We may earn a commission if you make a purchase through the links on our website.
The Best Tools for Penetration Testing
UPDATED: October 23, 2023
A penetration test (pen test) can be performed by hiring a certified professional or someone with strong ethical hacking skills to find vulnerabilities and attempt to breach them. The pen tester will assess the security by following the steps: defining the scope, reconnaissance/intelligence, scanning, finding vulnerabilities, gaining access, and reporting.
Every step along this process is executed with the help of a variety of penetration testing tools and a lot of skills.
Here is our list of the best penetration testing tools:
- CrowdStrike Penetration Testing Services A consultancy service that provides white hat hackers to perform penetration testing from remote locations, using a range of scenarios. Access a 15-day free trial of Falcon Prevent.
- Indusface Penetration Testing Services A consultancy service that provides a professional team of penetration testers to assess the security of applications, and APOs.
- Invicti Security Scanner A comprehensive vulnerability management solution capable of scanning for web application vulnerabilities (SQL injection, XSS, etc), and integrating with tracking systems and CI/CD pipelines software.
- Intruder Automated Penetration TestingA cloud-based vulnerability scanner that helps automate pen testing for websites and web applications.
- Acunetix Scanner A web application vulnerability scanner that checks a web application or website and attempts to find vulnerabilities like SQL injection, XSS, or more.
- Nmap and Zenmap CLI and GUI network mappers, capable of scanning the network via simple ping sweeps or intense TCP/UDP scans.
- Wireshark A robust network protocol analyzer capable of providing deep information about network protocols, packet information, etc.
- Metasploit Framework A powerful tool to test the network and server vulnerabilities. It uses pre-packaged exploit code (payload) to attempt to bypass security measures.
- John the Ripper A password-cracking software used for finding weak spots. It can run on brute force or dictionary attack.
- Aircrack -ng A suite of WiFi network security assessment tools. It can monitor, capture packets, test security, and crack passwords.
- Nessus A free and open-source remote vulnerability scanner for servers, network devices, OS, databases, and hypervisors.
- Kali Linux A complete distribution that gives you access to more than 600 tools.
- Plus Six Worthy Mentions Other tools that didn’t make it to the top list, but are worthy mentions: BeEF, W3af, THC Hydra, Maltego, SQL Map, and Nikto.
Some manual penetration testing tools require a high level of expertise to use them. But other testing tools are automated vulnerability scanners, which are easier to use and can turn out to be much more efficient for particular scenarios. Combining both types of tools is the best strategy.
On one hand, a security professional with knowledge on how to use these “manual” tools could be able to find the most complex and sophisticated vulnerabilities— where no automation tool is capable of. But automatic vulnerability scanners can help the pen test to be faster and continuously monitor for vulnerabilities. Automatic vulnerability scanners can also find vulnerabilities such as development mistakes, misconfigurations, etc, much faster.
Our methodology for selecting a penetration testing tool:
We reviewed the market for penetration testing systems and analyzed tools based on the following criteria:
- Define the scope of penetration testing. Establish which systems, applications, or networks will be tested as well as any applicable constraints like time or resources.
- Determine whether any compliance standards like GDPR, PCI DSS, or HIPAA need to be met prior to commencing penetration testing.
- Research both open-source and commercial options.
- Study tool categories such as network scanning, web application security scanning, and wireless network security scanning.
- Investigate functionalities like vulnerability scanning, exploit development reporting, and ease of use.
- Be certain your tools are compatible with existing systems, frameworks, and technologies.
- To get maximum value out of commercial tools while staying within your budget constraints.
The Best Tools for Penetration Testing (& Six Worthy Mentions)
1. CrowdStrike Penetration Testing Services
Although this list is all about penetration testing tools, this entry isn’t a tool but a consultancy service. If you don’t have the confidence to perform penetration testing yourself, use an external team instead. CrowdStrike's flagship tool which this service is attached to is Falcon Prevent.
Key Features:
- Reduction in Surface Attacks: Implementing WAFs to filter and monitor incoming traffic, cross-site scripting (XSS), endpoint detection and response (EDR) tools.
- Gain Visibility of Security Gaps: Includes conducting comprehensive risk assessments, vulnerability checks, due diligence assessments, and security audits to evaluate the security posture.
- Prioritizing Security Budgets: Allocate budgetary resources to ensure compliance with relevant laws, regulations, and industry standards, such as GDPR, HIPAA, PCI DSS, and others.
Why do we recommend it?
CrowdStrike Penetration Testing Services are highly recommended due to their ability to simulate real-world attacks on various IT components. By testing the detection and response capabilities of people, processes, and technology in your environment, CrowdStrike helps identify vulnerabilities within it. This proactive approach allows organizations to reduce attack surfaces against sophisticated threats prevalent today and strengthen security posture against evolving cyber threats.
Consultancy penetration testers can usually perform a better job at probing the security of your system than you or your team can. This is because they approach your system with fresh eyes, they have years of hacking experience, and they don’t have the reservations that you would have about being gentle. They will truly expose your system’s weaknesses.
Who is it recommended for?
Organizations seeking to optimize their security budgets effectively should utilize this tool as part of their toolbox. Pinpointing vulnerabilities and risks that threaten sensitive internal resources, helps prevent wasteful expenditures across the broader security landscape. Security professionals appreciate its ability to pinpoint areas of escalation and bypass, highlighting vulnerabilities within permissions, services, and network configurations – ultimately aiding teams in prioritizing resources where they're most needed and ultimately improving overall security posture while decreasing long-term costs.
Pros:
- Broader Visibility: Users can get broader visibility of events occurring within their network.
- Uses AL/ML: Uses AI/ML-based malicious activity detections.
- Restricts Unauthorized Usage: Helps prevent unauthorized use of USB storage devices within an organization's network or computer systems.
- Continuous Monitoring: IDP system continuously monitors network traffic and system logs for signs of suspicious behavior, such as unauthorized access attempts, unusual data transfer patterns, or known attack signatures.
Cons:
- False Alerts: If some malicious app uses Microsoft's signed binary like one drive, cmd, or w script, CrowdStrike would tag the Microsoft binary as malicious and fail to provide the actual file that tried to execute these.
Price and Trial: CrowdStrike Penetration Testing Services is a consultancy that quotes a price after a consultation over requirements rather than publishing a price list. To figure out your network requirements, you can access a 15-day free trial of CrowdStrike Falcon Prevent.
2. Indusface Penetration Testing Services
Indusface Penetration Testing Services is provided by a team of white hat hackers that will probe your system to discover the types of damage that could be implemented by real hackers. The group will test applications, such as web applications and mobile apps, and APIs, including microservices.
Key Features:
- Managed Dynamic Application: Supplies an extensive managed dynamic application security testing (DAST) solution.
- Cloud-Based Service: Offers daily web application monitoring, vulnerability scanning for systems and apps, and malware detection with no touch required.
- Real-World Attack Simulation: The team uses OWASP for web app penetration testing to detect real-world cyber attacks.
Why do we recommend it?
We recommend Indusface Penetration Testing Services because of its unique combination of manual and automated scanning capabilities for penetration testing. Built from the ground up, Indusface enables penetration testing teams to craft complex scripts for comprehensive findings without limitations imposed by automated tools or pricing lists. Clients receive reports that include details on found security vulnerabilities as well as recommendations on remediation ensuring thorough and tailored security assessments.
The idea of hiring an external team of consultants to perform your penetration testing is one that brings greater efficiency and expertise than you could get by having your in-house technicians perform that tests. External testers are objective and have no emotional relationship to the system. This means that they are more likely to model the actions of real-world hackers more closely than your own team would.
Who is it recommended for?
Businesses utilizing vulnerability scanners will find this tool indispensable, as penetration testing complements regular scanning efforts and provides greater visibility of vulnerabilities from an attacker's point of view. Though annual penetration tests may not be cost-effective for every business, even bi-annual tests remain recommended as this proactive approach helps strengthen security posture by uncovering flaws missed by automated scanners allowing experts to address critical issues effectively.
Pros:
- Launched Risk-Scoring Feature: Helps prioritize fixes based on the recently launched risk-scoring feature.
- Detects All Vulnerabilities: Proven to be quite valuable for security needs as it discovers all types of vulnerabilities and displays them in a single window.
- Automatic Web App Scanning: Automated web application scanning, security expert-validated business logic checks, proof of concept support, and eliminating false positives.
- Wide Support: Supports internal scans, external scans, and web applications.
Cons:
- Prices are Hefty: Only suitable for large enterprises. Small organizations or businesses with smaller environments may find this tool costly.
Price and Trial: As this is a bespoke consultancy service, there is no fixed tariff or menu of services. Instead, you negotiate a price. So, Hire an Expert instead of running your own penetration testing exercise.
3. Invicti Security Scanner
Invicti is a robust vulnerability management solution. It scans web applications, services, and APIs, automatically identifying a broad coverage of different vulnerability types. The tool emulates attacks to test the target’s defenses against SQL Injections, Cross-Site Scripting (XSS), and more.
Key Features:
- Application Security Scanner: Follow the best practice shift-left paradigm by integrating Invicti with market-leading CI/CD solutions and issue trackers to use the web application security scanner in your DevSecOps/SecDevOps environment.
- Complete Visibility: Scans your web apps and corners of the web assets and lets you know the status of the remediation efforts.
- Fully Automated: Totally automated and has many bundles of tools that will perform behavior analysis and other security checks.
Why do we recommend it?
We highly recommend Invicti Security Scanner due to its comprehensive automation features, seamlessly integrating security testing into all stages of the Software Development Life Cycle (SDLC). By automating security tasks and prioritizing critical vulnerabilities for remediation, Invicti frees up team time each month while prioritizing critical vulnerabilities for priority remediation efforts. Whether your organization operates an AppSec program, DevOps pipeline, or DevSecOps process, Invicti allows both security and development teams to stay ahead of their workloads while ensuring proactive measures are in place throughout the development process.
The Invicti web app security scanner can automatically assess between 500-1000 web applications simultaneously. You can also customize the scan with attack settings, authentication, URL rewrite rules, etc.
Who is it recommended for?
Invicti Security Scanner is the ideal way for organizations looking to integrate security into their development culture. By seamlessly integrating it with developers' daily tools and workflows, it provides actionable feedback to produce more secure code, thus decreasing security team workload and delays during the development process. Through continuous scanning, it prevents risks from being introduced which reduces delays during the process – giving Invicti the power to proactively improve security posture while streamlining workflows for greater efficiency and reliability.
Pros:
- Desktop and Cloud Version: Has both a desktop and cloud version.
- PoCs (Proof of Concepts): Produced to ensure they are not false positives, eliminating the need for users to double-check vulnerabilities.
- Scalable: Control permissions for unlimited users and have a look at security bottlenecks through complex infrastructure.
Cons:
- Outdated Knowledge Base: Documentation was outdated or not easy to follow when we initially started using the product. However, support has steadily been improving them.
4. Intruder Automated Penetration Testing
The Intruder Automated Penetration Testing is an online network vulnerability scanner. It can check for different types of application weaknesses, including SQL Injection, XSS, XML injection, and more. It can also identify infrastructure weaknesses such as remote code execution flaws, and misconfigurations like weaknesses in (or lack of) encryption in SSL/TLS or VPNs.
Key Features:
- Cloud-Based Software: Cloud-based software designed to track the attack surface and allow users to perform hands-on live simulations and penetration tests.
- Web App and API Scanning: Scans and resolves all the vulnerabilities in authenticated and unauthenticated web apps or APIs.
- Comprehensive Analysis: Allows organizations to analyze total checks, failed or passed checks, and unimportant callouts to prioritize critical issues and facilitate threat remediation processes.
Why do we recommend it?
We highly recommend Intruder for its reliability and effectiveness in continuous penetration testing. Backed by leading search engines, Intruder is trusted by businesses worldwide as an intermediary between automated scanning and point-in-time penetration tests. Continuous network scanning enables businesses to maintain 24/7 visibility into their perimeter while automatically testing newly discovered services for vulnerabilities – providing rapid control over their attack surface quickly.
The tool also performs banner-grabbing or fingerprinting to identify missing patches. When it detects a vulnerability, it creates a comprehensive report with recommendations.
Who is it recommended for?
The amazing features like Intruder's attack surface management tools, AWS integration enhancements, and improved web application scanning make it an invaluable asset to developers, startups, and enterprises alike. Serving as a vulnerability scanner to reduce expenses associated with human penetration testing experts; experts benefit from its comprehensive features like continuous monitoring, automated scanning of newly discovered services, and detailed vulnerability reports; this empowers them to proactively secure systems against potential threats.
Pros:
- Pre-Scripted Security Tests: Runs pre-scripted security tests without requiring manual work.
- Vulnerability Scans: Scans functional applications externally for vulnerabilities like SQL injection or XSS. Tracks issues as vulnerabilities are discovered. Documents activity throughout the resolution process.
- Anomaly Detection: Detects anomalies in functionality, user accessibility, traffic flows, and tampering.
- Easy Third-Party Integrations: Enables businesses to integrate the platform with various third-party applications, such as Microsoft Azure, Amazon Web Service (AWS), and more.
Cons:
- False Vulnerability Scans: It is found that the rate at which scans falsely indicate the detection of a vulnerability when no vulnerability legitimately exists.
Price and trial. There are three licenses; Essential (€78/ mo), Pro (€131/ mo), and Verified (€955/ mo). Subscribe to get a 14-day free trial.
5. Acunetix Scanner
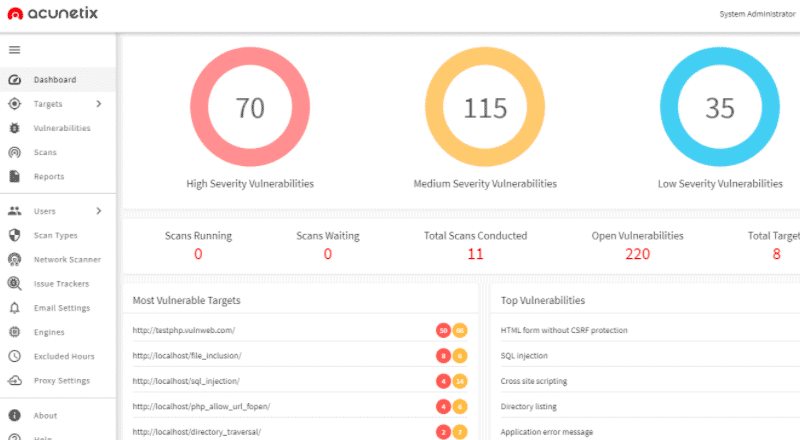
Acunetix Scanner is a dynamic web application security testing solution. It audits web applications, sites, and API, and identifies vulnerabilities such as SQL injection, XSS, weak passwords, misconfigurations, Out-of-Band (OOB) vulnerabilities, and more.
Key Features:
- Acunetix Reports and Classification: Provides reports that detail any security vulnerabilities found on your website or web app, and categorizes them based on severity so you can prioritize which ones need to be fixed first.
- Vulnerability Assessment Engine: Acts like an investigator to detect security holes within your website's code and configuration, scanning everything for vulnerabilities that hackers could exploit.
- Incremental Scanning: Instead of scanning everything again every time, Acunetix only checks those parts that have changed since its previous scan, saving time and resources while keeping your website secure.
- Compliance Management: Acunetix assists in making sure that your website complies with various security standards and regulations, as well as complying with laws and guidelines to protect both data and users.
Why do we recommend it?
Acunetix Scanner stands out among other scanners due to its exceptional flexibility for scanning hard-to-reach areas of websites and web apps. No matter the frameworks, languages, or technologies your web presence employs, Acunetix can run automated scans almost anywhere; be it single-page applications built with JavaScript/HTML5 script-heavy websites with complex paths/forms/multilevel forms/unlinked pages, etc. Acunetix provides comprehensive security testing across your entire web presence.
The Acunetix Scanner allows you to integrate your scans into a CD/CD pipeline with automation service tools like Jenkins. Additionally, you can also integrate third-party issue tracking systems, like Jira, GitLab, and GitHub to streamline vulnerability management.
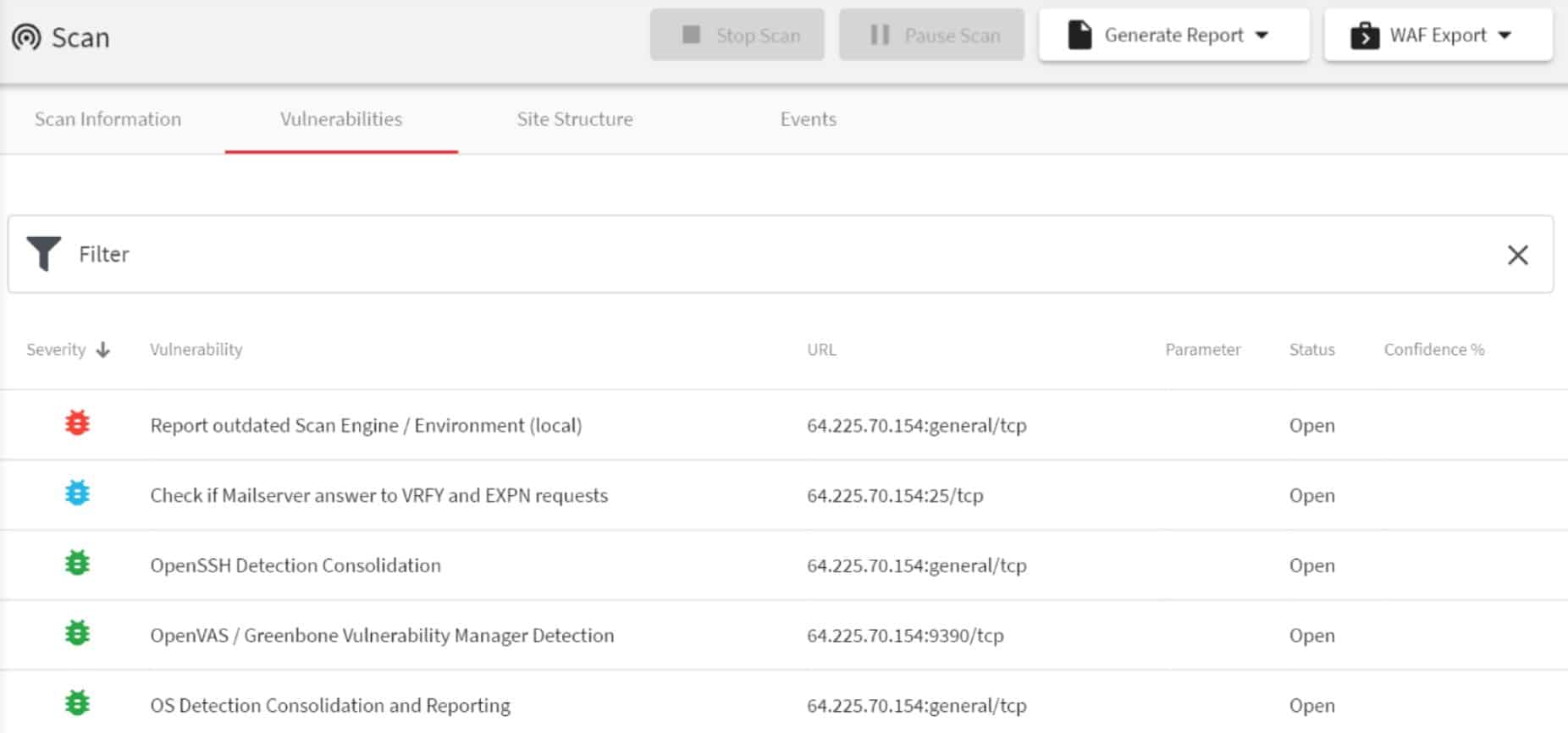
Who is it recommended for?
Organizations of all sizes that wish to improve their cybersecurity posture rely on this tool, with experts particularly reaping the rewards from its lightning-fast scans that immediately reveal vulnerabilities as they are discovered. Experts can quickly assess risks and take immediate action with its 90% results before halfway done scan time. Automatic prioritization of high-risk vulnerabilities allows efficient resource allocation, as well as its capability of scheduling one-off or recurring scans across multiple environments simultaneously, providing comprehensive security coverage and risk mitigation.
Pros:
- Regulatory Compliance: Designed to check regulatory compliance in real time.
- Intuitive Dashboard: Provides consumers with a dashboard to help them ease the process of checking their web applications in real time.
- Firewall Protection: Provides a firewall system to stop malware invasion.
Cons:
- Issue with API Integrations: Some users find they were not able to integrate dashboards with APIs.
- Authentication Issues: Issues with authentication when using contemporary workplace apps, which frequently reroute users to irrelevant endpoints, federated IDs, SSO, etc.
Price and Trial. Starts at $4,500 for the Standard edition, and $7,000 for the Premium edition, both for up to five websites. The price is based on multi-year contracts.
6. Nmap and Zenmap
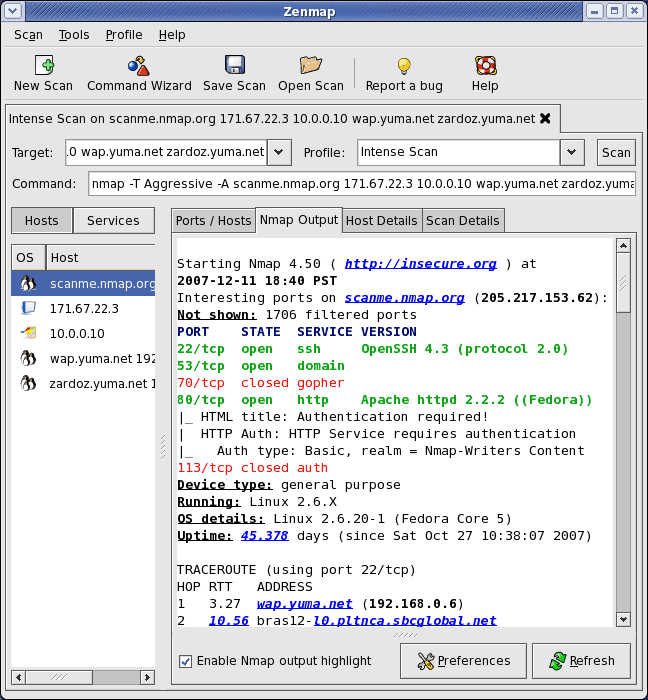
Nmap (Network Mapper) is a powerful CLI-based network mapper. It is the defacto standard for network mapping and port scanning. Nmap can discover hosts within a network by doing a ping sweep, find the services these hosts are offering, and identify their open ports. It can also discover the remote OS by using TCP/IP stack fingerprinting.
Key Features:
- Network Mapping: Allows you to map out your network by drawing a diagram showing which devices and services are connected and running on it.
- Port Scanning: Provides the ability to check whether ports on devices are open or closed – much like checking whether doors are locked or unlocked in a house.
- Service Port Scanning: Detects what services are running on open ports, giving a picture of what activities may be occurring.
- Host Discovery and Port Scanning: Provides information about the target, including host discovery, port scanning, operating system detection, and intrusion system detection.
Why do we recommend it?
Nmap and Zenmap offer powerful network mapping capabilities in complex environments with IP filters, firewalls, and routers. Their support for advanced techniques such as various port scanning mechanisms, OS version detection, and ping sweeps provide insights into network configurations and vulnerabilities. Nmap's strength lies in its efficient scans while its portability across different operating systems makes access easier across various platforms.
Znmap is the GUI-version of Nmap (screenshot above). It is as powerful as Nmap but easier to use. It provides results in a graphical and simpler way.
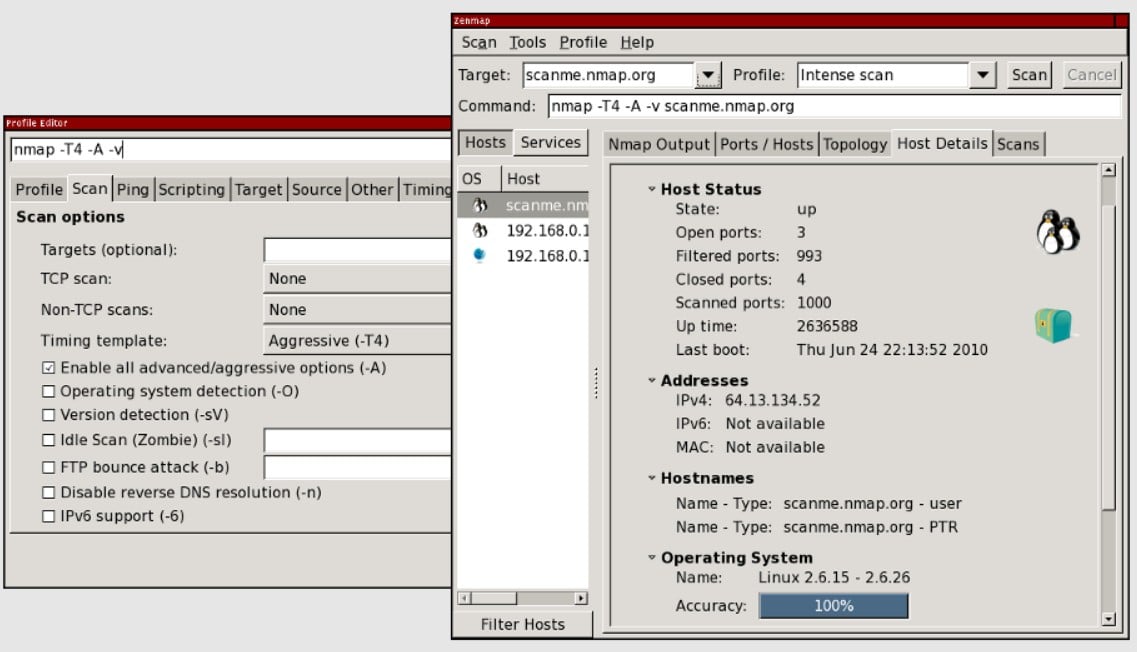
Who is it recommended for?
Nmap is a tool of great significance to cybersecurity professionals, network administrators, and ethical hackers alike. Security professionals with experience utilizing Nmap will find it especially useful for network reconnaissance, vulnerability assessment, and penetration testing. Ethical hackers may utilize its capabilities to detect potential security flaws that require remediation measures while network administrators depend on it to monitor and protect their networks against potential threats.
Pros:
- User-Friendly Graphic Display: With just two scans that yield a graphical display, one can quickly present the visual output of Nmap using Zenmap, a graphical user interface for Nmap.
- Effective Scans: Distinguish between the same scans even after they are run using commands from the command profile on different days.
- Scans in Text Modes: Shows scan findings in both graphical and text modes.
Cons:
- Issue with Human-Readable Format: Absence of choices for exporting data to a human-readable format that may be shared with stakeholders who need to be more technically inclined.
Nmap and Zenmap are free and open-source. Download from the official site.
7. Wireshark
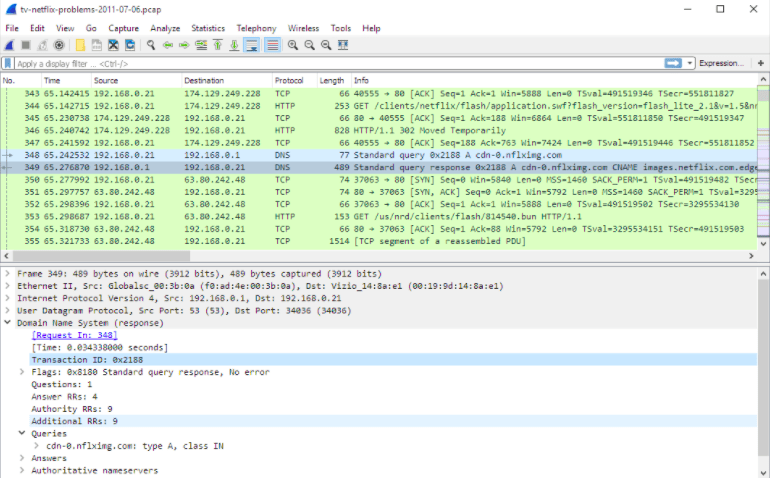
Wireshark, an award-winning network protocol analyzer, and one of the most preferred tools for network engineers, security experts, pen testers, and even hackers. Wireshark captures and analyzes network packets. It captures raw data, structures it according to the protocol, and filters it in the most detailed possible way.
Key Features:
- Network Protocol Analyzer: Records packets from a network connection, like one between the computer and the internet or your home office, is called a network protocol analyzer or Wireshark.
- Reliable and Widely Adopted: Award-winning network protocol analyzer used by professionals worldwide to analyze network traffic and diagnose network issues.
- Expose Packet Header Details: Allows users to inspect each packet's header, providing details such as its source and destination addresses, protocol used, and metadata relating to how data travels through networks. This enables a better understanding of how information travels over networks.
- Easily Comprehensible Reports: Analyzed reports make it easier for users and their clients to comprehend them and take appropriate steps based on them.
Why do we recommend it?
Wireshark is an easy and accessible open-source tool trusted by millions worldwide. Its greatest strength lies in producing analysis results that are understandable by clients. Penetration testers also rely on it, using its versatile features such as color coding for deeper investigation or isolating top-priority data packets. Users of Wireshark can efficiently analyze network traffic, identify anomalies, and address issues, making it an indispensable asset in cybersecurity assessments and network management.
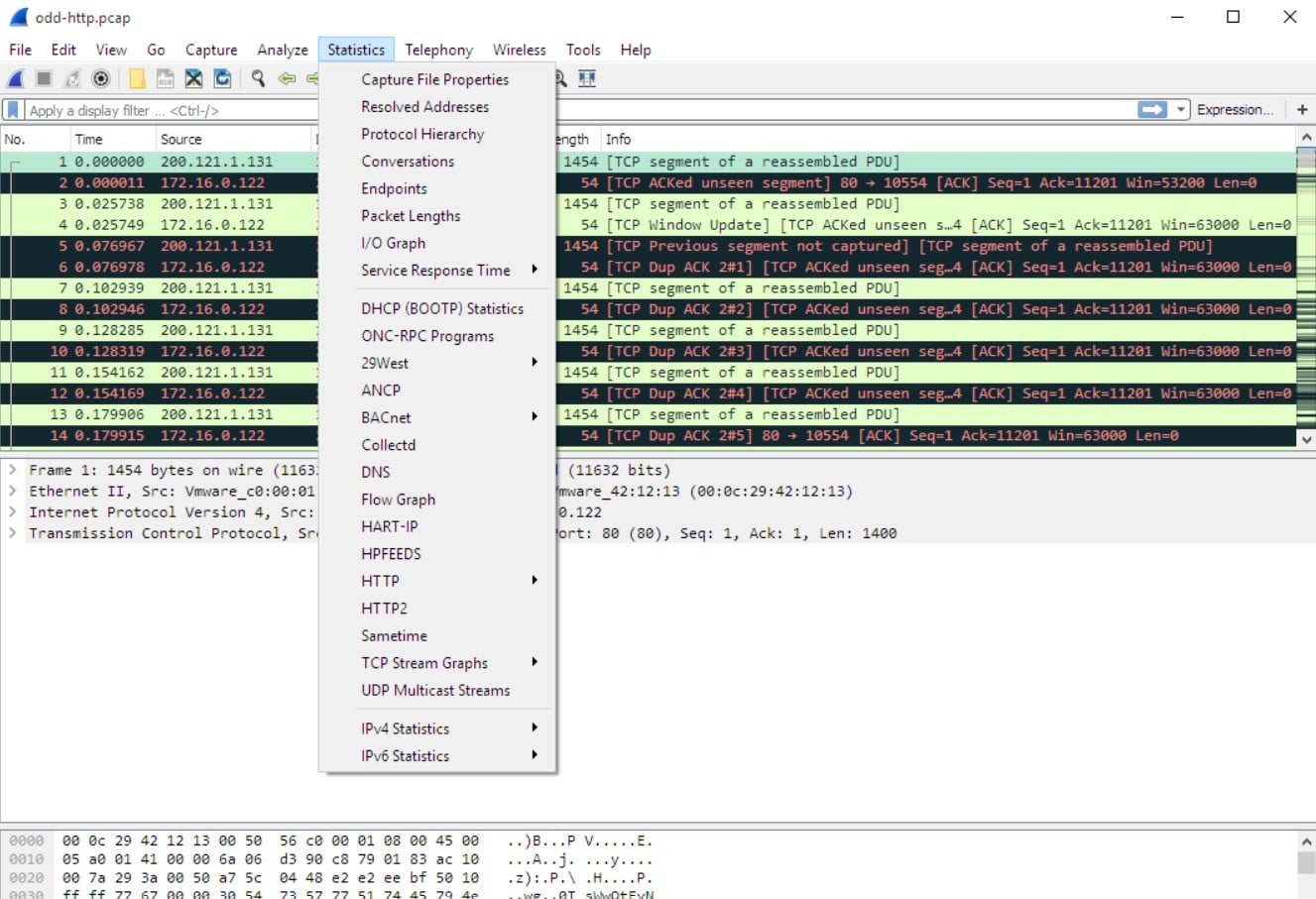
Who is it recommended for?
Wireshark is an essential tool for cybersecurity professionals, network administrators, and digital forensics specialists. Security analysts utilize Wireshark to monitor network traffic and detect any suspicious activities such as the transmission of unencrypted passwords or files. Penetration testers use it to assess vulnerabilities in network protocols and applications. Incident responders rely on its capabilities for investigating security breaches and insider threats.
Pros:
- Seamless Traffic: Sniffs traffic between your local computer and the remote system it is talking to.
- Human-Readable Format: Transforms network data into a usable format for humans, facilitating troubleshooting and understanding.
- Understandable Insights: Gives users a live picture of network traffic and instantaneous insight into what's going on in the network.
- Behavioral Insights: Gains insights into the behavior of individual protocols within the network.
Cons:
- Don't Record Network Communication: Under typical conditions, Wireshark cannot capture communication from every other system on the network.
- Not Useful for Decryption: Can't help with decryption with regard to encrypted traffic.
Wireshark is free and open source. The download is available for Windows, Linux, macOS, Solaris, and FreeBSD.
8. Metasploit
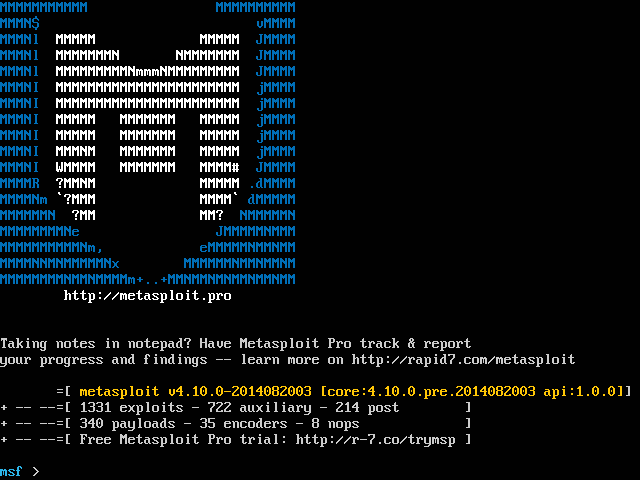
Metasploit is considered the swiss army knife for hackers. It is a robust collection of hacking tools, modules, and plugins. Metasploit automates several phases of a penetration test— from information gathering, gaining access, maintaining access, and even evading detection.
Key Features:
- SNMP Scanning and Windows Patch Enumeration: Two features that Metasploit may easily interact with during a penetration test's information-gathering stage.
- Vulnerability Scanner: Additionally, it offers a link to the Tenable Nessus vulnerability scanner.
- Multiple Unified Tools: Allows users access to an expansive set of attack vectors and techniques all in one convenient location.
- Rapid Testing: Enables users to conduct security and penetration tests quickly.
Why do we recommend it?
Metasploit Framework stands out due to its robust features and reliability. Created and maintained by Rapid7, known for their vulnerability scanner, Metasploit provides prepackaged exploits as well as customization to meet individual user requirements. Users can configure exploits with specific IP addresses, port numbers, payload types, or targets for precise targeting allowing for comprehensive penetration testing or security assessments, making it an invaluable asset to cybersecurity professionals or ethical hackers alike.
The Metasploit Project is one of the most popular pen testing and hacking frameworks. The project provides information about security vulnerabilities, helps with pen testing and the development of IDS signatures.
Who is it recommended for?
Metasploit is an invaluable resource for cybersecurity professionals, penetration testers, and incident responders. Security teams rely on this tool to verify vulnerabilities, conduct security assessments, enhance security awareness across networks and systems, and proactively identify security weaknesses before threats arrive. While penetration testers leverage its comprehensive features to simulate real-world attacks to pinpoint potential vulnerabilities before malicious actors exploit them. Incident responders rely on Metasploit for swift and efficient responses to security incidents with minimal damage and minimized risks.
Pros:
- Eliminates Risky Exploits: Anyone with any level of knowledge can safely do a penetration test.
- Permits: Adds particular custom modules and gaining access to its source code.
- Payload Command: Switching payloads is simple and quick as it becomes simple to convert shell-based access into a particular function.
- Deep Customizability: Stands out from many other pen-testing tools as it allows pen testers complete access to the source code and the capacity to install custom modules.
Cons:
- Time Consuming: Exploiting a system and keeping access to it takes a lot of work and time.
The Metasploit Framework (CLI) is free and open source. The Metasploit Pro is a GUI-version of Metasploit with the same capabilities.
9. John the Ripper
John the Ripper (JtR) is an open-source password-cracking tool. JtR was initially designed to test the strength of passwords for UNIX-based systems, but now it is supported by many operating systems.
Key Features:
- Supports Brute Force Attack Method: Follows dictionary, brute force attack, and rainbow tales methods.
- Command Line Tool: Through a command line interface, users can interact with the tool by typing commands into a terminal or command prompt. This provides flexibility and allows for the customization of cracking tasks.
- Password Cracker: Primary function is to crack passwords, using various techniques like dictionary attacks, brute-force attacks, and rainbow table attacks to guess or crack passwords, helping users recover lost or forgotten passwords or test the strength of existing ones.
Why do we recommend it?
We highly recommend John the Ripper tool as it is a component of Kali Linux hence it is the best addition to any security kit of the organization. It lets you know any weaknesses or problems around your database to get fixed as soon as possible. It is simple and effective and works by processing strings of complex characters.
JTR is capable of cracking passwords using any of the following methods:
- Dictionary Attack. Feed a list with a vast combination of words, phrases, and possible passcodes.
- Brute Force: Provide parameters to help JTR with successful password guessing.
- Rainbow Tables: Compares hashed passwords obtained from data leaks with plain-text passwords.
Who is it recommended for?
It comes in two versions: free and paid. You can use the free one for simple credential checking and is compatible with MacOS, Linux, and Windows. Security experts who are looking for advanced features might opt for the John Ripper Pro version. It is best at integrating modern password hashing with yescrypt or crypt_ blowfish.
Pros:
- Password Crackers: Password crackers may be operated from a single place, which also increases the application's efficacy.
- Helps for Password Hardening: Light-weight tool and the best option for maintaining security.
- Weak Password Identification: Admins can easily find weak passwords across organizations to make them stronger.
Cons:
- Comparatively Slow: Users noticed that it was slow compared to the most recent hashes. Hence not giving up on the mark performance.
Price and Trial. JtR is available in two versions; free (open source) and Pro version with additional capabilities like bigger dictionaries, multiple languages, optimized performance, and more.
10. Aircrack -ng
Aircrack -ng is the most popular suite of WiFi hacking tools. It works with a wide range of wireless NICs as long as they support raw monitor mode. Aircrack -ng is capable of capturing packets from 802.11a, 802.11b, and 802.11g WiFi standards and analyzing their hashes.
Key Features:
- Packet Reporting: Different packets from the reporting network will be captured by it. It can be applied to weakly-encrypted networks to retrieve usernames and passwords.
- Heavy-Scripting: All tools included in this platform are based on the command line and have an intuitive GUI, hence perfect for cracking WEP and WPA.
- Attacking: Users can perform packet injection to replay attacks, deauthenticate, find access points, and much more.
Why do we recommend it?
Aircrack -ng can be a one-stop solution tool for focusing on different aspects of WiFi security. Users can monitor deeply and capture useful packets and export the text files using other third-party tools. It is suitable for Linux as well as works on all popular platforms like macOS, Windows, open BSD, etc.
Aircrack -ng is armed with:
- Monitoring via a packet sniffer
- WEP and WPA/WPA2-PSK key cracker.
- Perform de-authentication, fake APs, and replay attacks.
- Capture and packet injection.
Who is it recommended for?
It is recommended for network and security experts to probe wireless networks. It is free to use and includes a wide range of security tools. Users can also perform penetration testing to check WiFi cards and understand driver capabilities.
Pros:
- Supports Wireless Technologies: Supports a variety of wireless technologies and can operate with numerous wireless cards.
- Crack WiFi Passwords: One primary feature is the ability to crack WiFi passwords using a variety of methods, such as dictionary attacks, brute force attacks, and WPS attacks.
Cons:
- Complex Learning: High learning curve and is primarily dependent on command-line tools, together with its intricate syntax and settings, can be a key disadvantage. Additionally, installing and configuring it might be challenging, particularly on non-Linux computers.
Download Aircrack -ng for free.
11. Nessus
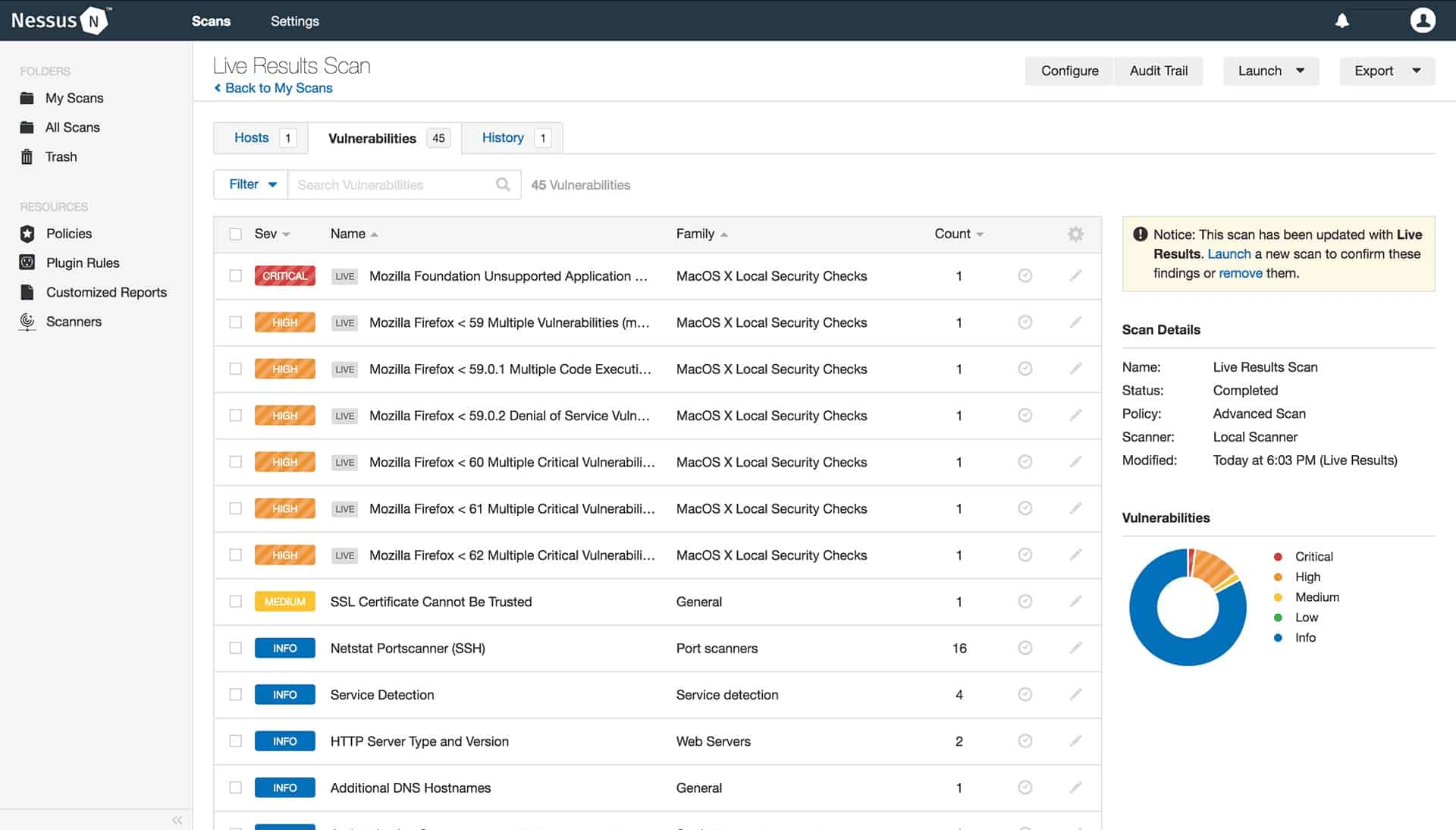
Nessus developed by Tenable is a powerful vulnerability scanner for infrastructures such as servers, network devices, databases, Operating Systems, and hypervisors. Nessus is capable of finding misconfigurations, default and weak passwords, and DoS risks. It is supported by Windows, Linux, and macOS.
Key Features:
- System Scanning: Checks a computer and sounds an alarm if any security holes that malevolent hackers might use to access any of the computers you have linked to the network.
- Web App Scan: Checks for vulnerabilities in your custom application code and third-party components.
- Pre-Built Policies and Templates: Over 450 pre-built templates to easily audit and understand the severity of vulnerabilities.
Pros:
- Seamless Navigation: Ease of navigation attracts a vast number of users.
- Live Results: Automatically does offline vulnerability analysis to accurately detect based on your scan history.
- Comprehensive Visibility: Valuable tool for network-to-endpoint scanning.
- Deployed on Any Platform: Portable tool that can be easily deployed on any platform including Raspberry Pi.
Cons:
- Wrong Detection: Incapable of appropriately handling false positives, frequently inaccurate detection technique, and sluggish in identifying novel vulnerabilities.
Price and Trial. Nessus is available in a free limited version (download Essentials) and a full-featured paid subscription version (Professional for one year for €3,036).
12. Kali Linux
Kali Linux is more than a tool; it is an entire Linux distribution— derived from Debian and designed for penetration testing, ethical hacking, reverse engineering, vulnerability assessment, and advanced forensics.
Key Features:
- Highly Customizable: With the high level of customization Kali Linux offers, users can customize the distribution to suit their own requirements.
- Flexible to Add New Tools: Provides flexibility to suit the needs of individual users, whether it's for adding new tools or customizing the UI.
- Undercover Mode: Be undercover where no traffic can see you and you can perform your task secretly.
Why do we recommend it?
We recommend Kali as it helps to reduce workload, making it easy for experts to quickly get up and running. Thanks to meta packages tailored specifically for security experts and an easily accessible ISO modification procedure, creating the optimal version of Kali for you is always straightforward.
Kali Linux gives you access to a long list with more than 600 tools, for information gathering, vulnerability analysis, brute-force password cracking, wireless attacks, spoofing, sniffing, and a lot more.
Who is it recommended for?
This tool benefits cyber security experts and penetration testers to detect vulnerabilities and exploits. It helps the experts involved with ethical hacking, penetration testing, sniffing, spoofing, and much more.
Pros:
- Easy to Use: Excellent for individuals with some familiarity with Linux commands and at an intermediate level.
- Compatibility: Possibly utilized with a Raspberry Pi with ease.
- Wide Range of Tools: Provides over 600+ tools for data collection, reporting, and performing other operations.
- Availability: Due to its linguistic support, Kali Linux is available to users everywhere.
Cons:
- Only for Professional Use: Not a suitable fit for domestic or personal use. It is only used by security or cyber experts for legal use.
Download: Kali Linux is a free and open-source project. Download an image at Kali’s official site.
Six Worthy Mentions
Below are six additional pen-testing tools also loved by security experts.
- BeEF The Browser Exploitation Framework (BeEF) was designed to hook (take control of) web browsers, and launch attacks from there.
- W3af Web application audit and attack framework (W3af) is an open-source web application security scanner.
- THC Hydra. A fast online password and network logon cracking tool. It can perform dictionary attacks over protocols like FTP, HTTP, HTTPS, SMB, and many more.
- Maltego. A robust tool for graphical link analysis, used for forensics and intelligence gathering. Maltego lets you mine data from open-source and distributed sources and compile it into a graph.
- SQL Map A powerful open-source penetration tool used for detecting and executing SQL injections and taking control of databases.
- Nikto An open-source web scanner for web servers. It tests servers against 6700 potentially dangerous files and programs. It also identifies outdated and problems with specific server versions.
Conclusion
The ten tools in this post cover all the required steps to perform a solid penetration test. Nmap to scan for open ports and map the network, Wireshark to analyze packets, and John the Ripper to crack passwords and gain access. Other tools like Metasploit use pre-packaged exploits to automate several phases. Similarly, Aircrack-ng for several wireless pen test phases.
Automatic security assessment tools such as Invicti, Acunetix, Intruder, and Nessus can help assess either external networks like web applications, websites, and APIs and internal networks such as computers, network devices, etc.