We may earn a commission if you make a purchase through the links on our website.
The Best Business Security Suites

UPDATED: February 28, 2025
With so many computer security software options on the market, finding the exact fit for your business can be challenging. Some tools may lack capabilities, while others may be too expensive and complex to deploy. Plus, having many different tools from different vendors to cover your business' cybersecurity needs can also be overwhelming. In this article, we will go through the best business security suites. We will review different solutions for different business needs. Some of the business security suites here focus on protecting access, others on protecting endpoints, and others on the data itself.
Here is our list of the best business security suites:
- NordLayer Network Access – EDITOR'S CHOICE A SaaS-based adaptive network access and security solution designed to address business needs. Access a free demo.
- UTunnel – GET DEMO A secure VPN solution with Zero Trust access controls; ideal for businesses and individuals seeking reliable remote access.Access a free demo.
- GoodAccess A remote access solution that combines a cloud VPN, zero-trust access, and software-defined perimeter.
- Cloudflare’s SASE and Zero Trust A platform that protects hybrid environments via SD-WAN and Zero trust. Includes services like ZTNA, CASB, SWG, cloud email security, and more.
- Bitdefender GravityZone A cloud-based business security suite (EDR and XDR) that protects the business’s networks and endpoint infrastructure.
- Malwarebytes Enterprise security A solution based on different security components, including remote work, ransomware protection, and managed detection and response (MDR).
- ESET PROTECT Enterprise Protection A unified security management tool that comes as a range of software packages for SOHOs, SMBs, or enterprises.
- CoSoSys Endpoint Protector An industry-leading DLP solution designed to protect endpoints from leaking or misusing sensitive data
- TrendMicro One A unified cybersecurity platform capable of connecting data from multiple TrendMicro security applications.
- Avast Ultimate Business Security A suite of tools designed to protect the privacy of users, devices, and applications from multiple threats and risks.
- WatchGuard Endpoint Security A protection, detection, and response solution for businesses of all sizes.
What is a business security suite?
A business security suite is a collection of software utilities designed to protect a business’s networks, endpoints, users, or data. These suites may encompass different utilities that are related to each other and are designed to protect a business from malware, data loss, ransomware, and even zero-day exploits. A particular characteristic of a business security suite is that it integrates all these security utilities in a single central console so that an admin has all remote control and security monitoring.
Business security suites vary according to the solution, use case and industry. Some of these security suites are built with specific compliance in mind to target specific industries. Additionally, some software suites like these may only be suitable for small office home offices (SOHO) and sometimes for Small-Medium-Business (SMBs). But as a business and network grow, and so do the number of endpoints, security suites should focus on protecting data or endpoints.
Good examples of business security suites that use a name are as followed:
- EDR – Endpoint Detection and Response: Endpoint-based detection, analysis, and response to threats and risks. EDR is an improvement of an Antivirus system.
- XDR – eXtended Detection and Response: an evolution to EDR. XDR provides more capabilities, such as network-based detection, user behavior analytics, and more.
- DLP – Data Loss Prevention: a central cybersecurity system that attempts to eliminate risks and threats associated with data. This is similar to EDR software but focuses on protecting data rather than endpoints.
- SIEM – Security Information and Event Management (SIEM): a security solution that helps identify security threats and vulnerabilities. May use user behavior analytics and AI to automate the process.
- SASE – Secure Access Service Edge is a “concept” that describes the convergence of WAN and network security services, such as CASB, FWaaS, and Zero Trust, into a central cloud-delivered service model. SASE is a suite of security technologies.
- ZTNA – Zero Trust Network Access. Often a requirement for a robust SASE implementation, ZTNA is a set of principles and technologies that aim to control user access.
What features should you expect when looking for a business security suite?
As mentioned in the previous section, a business security suite should vary according to business needs.
But generally, Antivirus and firewall are usually the core utilities of a security suite. Advanced “business” security suites may include more functions like spam filters, website authentication, password management, protection against identity theft, anti-ransomware, anti-phishing, remote access controls (i.e., MFA or SSO), or VPN access. These business security suites may include additional capabilities, like backup and recovery, to help improve the security standpoint of a business even more.
Having access to all business security features from a single (central) console allows a much easier and cost-efficient way to implement and manage security. If it is a cloud-based console, it should be more convenient. A business security suite also helps have more transparency and an overview of all the resources of an environment, whether physical, virtual, or cloud-based.
Security suites for larger businesses?
The business security suites described above will help protect business networks and endpoints, but they may be limited for larger businesses. A business security suite designed “for larger businesses” should focus on protecting endpoints or the data itself. This type of solution should also include access to technical support and threat intelligence. More advanced business security services will include services like global proxy networks, website and API protection, or entire SASE (Secure Access Service Edge) platforms.
The Best Business Security Suites
1. NordLayer – ACCESS FREE DEMO
Nord Security, the same company that provides the popular NordVPN, also brings NordLayer, the former service known as NordVPN Teams. NordLayer changed the focus from a pure VPN for teams to a remote access solution. NordLayer is a SaaS-based adaptive network access and security solution for business needs. It is tailored for all levels and sizes of business, including SOHOs, startups, SMBs, to enterprises with multiple networks and endpoints.
Key Features:
- SSO and 2FA Support: Provides support for Single Sign-On (SSO) and Two-Factor Authentication (2FA) for enhanced authentication and security.
- Compliance Assistance: Assists with compliance for regulations including HIPAA, GDPR, ISO 27001, and PCI-DSS, ensuring adherence to industry standards and regulations.
- Zero-Trust Remote Access: Offers zero-trust remote access with multi-layer security features, ensuring secure access to business resources from any location.
- Private Gateways with Dedicated IPs: Allows creation of private gateways with dedicated IPs for enhanced security and control over network access.
- SASE Features: Strengthens remote access with Secure Access Service Edge (SASE) features, providing comprehensive network security and performance optimization.
Why do we recommend it?
NordLayer is highly recommended as a comprehensive remote access solution tailored for businesses of all sizes. Our recommendation for NordLayer is based on its robust security features, including SSO and 2FA support, compliance assistance for regulations like HIPAA, GDPR, ISO 27001, and PCI-DSS, and zero-trust remote access capabilities. With its focus on adaptive network access and multi-layer security, NordLayer ensures secure remote access for all levels of business, from SOHOs to enterprises, making it an ideal choice for organizations prioritizing security and compliance.
On a basic level, NordLayer provides a business-oriented VPN manager so that admins can control all VPN setups from a central management console. NordLayer allows access to all employees on a business to their awarded VPN service with more than 30 global locations. But NordLayer is more than a VPN manager; in fact, it provides zero-trust remote access with multi-layer security. It also brings to the table some of the core features of the SASE framework.
Who is it recommended for?
NordLayer is recommended for businesses seeking a reliable and secure remote access solution with comprehensive security features. It caters to businesses of all sizes, offering scalability and flexibility to meet diverse remote access needs. NordLayer is particularly suitable for IT administrators, security professionals, and business owners looking for a centralized VPN manager with multi-layer security features and compliance assistance. Whether you require SSO and 2FA support, compliance assistance, or zero-trust remote access capabilities, NordLayer provides the necessary functionalities to ensure secure remote access for all employees. Additionally, organizations prioritizing security, compliance, and ease of management will find NordLayer to be a valuable asset in their remote access toolkit.
Pros:
- Robust Security Features: Offers robust security features including SSO and 2FA support, compliance assistance, and zero-trust remote access capabilities.
- Compliance Assistance: Assists with compliance for regulations like HIPAA, GDPR, ISO 27001, and PCI-DSS, ensuring adherence to industry standards.
- Flexible Subscription Plans: Available in different subscription plans including Basic, Advanced, and Custom, providing flexibility to choose features based on organizational needs.
- Ease of Management: Provides a centralized VPN manager for easy management of VPN setups from a central management console, enhancing administrative efficiency.
- Scalability: Scales to meet the needs of businesses of all sizes, from SOHOs to enterprises, ensuring secure remote access for all employees.
Cons:
- Custom Plan Pricing: Pricing for the Custom plan is not readily available, requiring users to contact NordLayer for pricing information, which may be a barrier for some organizations.
- Learning Curve for Advanced Features: Advanced features like SASE may require some learning curve for users unfamiliar with network security frameworks.
NordLayer is available in different subscription plans; starting from Basic ($7 user/month), Advanced ($9 user/month), and Custom (contact NordLayer).
No free trial is available, but you can schedule a demo to see the product in action.
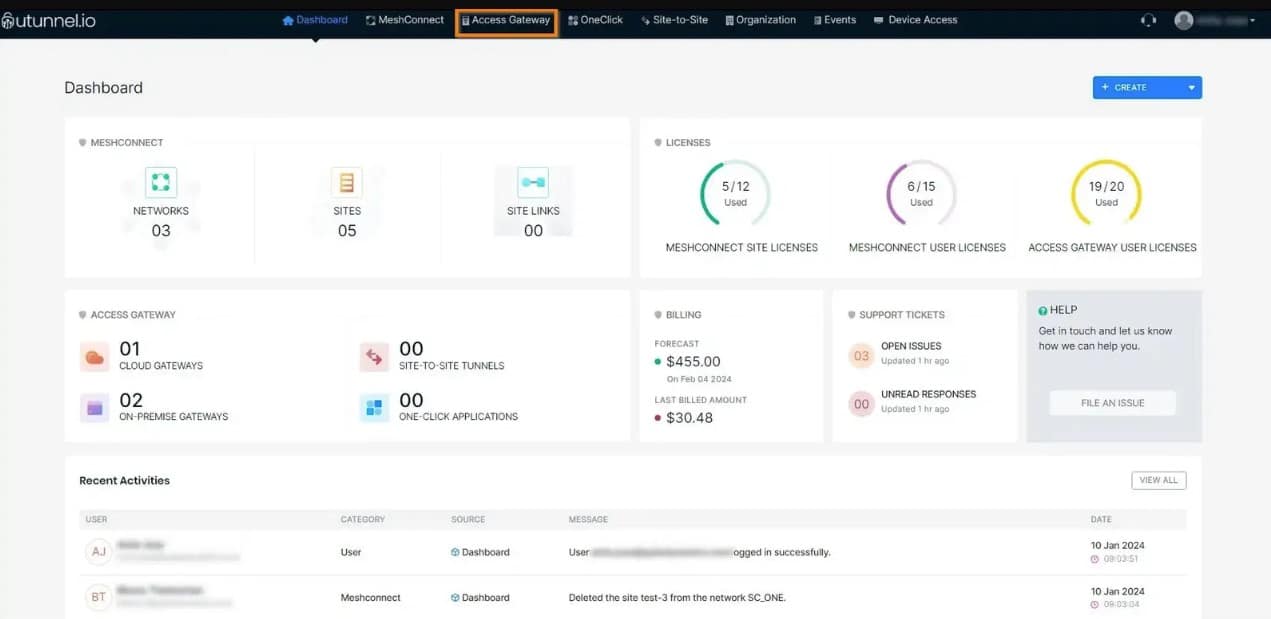
2. UTunnel – GET DEMO
UTunnel is a VPN solution designed for businesses and individuals seeking secure remote access, secure site-to-site links, and network management.
Key Features:
- Easy-to-Use Management Console: Intuitive web-based interface for effortless VPN setup and management.
- Site-to-Site VPN: Securely connect multiple office locations or networks.
- Multi-Cloud Support: Compatible with AWS, Azure, and Google Cloud for hybrid environments.
- Strong Encryption: Utilizes OpenVPN, IPSec, and WireGuard for top-tier security.
- Cross-Platform Compatibility: Works on Windows, macOS, Linux, iOS, and Android.
- Centralized Management: Easily manage users and devices from a single dashboard.
Why do we recommend it?
We recommend UTunnel for its simplicity, affordability, and enterprise-grade security. It provides a hassle-free setup, cross-platform compatibility, and excellent customer support. Whether for small businesses or large enterprises, UTunnel delivers reliable performance, ensuring secure remote access and efficient network management without compromising on ease of use.
It offers easy setup, strong encryption, and seamless integration with existing infrastructure. With features like site-to-site connectivity, multi-cloud support, and centralized management, UTunnel stands out as a reliable and scalable VPN service for modern networking needs.
Who is it recommended for?
UTunnel.io is ideal for businesses of all sizes, IT administrators, and remote teams needing secure access to company resources. It’s also suitable for individuals seeking a reliable VPN for personal use. Its scalability and flexibility make it a great choice for organizations with hybrid or multi-cloud environments.
Pros:
- Scalability: Adapts to the needs of small businesses or large enterprises.
- Affordable Pricing: Cost-effective plans for businesses of all sizes.
- Zero-Trust Security: Ensures strict access control and verification.
- Seamless Integration: Works with existing IT infrastructure without disruptions.
- Custom DNS: Provides DNS query protection
- Split Tunneling: Optimize traffic routing and enhance performance.
Cons:
- The self-hosting option is complicated: Should only be considered by businesses with technical experts on the payroll.
UTunnel is available in three plan levels: Basic ($6 per user per month), Standard ($8 per user per month), and Custom (priced by negotiation). There is a team size minimum of five members for the Basic and Standard plans; The Custom plan is designed for teams of more than 50 members. Schedule a free demo.
3. GoodAccess
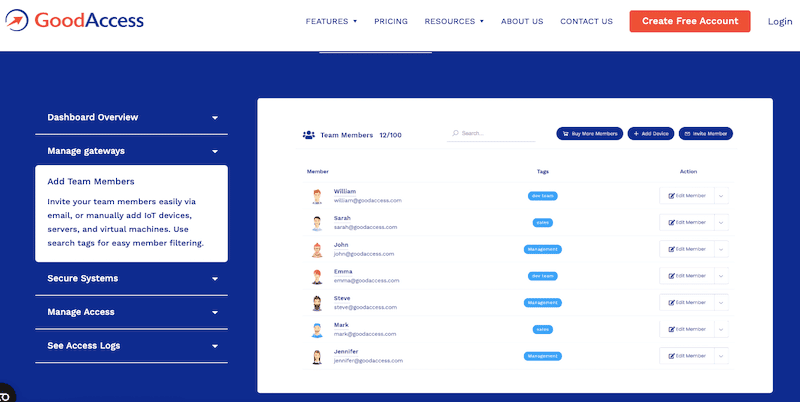
GoodAccess is a remote access solutions provider. Their main product, GoodAccess, is a business security suite that provides zero-trust global remote access to businesses of all sizes. The GoodAccess suite combines three vital security components; a cloud VPN, zero-trust access, and software-defined perimeter.
Key Features:
- Global Cloud-Based Virtual Network: Provides a global cloud-based Virtual Network for secure remote access from anywhere in the world.
- Identity-Based Access Controls: Offers identity-based access controls for enhanced security and access management.
- Compliance Assistance: Helps with compliance for regulations including GDPR, SOC2, and HIPAA, ensuring adherence to industry standards.
- Software-Defined Perimeter: Creates a virtual boundary around resources with software-defined perimeter, enhancing security and access control.
- Self-Intuitive Dashboard: Provides a self-intuitive dashboard with an overview and total control of remote access, allowing managers to add team members, strengthen team security, or troubleshoot via access logs.
- Instant Private Gateway Deployment: Allows instant deployment of a private gateway with a dedicated IP from 33 different locations, improving speed and creating backups.
Why do we recommend it?
GoodAccess emerges as a leading remote access solution provider, offering the GoodAccess business security suite tailored for businesses of all sizes. Our recommendation for GoodAccess is based on its comprehensive security components, including a global cloud-based Virtual Network, identity-based access controls, and compliance assistance for GDPR, SOC2, and HIPAA. With its focus on zero-trust global remote access and software-defined perimeter, GoodAccess ensures secure remote access for businesses, making it an ideal choice for organizations prioritizing security and compliance.
GoodAccess provides a self-intuitive dashboard with an overview and total control of remote access to employees and teams. The dashboard also allows managers to add team members, strengthen team security, or troubleshoot via access logs. In addition, GoodAccess also allows managers to instantly deploy a private gateway (from 33 different locations) with a dedicated IP to improve speed or create a backup.
Who is it recommended for?
GoodAccess is recommended for businesses seeking a reliable and secure remote access solution with comprehensive security features. It caters to businesses of all sizes, offering scalability and flexibility to meet diverse remote access needs. GoodAccess is particularly suitable for IT administrators, security professionals, and business owners looking for a business security suite with a cloud VPN, zero-trust access, and software-defined perimeter. Whether you require identity-based access controls, compliance assistance, or virtual boundary creation around resources, GoodAccess provides the necessary functionalities to ensure secure remote access for all employees. Additionally, organizations prioritizing security, compliance, and ease of management will find GoodAccess to be a valuable asset in their remote access toolkit.
Pros:
- Comprehensive Security Components: Offers comprehensive security components including a cloud VPN, zero-trust access, and software-defined perimeter, ensuring secure remote access for businesses.
- Compliance Assistance: Assists with compliance for regulations like GDPR, SOC2, and HIPAA, ensuring adherence to industry standards.
- Flexible Subscription Plans: Available in different editions including Starter (Free), Essential, Advanced, and Premium, providing flexibility to choose features based on organizational needs.
- Self-Intuitive Dashboard: Provides a self-intuitive dashboard for easy overview and control of remote access, enhancing administrative efficiency.
- Instant Private Gateway Deployment: Allows instant deployment of private gateways with dedicated IPs from multiple locations, improving speed and creating backups.
Cons:
- Custom Plan Pricing: Pricing for the Premium plan is not readily available, requiring users to contact GoodAccess for pricing information, which may be a barrier for some organizations.
- Learning Curve for Advanced Features: Advanced features like software-defined perimeter may require some learning curve for users unfamiliar with network security frameworks.
Four different editions start from Starter (Free), Essential ($4/user/month), Advanced ($8/user/month), and Premium ($10/user/month). Create a GoodAccess account to access a 14-day free trial with all premium features.
4. Cloudflare’s SASE and Zero Trust
Cloudflare is a Content Delivery Network (CDN) and DDoS mitigation service provider. It uses one of the internet's most extensive global networks to protect all your business's internet-connected infrastructure. Cloudflare uses various software packages or business security suites to protect anything from websites, APIs, internet apps, networks, endpoints, and employees.
Key Features:
- Zero Trust Network-as-a-Service Platform: Securing and improving hybrid environments via SD-WAN and Zero Trust.
- Internet-Native Zero Trust Services: Offers internet-native Zero Trust services via a central platform, ensuring enhanced security for apps running on the cloud, SaaS, or on-premise.
- Robust SASE Framework: Implements a robust Secure Access Service Edge (SASE) framework to strengthen business security and protect against threats.
- Website and API Protection: Ensures website and API protection, safeguarding internet-connected infrastructure from various cyber threats.
- DDoS Protection and FWaaS: Additional services include DDoS protection service and Firewall as a Service (FWaaS), providing comprehensive security solutions for businesses.
Why do we recommend it?
Cloudflare emerges as a leading provider of Content Delivery Network (CDN) and DDoS mitigation services, offering robust security solutions tailored to protect all aspects of your business's internet-connected infrastructure. Our recommendation for Cloudflare's SASE and Zero Trust services is based on its comprehensive security features, including a Zero Trust network-as-a-service platform, Internet-native Zero Trust services, and a robust Secure Access Service Edge (SASE) framework. With its focus on website and API protection and a wide range of security services including ZTNA, CASB, SWG, cloud email security, and DDoS protection, Cloudflare ensures enhanced security for businesses of all sizes, making it an ideal choice for organizations prioritizing security and reliability.
When it comes to protecting your business, Cloudflare provides various options. A SASE platform to secure and improve hybrid environments via SD-WAN and Zero Trust. Their zero trust security services (via ZTNA, CASB, SWG, cloud email security, and more) will help protect the access of apps running on the cloud, SaaS, or on-premise. An additional service to consider when looking at Cloudflare's security offerings is its DDoS protection service and FWaaS (Firewall as a Service).
Who is it recommended for?
Cloudflare's SASE and Zero Trust services are recommended for businesses seeking comprehensive security solutions to protect their internet-connected infrastructure. It caters to businesses of all sizes, offering scalability and flexibility to meet diverse security needs. Cloudflare's services are particularly suitable for IT administrators, security professionals, and business owners looking for a centralized platform for securing hybrid environments, implementing Zero Trust security measures, and protecting websites, APIs, internet apps, networks, endpoints, and employees. Whether you require SASE framework, Zero Trust security services, DDoS protection, or FWaaS (Firewall as a Service), Cloudflare provides the necessary functionalities to ensure enhanced security and reliability for your business. Additionally, organizations prioritizing security, scalability, and ease of management will find Cloudflare's services to be a valuable asset in their security toolkit.
Pros:
- Comprehensive Security Solutions: Offers comprehensive security solutions including SASE framework, Zero Trust services, website and API protection, DDoS protection, and FWaaS.
- Scalability and Flexibility: Caters to businesses of all sizes, offering scalability and flexibility to meet diverse security needs.
- Centralized Platform: Provides a centralized platform for implementing security measures, ensuring enhanced security and ease of management.
- Wide Range of Services: Offers a wide range of security services including ZTNA, CASB, SWG, and cloud email security, addressing various security requirements.
- Cost-Effective Plans: Plans and pricing vary according to the software package, providing cost-effective solutions for businesses of all sizes.
Cons:
- Learning Curve for Advanced Features: Advanced features like SASE framework and Zero Trust services may require some learning curve for users unfamiliar with network security frameworks.
- Custom Plan Pricing: Pricing for custom plans may not be readily available, requiring users to contact Cloudflare for pricing information, which may be a barrier for some organizations.
Plans and pricing vary according to the software package. You can begin with Cloudflare Zero Trust services for free with their Free Plan or pay $7/user on their Pay-as-you-go Plan. There is no free trial, but you can start with the Cloudflare Teams Free Plan.
5. Bitdefender GravityZone
Bitdefender GravityZone is a cloud-based business security suite that protects business networks and endpoint infrastructure from various threats and vulnerabilities, including malware, data breaches, ransomware, phishing, and more. Bitdefender GravityZone was designed to provide Endpoint Detection and Response (EDR) capabilities for small-to-medium businesses. It helps SMBs protect their entire infrastructure throughout the whole threat lifecycle.
Key Features:
- Patch Management: Offers patch management capabilities to keep systems up-to-date and protected against vulnerabilities.
- Next-Gen Antivirus Detection and Protection: Provides next-gen antivirus detection and protection against malware, ransomware, phishing, and more.
- Mobile Support: Extends protection to mobile devices, ensuring comprehensive security across all endpoints.
- Device Encryption: Offers device encryption to safeguard sensitive data and prevent unauthorized access.
- Automated Detection and Response: Implements automated detection and response capabilities to quickly identify and mitigate security threats.
- Enterprise Capabilities: Offers enterprise capabilities via GravityZone Business Security Enterprise, integrating with Security Event and Incident Visibility and incorporating EDR security with eXtended Detection Response (XDR) and risk analytics.
Why do we recommend it?
Bitdefender GravityZone emerges as a leading cloud-based business security suite, offering robust protection for business networks and endpoint infrastructure against various threats and vulnerabilities. Our recommendation for Bitdefender GravityZone is based on its comprehensive security features, including patch management, next-gen antivirus detection and protection, mobile support, device encryption, and automated detection and response capabilities. With its focus on Endpoint Detection and Response (EDR) for small-to-medium businesses, Bitdefender GravityZone ensures enhanced security throughout the entire threat lifecycle, making it an ideal choice for SMBs prioritizing security and reliability.
Bitdefender also offers enterprise capabilities via the GravityZone Business Security Enterprise. This solution protects enterprises by integrating with Security Event and Incident Visibility. GravityZone Business Security Enterprise also combines EDR security with eXtended Detection Response (XDR), incorporating risk analytics and hardening.
Who is it recommended for?
Bitdefender GravityZone is recommended for small-to-medium businesses seeking comprehensive security solutions to protect their network and endpoint infrastructure from various threats and vulnerabilities. It caters to businesses looking for advanced security features including patch management, next-gen antivirus detection and protection, mobile support, device encryption, and automated detection and response capabilities. Bitdefender GravityZone is particularly suitable for IT administrators, security professionals, and business owners looking for a cloud-based security suite with enterprise capabilities. Whether you require EDR security, risk analytics, or hardening capabilities, Bitdefender GravityZone provides the necessary functionalities to ensure enhanced security for your business. Additionally, organizations prioritizing security, scalability, and ease of management will find Bitdefender GravityZone to be a valuable asset in their security toolkit.
Pros:
- Comprehensive Security Solutions: Offers comprehensive security solutions including patch management, next-gen antivirus detection and protection, mobile support, device encryption, and automated detection and response capabilities.
- Scalability and Flexibility: Caters to small-to-medium businesses, providing scalability and flexibility to meet diverse security needs.
- Enterprise Capabilities: Provides enterprise capabilities for advanced security requirements, including EDR security, XDR integration, and risk analytics.
- Ease of Management: Offers a cloud-based management console for easy deployment, configuration, and monitoring of security measures.
- Cost-Effective Pricing: Offers budget-friendly pricing options for small-to-medium businesses, providing cost-effective security solutions.
Cons:
- Learning Curve for Advanced Features: Advanced features like EDR security and XDR integration may require some learning curve for users unfamiliar with endpoint security frameworks.
- Custom Plan Pricing: Pricing for custom plans may not be readily available, requiring users to contact Bitdefender for pricing information, which may be a barrier for some organizations.
GravityZone comes through different software packages. A budget-easy business security suite from Bitdefender GravityZone, to begin with, is GravityZone Business Security, starting at $258.99 (one-year subscription). Try GravityZone Business Security Enterprise through their free trial.
6. Malwarebytes Enterprise Security
Malwarebytes, from Malwarebytes Corporation, is originally a robust anti-malware solution for home and small office deployments. It has been a favorite anti-malware solution for a long time and has now grown into business security suites and solutions. Their Malwarebytes Business Security suite range in different capabilities and can protect businesses of all sizes, from SOHO to SMBS to enterprise.
Key Features:
- Endpoint Detection and Response (EDR): Provides Endpoint Detection and Response capabilities to detect and respond to advanced threats targeting endpoints.
- Ransomware Prevention: Offers ransomware prevention features with EDR, safeguarding endpoints against ransomware attacks and data encryption.
- Incident Management and Response: Facilitates incident management and response processes, enabling quick identification and remediation of security incidents.
- Threat Detection and Remediation Services: Provides threat detection and remediation services, including Managed Detection and Response (MDR), to proactively identify and mitigate security threats.
- Remote Work Protection: Includes features for protecting remote work environments, such as endpoint protection, USB device control, and protection from malicious websites.
Why do we recommend it?
Malwarebytes Enterprise Security, developed by Malwarebytes Corporation, stands as a robust business security suite offering comprehensive protection against malware and cyber threats. Our recommendation for Malwarebytes Enterprise Security is rooted in its extensive feature set, including Endpoint Detection and Response (EDR), ransomware prevention, incident management and response, and threat detection and remediation services. With a focus on protecting businesses of all sizes, from SOHO to SMBs to enterprise, Malwarebytes Enterprise Security ensures advanced security measures to safeguard endpoints and data, making it an ideal choice for organizations prioritizing cybersecurity.
The Malwarebytes Business Security suite comprises three different security components: remote work, ransomware protection, and managed detection and response (MDR). A highlight is the remote work feature which is designed to protect employees’ endpoints and their data. It protects from brute force attacks, controls USB devices, protection from malicious websites, and more.
Who is it recommended for?
Malwarebytes Enterprise Security is recommended for businesses seeking robust protection against malware and cyber threats, regardless of their size. It caters to organizations looking for comprehensive security solutions, including Endpoint Detection and Response (EDR), ransomware prevention, incident management and response, and threat detection and remediation services. Malwarebytes Enterprise Security is particularly suitable for IT administrators, security professionals, and business owners looking for an effective anti-malware solution with advanced security features. Whether you require protection for remote work environments, ransomware prevention, or managed detection and response (MDR) services, Malwarebytes Enterprise Security provides the necessary functionalities to ensure enhanced security for your business. Additionally, organizations prioritizing reliability, ease of management, and cost-effectiveness will find Malwarebytes Enterprise Security to be a valuable asset in their cybersecurity arsenal.
Pros:
- Comprehensive Security Features: Offers comprehensive security features including EDR, ransomware prevention, incident management and response, and threat detection and remediation services.
- Scalability: Caters to businesses of all sizes, providing scalability to meet diverse security needs.
- Effective Remote Work Protection: Provides effective protection for remote work environments, ensuring endpoint security and data protection.
- Reliable Threat Detection and Response: Facilitates reliable threat detection and response processes, enabling quick identification and remediation of security threats.
- Cost-Effective Pricing Options: Offers budget-friendly pricing options for businesses, providing cost-effective security solutions.
Cons:
- Pricing Variation: Pricing varies according to the number of devices and servers, which may lead to complexities in pricing management for some organizations.
- Learning Curve for Advanced Features: Advanced features like EDR and MDR may require some learning curve for users unfamiliar with endpoint security frameworks.
Pricing varies according to the number of devices and servers. Malwarebytes for Teams start at $37.49/device/year. Malwarebytes Endpoint Protection at $69.00/device/year and Malwarebytes Detection and Response at $84.99/device/year. Sign up to request a free Malwarebytes Business trial
7. ESET PROTECT Enterprise Protection
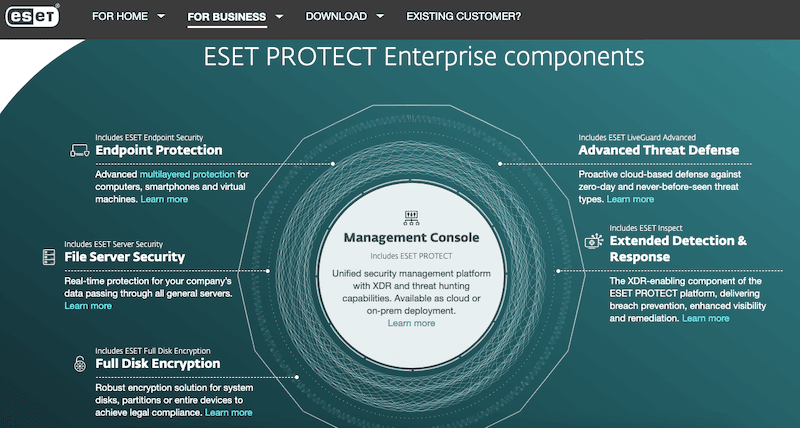
ESET is a leader in malware protection and internet security multi-platform solutions. ESET is the developer of the popular old-time antivirus known as NOD32. They have now grown from being a simple A/V solution into a provider of robust business security suites for businesses of any size, from SOHOs, and SMBs, to enterprises.
Key Features:
- Easy-to-Use Central Console: Provides an easy-to-use central console for unified security management across various operating systems.
- Access to Threat Intelligence: Offers access to ESET’s lab threat intelligence, enabling proactive threat detection and response.
- Detection and Response: Facilitates detection and response capabilities to identify and mitigate security threats effectively.
- Authentication and Encryption: Includes authentication and encryption features to safeguard sensitive data and prevent unauthorized access.
- Endpoint Protection: Provides endpoint protection to protect devices and endpoints against malware and internet security threats.
- World-Class Malware Detection: Offers world-class malware detection capabilities to ensure comprehensive security against evolving threats.
Why do we recommend it?
ESET PROTECT Enterprise Protection, developed by ESET, stands as a robust business security suite offering comprehensive protection against malware and internet security threats. Our recommendation for Enterprise Protection is grounded in its user-friendly central console, access to ESET’s lab threat intelligence, detection and response capabilities, authentication and encryption features, endpoint protection, and world-class malware detection. With a focus on providing unified security management for various operating systems deployed across environments, Enterprise Protection ensures effective security measures to safeguard businesses of any size, from SOHOs and SMBs to enterprises, making it an ideal choice for organizations prioritizing cybersecurity.
ESET PROTECT, one of their business security suites, is a unified security management tool for various operating systems deployed across environments (from on-premise to cloud). It comes as a range of software packages for SMBs, from ESET PROTECT Entry, Advanced, to Complete (for larger businesses). In addition, ESET PROTECT also provides enterprise solutions, including XDR, MDR, and Mail Plus.
Who is it recommended for?
ESET PROTECT Enterprise Protection is recommended for businesses seeking robust protection against malware and internet security threats, irrespective of their size. It caters to organizations looking for a unified security management tool with comprehensive security features, including a user-friendly central console, access to threat intelligence, detection and response capabilities, authentication and encryption features, endpoint protection, and world-class malware detection. Enterprise Protection is particularly suitable for IT administrators, security professionals, and business owners looking for an effective business security suite with enterprise-grade security features. Whether you require protection for SMBs or larger enterprises, Enterprise Protection provides the necessary functionalities to ensure enhanced security for your business. Additionally, organizations prioritizing reliability, scalability, and comprehensive security solutions will find Enterprise Protection to be a valuable asset in their cybersecurity arsenal.
Pros:
- Comprehensive Security Features: Offers comprehensive security features, including central console management, threat intelligence access, detection and response capabilities, authentication and encryption, endpoint protection, and malware detection.
- Scalability: Caters to businesses of any size, from SOHOs and SMBs to enterprises, providing scalability to meet diverse security needs.
- Unified Security Management: Provides a unified security management tool for various operating systems deployed across environments, ensuring effective security measures.
- Proactive Threat Detection: Enables proactive threat detection and response through access to ESET’s lab threat intelligence, ensuring timely mitigation of security threats.
- Reliable Malware Detection: Delivers world-class malware detection capabilities to protect against evolving malware and internet security threats.
Cons:
- Complexity for Larger Enterprises: Advanced features like XDR, MDR, and Mail Plus may introduce complexity for larger enterprises in terms of deployment and management.
- Pricing Variation: Pricing may vary depending on the software package and deployment environment, which may require careful consideration for budget planning and management.
ESET provides a wide range of tools. To get a tailored solution that fits your specific needs, contact an ESET sales representative. Try the ESET Enterprise protection bundle for 30 days.
8. CoSoSys Endpoint Protector
CoSoSys Endpoint Protector provides industry-leading Data Loss Prevention- DLP software. It is an excellent option for businesses looking for (on-premises, virtual, cloud, or SaaS) security suites with comprehensive data protection for enterprises like portable storage devices, mobile endpoints, or cloud-based services. A DLP solution like CoSoSys Endpoint Protector provides various tools and processes designed to prevent sensitive data from being misused, lost, or accessed by unauthorized users.
Key Features:
- Enforce and Monitor Encryption: Provides capabilities to enforce and monitor encryption for sensitive data, ensuring data protection and compliance.
- Device Monitoring and Control: Offers device monitoring and control features to manage and secure USB drives and other removable storage devices.
- eDiscovery for Data-at-Rest: Facilitates eDiscovery processes to scan data-at-rest and identify sensitive information, enabling proactive data protection measures.
- Content-Aware Protection: Delivers content-aware protection mechanisms to prevent unauthorized access and misuse of sensitive data.
- Real-Time Alerting & Reporting: Provides real-time alerting and reporting functionalities to notify administrators of potential security incidents and generate compliance reports.
- Integration with SIEM: Seamlessly integrates with Security Information and Event Management (SIEM) solutions to enhance security monitoring and threat detection capabilities.
Why do we recommend it?
CoSoSys Endpoint Protector stands out as an industry-leading Data Loss Prevention (DLP) software, offering comprehensive data protection for enterprises across various deployment environments. Our recommendation for CoSoSys Endpoint Protector is rooted in its robust feature set, including encryption enforcement and monitoring, device monitoring and control, eDiscovery for scanning data-at-rest, content-aware protection, real-time alerting and reporting, and seamless integration with SIEM solutions. With a focus on preventing sensitive data loss, misuse, or unauthorized access, CoSoSys Endpoint Protector provides essential tools and processes to ensure comprehensive data protection for businesses of all sizes, making it an excellent option for organizations prioritizing data security and compliance.
Endpoint Protector will discover and classify sensitive data and identify policy violations (typically driven by compliance). It will help businesses comply with GDPR, HIPAA, PCI DSS, CCPA, and LGPD. Their Endpoint Protector discovers data, blocks unsafe USB drives, and safeguards network endpoints’ from insider threats and IP theft. In addition, it also provides end-to-end PHI, PII, and source code protection.
Who is it recommended for?
CoSoSys Endpoint Protector is recommended for businesses seeking industry-leading Data Loss Prevention (DLP) software with comprehensive data protection capabilities. It caters to organizations looking for security suites that provide data protection across various deployment environments, including on-premises, virtual, cloud, or SaaS environments. CoSoSys Endpoint Protector is particularly suitable for enterprises looking to safeguard sensitive data, such as portable storage devices, mobile endpoints, and cloud-based services, from potential threats and breaches. Additionally, CoSoSys Endpoint Protector is ideal for organizations aiming to comply with regulatory standards such as GDPR, HIPAA, PCI DSS, CCPA, and LGPD, by providing tools for data discovery, policy enforcement, and compliance reporting.
Pros:
- Comprehensive Data Protection: Offers comprehensive data protection features, including encryption enforcement, device monitoring, eDiscovery, content-aware protection, and real-time alerting.
- Regulatory Compliance: Helps organizations comply with regulatory standards such as GDPR, HIPAA, PCI DSS, CCPA, and LGPD, by providing tools for data discovery and policy enforcement.
- Flexible Deployment Options: Supports deployment across on-premises, virtual, cloud, or SaaS environments, providing flexibility to meet diverse organizational needs.
- Customizable Policies: Enables customization of data protection policies to align with specific security requirements and compliance mandates.
- Integration Capabilities: Integrates seamlessly with SIEM solutions, enhancing security monitoring and threat detection capabilities.
Cons:
- Pricing Transparency: Pricing information is not readily available on the CoSoSys official site, requiring potential customers to contact sales for a customized quote, which may introduce complexities in budget planning and management.
- Learning Curve: Advanced features such as eDiscovery and SIEM integration may require a learning curve for users unfamiliar with DLP solutions, potentially impacting deployment and usability.
Pricing is not listed on the CoSoSys official site. Contact sales to request a customized quote. Register to get a 30-day free trial of the CoSoSys Endpoint Protector online version or register for a free demo.
9. TrendMicro One
TrendMicro is an industry leader in cybersecurity solutions, providing a range of capabilities, including enterprise (hybrid) cloud security, network security, user protection, and detection and response. TrendMicro has been recognized as a leader in business security suites by industry experts like Gartner and Forrester.
Key Features:
- Managed XDR and Incident Response: Offers managed Extended Detection and Response (XDR) capabilities and incident response services to detect, analyze, and respond to security threats effectively.
- Built-in Support for Zero-Trust: Provides built-in support for zero-trust security principles, enabling organizations to establish strict access controls and verify user identities.
- Cloud Platform Compatibility: Supports major cloud platforms such as AWS, Microsoft Azure, and Google Cloud, ensuring seamless integration with existing cloud environments.
- Global Threat Intelligence: Utilizes extensive threat intelligence powered by more than 250 million global sensors to identify and mitigate security threats in real-time.
- Executive Risk Dashboards: Offers executive risk dashboards for senior management to visualize and understand cybersecurity risks and trends within the organization.
- Endpoint, Email, and Mobile Security: Provides integrated endpoint, email, and mobile security solutions to protect against a wide range of cyber threats across multiple devices and platforms.
Why do we recommend it?
TrendMicro One stands out as a comprehensive cybersecurity platform offered by TrendMicro, a recognized industry leader in cybersecurity solutions. Our recommendation for TrendMicro One is based on its robust feature set, including managed Extended Detection and Response (XDR) and incident response, built-in support for zero-trust security, compatibility with major cloud platforms such as AWS, Microsoft Azure, and Google Cloud, extensive threat intelligence powered by more than 250 million global sensors, executive risk dashboards, and integrated endpoint, email, and mobile security solutions. With a focus on providing unified cybersecurity capabilities, TrendMicro One offers organizations a holistic approach to cybersecurity, enabling effective threat detection, response, and risk management across multiple environments and platforms.
Trend Micro One is their unified cybersecurity platform, capable of connecting data from multiple TrendMicro security applications. It seamlessly integrates with Trend Micro Cloud One, Workforce One, Network One, Vision One, and Service One. TrendMicro One (with its integrations) would include hybrid cloud security, network security, user protection, and Extended Detection and Response with attack/risk management. All these capabilities are powered by Artificial Intelligence and global threat intelligence.
Who is it recommended for?
TrendMicro One is recommended for businesses and organizations seeking a comprehensive cybersecurity platform with integrated threat detection, response, and risk management capabilities. It caters to organizations of all sizes, from small businesses to large enterprises, looking for a unified cybersecurity solution capable of addressing the evolving threat landscape. TrendMicro One is particularly suitable for organizations operating in hybrid cloud environments and those seeking to strengthen their security posture across endpoints, email systems, and mobile devices. Additionally, TrendMicro One is ideal for organizations prioritizing zero-trust security principles and leveraging advanced threat intelligence to proactively detect and mitigate security threats.
Pros:
- Comprehensive Cybersecurity Platform: Offers a comprehensive cybersecurity platform with integrated threat detection, response, and risk management capabilities.
- Scalability: Scales to meet the needs of organizations of all sizes, from small businesses to large enterprises, operating in diverse environments.
- Cloud Platform Compatibility: Compatible with major cloud platforms, facilitating seamless integration with existing cloud environments and applications.
- Advanced Threat Intelligence: Leverages extensive threat intelligence to proactively detect and mitigate security threats in real-time.
- Unified Security Management: Provides unified security management across multiple TrendMicro security applications, enabling centralized monitoring and control.
Cons:
- Pricing Transparency: Pricing information is not readily available and requires contacting TrendMicro’s sales representative, potentially introducing complexities in budget planning and management.
- Integration Complexity: Integration with multiple TrendMicro security applications may require additional setup and configuration, leading to potential complexity in deployment and management.
For pricing information, contact TrendMicro’s sales representative. Try TrendMicro’s Apex One, all-in-one endpoint security, through its free SaaS trial.
10. Avast Ultimate Business Security
Avast is an internet security applications developer known for its renowned Antivirus and VPN services. They also develop a range of cybersecurity (free and paid) products, including computer security, browser protection, firewall, anti-phishing, anti-spyware, and anti-spam—their cybersecurity solutions work for different business sizes, including SOHO, SMBs, and MSPs.
Key Features:
- Antivirus Protection: Protects devices with advanced antivirus capabilities to detect and remove malware, ransomware, and other cyber threats.
- Firewall and Wifi Inspector: Includes firewall and wifi inspector features to secure network connections and identify potential vulnerabilities.
- Remote Access Shield: Provides remote access shield functionality to prevent unauthorized access to devices and applications.
- Behavior-Based Machine Learning and AI-Enabled Tools: Utilizes behavior-based machine learning and AI-enabled tools to proactively detect and respond to evolving cyber threats.
- VPN and Password Protection: Offers VPN and password protection features to safeguard privacy and enhance security while accessing the internet.
- Patch Management: Facilitates patch management for Windows systems to ensure that devices are up-to-date with the latest security patches and updates.
- Ransomware Protection: Protects against ransomware attacks by detecting and blocking malicious ransomware activity before it can encrypt files and compromise data.
Why do we recommend it?
Avast Ultimate Business Security is a comprehensive cybersecurity suite designed to protect businesses of all sizes, including SOHOs, SMBs, and MSPs, from a wide range of cyber threats. Our recommendation for Avast Ultimate Business Security is based on its robust feature set, including advanced antivirus protection, firewall, wifi inspector, remote access shield, behavior-based machine learning, and AI-enabled tools. Additionally, Avast Ultimate Business Security offers essential security features such as VPN and password protection, patch management for Windows systems, and ransomware protection. With its focus on privacy, device protection, and application security, Avast Ultimate Business Security provides businesses with the necessary tools to safeguard their digital assets and sensitive information effectively.
Avast Ultimate Business Security is a suite of tools designed to protect users' privacy, devices, and applications from Malware, ransomware, zero-day and sophisticated cyberattacks. It is designed for SMBs ranging from 11 to 100 seats. Avast also provides a single console to manage all devices remotely and centrally.
Who is it recommended for?
Avast Ultimate Business Security is recommended for small and medium-sized businesses (SMBs) with 11 to 100 seats seeking comprehensive cybersecurity solutions to protect their digital assets, devices, and applications. It is suitable for organizations looking for a single, centralized security platform to manage and monitor all devices remotely. Avast Ultimate Business Security is particularly ideal for businesses operating in diverse environments, including remote and hybrid work settings, where robust protection against malware, ransomware, zero-day attacks, and other sophisticated cyber threats is essential.
Pros:
- Comprehensive Cybersecurity Suite: Offers a comprehensive suite of cybersecurity tools and features to protect against a wide range of cyber threats.
- Centralized Management: Provides a single console to manage all devices remotely and centrally, simplifying security management and monitoring.
- Advanced Security Technologies: Utilizes advanced security technologies such as behavior-based machine learning and AI-enabled tools to enhance threat detection and response capabilities.
- Privacy Protection: Includes VPN and password protection features to safeguard privacy and protect sensitive information while browsing the internet.
- Regular Updates: Facilitates patch management for Windows systems to ensure devices are protected against the latest security vulnerabilities and exploits.
Cons:
- Limited Scalability: Designed for SMBs with 11 to 100 seats, may not be suitable for larger enterprises with more extensive security requirements.
- Feature Complexity: Some advanced features such as behavior-based machine learning and AI-enabled tools may require additional configuration and expertise to maximize their effectiveness.
- Cost Considerations: Pricing and licensing models may vary, requiring careful consideration of budget and licensing requirements for SMBs.
Avast Ultimate Business Security pricing begins at $60.41/seat/year. Contact the Avast sales team to get a customized quote. Sign up to request a free Avast Ultimate Business Security 30-day trial.
11. WatchGuard Endpoint Security
WatchGuard (formerly Panda) is an industry leader in integrated and multi-functional threat management appliances. Their security devices are fast, intelligent, and capable of scanning for massive numbers of threats in real-time. WatchGuard has extended its portfolio and now provides various products and services, including Network Security, MFA, Secure WiFi, and Endpoint Security.
Key Features:
- Next-Gen Antivirus: Provides next-gen antivirus capabilities to protect endpoints against evolving cyber threats, including zero-day malware, ransomware, and APTs.
- Endpoint Detection and Response (EDR): Offers EDR functionality to detect and respond to advanced threats and suspicious activities on endpoints in real-time.
- DNS Filtering Solutions: Includes DNS filtering solutions to block malicious domains and prevent access to potentially harmful websites and content.
- Patch Management: Facilitates patch management via add-ons to ensure endpoints are up-to-date with the latest security patches and updates.
- Full Disk Encryption: Offers full disk encryption via add-ons to protect sensitive data and prevent unauthorized access to endpoint storage devices.
Why do we recommend it?
WatchGuard Endpoint Security offers comprehensive protection, detection, and response capabilities to safeguard endpoints against a wide range of cyber threats. We recommend WatchGuard Endpoint Security for its advanced features, including next-gen antivirus, endpoint detection and response (EDR), DNS filtering solutions, patch management, and full disk encryption. With its fast, intelligent threat management appliances and real-time scanning capabilities, WatchGuard Endpoint Security provides businesses of all sizes with robust endpoint protection against evolving cyber threats.
WatchGuard Endpoint Security is a world-class protection, detection, and response software for businesses of all sizes. It can safeguard endpoints against a wide range of threats, including zero-day malware, ransomware, Advanced Persistent Threats (APTs), phishing attacks, file-less malware, Potentially Unwanted Programs (PUPs), and in-memory exploits. All WatchGuard’s functionalities can be accessed and controlled via a remote cloud-based interface. This interface gives admins a detailed look into endpoints and detects abnormal behaviors.
Who is it recommended for?
WatchGuard Endpoint Security is recommended for businesses of all sizes seeking advanced endpoint security solutions to protect their endpoints from cyber threats such as malware, ransomware, phishing attacks, and file-less malware. It is particularly suitable for organizations looking for integrated and multi-functional threat management appliances that offer next-gen antivirus, EDR, DNS filtering, patch management, and full disk encryption capabilities. WatchGuard Endpoint Security is ideal for businesses that require remote cloud-based management and detailed endpoint visibility to detect and respond to abnormal behaviors effectively.
Pros:
- Comprehensive Endpoint Protection: Provides comprehensive protection against a wide range of cyber threats, including malware, ransomware, phishing attacks, and file-less malware.
- Real-Time Threat Detection and Response: Offers real-time threat detection and response capabilities through EDR functionality to detect and respond to advanced threats and suspicious activities.
- Cloud-Based Management: Enables remote cloud-based management for centralized control and detailed visibility into endpoints, allowing admins to monitor and manage endpoints effectively.
- Advanced Security Features: Includes advanced security features such as DNS filtering solutions and full disk encryption to enhance endpoint security and protect sensitive data.
- Scalability: Suitable for businesses of all sizes, from small businesses to large enterprises, offering scalable endpoint security solutions to meet varying security requirements.
Cons:
- Pricing Transparency: Pricing is not officially listed on the WatchGuard Endpoint Security site, requiring businesses to request a quote for pricing information.
- Add-On Requirements: Some advanced features such as patch management and full disk encryption may require additional add-ons, potentially increasing the overall cost of implementation and management.
- Learning Curve: Advanced features such as EDR may have a learning curve for admins unfamiliar with endpoint detection and response technologies, requiring training and expertise for effective utilization.
Pricing is not officially listed on the WatchGuard Endpoint Security site, so you’ll have to request a quote. Sign up to request a 30-day free trial of WatchGuard Endpoint Security.
Final Words
Business security suites vary according to business needs, size, and even industry. There is no one-size-fits-all solution that will adapt to the needs of your business. There are solutions only suitable for SOHO with VPN and antivirus management; others will focus on larger enterprises by protecting endpoints, networks, and data. Other security suites will change the approach and focus on safeguarding remote access.
In this business security suites article, we reviewed different software packages or solutions, including EDRs, XDRs, DLPs, SASEs, and ZTNAs. NordLayer and GoodAccess are alternatives for remote access (with ZTNA). Other security suites like Malwarebytes, ESET PROTECT, and Bitdefender focus on protecting endpoints.