We may earn a commission if you make a purchase through the links on our website.
Attack Surface Analysis Guide

UPDATED: June 27, 2024
Learn what it takes to map your attack surface, and what methods are available to keep you protected.
As your business expands, and your number of assets increases, the number of ways that you can be attacked also increases. It is therefore important for you to expand your walls of defense to cover your entire network—but how exactly do you do that? And how exactly do you keep track of every possible vulnerability on your network?
This article answers your questions by explaining how you can analyze and secure your attack surface, which is your external surface that is open to attack.
Here is our list of the best AWS monitoring tools & services: surface attack monitoring solutions
- ManageEngine ADAudit Plus – EDITOR’S CHOICE – Provides advanced monitoring, defending, and prevention features to safeguard your network effectively. The platform offers real-time monitoring and powerful policy-based rule-sets that make it easy for any size network to protect their attack surface. Access the 30-day free trial.
- Rapid7 InsightVM Best for extensive security monitoring, cloud/virtual support, customizable dashboards, and comprehensive integration capabilities.
- ImmuniWeb Discovery Ideal for enterprise-scale threat analysis with AI-driven monitoring and deep/dark web scanning.
- CoalFire Attack Surface Management Excellent for DevSecOps projects, offering extensive discovery, automation, and remediation support.
What is an Attack Surface?
An attack surface encompasses all points on your network that are capable of being attacked. It represents a lot, and effectively refers to every open port, every web-connected asset, and everything on your network that could be breached either physically or digitally. It is your entire externally facing surface.
While this scope sounds too large to handle, you will have barriers in place that reduce your attack surface. For example, a firewall protects all devices that sit behind it—reducing your attack surface from any number of devices to a single firewall. You might require a key to enter your server room—reducing your attack surface from a gargantuan number of physical ports to a single door. This is how you can visualize, and by extension support and reduce, your attack surface. Virtual assets and cloud-hosted assets all count towards your potential attack surface.
Analyzing your entire attack surface can still be extremely difficult, depending on the scale of your business. Since every asset can potentially be an attack surface, this also means forgotten or abandoned assets that haven’t been properly dealt with. It’s why cataloging and tracking all assets within your business is incredibly important and is the first step towards mapping and reducing your attack surface.
Each asset also has multiple facets to its attack surface—what do we mean by this? Well, to give an example, a single asset might have the following points of attack:
- Some physical unprotected USB ports
- An untested and unsecured piece of third-party software
- A handful of open ports that can bypass firewall traffic
- An unpatched piece of critical software
- A user—who could fall for any number of phishing/malware scams
This means that your attack surface isn’t exactly a flat record of every asset; each asset could provide more, or less, means of attack. Grouping devices properly helps to alleviate this kind of confusion, so long as each asset in a group is kept to the same standards. Group policies, team briefings, monitored hardware, etc. are all strategies that can simplify your attack surface by delineating the vectors of attack into easily understood groups.
What is ASM?
ASM stands for Attack Surface Management.
This all-purpose term covers several actions that your business should be undergoing to better manage your attack surface.
The most important part of ASM is discovery. This means progressively monitoring your network for any changes in your potential attack surface. Keep up-to-date records of your assets, both physical and virtual—and when an old asset is removed or replaced, take the time to ensure it can no longer pose a threat to your network inventory. As your business progressively grows and changes, discovery becomes exponentially important, and slacking on this will undoubtedly lead to security breaches.
The other half of ASM is mitigation. This means going through the steps to not only monitor your network infrastructure but put in place restrictions and policies to reduce your attack surface. Devices that connect to your network need to be properly classified, and they need to be grouped and assigned policy-based restrictions. New staff needs to be properly trained in basic network security rules. New software needs to be checked and kept up to date.
If your business is working on DevSecOps projects, where security is a key part of your development, then ASM is even more important to your pipeline. In this case, integration is also a deeply vital step for you to take. This means properly integrating the necessary steps to check the external-facing surface of your projects and mitigate the attack surface, as part of regular development. As we’ll discuss later, several ASM services can be smoothly integrated into your CI/CD pipeline.
ASM Made Simple
As your business expands, whether, through additional staff, new projects, or new digital/physical assets, you should now understand why ASM is critical. However, going about starting ASM can be a monstrous task, depending on how large your business infrastructure is already.
There are three ways that you can ultimately go about ASM—secure businesses should consider performing a mix of all three methods.
- Manual ASM which means going about ASM the hard way by doing it yourselves. This is easier for smaller businesses, or businesses that are just getting started, but gets exponentially harder the later you get started. Regardless of what method you choose, you should always be doing at least a little bit of this. Properly categorizing your assets, keeping your staff knowledgeable about network security risks, and keeping some physical assets behind closed doors—all of these manual steps are a part of fundamental ASM.
- Automated ASM through software platforms. This means paying for a third-party product that perpetually scans and catalogs your entire attack surface. This option is excellent for regular and consistent security as your company changes and expands. We discuss this in more detail below.
- Human-Driven ASM by teaming up with a third-party company that provides ASM services. This differs from automated ASM by keeping the work strictly human-oriented. You’ll be teamed up with experts who do all the hard work of categorizing and pen-testing your network assets. We also discuss this in more detail below.
Automated ASM Platforms
Relying on the assistance of software and services can massively increase your attack surface analysis capabilities. There is a variety of attack surface monitoring tools on the market, but generally, they each perform the same functions:
- Scan the web for potential threats that might interact with your assets
- Build a map of your attack surface
- Non-intrusively scan your third-party connections for vulnerabilities
These three main features are the core of most of these automated software solutions. The difference between them depends on the scalability of the platform, the means of deployment, and the information you get back. The best solutions also come with CI/CD integration capabilities that are crucial for DevSecops projects—this typically means an API, but also several pre-built integrations for things like Jenkins.
We’ve covered three different products below that come highly recommended when performing automated attack surface monitoring and threat remediation.
Our methodology for selecting automated ASM platform:
We've broken down our analysis for you based on these key criteria:
- The platform's ability to leverage comprehensive security data and research.
- How well the tool integrates with other systems and technologies.
- The platform's capability to adapt to different sizes and complexities of networks.
- The degree to which the tool can be tailored to specific organizational needs.
- Effectiveness in providing timely and actionable security alerts.
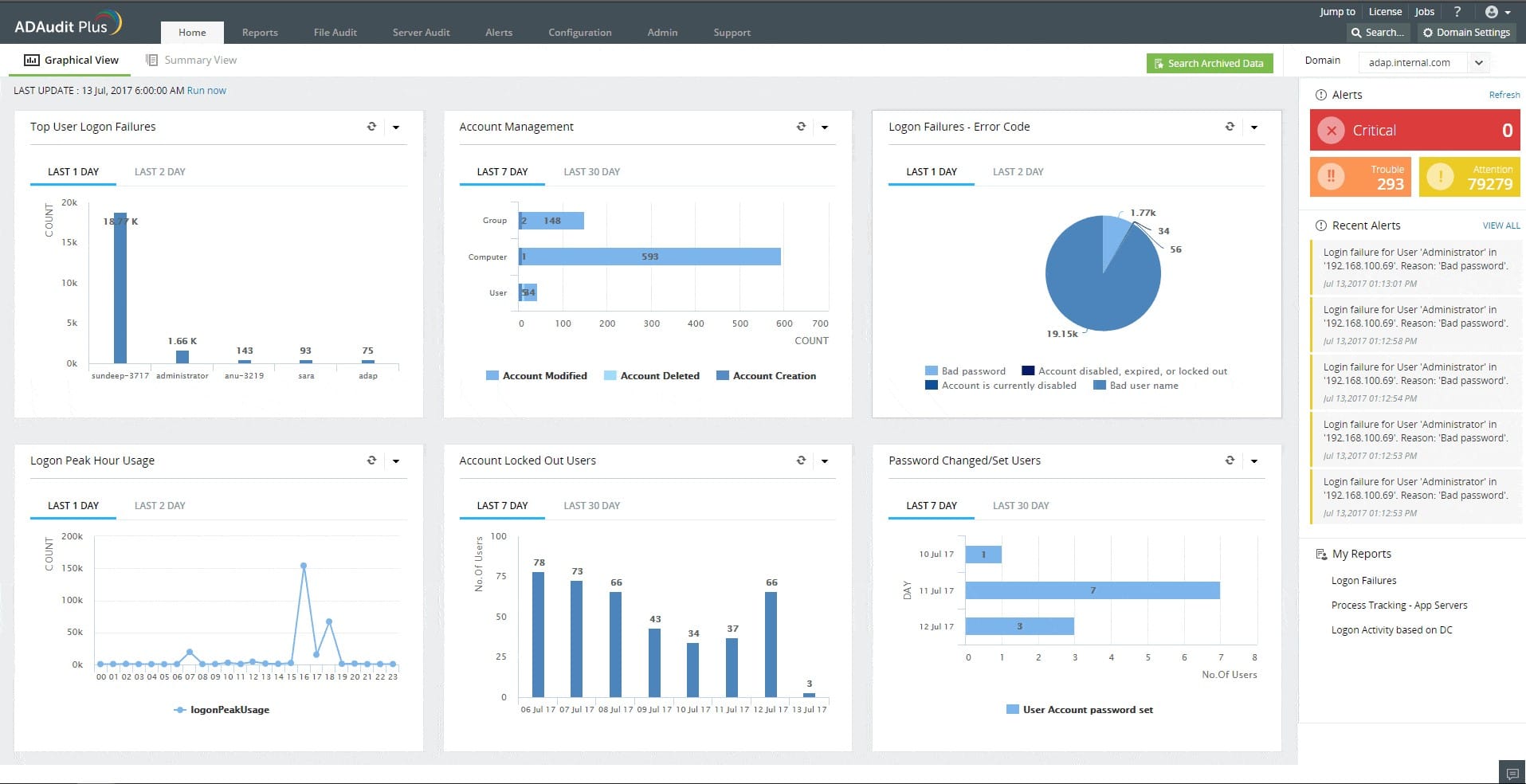
1. ManageEngine ADAudit Plus – EDITOR'S CHOICE
ManageEngine ADAudit Plus stands out as one of the best options for attack surface monitoring thanks to its comprehensive security features and reporting capabilities. Its real-time alerts ensure that potential threats are identified and addressed immediately, reducing the risk of security breaches. The detailed and customizable reporting capabilities facilitate compliance with regulatory requirements and provide valuable insights for security audits.
Key Features:
- Attack Surface Monitoring: Continuously monitors and identifies potential vulnerabilities across your network.
- Real-Time Alerts: Instantly notifies you of any suspicious activities or potential threats.
- Comprehensive Reporting: Generates detailed reports for compliance and security audits.
- User Activity Tracking: Monitors user behavior to detect anomalies and prevent insider threats.
- Customizable Dashboards: Allows you to tailor the interface to display the most relevant metrics and alerts.
Why do we recommend it?
We recommend ADAudit Plus for its robust attack surface monitoring capabilities, which are crucial for proactive security management. Its real-time alerts and comprehensive reporting features make it a valuable tool for maintaining network security and compliance.
User activity tracking also helps detect and mitigate insider threats, enhancing overall network security. The software's customizable dashboards allow users to focus on the most critical metrics, making monitoring both efficient and personalized. Despite its steeper learning curve, ADAudit Plus delivers exceptional value through its proactive security measures and in-depth analysis.
Who is it recommended for?
ADAudit Plus is recommended for medium to large enterprises that require detailed monitoring and reporting for compliance and security purposes. It's particularly suited for organizations looking to enhance their proactive security measures and prevent insider threats.
Pros:
- Proactive Security Measures: The attack surface monitoring helps identify vulnerabilities before they can be exploited.
- Immediate Threat Notifications: Real-time alerts ensure swift responses to potential security incidents.
- In-Depth Reports: Detailed reporting assists in meeting compliance requirements and enhances security audits.
- Behavior Analysis: Tracking user activity helps in identifying unusual patterns that might indicate insider threats.
- Flexible Interface: Customizable dashboards provide a personalized and efficient monitoring experience.
Cons:
- Pricey for Small Businesses: The cost might be prohibitive for smaller organizations with limited budgets.
Gain access to the 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top choice for attack surface monitoring because of its comprehensive approach to identifying and mitigating potential security threats. It excels in real-time alerting, ensuring that any suspicious activities are promptly addressed.
The detailed reporting capabilities are invaluable for compliance and security audits, providing clear insights into network vulnerabilities. User activity tracking adds an extra layer of protection by identifying unusual behaviors that could indicate insider threats. The customizable dashboards make it easy to focus on the most critical metrics, offering a tailored and efficient monitoring experience.
Download: Access the 30-day FREE Trial
Official Site: https://www.manageengine.com/products/active-directory-audit/sem/lp/attack-surface-analyzer.html
OS: Windows, Cloud-based
2. Rapid7 InsightVM
Rapid7 InsightVM is one of the best surface attack monitoring solutions on the market, owing to the extensive security research and testing conducted across Rapid7's inventory of security-focused products. For full security monitoring, the system uses a lightweight distributed agent that can be expanded to span cloud and virtual environments. Customizable dashboards may provide you with essential data on the fly, while insight metrics can help you manage vulnerabilities and improve responsiveness.
Key Features:
- Cloud/virtual support
- Customizable dashboards with deep insights
- Policy assessment and risk prioritization
- Goals and SLAs
- RESTful API
Why do we recommend Rapid7 InsightVM?
We recommend Rapid7 InsightVM due to its robust security research foundation, extensive integration options, and its ability to offer real-time insights and vulnerability management. It's a comprehensive tool that balances depth of monitoring with user-friendly features.
Building the greatest security tools necessitates a rich source of security data, one that is regularly updated to keep ahead of the curve, and InsightVM excels in this regard. InsightVM stands out for the sheer number of integrations it offers, in addition to the large amount of security data it collects. It comes pre-integrated with over 40 key technological platforms. For optimal security coverage, you may also leverage the built-in open RESTful API to increase your integration choices.
If you’re looking for a tool that serves as a good all-rounded, with decent associated costs combined with excellent features, then you might want to try the Rapid7 InsightVM’s free trial.
Who is it recommended for?
Rapid7 InsightVM is recommended for organizations of various sizes seeking a versatile and comprehensive attack surface monitoring solution. Its ability to integrate seamlessly with a wide range of platforms makes it suitable for businesses looking for a scalable and customizable security tool.
Pros:
- Extensive security research and integrations.
- Customizable dashboards for real-time insights.
- Effective for both cloud and virtual environments.
- Offers policy assessment and risk prioritization.
Cons:
- May be complex for smaller organizations or those new to attack surface monitoring.
Rapid7 InsightVM shines with it's unwavering commitment to security research and its expansive suite of security products. This platform distinguishes itself with a nimble, distributed agent that seamlessly extends across cloud and virtual spaces, ensuring comprehensive security monitoring.
The custom dashboards offer instant access to critical data, enhancing your ability to swiftly address vulnerabilities and elevate your security posture. Rapid7 InsightVM is not just about broad security coverage; it's about smart, adaptable, and thorough protection for today's complex digital landscapes. Experience its capabilities firsthand with a free trial.
3. ImmuniWeb Discovery
Immuniweb Discovery is a comprehensive threat analysis and surface monitoring solution that focuses on data breach prevention and web monitoring. Immuniweb was designed from the ground up to be an enterprise-scale solution with a global reach—while this means the solution is more expensive, it also ensures consistent quality and scalability.
Key Features:
- AI-driven OSINT surface monitoring
- Cloud and on-prem analysis
- Instant alerting
- Deep/dark web vulnerability scanning
- Third-party scanning
Why do we recommend ImmuniWeb Discovery?
We recommend ImmuniWeb Discovery for its advanced AI-driven OSINT surface monitoring capabilities. It excels in data breach prevention and deep/dark web scanning, making it a top choice for comprehensive web monitoring and threat analysis at an enterprise level.
It monitors your attack surface through the deep and dark web using OSINT and its AI-driven detection algorithms. The program can search for assets that have been abandoned or forgotten, and it provides real-time alerts when vulnerabilities are discovered. The system does not require an agent deployment or on-premise support because it is based on OSINT and is focused on external online threat analysis.
This solution is perfect if you’re looking for an enterprise-scale solution that can compete with security threats on the global front; while having excellent web discovery and asset detection. While there’s no free trial, there is a demo available on the company website.
Who is it recommended for?
ImmuniWeb Discovery is best suited for large organizations and enterprises that require a global-scale threat analysis solution. Its focus on advanced web discovery and asset detection makes it ideal for businesses with significant online presence and those needing detailed external online threat analysis.
Pros:
- AI-driven for efficient surface monitoring.
- Capable of deep and dark web scanning.
- Instant alerting for immediate threat response.
- Scalable for enterprise-level needs.
Cons:
- Higher cost and complexity may not suit smaller organizations.
4. CoalFire Attack Surface Management
CoalFire Attack Surface Management uses automation and guidance-based support to solve the problem of attack surface monitoring. The program can continuously scan the internet to monitor your external attack surface, creating vulnerability maps and relevant dashboard data that you can use to plan for your DevSecops projects or your personal network infrastructure.
Key Features:
- Comprehensive discovery features
- In-depth automation
- External attack surface monitoring
- Actionable data testing
- Remediation support and reporting
Why do we recommend CoalFire Attack Surface Management?
CoalFire Attack Surface Management is recommended for its blend of automation and expert guidance in attack surface monitoring. It is particularly effective in providing actionable security feedback and detailed vulnerability maps, which are essential for planning and executing DevSecOps projects.
Through risk exposure and pen-testing tools, the solution gives actionable security feedback that is translated into usable information with goals and estimates on how your DevSec team can address the detected issues.
This third solution is best if you’re analyzing the attack surface of a DevSecOps project, especially since it helps to create remediation goals that speed up development fixes by removing the need to spend time parsing the data.
Who is it recommended for?
This solution is recommended for organizations focusing on DevSecOps projects, where continuous and comprehensive attack surface analysis is critical. It's also suitable for businesses seeking to streamline their security processes with automated solutions that provide both detailed analysis and actionable remediation support.
Pros:
- Automated with guidance-based support.
- Comprehensive discovery and monitoring features.
- Actionable data testing for informed decision-making.
- Supports DevSecOps project goals.
Cons:
- May require technical expertise for optimal use.
Human-driven ASM Services
While automated software platforms like those listed above are excellent for perpetual and thorough attack surface monitoring, sometimes you need a human touch. There are several services available online that put you in contact with expert analyzers who do all the hard work for you. More importantly, they don’t just rely on software and automation.
Sometimes, threats take advantage of the blind spots of technology to exploit your vulnerabilities, and a human analyzer can find these blind spots where an automated system wouldn’t be able to identify them. What’s more, you know that you can trust the data that is reported to you, since it has already been read-through and thoroughly checked.
1. Bugcrowd
One such service is Bugcrowd, which is a crowd-sourced solution that puts you in contact with expert analyzers for you to map and remediate your attack surface. The service was built first for crowd-sourced bug fixing (hence the name) but has branched out into other areas—including attack surface analysis.
Key Features:
- Crowd-sourced expert analysis
- Personalized attack surface mapping
- Detailed risk reporting
- Asset discovery and management
Why do we recommend Bugcrowd?
Bugcrowd is recommended for its unique crowd-sourced approach to attack surface analysis, leveraging the expertise of skilled security researchers. This human-driven analysis provides a nuanced understanding of vulnerabilities, going beyond what automated software can detect.
The company's experts are hailed as expert ‘hackers,' capable of turning the tide on vulnerability threats with a personal touch that software cannot match. The experts provide complete attack surface maps to find neglected or abandoned assets. They produce detailed risk reports that outline exactly what has been discovered and what can be done to resolve any vulnerabilities. The solution places a premium on asset discovery and management.
This service is best used for occasional, human-focused analysis, possibly in conjunction with an automated software solution. Since Bugcrowd can provide other services like bug fixing, you can feasibly pipeline your projects alongside Bugcrowd and get them involved in other aspects of your DevSecOps projects.
Who is it recommended for?
Bugcrowd is ideal for organizations seeking a more personalized and detailed approach to security analysis. It's particularly beneficial for businesses that require occasional, in-depth analysis of their attack surfaces, and can be effectively paired with automated solutions for a well-rounded security strategy. Companies involved in DevSecOps projects would find Bugcrowd's services, including bug fixing and attack surface analysis, highly advantageous.
Pros:
- Provides crowd-sourced expertise for detailed attack surface analysis.
- Capable of identifying neglected or overlooked assets.
- Offers comprehensive and personalized risk reports.
- Enhances other DevSecOps project aspects with its versatile services.
Cons:
- May not be as continuous or automated as software-based solutions, requiring more occasional, targeted use.