCs.
This separation of roles provides full redundancy in case one DC goes down.
There are five different FSMO Roles
- Schema Master An enterprise-level FSMO role. There is only one schema master in the entire forest, which is capable of handling schema changes.
- Domain Naming Master An enterprise-level FSMO role. There is only one domain naming master, which is in charge of managing domain names.
- Primary Domain Controller Emulator A domain-wide FSMO role. The DC with the PDC Emulator role is, the DC with the highest authority within the domain. This role deals with authentication requests, passwords changes, group policy objects, and also provides the time.
- Relative Identifier Master The RID is a domain-level FSMO role. It is in charge of keeping blocks of SIDs and assigning them to different DCs within the domain.
- Infrastructure Master It is a domain-level FSMO role that translates GUIDs, SIDs, and DNs between domains. This role gets references from other objects in other domains.
Active Directory Recycle Bin
The AD Recycle Bin is an additional feature that came with Windows Server 2012 R2's.
This feature allows you to restore deleted objects and their attributes.
For example, if you accidentally removed the user accounts within a domain, the recycle bin will allow you to restore them with group memberships, access rights, etc.
Read-Only Domain Controller
The Read-Only Domain Controller (RODC) is a server that stores an AD domain database read-only copy.
The primary purpose of RODC is to improve physical security in branch offices with the following functionalities:
- The read-only characteristic
- Protection of DNS server
- Password management and protection
- Admin role delegation
SYSVOL Folder
SYSVOL is a shared folder on each domain controller (DC).
It can store information from Active Directory and replicate it to other domain controllers.
SYSVOL provides the location where DCs replicate the data to each other.
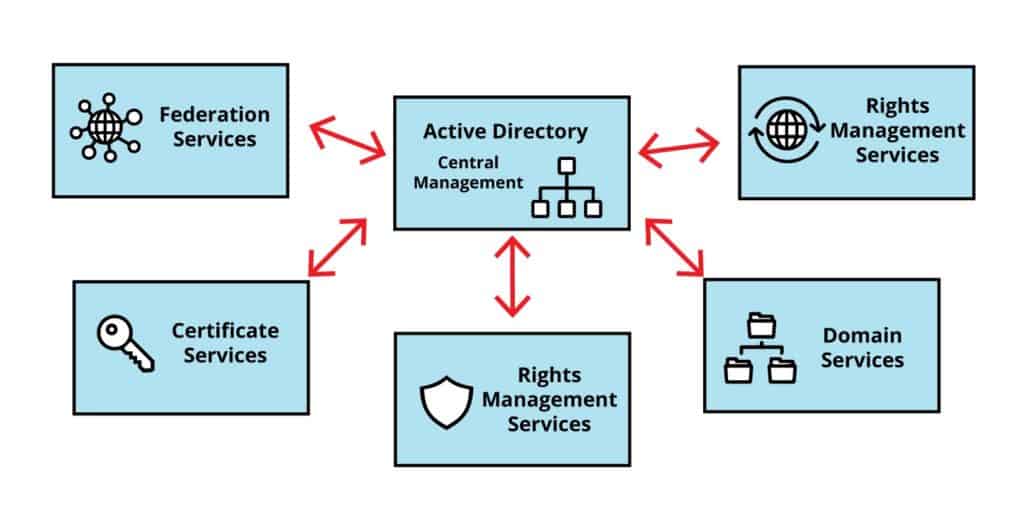
Active Directory Services
Active Directory provides multiple out-of-the-box services to manage identities, permissions, and access to a network’s resources.
The AD services available in Windows Server 2008 and Windows Server 2008 R2 are:
- Active Directory Certificate Services (AD CS).
- Active Directory Domain Services (AD DS).
- Active Directory Federation Services (AD FS).
- Active Directory Lightweight Directory Services (AD LDS).
- Active Directory Rights Management Services (AD RMS).
Active Directory Domain Services
Active Directory Domain Services (AD DS) is the most popular server role in Active Directory.
It is the directory service that provides the technology for storing directory data. It also makes this data available and manageable for all end-users.
Active Directory Federation Services
The Active Directory Federation Service (AD FS) is an identity management services solution.
It provides Single-Sign-On (SSO) access control for web applications, web sites, or multiple resources within a network.
The AD FS gives flexibility when accessing multiple resources. End-users only need to remember a set of credentials to use them all across these resources.
When a user signs in to a workstation, the authentication claim can be used by third-party applications on behalf of AD.
AD FS sends the authentication claim rather than credentials.
Active Directory Rights Management Services
The Active Directory Rights Management Services (AD RMS) is a data access control solution.
It protects documents like emails, Office docs, and web pages, using encryption. It can also enforce data access policies.
The AD RMS can let you deny/permit access to specific users, modify/read-only actions, limit certain operations, and more.
The software also encrypts and decrypts all digital content.
Active Directory Certificate Services
The Active Directory Certificate Services (AD CS) is a server role that lets managers generate and manage the Public Key Infrastructure (PKI), including digital certificates and signatures.
This tool helps you set roles and policies with the purpose of creating, managing, distributing, using, storing, and revoking certificates and public keys.
You can also automate certificate provisioning.
With AD CS, you can use the existing identity data found Active Directory to register new certificates. You can also set AD group policies to enforce specific certificates on particular resources.
Active Directory Lightweight Directory Services
Active Directory Lightweight Directory Services (AD LDS) is an LDAP directory service for applications.
This service is independent of the domain limitations of AD DS.
In other words, it is not bounded to Active Directory, its domains, and forests.
You can run this service on any stand-alone server. AD LDS provides its data store and the services for accessing it.
Active Directory DNS
The functionality of the Active Directory is tightly related to the Domain Name Server (DNS).
To run your first domain controller, you’ll be required to install AD and the DNS role.
You’ll need DNS for the translation of hostnames into IP addresses within your domain.
All the clients in AD use DNS for finding the domain controllers, and the domain controllers use it to talk to each other.
The DNS namespace is used across the Internet, but the Active Directory namespace is used inside the private network.
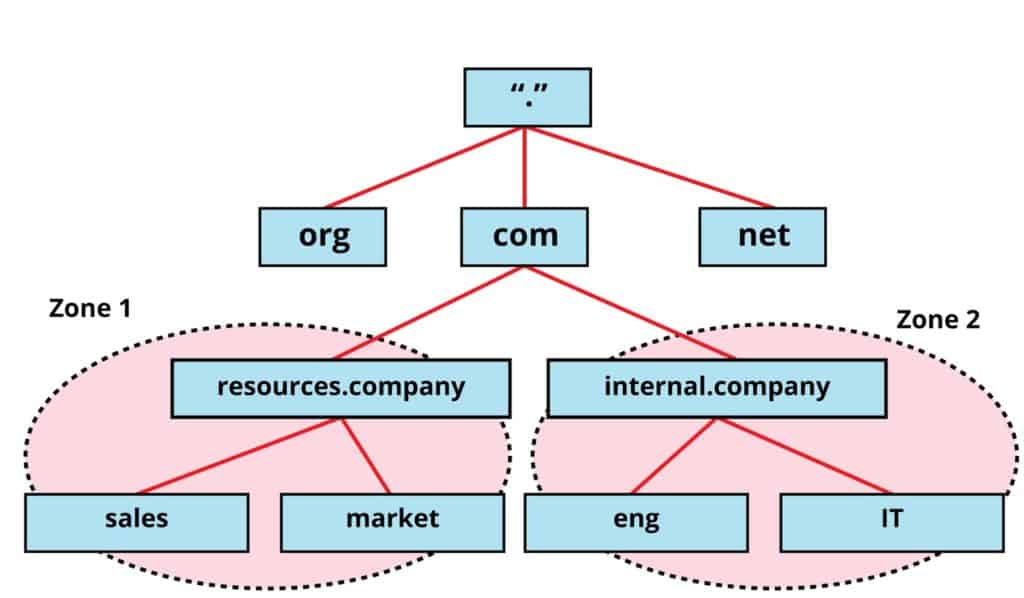
DNS Zones
A DNS Zone is a section of the DNS namespace.
They divide the namespace for administrative and redundancy reasons.
DNS Zones are composed of resource records, which are blocks of IP and name information used to resolve DNS queries.
Some common resource types are A, AAA, CNAME, MX, NS, and more.
There are multiple zone types in AD; the most common is Active Directory-integrated DNS zone.
The other zones are Primary, Secondary, Stub, Forward Lookup, Reverse Lookup Zones, and Zone transfers.
Dynamic DNS
While DNS maps hostnames to static IP addresses, Dynamic DNS (DDNS) maps names to dynamically assigned IP addresses, from services such as DHCP.
DDNS automatically updates the DNS server with new information when there are changes in IP addressing.
Clients in an AD domain controller use DDNS to register and update their resource records dynamically.
For example, if a client moves from one LAN to another, its IP address will likely change, DDNS will automatically adjust the new configuration in the DNS.
SRV Records in Active Directory
The Service (SRV) record defines the location of servers that host particular services.
In Active Directory, when clients want to locate a domain controller for a given service, they query the SRV records in DNS. When a new domain controller is created, its SRV records registers in the DNS server.
DNS Forwarders
DNS Forwarders are servers that forward DNS queries for addresses that do not belong to a zone or cannot be resolved locally.
These types of servers help send all queries of unknown Internet browsing or public addresses to DNS outside the network.
Without a DNS forwarder, the DNS server would have to query the root DNS every time there is an unknown address.
DNS Aging and Scavenging
Stale resource records that were added via DDNS or manually recorded are accumulated over time.
DNS aging and scavenging is a service that solves this problem. It performs automatic cleanups and stale resource records removals from the DNS database.
Root Hints
Root Hints are DNS files kept on a server to provide a list of resource records that can be used to resolve hostnames that the local DNS server cannot.
The roots hints file contain names and IP addresses of the authoritative DNS servers for the root zone.
The difference between DNS forwarders, which also help resolve external hostnames, is that Root Hints has a list of authoritative name servers while DNS forwarders only have a list of DNS servers that can help resolve a query.
Dynamic Host Configuration Protocol (DHCP)
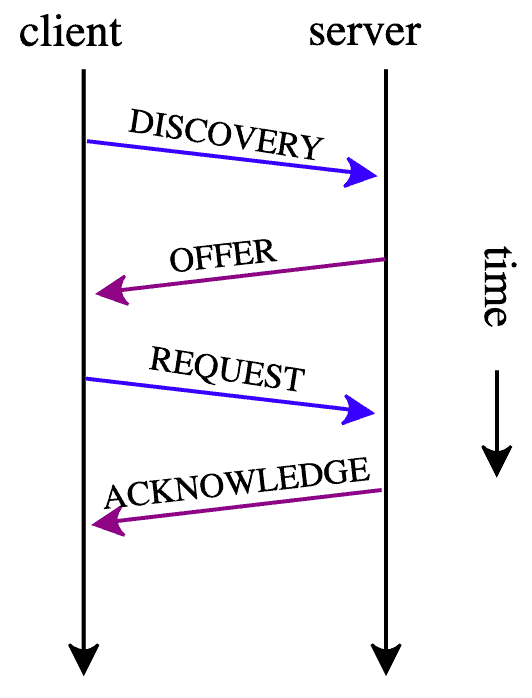
The DHCP is a network management protocol used for dynamic address allocation. The protocol relies on the DHCP server to automatically provision IP addresses, default gateway, and other information to DHCP clients. Active Directory depends on a DHCP server to start responding to client requests.
When a client using DHCP connects to a network, it instantly sends a DHCP discovery to find the server, which in turn sends a DHCP offer with an available IP address.
DHCP Scope
The DHCP Scope is an IP address range that is available for distribution to computers, or DHCP clients on a specific subnet.
The DHCP scope is composed of the following parts:
- The IP address range The range of the DHCP scope is defined by a start IP address, an end IP address, and the subnet mask.
- IP address exclusion Within a DHCP scope, you can also exclude non-DHCP clients. A computer with a static IP address must be excluded within the scope to avoid any IP address conflict.
- Lease Duration This defines the lease time of the set of addresses. In other words, how long an IP address is given to a client before it goes back to the IP address pool.
- Other settings Within the scope, you can also define the default gateway, DNS, and WINS configuration.
IP Address Pools
The DHCP Scope, including exclusions, determines an IP address pool.
The DHCP server, with its already established DHCP scope, starts to assign IP addresses from the pool.
When a DHCP client leaves the network, the IP address is returned to the pool. If a pool is exhausted, the size of the IP address range must be expanded.
DHCP Reservations
A DHCP server can be configured to reserve and allocate permanent addresses to specific clients.
The server reserves the address in the IP address pool and ensures that only the defined client with a MAC address, receives it.
These reservations are helpful to avoid IP conflicts.
They are often used for printers, servers, VIP workstations, etc.
DHCP Filtering
DHCP filtering is a function of the server used for access control.
With this feature, you can explicitly allow and deny DHCP requests to specific clients with MAC addresses.
DHCP filtering prevents unknown clients from being allocated a dynamic IP address by the DHCP server.
DHCP Failover
DHCP failover is a Windows Server 2012 feature that ensures fault tolerance and load balancing for DHCP requests.
In a DHCP failover scenario, two (or more) DHCP servers manage the same IP pool.
If one DHCP server fails, the load is automatically taken over by the other server.
In load balancing, the two (or more) servers share an entire load of DHCP client requests, while also allowing fault tolerance.
Active Directory Replication
Replication in Active Directory is the process that helps ensure that the information between domain controllers remains consistent. If a change is made in one domain controller, the AD replication methods help the other DCs to synchronize in time.
Subnets
A subnet is a logical portion of a network that is usually connected by a router or switch.
Each subnet within the network has a different TCP/IP addressing scheme.
In Active Directory, subnets are used by clients and domain controllers for logon and replication purposes. They help domain controllers to determine the best route between them, during replication.
Active Directory Sites
Sites are objects within Active Directory that represent one or more TCP/IP subnets.
Within each AD site, there are domain controllers that are associated with connection objects.
These sites help in the configuration of replication by taking into account the accessibility of the network’s physical resources.
Connection Object
It is an AD object that serves as a replication connection between a source and a destination domain controllers, within a site.
The Connection Object determines which domain controller replicates with which other, specifies their schedule, and also their replication transport type.
KCC
The Knowledge Consistency Checker (KCC) is a directory service utility that guarantees consistency in the directory database.
It runs on all domain controllers and creates the replication topology of the entire forest.
The KCC process can generate individual topologies if the replication is in a site or between sites.
Site Link
Active Directory site links are logical paths created to connect sites and are used during replication.
The site link allows the KCC to create connections between domain controllers.
A single site link object can represent a group of sites that can talk to each other using the same network type.
Site Link Bridge
The Active Directory Site Link Bridge is an object that represents a logical connection between site links.
It provides a transitive path between two and more disconnected site links.
A site link bridge can allow domain controllers that are not linked together to replicate each other.
Global Catalog
The Global Catalog (GC) is a data storage service for a Domain Controller (DC). A DC running the GC is known as the Global Catalog Server.
The GC server stores full copies of the objects within the directory of a domain. It can also save a partial copy of all objects in the entire forest.
With this partial replica of the forest, users and applications can quickly search and find objects within any domain.
The GC provides a catalog where users can search for objects in a multi-domain environment.
Universal Group Membership Caching
Universal Group Membership Caching (UGMC) stores membership data of the universal groups in the cache.
The UGMC helps when the GC is not available, or the Universal Groups are being used, which helps relieve network bandwidth utilization and also to improve user logon times.
The UGMC helps keep replication traffic to a minimum.
Active Directory Replication Traffic
The traffic replication throughout Active Directory can consume precious bandwidth.
The KCC creates different replication topologies depending if replication is occurring intersite or intrasite.
Setting a CG at each site helps reduce replication traffic. There are two types of traffic.
- Intra-site Replication When domain controllers are part of the same site, the replication of the AD database can happen much faster.
- Inter-site Replication When domain controllers belong to different sites. Optimizing this type of replication can help to reduce the traffic between sites.
Active Directory Security
Kerberos
Kerberos is an authentication protocol.
It provides security in client/server communication applications using cryptography.
Active Directory uses Kerberos to provide authentication mechanisms between server and client.
It authenticates users and gives access to a domain.
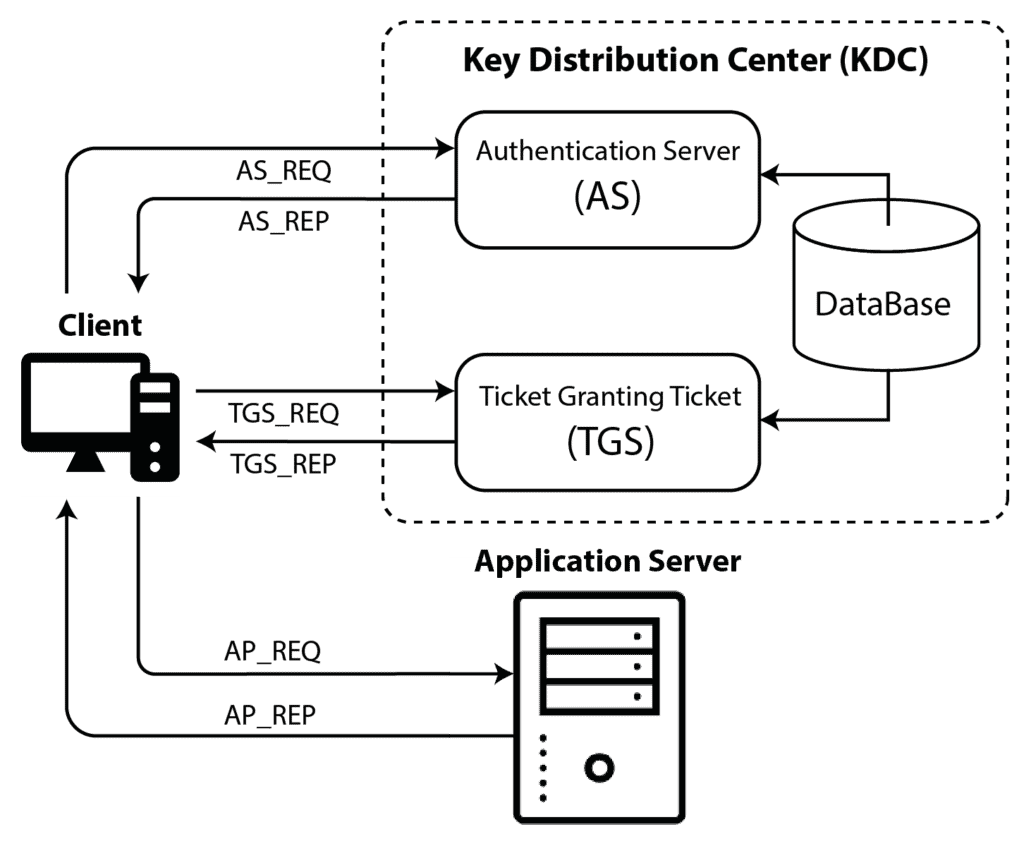
The three main elements in a Kerberos system are:
- The Key Distribution Center (KDC) The KDC service is the core of the Kerberos server that issues all the tickets. The service runs on all Active Directory domain controllers. When an AD client authenticates with KDC, it issues a TGT.
- Ticket Granting Ticket (TGT) It is an authentication file that contains the user’s IP, a validity period, and a TGT session key. The TGT is encrypted during the Kerberos authentication procedure.
- The Ticket Granting Service (TGS) This service provides the TGTs and other tickets to the systems.
Service Principal Names
The Service Principal Name (SPN) is a unique identifier used in the Kerberos authentication process.
An SPN links a network controller service instance to a logon account.
An SPN can be used to authenticate services to a client application when the service account or user account is not being used.
NTLM
The NT LAN Manager (NTLM) is another authentication protocol that uses the challenge/response mechanism.
NTLM was widely used before Kerberos came by.
Although NTLM is still supported on AD, Kerberos is the preferred choice for authentication.
NTFS Permissions
NT File System (NTFS) Permissions are used to grant or deny access to files or folders on Microsoft Windows NT systems.
NTFS permissions can be enforced to local or network users.
These permissions are granted or denied to a user at the logon phase.
The NTFS permissions are:
- Full Control
- Modify
- Read & Execute
- Read
- Write
Share Permissions
Share Permissions have the same function as NTFS Permissions, which is to prevent unauthorized access.
But the main difference is that Share Permissions only manage access to files and folders on shared resources.
These types of permissions can be used with FAT, FAT32, and NTFS.
The types of share permissions are:
- Read
- Change
- Full Control
Windows Access Control Lists
The Microsoft Windows Access Control Lists (ACLs) are a core element in the security model.
These lists can provide a set of permissions to help control access to network resources.
Every object in Windows systems can be linked to an ACL. There are two types of ACLs in Windows, Discretionary (DACL) and System (SACL).
ACLs are formed by Access Control Entries (ACEs), which are statements to allow or deny access to a group or individual to resources.
The main difference between DACL and SACL is between their ACEs.
- Discretionary Access Control List (DACL) It is a set of permissions that can be linked to an Active Directory object. The DACL specifies the users and groups that can access such an object. It also determines the type of actions that can be performed over the object.
- System access control lists (SACLs) This list helps perform audits of users and groups that attempt (successfully or failed) to access an AD object.
Fine-Grained Password Policy
A Fine-Grained Password Policy (FGPP) is an Active Directory object that is used for deploying password and account lockout policies for domain users.
With FGPP, managers can enforce password policies such as type of characters, minimum password length, or password age to an AD domain.
Group Policy
Group Policy (GP) is a Microsoft Windows tool that allows central management of user and computer accounts, OS configuration, and apps/user settings.
Group policies are used within an Active Directory environment and can be used to set password policies, lock screen, restrict access to certain portions in the system, force a home page, even run specific scripts, among many more.
Group Policy Objects (GPO)
Group Policy Processing is the procedure of sending and receiving policies.
Once GPOs are applied to any user or computer object within Active Directory, GP will automatically send all the settings to that object.
The client will receive the settings and put them on the computer.
The GPO can be divided into two parts the user settings and the computer settings:
- User Settings: GPO that applies a configuration to user objects.
- Computer Settings: GPO that applies a configuration to computer objects
Group Policy Processing
Group Policy Processing is the procedure of sending and receiving policies.
Once GPOs are applied to any user or computer object within Active Directory, GP will automatically send all the settings to that object.
The client will receive the settings and put them on the computer.
Group Policy processing follows a four-level hierarchy:
- Local policy
- Site-level policies
- Domain-level policies
- OU-level policies
GPO Inheritance
GPOs can be associated local, to sites, domains, or OUs.
By default, GPOs linked to objects are inherited by their child objects.
The GPO inheritance allows admins to configure a common set of policies to the site-level, domain-level, and OU-level in the four-level hierarchy.
This GPO Inheritance can be broken with the Block Inheritance option. This option can help administrators to change the inheritance behavior of GPOs within a domain or OU.
GPO Enforced
The GPO Enforced (or No Override) is a setting enforced on a GPO that prevents it from being superseded by other GPOs.
This setting helps avoid conflicting GPOs with higher precedence in the four-level hierarchy.
Resultant Set of Policy (RsoP)
The Resultant Set of Policy (RsoP) is a Microsoft Windows utility that simplifies the GPO management and provides capacity planning.
The RsoP is like a report that includes all the group policies within Active Directory applied to all users and computers.
This report can show how GPOs affect the network.
Group Policy Preferences
Group Policy Preferences is a set of Group Policy extensions that increase the functionality of GPOs.
These extensions deliver preference settings for AD objects such as computers, servers, printers across a domain.
With these settings, administrators can configure and manage an extended number of OS and application settings, such as install printers, scheduled tasks, configure registry, set power settings, configure file/folder permissions, and more.
Group Policy Administrative Templates
The GP Administrative Templates are Group Policy features used for centralized management of users and machines.
The templates are files, with extensions .ADM or .ADMX, which are used by Group Policies to describe the registry keys that need to be updated.
When using administrative templates, you can modify machine and user portions of the registry in computers.
Active Directory Management Consoles
Active Directory management consoles can be used for daily AD maintenance and operation.
Some of these consoles are Microsoft-proprietary, while others are third-party solutions that offer different management capabilities, such as automation, reporting, integration with other services, and more.
MMC Snap-ins
The Microsoft Management Console (MMC) is used to create and open consoles, which can help manage all the IT components within a Microsoft Windows network.
The MMC hosts the snap-ins, which are administrative tools that can be used from a single interface.
Almost all Microsoft management tools can be implemented as MMC snap-ins. But MMC also supports some third-party snap-ins using the MMC API.
Active Directory Users and Computers (ADUC)
ADUC is the most popular MMC snap-in for managing AD.
It is used for day-to-day domain administration, including objects, OUs, and their attributes.
The ADUC (dsa.msc) console is installed by default during the AD DS installation.
Active Directory Administrative Center (ADAC)
The ADAC console was introduced with Windows Server 2012.
This console can be used to deploy and manage user accounts, computers, groups, OUs, and more.
The ADAC includes improved management features over ADUC, like Active Directory Recycle Bin, Fine-Grained Password Policy, and Windows PowerShell History Viewer.
Active Directory Domains and Trusts
The Active Directory Domains and Trusts is an administrative console that allows you to manage trust relationships between domains and forests.
This console also helps you to raise the domain and forest functional levels and manage UPN suffixes.
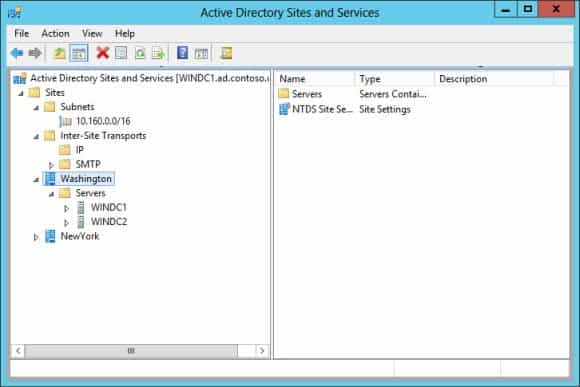
Active Directory Sites and Services (ADSS)
The ADSS is an MMC snap-in console that is mainly used for managing site replication and other components such as topology objects, subnets, connection objects, the global catalog, and universal group caching.
Active Directory Service Interfaces Editor (ADSI Edit)
The ADSI Edit is an advanced Active Directory object editor. It allows viewing, modifying, and removing AD objects, and any of their attributes within a forest.
ADSI Edit is often compared to the Windows Registry Editor, due to its level of fine-grain edition.
This tool is designed to access data that is usually not available in consoles such as ADUC.
Local Users and Groups
Local Users and Groups is an MMC snap-in console (under Computer Management) that allows AD administrators to manage and secure local computers.
It gives data access control through a set of permissions and rights for a local or group account on the computer.
DHCP
The MMC snap-in console (dhcpmgmt.msc) that is used for DHCP management.
With this console, you can configure IP address range, lease time, DNS and WINS server, etc.
DNS
The DNS MMC snap-in (dnsmgmt.msc) console allows you to manage DNS configuration.
With this console, you can create, browse, and manage DNS zones and resource records.
Group Policy Management Console
The Group Policy Management Console (GPMC) is an MMC tool (gpmc.msc) that allows administrators to manage Group Policy Objects (GPOs) from a single console.
With GPMC, administrators can deploy, manage, view, and troubleshoot any GP implementation.
Want to Learn More About Active Directoy?
A great resource to learn more about Active Directory is from the Microsoft Active Directory Knowledgebase, which is the official source to learn everything about Active Directory.
Third-party Software for Monitoring and Troubleshooting AD Performance
SolarWinds Server & Application Monitor
Third-party software allows you to extend the functionality of AD.
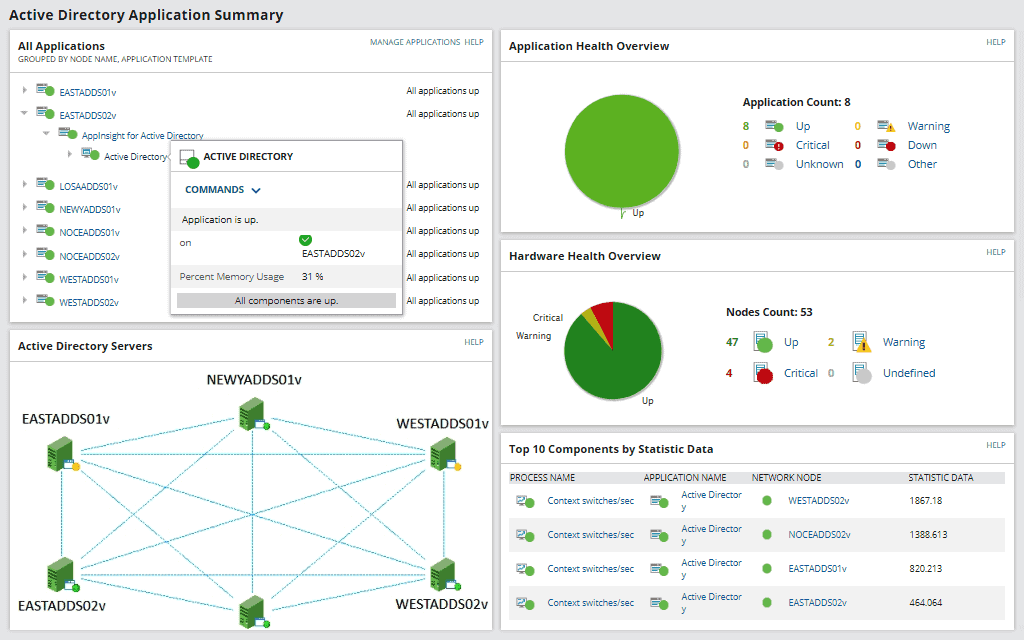
With tools such as SolarWinds Server & Application Monitor (SAM), you can not only monitor and troubleshoot AD performance but also keep track of all the applications, servers, operating systems in your IT infrastructure.
SAM helps you to monitor the state of each Domain Controller (DC), the AD replication status, and find issues between sites and DCs.
Some SAM built-in features:
- Display site details
- View Windows logon and events
- Keep track of replication
- Monitor DCs
- Browse through FSMO roles
SAM gives some features that are not found on AD as well, such as a friendly dashboard, reporting, alerting, and even some automation features.
Pros:
- Takes a holistic approach to server performance and health monitoring
- Supports auto-discovery that builds network topology maps and inventory lists in real-time based on devices that enter the network
- Supports both SNMP monitoring as well as packet analysis, giving you more control over monitoring than similar tools
- Uses drag and drop widgets to customize the look and feel of the dashboard
- Robust reporting system with pre-configured compliance templates
Cons:
- Designed for IT professionals, not the best option for non-technical users
Below is a picture of how SAM looks like when monitoring AD.
Where to get it?
SolarWinds also offers a freeware called the Free Admin Bundle for AD, which is a lightweight piece of software that helps you find and remove inactive users and computers, and add users in bulk in AD. The price for the full “SAM” starts at $2,700.
But before buying a license, SolarWinds gives you a free ride.
You can download the 30-days free trial of SAM.
Did we miss an important concept or term in Active Directory? What would you like to learn deeper?