We may earn a commission if you make a purchase through the links on our website.
The Best AWS Penetration Testing Tools

UPDATED: July 18, 2024
Rigorously test the security of your AWS instances with these specifically selected pen testing tools.
This article delves into the world of pen testing tools, preparing you to understand the enormous diversity of alternatives accessible. Understanding what to look for in a pen testing tool is critical whether you're a security professional looking for the finest tool for the job or an organization attempting to bolster your defenses.
Here is our list of the best AWS Penetration Testing Tools:
- Invicti To generate precise findings while eliminating false positives, Invicti employs the strength of its strong scanning engine, which is powered by cutting-edge Proof-Based Scanning technology.
- Acunetix Provides automated scanning techniques that detect a wide range of vulnerabilities, while Its powerful crawling algorithm probes the application comprehensively, mapping out its structure and identifying potential attack vectors. The product’s ability to execute authenticated scans is one of its standout features, allowing it to thoroughly assess access constraints and detect privilege escalation vulnerabilities.
- Burp Suite A popular penetration testing tool for evaluating the security of AWS applications. It enables you to intercept and manipulate traffic, launch various forms of attacks, and identify vulnerabilities in AWS-hosted web services.
- Nmap Network Mapper is a powerful network scanning tool that may be used to conduct AWS penetration testing. It aids in the detection of open ports, the discovery of hosts, and the mapping of network services. Nmap may be used to evaluate the security of AWS infrastructure from the outside.
- OWASP ZAP Another effective open-source web application security scanner is Zed Attack Proxy. It can be used to identify vulnerabilities, execute automated security checks, and analyze the security of AWS-hosted web applications.
- Metasploit A framework that includes a collection of tools for penetration testing and vulnerability assessment. It can be used to perform targeted attacks, exploit vulnerabilities, and test AWS system and application security.
Before we go into the upcoming products, let's take time to talk about the main elements to consider when choosing a pen testing tool. Penetration testing necessitates tools with extensive features, solid functionality, and ease of use.
Here are some critical points to remember:
- Scanning Capabilities A powerful pen testing tool should be able to scan multiple systems and networks for potential vulnerabilities and flaws. To give a full examination, look for instruments that support a wide range of scanning techniques, including active and passive scanning.
- Customization and Flexibility Because each organization's security requirements are unique, it's critical to select a solution that allows for customization. Look for capabilities that allow you to customize scans, set policies, and configure parameters to meet your specific needs.
- Reporting and Documentation To effectively disclose vulnerabilities and their severity, clear and detailed reporting is required. Look for technologies that produce detailed reports explaining found vulnerabilities and providing actionable recommendations for remedy.
- Integration and Collaboration The capacity to interface with other tools and collaborate with team members is critical in a world of interconnected systems. To streamline operations, look for technologies that integrate with issue-tracking systems, collaboration platforms, and automation frameworks.
- User Interface and Ease of Use A user-friendly interface is critical to maximizing the tool's efficacy. To encourage ease of use, look for solutions with intuitive interfaces, streamlined workflows, and thorough documentation and support.
Considering the above factors, we will look at six well-known and strong products: Acunetix, Burp Suite, Nmap, OWASP ZAP, Invicti, and Metasploit. Each tool has its own set of features, functions, and price structures that cater to various areas of penetration testing. You will be better equipped to choose the best tool for your needs if you grasp its strengths and weaknesses.
The Best AWS Penetration Testing Tools
1. Invicti
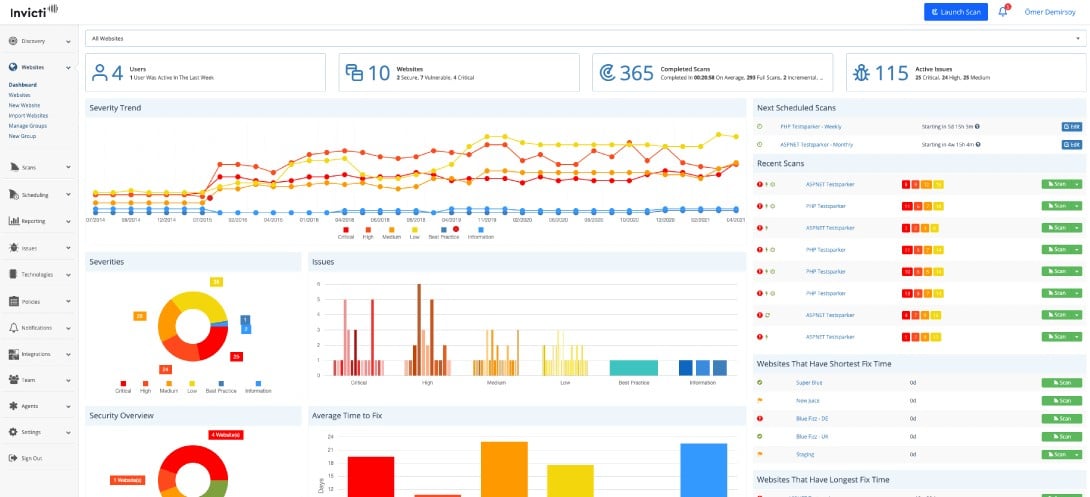
Invicti uses the strength of its powerful scanning engine, which is powered by its ‘Proof-Based Scanning’ technology, to produce accurate results while reducing false positives. Its powerful capability includes a plethora of capabilities geared to meet the complicated challenges of web application security.
Organizations may use Invicti to do full vulnerability assessments, scanning both classic online applications and contemporary Single Page Applications (SPAs) with ease. This extensive coverage guarantees that no stone is neglected, giving you peace of mind that weaknesses have been revealed, and potential access points have been reinforced.
Invicti's user-friendly interface allows security professionals to easily navigate through the scanning process. Its user-friendly dashboard displays scan results in a simple and structured manner, allowing you to quickly detect vulnerabilities and prioritize remedial activities. Organizations may take rapid and focused action thanks to detailed reports explaining found vulnerabilities and recommended remedial methods.
Invicti pricing is based on a subscription-based model that is adaptable to the needs of enterprises. The subscription fee may vary depending on criteria such as the number of web apps to be scanned, the desired degree of support, and the additional features necessary. While detailed pricing information is best received from Invicti, Invicti's dedication to providing cost-effective solutions remains a pillar of its products.
While Invicti has many advantages, it is crucial to examine the disadvantages. Invicti's effectiveness, like that of any scanning tool, is dependent on correct configuration and optimization to achieve accurate results. Users may need to devote time and effort to fine-tuning the tool to their individual environment and security needs.
While the tool may need to be configured and should be used in conjunction with a comprehensive security strategy, its ability to properly identify vulnerabilities and deliver actionable insights enables enterprises to strengthen their online apps and prevent possible attacks. Organizations can confidently negotiate the complicated environment of web application security, knowing that any possible vulnerabilities are exposed and their digital systems are secure.
2. Acunetix
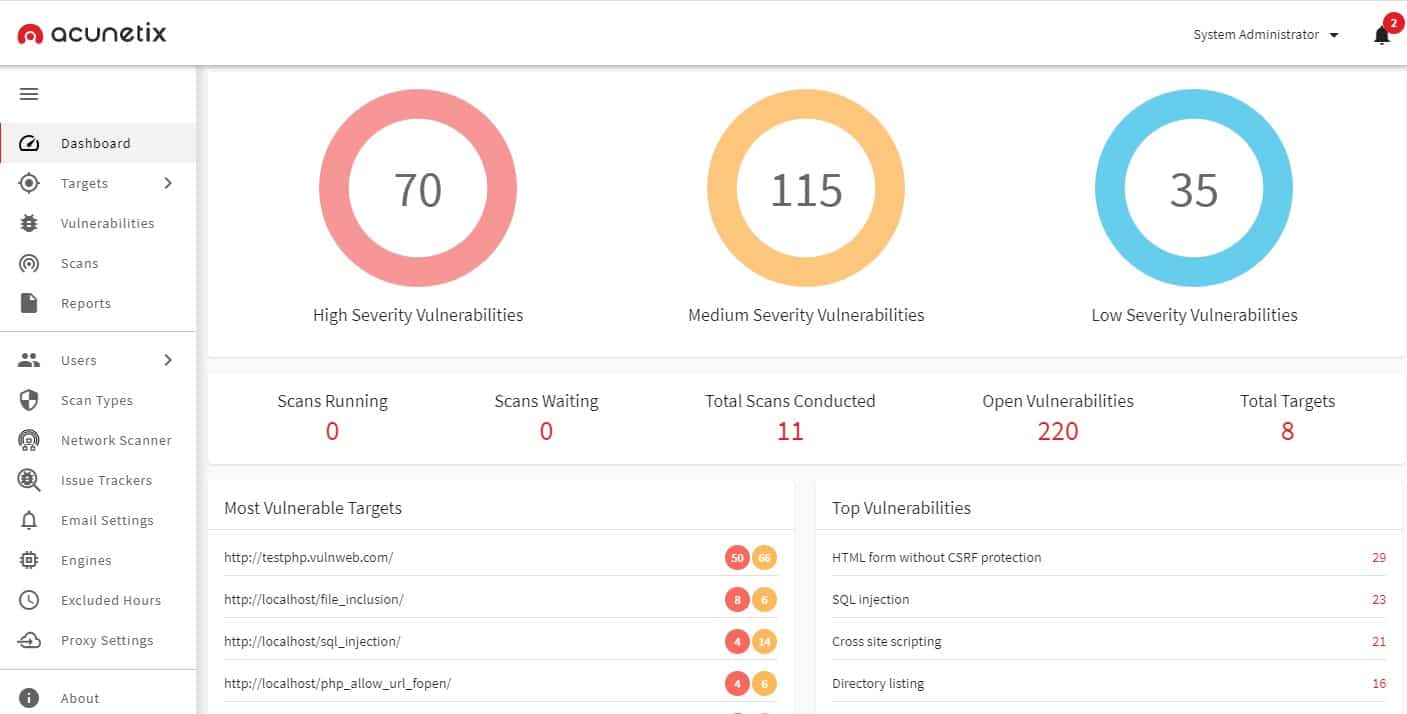
Acunetix excels at offering an automated scanning procedure that discovers a variety of vulnerabilities such as SQL injection, cross-site scripting (XSS), and unsecured server configurations. Its sophisticated crawling mechanism thoroughly investigates the application, mapping out its structure and finding potential attack vectors. Acunetix enables both black-box and gray-box testing, allowing security professionals to examine the application from both the outside and inside.
Acunetix's capacity to run authenticated scans is one of its notable capabilities, allowing it to comprehensively evaluate access controls and uncover privilege escalation flaws. Acunetix also integrates with issue-tracking systems, making it easier to collaborate on and handle detected vulnerabilities throughout the development lifecycle.
Acunetix's pricing is based on a subscription-based strategy. It provides several editions customized to specific purposes. The pricing tiers grant access to various features and functionalities, ranging from simple scanning to extensive reporting and integration possibilities. The cost is decided by parameters such as the number of target web apps, the number of concurrent scans, and the added support services.
Ultimately, the solution is a powerful web vulnerability scanner with numerous features and capabilities. Its automated scanning method, authenticated scanning, and integration possibilities make it an invaluable tool for discovering and mitigating vulnerabilities in AWS-hosted web applications. While false positives, resource consumption, and the learning curve can all be issues, Acunetix's subscription-based pricing and support services make it an appealing option for enterprises looking to improve the security of their web applications.
3. Burp Suite
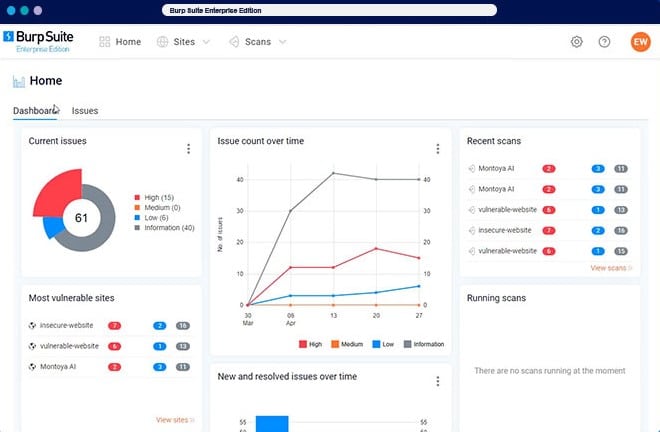
Burp Suite is a robust and adaptable penetration testing tool that is well-known for its extensive capabilities and user-friendly interface. It is widely used by security professionals and ethical hackers to evaluate the security of web applications, particularly those hosted on AWS. Burp Suite includes several capabilities that aid in the identification of vulnerabilities and the performance of security assessments.
The Intercepting Proxy, which allows users to intercept and change HTTP/S traffic between the client and the server, is at the heart of the Burp Suite. Security testers can use this to analyze requests and answers, modify parameters, and find potential security issues. Burp Suite also includes numerous scanning tools, including an active scanner that discovers and exploits vulnerabilities in web applications.
Burp Suite pricing varies depending on the edition selected. The community edition is free and includes many basic features, making it ideal for individual users or small projects. In contrast, the professional edition includes additional features like automated scanning, targeted scanning, and vulnerability verification. It is an annual membership service with tiered pricing dependent on the number of users. The enterprise edition provides additional capabilities for larger enterprises, such as centralized management, team communication, and connection with other security products.
As is common with automated scanning solutions, Burp Suite's scanning capabilities may produce false positives or false negatives. To ensure accuracy, security testers must manually verify and validate the detected vulnerabilities. Furthermore, Burp Suite concentrates on web application security and may be lacking in other areas, such as network-level assessments or AWS-specific vulnerabilities.
4. Nmap
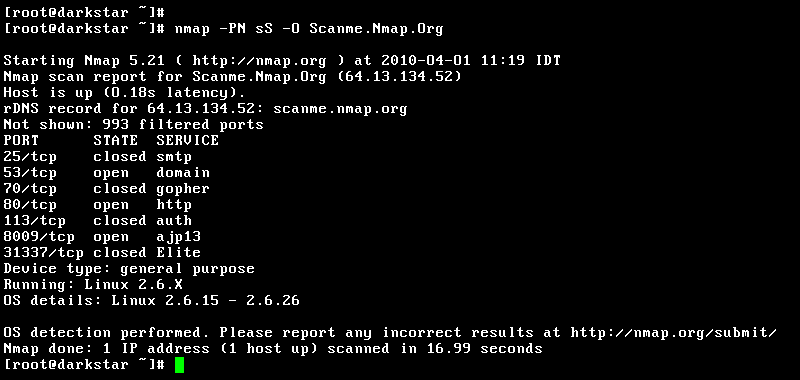
Nmap, which stands for Network Mapper, is a well-known and versatile network scanning program that is a must-have in the toolkits of security professionals and network administrators. Nmap provides a powerful set of services for checking the security of networks, including those hosted on AWS, thanks to its vast feature set.
Nmap's fundamental functionality is to allow users to execute extensive network scans, discovering hosts, open ports, and services running on the target network. To give an accurate picture of the network architecture, it employs several scanning techniques, including TCP SYN scan, UDP scan, and ICMP scan. The NSE (Nmap Scripting Engine) of Nmap allows users to automate processes, perform vulnerability scanning, and even create custom scripts for specialized scanning.
Nmap's pricing is based on an open-source paradigm, which means it is free for all users. This ease of use has aided its popularity and widespread adoption in the security sector. Because it is open source, Nmap benefits from continual community-driven development and enhancement, with new features and scanning capabilities being released regularly.
However, it is crucial to remember that Nmap has several possible drawbacks. One point to consider is its intricacy, which might be intimidating to new users. Nmap has a plethora of options and command-line parameters, so users must devote time to studying its intricacies to use it properly. Fortunately, there are a plethora of internet resources, tutorials, and user forums to assist users in mastering Nmap.
5. OWASP ZAP
OWASP ZAP, the Zed Attack Proxy, is a powerful and popular open-source web application security scanner. Designed by the Open Web Application Security Project (OWASP), ZAP offers a comprehensive suite of features and functionalities for identifying vulnerabilities in web applications hosted on AWS.
ZAP's key functionality is to give users a user-friendly interface for scanning and analyzing web applications. Because of its automated scanning capabilities, it can discover typical vulnerabilities like cross-site scripting (XSS), SQL injection, and unsecured direct object references. Manual testing is also supported by ZAP, allowing security professionals to interact with the application, modify requests, and examine answers.
Active scanning allows ZAP to crawl through the web application, scanning each component for potential vulnerabilities. It is capable of intercepting requests and responses, analyzing traffic, and performing fuzzing attacks to uncover security weaknesses. Additionally, ZAP's scripting engine enables users to create custom scripts and extensions to expand its scanning capabilities and adjust them to certain settings.
However, there are some potential disadvantages to employing ZAP. To begin, ZAP may necessitate some configuration and customization to be adapted to specific web application settings. To minimize noise and increase the tool's performance, users may need to spend time fine-tuning it.
6. Metasploit
For penetration testers, Metasploit is a powerful tool that allows them to replicate real-world attacks and exploit vulnerabilities. Its wide collection of vulnerabilities, payloads, and auxiliary modules allows testers to create customized attacks and analyze system resilience to various threats.
Metasploit provides testers with a great level of flexibility and control via the command-line interface and integrated graphical user interface (GUI), but it demands accuracy and comfortability with CLI tools. It provides both manual and automatic exploitation approaches, guaranteeing that every angle of attack is investigated and exploited to identify any security issues.
Metasploit pricing is based on a subscription basis. Metasploit Framework, Metasploit Pro, and Metasploit Community are among the editions available. The open-source version, Metasploit Framework, provides a robust framework for penetration testing and is freely available to everybody. Metasploit Pro has sophisticated capabilities for professional use, like reporting and collaboration tools. Metasploit Community achieves a mix between the two, providing extra features for enterprises with smaller-scale testing requirements.
While Metasploit's extensive feature set is a plus, it may also be intimidating to new users. Acquiring proficiency in using the tool's higher functions necessitates commitment, training, and experience. Furthermore, Metasploit's usefulness is dependent on maintaining current with the latest vulnerabilities and exploits. Keeping an up-to-date library of exploits and modules on hand guarantees that testers may use the most relevant techniques throughout assessments.
Conclusion
In this post, we looked at six powerful tools known for their ability to penetrate the depths of security flaws: Burp Suite, Nmap, OWASP ZAP, Acunetix, Invicti, and Metasploit. Let's take a moment to consider each of these tools and compare their advantages. When we compare these tools, we discover that Burp Suite and OWASP ZAP are largely focused on web application security testing, whereas Nmap is focused on network-level examinations. Acunetix provides a good mix of web vulnerability scanning and integration features. Metasploit, on the other hand, appeals to penetration testers with its extensive exploit library and automation features.
Burp Suite and Metasploit offer numerous editions with varying pricing structures, whilst OWASP ZAP and Invicti use subscription-based models. Nmap is an open-source utility that is freely available to everyone.
While each tool has its own set of capabilities and strengths, they all share the goal of discovering and mitigating security flaws. The final decision on which tool to utilize is based on the individual demands and objectives of a business or security expert.