We may earn a commission if you make a purchase through the links on our website.
The Best Device Control Software
UPDATED: April 4, 2023
In March 2021, Dobbins, a former employee of a medical device packaging company, was charged with a criminal complaint about hacking into the company’s network. He granted himself administrative privileges and deleted close to 120,000 shipping records. Such an event led to a significant delay in the medical equipment delivery to healthcare providers during the COVID-19 pandemic.
Without some data loss prevention or device control, former employees such as Dobbins, with access to inside resources can easily exfiltrate data, expose it, sell it, sabotage it, or even hijack systems. But that is not all. The unaware and innocent work-from-home employees may also fall victim to scams and infiltrate Malware that creates havoc on an internal network.
In this post, we’ll go through the top ten best device control software. These tools include software solutions that range in capabilities such as monitoring and blocking USB devices, preventing unencrypted transfers, or blocking all ports from specific types of devices.
Here is our list of the best Device Control Software:
- ManageEngine Device Control Plus – EDITOR'S CHOICE An endpoint security solution that monitors and controls multiple built-in peripherals, USBs, and devices. Download a 30-day free trial.
- Acronis DeviceLock DLP – FREE TRIAL A robust data loss protection solution including event logging, data shadowing, and alerting capabilities. Start a 30-day free trial.
- CrowdStrike Falcon Device Control An advanced device control tool that automatically discovers, monitors, and protects USB device storage.
- Endpoint Protector by CoSoSys An industry-leading cross-platform DLP solution. It protects data by controlling devices, enforcing USB encryption, and more.
- Symantec Data Loss Prevention by Broadcom An endpoint security and management leader. Symantec DLP protects data on endpoints, networks, and the cloud.
- McAfee DLP Its core DLP functionalities include discovery, prevention, monitoring, endpoint protection, device control, and cloud integration.
- Ivanti Device Control (Neurons) A device control solution allows you to discover, manage, control, and secure resources using a zero-trust approach.
- ESET Endpoint Protection Advanced A software bundle includes endpoint antivirus, disk encryption, mobile security, and file server security with device control capabilities.
- DriveLock A zero-trust platform that provides DLP capabilities, device control, and protection from Malware. It is Common Criteria EAL 3+ certified.
- Incydr by Code42 A next-gen SaaS data loss protection and prevention (DLP) solution.
What is Device Control Software? And how can it help prevent data loss?
External drives or USB pen drives may be used to exfiltrate or steal internal data such as intellectual data, proprietary code, designs, plans, financial records, or customer lists, so they must be monitored and controlled in real-time. In addition, these devices may also infiltrate Malware, Trojan Horses, or malicious scripts that pose a potential risk to the organization.
Device control software allows you to monitor and control such removable devices. Device control is a crucial component within any solid and successful Data Loss Prevention (DLP) solution. To achieve this, the device control software does the following:
- Monitor data transfers from different removable devices.
- Allow or block access to removable devices like notebooks, smartphones, PCs, etc.
- Prevent transfers from unencrypted data or unauthorized devices.
- If data is unencrypted, some device control solutions can enforce encryption.
The best device control software
Our methodology for selecting the best device control software
We reviewed device control software platforms and analyzed the options based on the following criteria:
- Support for various devices, vendors, and environments
- Ability to restrict and provide access at scale and granular levels
- Ease of use and ability to deploy at scale
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
1. ManageEngine Device Control Plus – FREE TRIAL
ManageEngine, a division of Zoho Corp, is an industry-leading provider of IT management software. More than 50,000 organizations use their software in more than 200 countries.
Key Features
- Device and Port Control: Controls all ports and removable devices, this tool will monitor the devices connected and file actions and will block unauthorized access.
- File Access Control: Set role-based access like read-only to prevent file from copying from a particular user.
- Report and Audits: Users can schedule weekly or monthly reports to get an idea of devices connected, users who tried to connect, and the data activities they performed.
- Set Temporary Access: Users can set temporary access for a short period, and it needs approval when a specific user wants to access a file or folder.
Why do we recommend it?
ManageEngine Device Control Plus is recommended because it effectively addresses the risk of insider threats through removable media, a concern for 90% of organizations. With this solution, you can enforce strict control over devices, monitor unauthorized activities through a user-friendly dashboard, and prevent data tampering or loss. It empowers you to restrict unnecessary data movements and provides insights into all actions performed on your data.
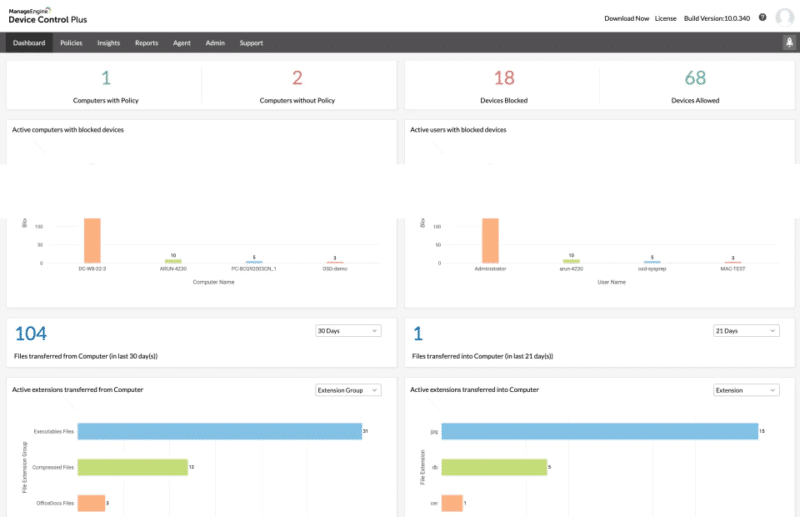
The ManageEngine Device Control Plus DLP software is an endpoint security solution that monitors and controls various built-in peripherals, USBs, and devices. It scans, controls, and blocks devices (including removable media, such as drives, auxiliary ports, and USBs) in real-time from doing unauthorized data transfers.
Who is it recommended for?
ManageEngine Device Control Plus is recommended for sysadmins and IT managers who need easy-to-use, feature-rich software for comprehensive IT management. It simplifies tasks, integrates seamlessly, and enhances security, facilitating digital transformation and supporting remote work. For senior-level IT executives, it offers stability as a trusted long-term partner with over two decades of experience in IT management. Rest assured, we'll continue to support your business needs as long as IT remains relevant.
Pros:
- File Transfer Control: Allows setting the specific limit of file sharing that can be allowed from your system. This way you can restrict and control file transfers.
- Trusted Device List: Users can make a list of devices that are trusted and safe to quickly access your network without hassle.
- File Shadowing: File mirroring allows users to copy important files to a secured location; hence, you can use your files in case they are lost.
- File Tracing: The user can monitor and record file activities like device name and location and computers.
Cons:
- Slower APN While Connecting with iOS: Many iOS users reported that the APN gets slower when they try to use a query. But that's not the case with Android; it works fine with Android.
Get a free 30-day trial.
EDITOR'S CHOICE
ManageEngine Device Control Plus stands out as our top choice due to its comprehensive data protection features. It enables businesses to enforce timely data protection measures by setting restrictions on file size and type, aligning with specific data handling needs. Moreover, the platform simplifies the identification and blocking of malicious devices by establishing a trusted device list. This proactive approach ensures that unauthorized devices are prevented from accessing endpoints, enhancing security and mitigating risks efficiently.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/device-control/
OS: Windows Server
2. Acronis DeviceLock DLP – FREE TRIAL
Acronis is a Singapore-based data protection and cybersecurity solutions provider. They provide services to over 5.5 million home users and close to 500,000 companies. Acronis offers the DeviceLock DLP, an endpoint data loss prevention solution tailored for businesses, among their comprehensive list of products and services. This solution is designed to reduce the risk of insider-related data leaks and threats.
Key Features:
- Data Loss Protection: Stops employees from leaking or stealing data by blocking any unauthorized attempts to access or move data, and find and safeguard sensitive data where it's stored.
- Modular Architecture: Get a clear view of data protection, ensure compliance by monitoring user actions and data flows, and save money by buying only the DLP features you need.
- Content Analysis and Filtering: Reduce insider threat risks by allowing only necessary business operations and blocking any unauthorized activities with policies users can't get around.
- Device Lock Discovery: Automatically find sensitive data stored insecurely, protect it with customizable actions, and get alerts, logs, and reports to stay on top of security.
Why do we recommend it?
Acronis DeviceLock DLP is perfect to manage expenses effectively and keep every module secure. It has various components for securing data while it is being used, transported, or stored. You can select the pieces you require, ensuring that you only pay for what is essential. This way, you can receive extensive data protection without spending more money. Acronis DeviceLock DLP is both adaptable and cost-effective, making it ideal for a wide range of companies.
DeviceLock DLP includes event logging, data shadowing, and alerting. But the most significant capability to control devices is its fine-grained contextual control based on multiple factors such as:
- User authentication
- Security control memberships
- Data types
- Device types
- Network protocols
- The direction of data flows
- Media state
- SSL encryption
- Data and time
- And many more
Aside from allowing you to enforce such controls, the software also analyzes and filters content to permit/deny data access and transfers. In addition, the software protects endpoints based on local data channels, including USB or FireWire, Bluetooth, WiFi, SMBs, printers, mobiles, social networks, Memory cards, FTP/FTPS, Torrents, forums, etc. Such channels can be blocked, allowed, alerted, or logged.
Who is it recommended for?
Acronis DeviceLock DLP is a good choice for organizations and experts who want careful control over how data is accessed and shared. It lets you do things like decide which USB devices can be used or give temporary access for offline tasks so data stays safe. Administrators can also allow specific storage devices and users while controlling network communication based on protocol and application settings. It works with Windows PC, Mac, and Windows servers, providing controlled ways to handle data securely.
Pros:
- Clipboard Control: Acronis DeviceLock DLP prevents unauthorized data transfers early on, like when copying text or images using the Windows clipboard or the print-screen function. It can block specific actions, such as print-screen, or control them based on what's being copied.
- Log Collection: Automatically gathers audit and shadow logs and sends them to a secure central location. This makes it easier for security investigations and auditing processes.
- Alerting: Sends real-time alerts through email (SMTP), network management (SNMP), or system logging (SYSLOG) when unauthorized actions occur. These alerts help administrators respond quickly to security incidents.
- Tamper Protection: Prevents local administrators from changing DLP policy settings on protected endpoints, ensuring that security measures remain intact and consistent across the network.
Cons:
- Specific CPU Limitations: The user reported certain limitations related to the operation of its modules, particularly in environments with specific CPU configurations.
Contact sales and download a 30-days free trial.
3. CrowdStrike Falcon Device Control
CrowdStrike is a leader in next-generation endpoint protection, A/V (AntiVirus), threat intelligence, and EDR (Endpoint Detection and Response) services. The core technology, CrowdStrike Falcon, is a software bundle designed to prevent and respond to all types of attacks and threats. One of the crucial elements that build up that bundle is the Falcon Device Control.
Key Features
- Cloud-Native: Cloud-native cybersecurity with unrivaled scalability and efficiency utility in place allows fast deployments and the removal of on-premises hardware.
- AI-Powered: It prevents and saves cloud data, enabling instant threat identification and preventive measures of predictive analytics.
- Supports Single Agent: Simplifies cybersecurity by consolidating intelligence and protection into a single agent, offering a user-friendly, centralized system with minimal system impact.
- Fully Managed Service: By choosing a fully managed solution based on cloud-native cybersecurity, the organization eliminates the risk of being hurt by security interruptions and can focus on its core business activity.
Why do we recommend it?
CrowdStrike Falcon Device Control is the best tool for effectively mitigating USB device risks. Users can keep their USB safe and secure by having granular control and insights that will protect against both external and internal threats. It allows users to monitor USB device operations automatically to look for potential risks. Users can quickly investigate data loss instances. Choose Crowdstrike if you want to enhance your organization's security with full user activity context, deep file visibility, and automatic source code identification.
The CrowdStrike Falcon Device Control scans for data exfiltration attacks. The software is deployed on endpoints alongside the Falcon Prevent, an EDR package protecting against threats and vulnerabilities. The Falcon Device Control is designed to provide automatic discovery, visibility, and protection for USB device usage.
Who is it recommended for?
CrowdStrike Falcon Device Control is ideal for enterprises that don't want to compromise on their organization's security. This tool is flexible and scalable, so as a user, you can also add more platform modules. It also allows you to integrate data from several sources, investigate partner applications, and create custom solutions using low-code tools. It includes a fully managed detection and response service to provide you with continuous ongoing protection against breaches through skilled management. In the end, it is best at proactive threat hunting, constant monitoring, and rapid remediation processes.
Pros:
- World-Class Intelligence: CrowdStrike integrates this functional element via their global Threat Graph for on-the-spot security intelligence and trumps any new threat with time-based, dynamic decisions.
- 24/7 Threat Hunting: it brings 24/7 expert intrusion forensics to the picture of security that will proactively detect and eradicate sophisticated threats that avoid automated systems, thus leading to a holistic security enhancement.
- Firewall Management: The former will enable the implementation of device access control features together with firewall management policies. Hence, only authorized devices and traffic can access the networks.
Cons:
- Dependent on Internet Connection: It is a cloud-native application that requires a constant Internet connection for real-time intelligence; however, the incidence is the lack of stable connectivity systems.
If you already own a license of Falcon Pro, Falcon Enterprise, or Falcon Premium, you can add a subscription to the CrowdStrike Falcon Device Control. Get a 15-day free trial of the Falcon Prevent software.
4. Endpoint Protector by CoSoSys
CoSoSys Endpoint Protector is an industry-leading cross-platform Data Loss Prevention (DLP) solution. It is a 2020 winner of the Cyber Security “Excellence Awards,” 2020 Infosec Awards Winner, and the 2020 Computing Security Awards Finalist. Its platform is available as a cloud service (AWS, Azure, and GCP) or as a virtual appliance.
Key Features:
- USB and Peripheral Control: It governs the use of USB devices and external peripherals and is also responsible for shutting down unauthorized data transfers that could cause security breaches.
- Content-Aware Protection: DLP features that detect sensitive info and keeps the network secure.
- Enforced Encryption: Ensures data transferred to external devices like pen drives is automatically encrypted, preventing data theft or loss.
- E-Discovery: Offers mechanisms for scanning and retrieving confidential data across the organization's network, which greatly improves the alignment of compliance and risk management goals.
Why do we recommend it?
Endpoint Protector by CoSoSys is user-friendly device control software that gets easily set up. It comes with predefined policies, which makes its deployment quick and hassle-free. You can customize policies easily to meet specific department needs by specifying device usage permissions. Moreover, you can also create whitelists and blacklists and define policies per user, computer, or group. When you use this tool, you will surely experience fewer interruptions to business operations with minimal interference. Thanks to advanced technologies, false positives, and resource wastage are minimized.
Endpoint Protector provides diverse capabilities to protect your data, including intellectual property protection or Personal Identifiable Information protection. The tool uses sophisticated text-categorization technology known as N-gram to identify intellectual property and monitor and control transfers accurately. The software also uses the eDiscovery feature to scan and protect personal information.
Device control capabilities
Its device control capabilities allow you to discover, lockdown, manage, and granularly control devices based on vendor ID, product ID, and serial number. You can also control the device’s USB and peripheral ports.
- Content-aware protection. Monitor, scan, control, and block transfers based on content and context inspection.
- They enforce USB encryption. Encrypt and secure USB devices by protecting data in transit.
- eDiscovery. Discover, encrypt, or remove sensitive data via manual or automatic scans.
- Compliance and Regulations. Achieve compliance and regulations of HIPAA, PCI-DSS, GDPR, SOX, and others.
Who is it recommended for?
We suggest Endpoint Protector for enterprises looking for centralized devices and data flow management. It helps to manage connected devices and data flows remotely via a single dashboard. You can also receive real-time alerts and reports. It gives freedom to configure policies and gain access to specific information and records to help prevent or mitigate incidents more quickly. Using the SIEM integration feature, you may customize reports and dashboards and analyze user behavior. Experts can use these features to improve data security, assure compliance, and streamline incident response processes.
Pros:
- Insider Threat Protection: Mitigates risks posed by insider threats by enhancing overseeing and managing data transmitting/device access.
- Compliance and Regulation: Aids enterprises in meeting legislation mandates for data protection (e.g., GDPR, HIPAA, etc.) using comprehensive DLP and device control.
- Supports Multiple Deployment Options: Different deployment options with on-premises, cloud-based, or hybrid solutions fosters compatibility with multiple IT infrastructures to serve clients.
- Protects Personal Identifiable Information: Designed for PII including protection against unauthorized access and transfers to avoid disclosure while complying with regulations.
Cons:
- Complexity and Overhead: Sophisticated control systems with diverse options may create a challenge, impacting the need for dedicated management and outline of the services provided.
5. Symantec Data Loss Prevention by Broadcom
Symantec, acquired by Broadcom in 2019, is an all-time cybersecurity industry favorite. Its endpoint security and management, web security, data loss prevention, email security, and privileged access management. Symantec has been awarded the “2020 Gartner Peer Insights Customers Choice for Endpoint Detection and Response” and the “Best Cross-Platform Endpoint Protection of 2020 by AV-Test”.
Key Features
- Data Leakage Prevention: Provides effective means to rectify and safeguard data from unlawful access and exports, and maintains confidentiality of sensitive information.
- Remediate Incidents: Provides tools for speedy reaction and remediation of data breaches and loss incidents so that incidents are contained and mitigated effectively.
- Critical Data Protection: Incorporates the latest technology to preserve corporate data no matter whether it is located within the network infrastructure or a third-party telecommunications system.
- Unified DLP Policies: Empowers designing and maintaining DLP policies only on a single console, which, as a result, makes it easier for the DLP efforts administration purposes, that are cross-platforms and multi-devices.
Why do we recommend it?
We recommend Symantec Data Loss Prevention as a complete Zero Trust solution because it guarantees endpoint, network, information, and identity security across on-premises and cloud infrastructures. You can efficiently safeguard your personnel, data, and tasks with greater visibility and control. It provides you with high accuracy and enterprise-scale security, which will reduce the risk of data breaches and compliance violations. It's a reliable option to protect confidential data belonging to your company and uphold legal compliance requirements.
Symantec DLP is their data loss prevention solution for data stored on endpoints, on-premises, and the cloud. It is famous for its capability to combine user activity monitoring with data risk controls. It gives you full device control capabilities with policy violations and abnormal user behaviors monitoring from a singular Symantec DLP for endpoints.
Who is it recommended for?
This tool is best fit for organizations needing comprehensive discovery, monitoring, and protection for sensitive information. Generally, experts use this tool to check and control over data across endpoints, network file shares, databases, and other repositories. It has great scanning capabilities and detects sensitive information in case of any loss or breach. This solution is for every big and small business that wants to safeguard their data assets and maintain compliance with data protection regulations.
Pros:
- Gives Accurate Visibility: Using it helps data map the data flow, use history across the whole organization, determine the possible risks and threats and reduce the carts.
- Meet Standard Compliance: Serves as a gateway for organizations to align with data security regulations and maintain strict reporting procedures.
- Classify MIP Labels: Integrates with Microsoft Information Protection (MIP) for data disposal classification and labeling, therefore, improving data governance and compliance.
- Uses Data-Centric Framework: Embraces a data-center security paradigm that protects data itself rather than just the boundary and covers the whole data protection of newly emerging demands.
Cons:
- Resource Intensive: However, implementation may demand a considerable focus on both the system and conditions at hand to manage the solution sufficiently.
Contact sales to request a demo or trial.
6. McAfee DLP
McAfee is one of the largest dedicated security IT companies. They provide proactive solutions and services that protect end-users and their data from virtually any online threat. In addition, they offer a data loss prevention solution in one suite, known as McAfee DLP. The suite includes McAfee DLP Discover, McAfee DLP Prevent, McAfee DLP Monitor, McAfee DLP Endpoint, McAfee Device Control, and MVISION Cloud Integration.
Key Features
- Malware Detection: Incorporates advanced malware detection capabilities to identify and block malware threats that could lead to data breaches.
- Internet Content Pack: Utilizes user and entity behavior analytics (UEBA) to detect anomalous activity and potential insider threats, enhancing the ability to prevent data loss.
- Hardware Health Pack: Monitors the health and security status of hardware devices, ensuring that they are not compromised and pose no threat to data security.
- Firewall Content Discovery: Employs deep inspection techniques to identify sensitive data being transmitted through the firewall, preventing unauthorized data exfiltration.
Why do we recommend it?
Because McAfee DLP integrates AI and ML into security processes, it is the best software to protect against data loss. For network and endpoint DLP devices, it enables centralized policy sharing and incident management through the use of McAfee ePolicy Orchestrator (ePO), which is both deployable and managed. Installed on the ePO server, the McAfee DLP extension is the first step in any deployment, as it acts as the central location for policy control and data analysis for all DLP apps.
The McAfee DLP platform allows you to deploy and manage standard policies from a central platform. Use the typical policy engine across on-premise resources, the cloud, or endpoints. You don’t need to recreate the policies to protect the same data; just synchronize them to affect any environment. Plus, you can manage all DLP violations and reports from the same platform, regardless their source is on-premises or cloud applications.
Who is it recommended for?
This tool is recommended by every organization or security specialist who wants certified integrations and simplified security solutions. Users don't need to spend a lot of time setting up when using pre-validated connectors to quickly solve essential security concerns. Trellix and its partners support these solutions, which go through extensive testing to ensure their dependability. To further improve control over data protection measures, the Domain Policy Content Pack also makes it possible to trace changes to security groups and policies. For those looking to effectively manage and secure sensitive data throughout their network, McAfee DLP is a great choice.
Pros:
- Checks for Email Content Loss: Specifically designed to monitor and protect against the loss of sensitive information through email, ensuring compliance and data security.
- Reveal DOS Attack: Capable of detecting and alerting on Denial of Service (DOS) attacks, which could be indicative of broader security incidents affecting data integrity.
- Threat and Risk Views: Provides comprehensive dashboards and reports that offer visibility into threats and risks, facilitating informed decision-making and prioritization of security efforts.
- User Authentication Events: Tracks and analyzes user authentication events to identify suspicious behaviors that could lead to data compromise, enhancing overall security posture.
Cons:
- Cost Considerations: As with many comprehensive security solutions, the cost of McAfee DLP could be a problem for smaller organizations or those with limited budgets.
Request a Free Demo.
7. Ivanti Device Control (Neurons)
Ivanti is a developer of IT security, IT Service & Asset Management, Unified Endpoint Management, and Identity Management software. The company was named ITSM leader by the 2021 Gartner Magic Quadrant for IT Service Management Tools.
Key Features
- Data Theft Prevention: Commit to the deployment of tightly managed protocols of data access and avoidance of stolen sensitive data.
- Endpoints Prevention: An endpoint security suite packed with strong capabilities to guard against different threats ranging from malware and ransomware, to phishing attacks by stringent controls and monitoring.
- Security Policies: Helps to create security policies confined to device and data use with which the organization can be compliant with the rules and regulations, both internal and external.
- Productivity Tools: Ensure the availability of tools that help enhance productivity whilst ensuring the safety of the device does not get compromised, all at the same time without jeopardizing the data security measures.
Why do we recommend it?
We recommend Ivanti Device Control because it is best at organization-wide control and enforcement capabilities. It uses a scalable client-server architecture with a central database, supporting various operating systems, including Windows, macOS, and Microsoft Surface devices (ARM64). This tool specializes in unauthorized removal to provide security even when users have administrative permissions. Hence, you can safely work and collaborate with a team without violating security policies.
Ivanti uses the following flow: Discover every endpoint > Manage and control them from a single console > Secure them with zero-trust and access technology > provide Service and asset management.
Ivanti provides a device control solution that lets you enforce security policies for removable devices (USBs, pen drives, printers) and data. Regardless of the device type plugged into the network, the software ensures the internal sensitive data can’t be transferred. In addition, Ivanti protects the internal network and endpoints from external threats like Malware.
Who is it recommended for?
Ivanti Device Control works well for enterprises that require centralized device management. This solution allows experts to centrally configure and control user and workstation access to permitted devices, cloud storage services, and Microsoft BitLocker System Drive encryption. Unauthorized devices, media, and users are automatically denied access, providing stringent data protection. This solution offers complete management features, making it ideal for enterprises that want to maintain tight control over device access and data protection.
Pros:
- Manage IT Service Delivery: Empowers management of IT services, combining delivery and reactions under the needed conditions to serve the users.
- Extend Service Management: The inclusion of the dashboard provides a tool that can be used beyond IT to focus on a more collaborative and efficient means for implementing service management practices.
- Optimize Software and Hardware Assets: This gives insight into software and hardware asset management practices that consequently ensure that all resources are utilized to full capacity without leading to cost inefficiencies.
- Get ITOM Insights: Providing perspectives on ITOM that help to make decisions based on the complete understanding of the IT performance and the nature of maintenance activities.
Cons:
- Complex Configuration: Because of a wide array of options and different customization processes, users can connect to the devices without special knowledge of the system itself but through heterogamous interfaces.
Get a quote for pricing details. Request a free demo.
8. ESET Endpoint Protection Advanced
ESET Endpoint Protection Advanced is a software bundle comprising Endpoint Antivirus, Full Disk Encryption, Cloud Sandbox, Mobile Security, File Server Security, and Endpoint Security. Besides providing robust device control, ESET Endpoint Protection Advanced keeps your endpoints secure from ransomware attacks, zero-day risks, and other threats.
Key Features
- Endpoint Antivirus: Equips a robust antivirus solution for endpoints, which entails employing heuristic detection to break through and cleanse malicious threats such as viruses, worms, and spyware.
- Mobile Security: This expands protection to mobile devices, offering functions like app scanning, anti-theft, and security audits that ensure that cell phone endpoints are as safe as possible from attacks.
- Remote Management and File Security: Disk Security Server also offers central control of security policies and monitoring of the network security status of file servers while encoding them from viruses and illegal access.
Why do we recommend it?
We recommend ESET Endpoint Protection Advanced since it works effectively at both home and work. It protects your computers from viruses and malware on both Windows and Mac. It also protects you from falling for fraudulent websites that attempt to steal your information. It also includes additional features such as Cloud-Powered Scanning and Device Control to ensure your security. Whether you are securing your personal computer or running a business, ESET Endpoint Protection Advanced keeps you secure from online threats.
The ESET File Server Security is an advanced protection module for data passing through all kinds of servers, including cloud-based servers (OneDrive) and network file storage devices. The module provides automatic device control for USBs, CDs, and DVDs. It allows you to scan, block, permit, or adjust permissions to access and use a specific device.
The ESET Full Disk Encryption is another critical component for device control, as it provides encryption capabilities managed by the ESET remote management console. This module helps you encrypt (and activate) system disks, partitions, and devices.
Who is it recommended for?
ESET Endpoint Protection Advanced is a good choice for businesses and cybersecurity experts who want strong endpoint security. It has a feature called Advanced Memory Scanner that watches out for harmful activities on your computer. You can also use cloud-powered scanning for better performance and finding threats, helping you manage communication with devices and store data effectively. It's fast, even when dealing with lots of computers, making it perfect for businesses that need top-notch protection and easy management.
Pros:
- Easy to Manage: It involves a User-Friendly Administration Console that allows fast management, configuration, and monitoring of security at endpoints.
- Simple Licensing: Simplified licensing options that directly clarify and help manage time and coverage, which is straightforward for businesses to understand.
- Lightweight: The final goal is a low-impact tool, without negatively impacting the performance of the system.
- Gives Endpoint Protection: Gives a one-stop solution to cover the plethora of risks that networks and data are exposed to on endpoints, enabling businesses to secure their data and their network.
Cons:
- Limited Advanced Threat Defense: It is effective in a broad spectrum of threats though it shouldn't be as evolved/sophisticated compared to other products against severe and more complex threats.
Request a quote. Download a full 30-day free trial.
9. DriveLock
DriveLock is a German-based IT and data security company. They are focused on protecting corporate data, devices, and systems by using the zero-trust approach. DriveLock has been awarded a TOP innovator by Infosec Awards, ISG Provider Lens, and Trust Seal. In 2021, DriveLock was also awarded Champion in the endpoint category by the “Professional User Rating Security Solutions 2021”.
DriveLock is a fully integrated zero-trust platform that provides data loss prevention, device control, and protection from Malware, Ransomware, and zero-day exploits. It helps you enforce a device control policy, which lets you decide which devices and external drives connect (or not) to your corporate network. You can configure policies to suppress CD and DVD burners proactively or simply prevent transfers from unencrypted data transfers or unauthorized media devices. Different operating systems and end devices support the solution. It can be deployed as an on-premise or cloud-based solution.
Key Features
- Application Control: Users can whitelist and blacklist particular apps and block their usage from the endpoint.
- Device Control: Allows the ability to encrypt USB media securely. You can also record which files were copied by whom in what format.
- Security Management: As it supports automation, you can schedule campaigns weekly or monthly, also showing security information in interactive display form.
- Bitlocker Management: Track disk encryption with smart authentication methods, powerful pre-boot, and secure one-time recovery methods.
Why do we recommend it?
DriveLock is the best tool for comprehensive data security features. It has a 30-day, hassle-free trial period, which allows you to enjoy all the features. Its features involve visibility, control, and security for shared data effortlessly. Users can gain insights into permissions and shares all files and directories with automated control and analysis in the background. DriveLock delivers quick visibility into security infractions and simplifies management with automated access control. It interacts perfectly with Microsoft OneDrive, Teams, and SharePoint Online to ensure safe file sharing for enterprises.
Who is it recommended for?
DriveLock should be considered for enterprises and experts looking for robust endpoint vulnerability management solutions. DriveLock Vulnerability Management allows users to identify and prevent potential malware assaults by regularly scanning for missing updates and obsolete software products. Organizations can successfully decrease cyber threats by regularly monitoring their security and compliance postures. DriveLock also assists in detecting and prioritizing undiscovered assets and vulnerabilities, allowing users to examine and manage them directly from the DriveLock Operations Center. This automation improves efficiency, lowers costs, and boosts cybersecurity throughout the firm.
Pros:
- Easy to Set Up: Easily available and quick to set up. You can rely on it for hosting to comprehensive management.
- Efficient and Economical: Efficient and scalable; allowing you to customize security standards according to company size, need, and growth.
- Supports Precise Security Management: Every company has different security policies, and this tool offers accurate security policies and configurations suitable to each organization's needs.
- Offers Maximum Data Protection: Offers maximum data protection to your cloud and drive where confidentiality matters the most.
Cons:
- Expensive Tool: Small businesses or startups might not be able to afford this tool for their necessary use.
Register to DriveLock and download a 30-days free trial.
10. Incydr by Code42
Code42 is a cybersecurity company focused on insider risk protection. The company has been awarded “Silver Winner” of the 2020 Cybersecurity Excellence Awards as Best Cybersecurity Company in North America, and winner of the PG’s 2020 Global Excellence Awards, as Best Insider Threat Solution.
Key Features
- Incydr Risk Dashboards: Comes with a risk dashboard that displays how much data is exposed, policy non-compliance, or training gaps to understand risk areas of organization.
- Risk Indicators: Shows contextual scoring based on the file activity so you can take instant action according to risk factors.
- Response Controls: The tool supports automated response controls that can be used for data protection without impacting workflow.
- Forensic Search: Provides a cloud-based index of every activity's metadata, which gives an idea of event details.
Why do we recommend it?
Incydr by Code42 is known for its comprehensive data leak and theft-detection capabilities. You don't need to use multiple security solutions like DLP, CASB, and UEBA. This tool offers full visibility across cloud and endpoint environments. It is best at detecting data leaks and thefts from various sources such as browsers, USB devices, cloud apps, email, and more. Moreover, contextual prioritization adds an extra layer of protection to your intellectual property, providing organizations with a robust and efficient solution to safeguard their sensitive data.
Code42 provides Incydr, a next-gen SaaS data loss protection, and prevention (DLP) solution. Incydr helps you mitigate insider risks, such as data exfiltration and exposure. For example, it can be integrated into cloud storage services to help detect and respond when end-users share the corporate’s sensitive data via such cloud services. In addition, it can also see when a device or smartphone is used to send a sensitive file attached to an email to an unknown recipient.
Who is it recommended for?
If your organization is facing challenges with departing employees and remote workforces then Incydr by Code42 is the best tool you must have. No matter how much you trust employees, they might take some data or a premium tool data with them for personal use. Incydr helps mitigate these risks by stopping data from leaving with departing employees and preventing data from going to untrusted locations. You can ensure data security and compliance even in remote work settings. This tool is best for safeguarding sensitive information when operating remotely.
Pros:
- Watchlists: Supports automated workflow management, which means you can keep track of user file activity.
- Offers Security Education: Various video lessons related to network security that are being sent to users to educate them on where it goes wrong.
- Useful for Remote Workspace: Handles a lot of data and keeps monitoring on comprehensive activity happening on the network. It checks for risky data activities and data leaks.
- Prevents IP theft: Helps protect your intellectual property by providing a complete view of activity and getting real-time alerts.
Cons:
- Lack of Integrations with Centralized Platforms: Many users find that the tool does not properly integrate with various centralized platforms like ConnectWise and Kaseya.
To buy Incyder, contact Code42 sales. Get Incydr for a 30-days free trial.
Final Words
Use device control software and avoid data exfiltration and other insider risks. Fortunately, you can start today!
Most of the ten best device control software shown here provides a 30-day free trial.
Device Control Software FAQs
How does device control software work?
Device control software works by monitoring the use of devices on a network and enforcing policies and controls to ensure that only authorized devices are used and that sensitive data is not transferred or copied to unauthorized devices.
What are some common features of device control software?
- Device monitoring and control
- Policy enforcement and configuration
- Device blocking and whitelisting
- Audit trails and reporting
- Remote management and deployment
What are some use cases for device control software?
- Data loss prevention
- Compliance with regulatory requirements (such as HIPAA or GDPR)
- Protection against malware and viruses
- Prevention of insider threats and theft
How can I choose the right device control software for my organization?
When selecting a device control software solution, you should consider factors such as the types of devices and operating systems that are supported, the level of granularity and control offered by the solution, the ease of use and deployment, and the pricing and licensing model. You may also want to evaluate the vendor's reputation and customer support.