We may earn a commission if you make a purchase through the links on our website.
How to protect your backups from ransomware

UPDATED: December 13, 2022
Do you want to protect backups from ransomware? Then, read this article to know everything about ransomware, like what ransomware is, how it works, the exact steps to protect your backup from ransomware, and the best tools to protect backups from ransomware.
Here is our list of the best tools to Protect backups from ransomware:
- NinjaOne Protect – FREE TRIAL A comprehensive tool that combines endpoint protection, backup services, and malware protection in a user-friendly, web-based management platform.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL Offers continuous scanning, patching, and robust reporting.
- Acronis Ransomware Protection – FREE TRIAL A free anti-ransomware application that combines backup solutions with ransomware protection.
- CrowdStrike Falcon An Endpoint Protection Platform with advanced ransomware detection and prevention capabilities.
- Kaspersky Anti-Ransomware Tool Provides behavioral detection, vulnerability scanning, and cloud analysis.
What is ransomware?
Ransomware is a kind of virus that uses encryption to hold a victim's data hostage. First, the vital data of a person or organization is encrypted, making it impossible for them to access files, databases, or apps. Then a ransom is asked to gain access. Ransomware is frequently designed to propagate over a network and target database and file servers, paralyzing a whole enterprise in the process. It's a growing menace that generates billions of dollars in payouts to hackers while causing considerable damage and costs to businesses and government agencies.
How does ransomware work?
Asymmetric encryption is used by ransomware. This is a type of encryption that encrypts and decrypts a file using a pair of keys. The attacker generates a unique public-private pair of keys for the victim, with the private key used to decrypt files saved on the attacker's server. The attacker usually only gives the victim the private key once the ransom is paid, but this is not always the case, as recent ransomware operations have shown. It's nearly hard to decode the files being held for ransom without access to the private key. There are many different types of ransomware.
Ransomware employs asymmetric encryption. This is a sort of encryption that uses a pair of keys to encrypt and decode a file. For the victim, the attacker creates a one-of-a-kind public-private key pair, with the private key being used to decrypt files saved on the attacker's server. The private key is usually only given to the victim once the ransom is paid, but as recent ransomware attacks have proven, this is not always the case. Without the private key, decoding the files held for ransom is practically impossible. Ransomware comes in a variety of forms.
Once data have been encrypted, ransomware will demand a ransom payment within 24 to 48 hours, or the files would be permanently lost. If a data backup isn't available, or if the backups are encrypted, the victim will have to make the payment to the ransom to get their files back.
Why do you need protection against ransomware?
Simply put, ransomware has the potential to ruin your business. Even if you are only locked out of your files for a day, it will impact your revenue. However, because ransomware puts most victims offline for at least a week, the financial losses can be substantial, if not months. Not only do systems fail for long periods due to ransomware, but also due to the time and effort required to clean up and restore networks.
Consumers grow apprehensive of handing their data to firms they perceive are vulnerable, not just because of the immediate financial impact of ransomware. In addition, cyber criminals have discovered that vital infrastructures like hospitals and even industrial facilities are profitable targets for ransomware attacks and that interrupting these networks can have severe ramifications for people in the physical world.
Steps to Protect Backup from ransomware
How to Protect Your Windows System?
The bulk of ransomware attacks target Windows hosts, and once one is infected, it spreads to additional Windows hosts in your computing environment. Finally, the attacker activates the encryption program after the ransomware has spread to enough hosts, and your entire world is instantly shut down. As a result, the most obvious thing to do for your backup server is to utilize something other than Windows.
Unfortunately, many popular backup programs are Windows-only. The good news is that a lot of them also have a Linux version. Even if the primary backup program is Windows-only, it may have a Linux media-server alternative. Because the data you're trying to safeguard is stored on the media servers, they're crucial. Ransomware assaults against Windows-based servers will not access your backups if they are only accessible via Linux-based media servers.
Make sure your central backup server's backups are also saved behind a Linux-based media server, in addition to your regular backups. It doesn't matter if your backups are unencrypted. If the ransomware has encrypted the database, you need to access them. Windows-based backup servers should likewise be as secure as feasible.
Learn which services are used by ransomware to target servers (such as RDP) and disable as many as feasible. Remember that this server is your last line of defense, so think security rather than convenience while configuring it.
Save Backups In a Separate Location
Backup copies should be saved in a separate location, regardless of the backup method you use. This entails more than merely installing your backup server in a cloud-based virtual machine. It's just as easy to attack a virtual machine if it's just as accessible from an electronic standpoint as if it were in the data center.
You must design things in such a way that attacks on your data center systems do not spread to your cloud backup services. This can be accomplished in several methods, including firewall rules, operating system changes, and storage protocol changes. Most cloud vendors, for example, provide object storage, and most backup software products and services can write to it. However, despite the sophistication of ransomware attackers, they have yet to figure out how to target backups saved on object-based storage.
Furthermore, such services frequently have a write-once, read-many option, which allows you to set a time limit for backups to be updated or deleted, even by authorized staff. There are additional backup services that can store data that is only available through their user interface. If you can't see your backups directly, the ransomware can't either. The goal is to get your backups—or at least one copy of your backups—as far away as possible from an infected Windows PC. Put them on a cloud provider's cloud that is secured by firewall rules, run your backup servers on a different operating system, and save your backups to another type of storage.
Deny file-system access to backups
If your backup system saves backups to disc, be sure they can't be accessed through a conventional file system directory. E:\backups, for example, is the very worst place to save your backup data. Ransomware deliberately targets directories with names like those, encrypting your backups in the process. Unfortunately, this means you'll have to find out a way to store those backups on disc without the operating system recognizing them as files.
For example, a backup server might write its backup data to a target reduction array installed to the backup server through a server message block or network file system. Because the backups are accessible via a directory, if a ransomware product hits that server, it will encrypt those backups on the target deduplication system.
You should look at allowing your backup software to write to your target deduplication array without utilizing SMB or NFS. This feature is available in all popular backup software.
Save Multiple Copy of Backup
Make it difficult for ransomware to access your backups and encrypt them. If possible, avoid storing them on a Windows server and keep at least one copy elsewhere that is not electronically accessible from your data center. Finally, set up your backup system so that backups aren't visible on your backup server as files. Then, in the event of a ransomware attack, give yourself a fighting chance.
Our methodology for selecting the best tools to protect backups from ransomware:
We've broken down our analysis for you based on these key criteria:
- Comprehensive endpoint protection and system hardening.
- Effective backup services with secure storage options.
- Advanced malware and ransomware protection capabilities.
- Efficient patch management to prevent vulnerabilities.
- User-friendly management consoles for streamlined operations.
Best Tools to Protect Backups from Ransomware
1. NinjaOne Protect – FREE TRIAL
NinjaOne Protect is a package of tools offered on the NinjaOne cloud platform, blended with the on-site services of BitDefender Gravity Zone. This joint project gives you extensive security for all layers of your IT assets from individual endpoints and network-wide services, while providing multi-site visibility.
Key Features
- Endpoint protection and system hardening
- Backup services
- Malware protection
Why do we recommend it?
NinjaOne Protect is recommended for its integrated approach to ransomware protection, combining NinjaOne's expertise in endpoint management and backup services with BitDefender's GravityZone ransomware protection. This unique combination provides comprehensive security across all IT asset layers.
While NinjaOne provides endpoint management, backup services, and patch management to the bundle, BitDefender provides its GravityZone ransomware protection, threat intelligence, and endpoint detection and response. This is a great combination because each provider fills in the gaps of the other.
GravityZone is an excellent bundle of on-site security systems. However, for full ransomware protection, you really need a safe backup system so that you can recover from an attack without having to pay the ransom. BitDefender doesn’t offer a backup system, but NinjaOne does.
The backup service in Ninja Protect includes cloud storage space your backup repository and the platform is multi-tenanted, which makes it ideal for managed service providers. As a cloud-based system, endpoint management and patch management can be applied to endpoints anywhere in the world – they don’t all need to be on the same network. Download the BitDefender agent onto each protected device through the NinjaOne Web-based console to complete the security system installation.
Who is it recommended for?
NinjaOne Protect is ideal for organizations looking for a multi-faceted security solution, especially managed service providers, given its cloud-based system and multi-tenanted platform. It's well-suited for businesses seeking both endpoint protection and a reliable backup system.
Pros:
- Simple and easy-to-use admin dashboard
- Can silently install and uninstall applications and patches while the user works
- Patch management and other automated maintenance tasks can be easily scheduled
- Platform agnostic web-based management
Cons:
- Lacks support for mobile devices
EDITOR'S CHOICE
NinjaOne Protect emerges as our Editor's Choice in this category. This tool brilliantly integrates the strengths of NinjaOne's endpoint management and backup services with BitDefender's acclaimed GravityZone ransomware protection. The synergy between these two providers creates a robust defense mechanism against ransomware, ensuring not just real-time protection but also reliable backup for recovery.
Its multi-tenant cloud storage and platform-agnostic management capabilities further enhance its appeal. The simple, easy-to-use dashboard, coupled with the ability to silently install and manage patches, makes it an ideal choice for diverse IT environments.
Download: NinjaOne Protect Free Trial
OS: Windows
Register for the free trial.
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus is a solution that protects against ransomware attacks by blocking entry points that hackers can use. Endpoints, network appliances, and web applications will all be protected with this system hardening tool. A vulnerability scanner and a patch manager are the two main components of this software. Patches for operating systems and software packages are frequently published due to security flaws discovered in the software house's products. If you don't deploy patches as soon as they become available, your system is vulnerable to a variety of malicious activity, not simply ransomware.
Key Features
- Real-time bulk access alerts can help you detect ransomware.
- Activate notifications as soon as ransomware begins encrypting your files.
- Ransomware was quarantined using a configurable and automated response mechanism.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is recommended for its proactive approach to ransomware protection, focusing on blocking entry points for hackers through system hardening. Its combination of a vulnerability scanner and a patch manager ensures timely updates and security against emerging threats.
A live threat intelligence feed keeps the vulnerability scanner up to date. After the initial sweep, the scanner continues to function, doing a system sweep every 90 minutes and conducting additional investigations whenever a threat information update is received. In addition, the system identifies all networked devices and scans them to create a software inventory.
A patch management method starts with a list of operating systems and apps, along with their version numbers. Next, the patch manager monitors its registered list of resources for patches and updates. Then, it prepares the installers for deployment when one appears. Finally, system administrators can configure the patch management to apply all patches at the next available install time window. Vulnerability Manager Plus is an on-premises vulnerability management solution that employs a distributed approach.
An agent application is installed on each endpoint on the network; agents are available for Windows, macOS, and Linux. Agent operations are coordinated, and threat intelligence actions are channeled to them by a central server that runs on Windows and Windows Server. It also compiles feedback from each agent into a report that can be analyzed on the system console.
Who is it recommended for?
This tool is particularly suited for enterprises that require continuous scanning and patching across various operating systems. It's ideal for environments that need robust reporting and a detailed security ecosystem.
Pros:
- Great for continuous scanning and patching throughout the lifecycle of any device
- Robust reporting can help show improvements after remediation
- Flexible – can run on Windows, Linux, and Mac
- Backend threat intelligence is constantly updated with the latest threats and vulnerabilities
- Supports a free version, great for small businesses
Cons:
- The ManageEngine ecosystem is very detailed, best suited for enterprise environments
You can get started by downloading a 30-day free trial.
3. Acronis Ransomware Protection – FREE TRIAL
The Acronis Ransomware Protection program is a free, independent anti-ransomware tool with the same features and capabilities as the more comprehensive Acronis True Image backup utility.
Key Features
- Acronis Ransomware Protection is a free anti-ransomware application
- It also includes 5GB of hosted online backup
- More crucially, by prohibiting any efforts to edit its files, this utility maintains its integrity
Why do we recommend it?
Acronis Ransomware Protection is recommended for its dual focus on ransomware protection and backup solutions. Its free offering, inclusive of 5GB of hosted online backup, makes it an attractive option for users seeking reliable ransomware defense without significant investment.
All of the crucial data that the user chooses to secure is saved in the cloud. In the event of a ransomware attack, this online backup system is used as a recovery point.
This is in addition to the local backup cache, which Acronis Ransomware Protection protects against ransomware attacks by blocking access to. Any program or process that does not have the necessary permissions is denied access.
Meanwhile, the program monitors for signals of ransomware attacks and employs “whitelisting” of other essential activities to ensure it doesn't flag legitimate users who require access.
Finally, Acronis Ransomware Protection is a free anti-ransomware application offered by its creator in the hopes that you would enjoy it so much that you will upgrade to the premium version.
Who is it recommended for?
This tool is ideal for individual users and small businesses needing basic ransomware protection combined with cloud backup solutions. It's not the best fit for larger enterprise solutions but offers a solid foundation for personal and small-scale use.
Pros:
- Combines backup/BDR solutions with ransomware protection
- Comes with 5GB of free online storage
- Completely free
Cons:
- Not the best option for enterprise solutions
Get started with a 30-day free trial.
4. CrowdStrike Ransomware Protection
CrowdStrike Falcon is an Endpoint Protection Platform (EPP) with ransomware detection and prevention capabilities. Falcon Prevent, a next-generation antivirus service, is one of the modules included in the EPP. This is the main ransomware-blocking module. The Falcon EPP is a cloud-based platform. This cutting-edge architecture allows powerful cybersecurity software to safeguard devices without putting a strain on their processing capacity. To coordinate threat detection and response, a tiny agent application must be deployed on the endpoint. Windows, Windows Server, Linux, and Mac OS are all supported by the agent. A mobile version for Android and iOS is also available.
Key Features
- Stop the spread of ransomware by turning off affected devices
- View in-depth details of events to conduct further research
- This cutting-edge architecture allows powerful cybersecurity software to safeguard devices without putting a strain on their processing capacity
Why do we recommend it?
CrowdStrike Falcon is recommended for its advanced AI-driven ransomware detection and prevention capabilities. Its cloud-based platform and lightweight agent design ensure powerful cybersecurity without compromising device performance.
To detect attacks, the Falcon defense system employs AI-based machine learning. Before touching the operating system, suspicious files are uploaded to the CrowdStrike server for further examination. The antivirus service compiles a list of “attack indicators” for freshly found malware (IOCs). This document outlines the entry points and vulnerabilities exploited by modern ransomware, allowing an antivirus to harden an endpoint before it is attacked. This method effectively prevents infection from email attachments and Trojan and ransomware programs disguised as useful utilities.
CrowdStrike is a team of cybersecurity experts and researchers who are constantly looking for new malware. The team also detects malware sources, allowing them to map linked attacks. As a result, they can prepare CrowdStrike customers' devices for various attacks that tend to come in waves. In addition, CrowdStrike Falcon's administration console is cloud-based and accessible through the browser. As a result, systems administrators may manage the security of a large number of devices in one location, including endpoints at several locations.
Who is it recommended for?
CrowdStrike Falcon is best for organizations operating in hybrid environments (Windows, Linux, Azure, multi-cloud, etc.) and those needing an intuitive, easily accessible cloud-based admin console for managing a wide network of devices.
Pros:
- Excels in hybrid environments (Windows, Linux, Azure, multi-cloud, etc)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Can proactively stop ransomware with AI-driven detection methods
Cons:
- Would benefit from a longer trial period
You can test out CrowdStrike Falcon through a 15-day free trial.
5. Kaspersky
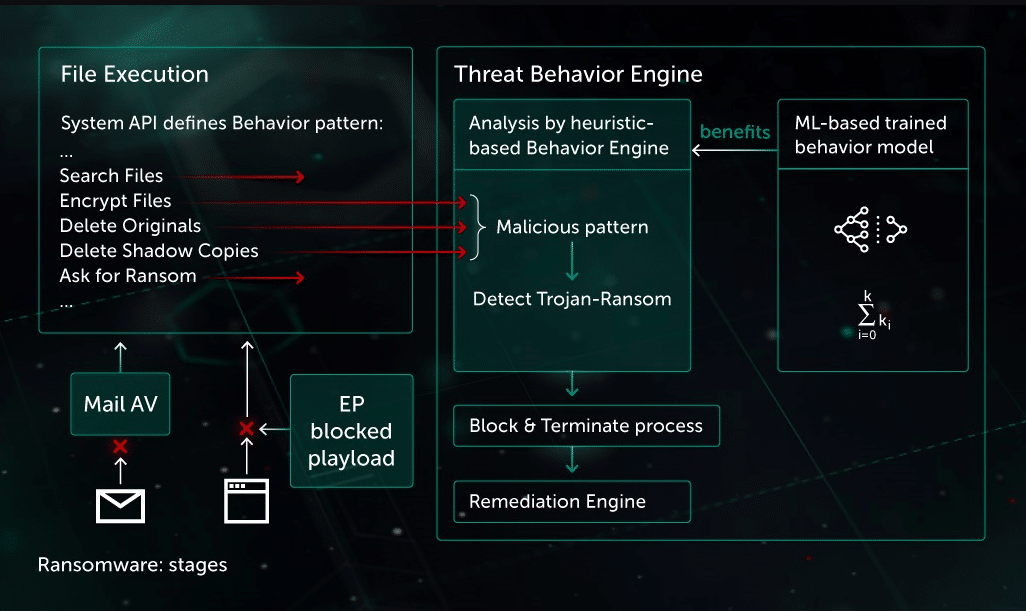
The Anti-Ransomware Tool from Kaspersky comes with three primary functions, the first of which is behavioral detection. This function monitors the operations of programs and searches for unusual behavior. It is blocked if something out of the ordinary is found. This capability can maintain track of both local and remote sites, allowing it to stop suspicious activity from both intentionally downloaded files and network programs.
Key Features
- It monitors the operations of programs and searches for unusual behavior
- In the free version, the list of suspected files is shown
Why do we recommend it?
The Kaspersky Anti-Ransomware Tool is recommended for its effective behavioral detection, vulnerability scanning, and cloud analysis. Its ability to monitor operations and identify unusual behavior in programs makes it a strong contender for ransomware protection.
A vulnerability scan is also included, which scans for apps with known flaws. You just get a list of suspect files in the free edition, and it's up to you to keep up with the updates. The premium edition, of course, will automatically update this program.
The final key component is cloud analysis, as defined by Kaspersky. You must join Kaspersky's cloud network as part of the setup process for this tool, which keeps you constantly connected to a vast list of other users, generating a list of trusted and untrusted applications. This cloud network is being integrated into several of Kaspersky's security products, but it isn't for everyone, especially if you're a gamer who requires a continuous network connection.
Who is it recommended for?
This tool is particularly beneficial for businesses looking for a robust ransomware protection system with advanced alert templates and file-level encryption. It's also suitable for environments that integrate with Active Directory for enhanced access control.
Pros:
- Offers file-level encryption to secure locally stored data on endpoints
- Integrates with AD for access control and policy-based configuration
- Offers advanced alert templates and locally stored roll-backs
- Leverages behavioral analysis to identify previously unknown threats
Cons:
- US-based companies might be restricted from using foreign security solutions
Conclusion
Ransomware is quickly becoming the most common data threat. Thus it's critical to ensure bad actors don't encrypt your backup data with your primary data when they launch ransomware assaults. If they succeed, you'll be forced to pay the ransom, which will only inspire them to try it again. Having backups to restore systems that have been encrypted by ransomware is crucial to not having to pay the ransom. The key to preventing ransomware attacks on backups is to create as many barriers as possible between production and backup systems. Whatever you do, make sure your backups aren't just sitting in a directory on a Windows server in the cloud.