We may earn a commission if you make a purchase through the links on our website.
RBAC vs. ABAC: What’s the Difference?
UPDATED: April 1, 2022
As per a study conducted by IBM, the average cost of a data breach is $3.86 million, and the average time to find it comes around 207 days (as of 2020). Remote work and the COVID-19 pandemic increased the attack surface and the difficulties of avoiding such data breaches.
For any organization – big or small – that wants to secure its data and to avoid the massive cost and headache that will come with the data breach, a well-defined authentication and authorization are of paramount importance.
There are mainly two methods for managing access control or authorization for your systems – RBAC (Role-Based Access Control) and ABAC (Attribute-Based Access Control). And so, what’s the difference between RBAC and ABAC methods? Which one is better? RBAC or ABAC?
To know the answers to such questions, we'll first look into these two managing access control methods individually and then we’ll do a comparison of RBAC vs ABAC. In the last sections, we’ll see how they can work together and what are some access control tools that can be used with RBAC or ABAC.
Authentication, Authorization, and Accounting
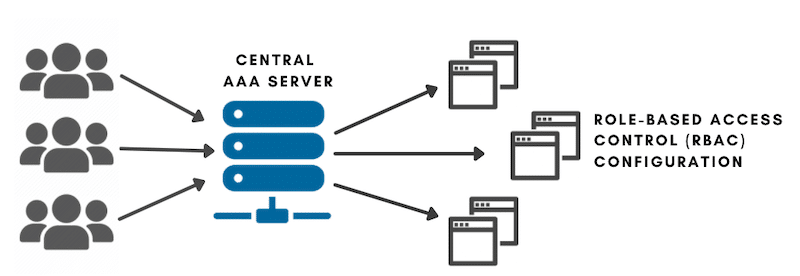
The access control framework, known as the AAA, which stands for Authentication, Authorization, and Accounting, deals with access to computer resources, policy enforcement, and usage audits. Combining all these processes is vital for robust network security and management.
Although AAA is simply a set of protocols that mediate network access, the framework is quite helpful in understanding RBAC and ABAC's role in access control.
- Authentication Granting or denying access is the first step to access control. Authentication happens when users attempt to log into an app or network using their credentials. They are either permitted or denied access. Authentication determines who the user is.
- Authorization Only once users are authenticated, the server (in some cases, the AAA server) determines the authorization level. Authorization is simply the process of enforcing policies. Users gain authorization for doing specific tasks, such as issuing commands or accessing particular resources. Authorization determines what a user can do.
- Accounting Accounting is the final process in the access control framework. It measures or audits the resources a user can consume during access. Such resources vary from system time, amount of sent or received data, and more. Accounting determines what the user did.
A central AAA server can help administrators centrally define attributes such as credentials (username and password) and authorization policies. Such attributes can be mapped to an RBAC or ABAC configuration (on an endpoint).
What is RBAC?
If you run an organization with a lot of employees at different levels and various third-party members or contractors on the same network, then you can maintain a solid network access control using RBAC.
The RBAC or the Role-Based Access Control is an advanced access control method that restricts network access based on a person’s role within an organization.
The “Role” essentially means the Level of Access a person or employee of an organization is given within the network. You can define the level of access for an employee based on factors like authority, task competency, department, location. Popular examples for roles are the defined WordPress roles: Administrator, Editor, Contributor, Subscriber, Manager, and more.
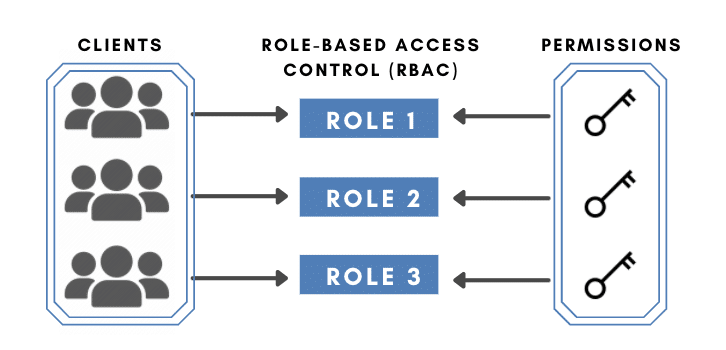
So, with an RBAC implemented, employees can be allowed to access only the necessary information for them to perform their duties. In addition, with RBAC, you can restrict access to computer resources to specific tasks like viewing, editing, or executing a file.
The National Institute of Standards and Technology presents four different ways of implementing the RBAC model, namely:
- Flat In this RBAC method, all the individuals have at least one role that defines permissions.
- Hierarchical In the hierarchical method, the seniors have their role in defining permissions, but they can also manage or define roles underlying them.
- Constrained This method uses the Separation of Duties (SOD), a well-known security practice, to spread a single duty among several employees. This practice is helpful for large enterprises or medium-sized businesses as it ensures no one else can perform changes or audits to your system.
- Symmetrical Finally, in the symmetrical model of RBAC, which has similar features to the Constrained RBAC, with the exception that permissions are reviewed frequently and then changed accordingly.
What is ABAC?
ABAC stands for Attribute-Based Access Control, and it’s another way of securing access to your network. The ABAC method manages an individual’s access inside a network based on specific attributes.
Attributes are simply a set of characteristics or values of an element involved in the access process. Access control based on attributes (as ABAC does) analyzes the attributes of such elements using rules.
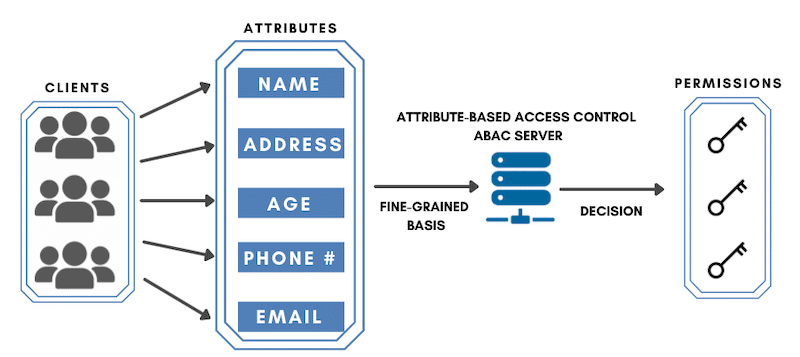
As an administrator using an ABAC method, you can define attributes as:
- User Attributes may include the individual’s name, role, or position.
- Resource Attributes can be the file type, its creation date, and its sensitivity level.
- Environmental Attributes may include access time or data location.
So an employee or an individual inside the network would be allowed to access the network only when they meet the criteria defined by these attributes.
RBAC vs ABAC
So now that we understand RBAC and ABAC individually, we can clearly see the similarities and differences between them.
Both RBAC and ABAC are methods to manage the authorization, authentication, and accounting of users inside a network. RBAC method is based on the Role of an individual, and ABAC is based upon the Attributes designated to a user or resource. So, while RBAC has a broader approach to managing access control, the ABAC can be used for a more granular network access control.
So, ABAC vs. RBAC, which one is better?
Well. It depends upon the situation or requirement.
One of the advantages of ABAC is that it allows a higher level of control to administrators. But, although you can create well-defined rules with ABAC, which may seem tempting in the first place, ABAC does have a few cons. ABAC requires complex configuration; it takes more time to fix in case of any error and requires considerable processing power. Nevertheless, as per the research and consulting firm Gartner states, “Attributes Are Now How We Role” and they predict that “By 2020, 70% of businesses will use attribute-based access control (ABAC) to protect critical assets.”
So, suppose you’re running an organization with a geographically diverse workgroup. And you may want to define access to your network or information based on business hours, location, and employee type. In that case, implementing ABAC might be a better idea.
On the other hand, RBAC is easy, takes less time, and requires less processing power to execute and manage. However, the configuration might become challenging with RBAC when adding granularity. Adding more roles may result in what is called role explosion.
So, RBAC is the best choice to go with when a company is small (10 to 15 people) and has few files. Or, if you are a large organization with simple structured workgroups where your employees don’t need to see the sensitive information, you can also implement RBAC.
Combining RBAC and ABAC
An organization can also use RBAC and ABAC combined (RBAC/ABAC hybrid solution). This access control model is called RBAC – A.
Many organizations will start combining RBAC and ABAC when required. Let’s say there’s a small company that uses RBAC as it’s easier to implement, manage and also because no attribute-access control is needed. But as soon as the organization grows, the system would require a more robust method for securing the data and the network with a well-defined set of rules. Given the case, the company can decide to use the RBAC – A model where RBAC will do the broad access control and the ABAC will help to define granular rules.
Which are some of the best access management tools?
Given the importance of RBAC and ABAC, an Identity and Access Management (IAM) tool is essential for your business to allow the right individuals access to the correct information at the right time and place.
Some of the best IAM tools available in the marketplace are Solarwinds Access Right Manager, Centrify,Okta, and OneLogin
Solarwinds Access Rights Manager, for instance, includes an RBAC solution that can help you secure your data, automate access control and management, and prove compliance.
You can test out Solarwinds Access Right Manager through a 30-day free trial.
Frequently Asked Questions (FAQs)
Let’s also look at some Frequently Asked Questions around access control methods.
- What are the different types of Access Control Methods? There are mainly four different types of access control methods – Role-Based Access Control(RBAC), Attribute-Based Access Control(ABAC), Mandatory Access Control (MAC), and Discretionary Access Control (DAC).
- What is Authentication? Authentication is the process of verifying who someone is. So it’s a process of validating your credentials when you enter your user ID and Password into the system to verify your identity. Users are authenticated then authorized.
- What is Authorization? The authorization is a process that permits you to access resources like files, folders, or any form of data stored on a network or server. Another term that is used in conjunction with authorization is authentication.
- What is Attribute-Based Authentication(ABA)? As the name itself suggests, Attribute-Based Authentication is a process of authenticating users based on attributes assigned to them.
- What is PBAC? PBAC is an acronym for Policy-Based Access Control, which is similar to the Attribute-Based Access Control(ABAC) method. The key difference is that PBAC enforces policies using attributes. So, PBAC and ABAC can also be used interchangeably.
- What is NGAC? The NGAC or New Generation Access Control is a new method of managing the authorization of a network developed by NIST. NGAC is based on ABAC, except that it uses a more defined approach for policy implementation.
Final Words
Role-Based Access Control (RBAC) and ABAC (Attribute-Based Access Control) are the primary access control methods for maintaining the confidentiality of data and protecting a network.
RBAC is based upon “Roles,” whereas ABAC uses “Attributes” defined and assigned to the users or resources in the network. While RBAC is simple and easy to manage, ABAC is complex to implement but allows finer security rules.
RBAC is best suited for smaller organizations with simple workflow infrastructure. ABAC, on the other hand, is better for medium-size or large enterprises with complex and geographically diverse workflows. In addition, depending upon the requirement or situation, companies can combine RBAC and ABAC, a model known as RBAC – A, for a more feasible and robust network infrastructure.