We may earn a commission if you make a purchase through the links on our website.
The Best Endpoint Protection Software & Services for Protecting your Networks & Infrastructure!

UPDATED: November 1, 2024
Endpoints can be found across the entire network, from the LAN to the WAN. Some are connected remotely, while others are frequently on the move. Hackers find these endpoints as high-value targets as they are the first line of defense and are usually unpatched and vulnerable. According to an investigation done by Verzion, 30% of all security breaches involve some malware running on endpoints. In this article, we'll highlight the best endpoint protection software and services, and give a brief description, features, price, and download links.
Here is our list of the top Endpoint protection software:
- Guardz – EDITOR'S CHOICE This cloud-based SaaS package provides a comprehensive security environment that protects endpoints, web traffic, and emails, as well as networks with additional services that include Dark Web scanning and cloud data protection. Get a 14-day free trial.
- ThreatLocker – GET DEMO This cloud-based system prevents unauthorized software from executing, which means that malware and hacker utilities are unable to run and so malicious activity can’t be implemented. Access the free demo.
- ManageEngine Endpoint Central – FREE TRIAL A unified endpoint management system that includes vulnerability scanning and patch management. This system manages endpoints running Windows, macOS, and Linux plus mobile devices. Installs on Windows Server and Linux. Start a 30-day free trial.
- NinjaOne Endpoint Security – FREE TRIAL This package is part of a cloud-based remote monitoring and management (RMM) package designed for use by managed service providers. Access the 14-day free trial.
- N-able N-sight – FREE TRIAL A system for managing remote sites that includes endpoint detection and response. This is a cloud-based service.
- ESET Protect – FREE TRIAL This hybrid package provides four plan levels of endpoint protection with on-device elements and a central cloud controller. 30-day free trial.
- Sophos Endpoint Protection This system installs on Windows and Windows Server and can also protect devices that run Linux and macOS over a network.
- Bitdefender GravityZone Elite A coordinated protection system for all endpoints on a network that is a virtual appliance that runs on Linux Ubuntu.
- Symantec Endpoint Protection This system covers desktops, laptops, mobile devices, and servers. The administrator’s console is a cloud-based system.
- Trend Micro Apex One A site-wide service that coordinates endpoint protection for devices connected to the network. The console is a cloud-based system.
- CrowdStrike Falcon A suite of cybersecurity tools that can coordinate endpoint protection software that is installed on each device. the central console is a cloud-based system.
- Webroot Business Endpoint Protection A cloud-based service that covers all of the endpoints on a network through an onsite agent.
- CylancePROTECT An AI-driven endpoint detection system that is available for Windows, macOS, Android, and iOS.

Why is Endpoint Protection So Important?
An endpoint is a node or device connected to the corporate network, which is often exposed to other networks, such as the internet. This node can be located on-premise or remotely, and it is usually communicating back and forth with the corporate network.
Some common examples of these types of endpoints include:
- Laptops
- Desktops
- Smartphones
- Tablets
- IoT-sensors
- Cloud-based systems
- Virtual machines
- and many other devices
All of these different types of endpoints, with one interface connecting to the corporate network and another interface to the internet, pose a real threat to security. Endpoints open all sorts of new entries into the network. Manually protecting these endpoints and their entry point to the corporate network is almost impossible and extremely laborious. But there are solutions that can assist you in monitoring these endpoints seamlessly.
Endpoint protection software uses specific techniques and technologies to provide threat detection and response to all of these systems.
What to Look for in an Endpoint Protection Solution
An endpoint protection solution uses the server/client communication model. The “server” consists of a centrally managed software usually deployed in the cloud or on-premises. And this server communicates with every endpoint connected to the central network through an agent software.
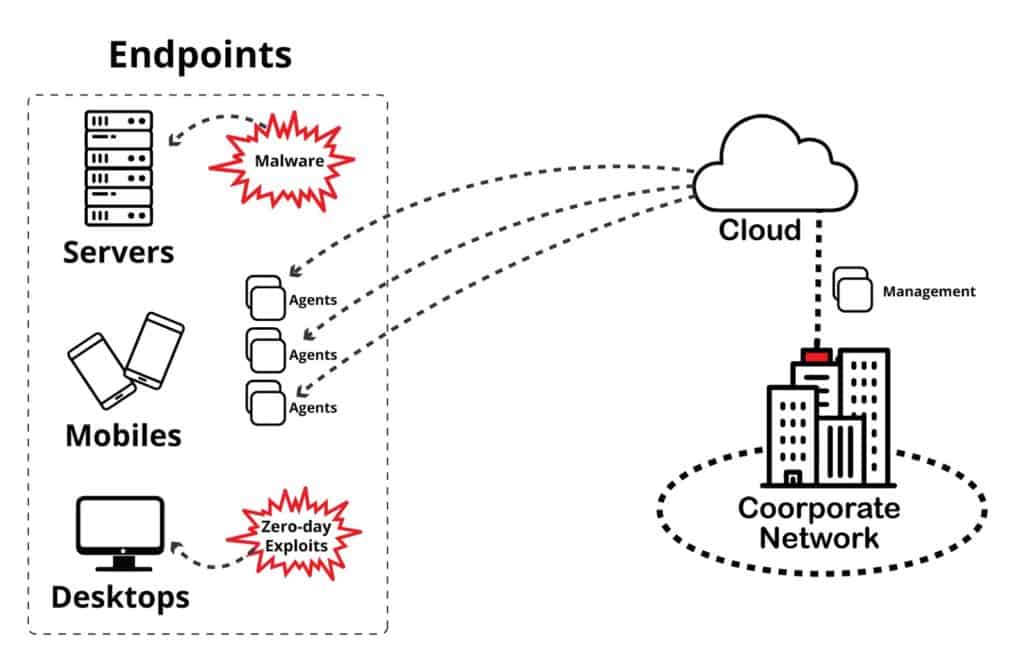
The endpoint protection software provides security and management across all devices that have access to the private network. It protects against external and internal threats by enforcing policies or by pushing security mechanisms across multiple and different devices.
Key Features:
- Automated detection and Response
- Threat Intelligence
- Advanced Malware Detection
- Device and App Control
- Limit Protocols or Close Ports
- Web Protection
- Automatic Scans
- Advanced Reporting and Alerting
- Full Visibility of Activities and Events
The endpoint protection software also keeps endpoints with updated software, such as Patching, Anti-Virus, Firewall, VPN, and HIPS (Host Intrusion Prevention Systems). And in some cases, the server can also work as a proxy or gateway for all authentication login attempts.
It is essential to notice that most modern endpoint protection software does not use the traditional signature-based protection mechanism. These tools provide alternative detection techniques empowered with Artificial Intelligence (AI), Machine Learning (ML), and behavior analysis to detect a wide arrange of known and unknown threats.
The Best Endpoint Protection Software & Services
Our methodology for endpoint protection software
We reviewed various endpoint protection tools and analyzed the options based on the following criteria:
- How much local resources each agent uses
- Deployment options available
- Facility to analyze protection and threats over time
- Graphical interpretation of data, such as charts and graphs
- Free trial period, a demo, or a money-back guarantee for no-risk assessment
- Good price that reflects value for money when compared to the functions offered
1. Guardz – FREE TRIAL
Guardz is a security package that protects endpoints, cloud drives, and email systems. The endpoint protection service scans for malware and intruders. The platform is hosted in the cloud and its dashboard can be accessed through any standard Web browser. The package is intended for use by managed service providers to look after the systems of their clients.
Key Features:
- Cloud-Based Dashboard: Access security management tools from any browser without on-premises installation.
- Automated Malware Detection: Instantly identifies and neutralizes threats like ransomware, spyware, and Trojans.
- Advanced Threat Protection: Detects stealthy attacks including fileless malware and persistent intrusions.
- Phishing & Email Scanning: Actively monitors email systems for phishing attempts and embedded malware.
- Dark Web Monitoring: Alerts if stolen credentials appear on known dark web marketplaces.
Why do we recommend it?
Guardz is recommended for its comprehensive threat detection and response capabilities. It safeguards against common attack vectors like emails, cloud apps, web browsers, endpoints, and external exposure and enhances employee awareness. It offers an all-in-one solution in a unified platform for advanced real-time protection.
Guardz scans for both automated and manual attacks on endpoints. The most common entry point for these threats is through emails with malware being hidden in attachments, and hackers gaining account credentials through phishing.
The platform scans the email systems in both Microsoft 365 and Google Workspace, which means Exchange Server/Outlook and Gmail. If email account details have already been stolen, they will probably be for sale on hacker forums. Guardz includes a Dark Web scanner, which will raise an alert if those email details are encountered. The platform is designed to be administered by managed service providers rather than being used by companies to protect their own endpoints.
Threat remediation is implemented automatically upon the detection of an attack. The tool also logs its discoveries and actions for analysis. The Guardz platform includes a library of employee awareness training courses, which reduces the security risks to a company. Even further automated attacks involve a variety of malware and Guardz spots them all. These include spyware, ransomware, trojans, adware, keyloggers, viruses, and fileless malware.
Who is it recommended for?
Guardz is recommended for fully-fledged businesses seeking comprehensive and integrated security controls. It's an ideal choice for experts and professionals who prioritize a unified solution. It has a growth hub feature, which includes customer service tools and prospecting reports, making it valuable for those aiming to enhance their business at an affordable price.
Pros:
- Comprehensive Malware Coverage: Detects and blocks a wide range of threats including spyware, Trojans, and fileless malware.
- Email Threat Prevention: Filters phishing, spoofing, and malware from inbound emails for Microsoft 365 and Gmail.
- Threat Response Logging: Tracks and logs all threat-related events for post-incident analysis.
- Employee Training Tools: Includes a phishing simulator and awareness programs to reduce user-related risks.
- Customizable MSP Dashboards: Allows branding of the interface for service providers managing client environments.
Cons:
- Limited Direct Access: Not intended for use by internal IT teams in end-user businesses.
There are three plans for Guardz:
- Starter for 1 – 99 users at $9 per user per month
- Pro for 100 + users at $5 per user per month
- Ultimate which is a managed security service and doesn’t have a published price
The charge rate for Guardz is per user and there is no minimum team size. You can examine the Guardz platform with a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for an endpoint protection system because provides comprehensive cybersecurity for businesses of all sizes. It is a suite of security services such as antivirus, anti-malware, and advanced threat detection, which work together to safeguard devices from a wide range of cyber threats. The platform includes automated backup processes, which continuously secure critical data, ensuring recovery options in the event of ransomware attacks or other data loss incidents. Guardz employs web filtering to block access to harmful websites and includes email security functionalities that protect against phishing attempts—one of the most common entry points for attacks. The cloud-based platform's versatility is another significant advantage, as it supports multiple operating systems; including Windows, macOS, and mobile devices, making it suitable for organizations with diverse technology environments. Guardz is a notable and effective endpoint protection system, combining essential security features with user-friendly management tools. Its focus on proactive threat prevention and data recovery positions it as a valuable asset for businesses looking to enhance their cybersecurity posture and protect sensitive information against evolving threats.
Download: Start a 14-day FREE Trial
Official Site: https://app.eu.guardz.com/signup
OS: Cloud-based
2. ThreatLocker – GET DEMO
ThreatLocker implements a threat prevention approach to software management that automatically blocks malware and unapproved packages. The tool doesn’t stop malware from getting on your endpoints but instead, it stops it from running, so they are just useless files and don’t represent a threat. You don’t need to detect malware or take mitigating action – you just need to delete the dead files.
Key Features:
- Application Whitelisting: Only approved software is allowed to execute, blocking everything else by default.
- Peripheral Device Control: Restricts USB and external device usage based on admin permissions.
- Hybrid Environment Support: Manages both on-premises endpoints and cloud resources from a unified platform.
- Ring-Fencing for Legitimate Tools: Prevents misuse of trusted applications like PowerShell through granular control.
- Cloud-Based Management Console: Centralized control across multiple locations with no need for local infrastructure.
Why do we recommend it?
ThreatLocker helps to block untrusted software, and safeguards the organization against ransomware by permitting only approved applications. It has a ring-fencing feature that prevents attackers from exploiting legitimate tools like PowerShell so that you can ensure that software operates within specified limits, enhancing overall cybersecurity.
The full ThreatLocker package provides blocks on USB devices and those memory sticks can only be used if they are specifically permitted by the administrator and only for use by a specified user. The platform also limits the resources that each software package can access. The ThreatLocker system can protect cloud accounts as well as on-site endpoints.
ThreatLocker provides a combination of systems that block unauthorized software, fence resources, and extend access rights management to include application activity as well as user permissions per resource. All software is blocked from executing by default. Packages that are registered in an allow list will run but you can then further fine-tune activity by allowing only certain software to access specific resources. That access list also includes user accounts, so specific actions can only be performed by a named user account with a specific application, acting on a specific resource.
Who is it recommended for?
It is recommended for anyone seeking top-notch support and dynamic control over network traffic. This tool is widely used in huge organizations for protecting confidential data. The tool has a US-based Cyber Hero Team, which offers a rapid response time of under 60 seconds. You can have control of your network because you decide what to allow and what not.
Pros:
- Fast Deployment: Simple initial setup makes it easy to get up and running quickly.
- Centralized Endpoint Control: Manages devices across different sites from a single cloud dashboard.
- Strong Hybrid Support: Works effectively across both local infrastructure and cloud accounts.
Cons:
- Limited Access Control Tools: Lacks full-featured permissions and role-based access management.
As it is a cloud-based system, there is no download for ThreatLocker. Your first point of contact should be to request a demo.
3. ManageEngine Endpoint Central – FREE TRIAL
ManageEngine Endpoint Central – formerly Desktop Central – gives you a complete overview of your network and helps you keep everything patched including 3rd party software and operating systems. This tools helps you not only automate patch management for Windows systems, but for Linux and Apple Mac systems as well.
Key Features:
- Automated Patch Management: Keeps endpoints secure by automatically deploying patches for OS and third-party apps.
- Secure Login Controls: Enhances access security through authentication policies and credential enforcement.
- Mobile Device Management: Applies security policies to smartphones and tablets, including passcode enforcement and remote wipe.
- Geo-Fencing Capabilities: Restricts device access based on geographic location to prevent unauthorized use.
- Security Configuration Templates: Predefined settings for USB control, firewalls, and system policies streamline endpoint hardening.
Why do we recommend it?
We recommend ManageEngine Endpoint Central for robust security with data hardening and multi-layered endpoint protection. It offers a seamless end-user experience while maintaining top-notch security, giving a crucial balance between user satisfaction and robust protection against cyber threats.
Endpoint Central helps you develop a more robust endpoint security protocol by helping you regularly assess vulnerabilities within your perimeter, monitor browsers and control devices and software applications on your network.
ManageEngine Endpoint Central is a web-based unified endpoint management software for desktops, laptops, servers, and mobiles. The solution provides tools such as automated patch management, software deployment, remote control, IT asset management, and more.
Among its many features, ManageEngine Endpoint Central provides fantastic endpoint protection. First, it secures the endpoints with the latest software by automating patch deployments. And it can also let you enforce policies for mobiles, such as imposing device passcodes, remote locking, restricting the camera, geo-location tracking, and more. The software also includes predefined security configurations like USB settings, firewall settings, security policies, and more.
Who is it recommended for?
This tool is a perfect choice for organizations who can't compromise on security; Manage Engine Endpoint Central is used by experts aiming to mitigate insider threats and security breaches. It allows precise management of privileges, app monitoring, and control over sensitive data at the endpoint level. Overlap is perfect for maintaining policy compliance and industry-standard security baselines across the organization.
Pros:
- Ideal for On-Premises Environments: Great choice for administrators who prefer running endpoint tools in-house.
- Cross-Platform Compatibility: Works across Windows, Linux, and macOS for greater deployment flexibility.
- Comprehensive Reporting Tools: Offers detailed inventory, patch, and vulnerability reports for auditing and compliance.
- Built-In Vulnerability Scanning: Identifies endpoint weaknesses before automating patch remediation.
- MDM Functionality Included: Provides full mobile device management alongside desktop controls.
Cons:
- Not Suited for Small Networks: Feature set and complexity are overkill for smaller businesses or simple environments.
Give this tool a look, you'd be surprised at the versatility it has and we're happy to recommend it to our readers. You can find out more about pricing when you register for a 30-day free trial.
Pros:
- Granular Technician Control: Role-based permissions allow for strict control over who can do what in the system.
- Complete Device Visibility: Tracks all active and rogue endpoints for better oversight and response.
- Integrated Antivirus Solutions: Supports robust AV tools with a single management dashboard.
- Built-In Encryption Tools: Protects sensitive data through local disk and device encryption.
Cons:
- Not a Standalone Tool: Requires use of the full RMM suite, which may be unnecessary for some users.
NinjaOne is an RMM package and the Endpoint Security system is part of that. You can register for a free trial and get a custom price quote. Access a 14-day free trial.
5. N-able N-sight – FREE TRIAL
N-able N-sight RMM is a comprehensive set of tools integrated into a single web-based dashboard that helps enterprises to secure, maintain, and optimize IT resources. Among these tools, there are excellent endpoint protection services such as Endpoint Detection & Response (EDR), Remote Monitoring, Patch Management, and more.
Key Features:
- AI-Powered Offline Protection: Detects and mitigates threats even when devices are disconnected from the network.
- Automated Endpoint Policies: Applies consistent security protocols across devices based on pre-set rules.
- Behavioral AI Analysis: Uses eight intelligent engines to assess file behavior and detect malicious activity.
- Built-In Forensics & Reporting: Provides detailed threat insights and incident summaries for investigation.
- Data-Driven Alert System: Generates actionable alerts and reports to guide threat response and decision-making.
Why do we recommend it?
N-able N-sight is an efficient RMM platform, offering a powerful blend of capabilities at a budget-friendly cost. It helps to boost earnings while keeping costs low. It offers seamless integration with Apple Business Manager for zero-touch deployment across iOS and macOS devices.
The N-able EDR is a brand new tool, born from a partnership with SentinelOne, an autonomous endpoint protection company. The EDR is an effective endpoint protection tool that can help prevent cyberattacks, detect threats, and respond automatically. It performs continuous file and data points analysis using behavioral AI/ML engines without the need for signatures. The automatic processes will determine how to respond to threats and adjust over time.
Who is it recommended for?
If you are a business with complete remote management, N-able N-sight is your go-to choice. It handles monitoring, alerting, and patch management across various platforms, including Windows, macOS, Linux, and iOS. This tool helps in ticketing, billing, automatic scheduling, a brandable customer portal, and a mobile app for technicians.
Pros:
- User-Friendly Interface: Clean design and color-coded metrics make system health easy to interpret.
- Remote-Ready Management: Cloud delivery enables efficient control of endpoints from any location.
- Comprehensive Patch Tools: Built-in patch management integrates smoothly with endpoint protection.
- Quick Device Onboarding: Custom configuration profiles speed up setup for new endpoints.
Cons:
- Short Trial Duration: Limited trial window may not be long enough for thorough evaluation.
N-able N-sight is an enterprise Managed Service Provider (MSP) solution, offered by N-able MSP. To find more information about prices and licensing, request a quote. Start with a 30-day free trial.
6. ESET Protect – FREE TRIAL
ESET Protect is available in four plans that offer levels of cybersecurity services that begin with a baseline of on-device anti-malware protection. Those four plans are called Entry, Advanced, Complete, and Elite.
Key Features:
- Hybrid Security Architecture: Combines on-device scanning with cloud-based threat intelligence for layered protection.
- Cloud Sandbox Option: Uses virtual environments to safely analyze suspicious files before execution.
- Centralized Management Console: Unifies control and monitoring of all endpoints through a single dashboard.
- Integrated Patch Management: Offers automated updates and vulnerability remediation in higher-tier plans.
- Email & Cloud Protection: Secures email systems and cloud storage platforms like OneDrive from malware and phishing.
- Automated Threat Response: Instantly takes action on identified threats based on policy-driven rules.
Why do we recommend it?
ESET Protect is very easy to install as it comes with pre-configured live installers. These installers automatically connect your endpoints to the right instance and valid subscription. ESET Protect provides robust protection against ransomware and emerging threats by employing adaptive scanning, machine learning, cloud sandboxing, and in-depth behavioral analysis.
The on-device units provide the immediate threat detection service and it is available for Windows, macOS, Linux, iOS, and Android – this system protects mobile devices as well as computers. Endpoint units upload activity data to the central console. At a minimum, this displays live reports on system attacks and responses.
Higher plans get more features in the cloud-based server. This includes protection for email systems, including both on-site and cloud based. The tool will also protect cloud storage systems, such as OneDrive. Progress to the highest plans to get vulnerability scanning and patch management. The highest plan also provides centralized threat hunting and response, which is a service that is a paid extra for the two middle plans.
Who is it recommended for?
ESET Protect is used by network experts who want single-click functionality. It can easily perform actions like creating exclusions, submitting files for analysis, or initiating scans effortlessly. The tool offers a user-friendly notification system with a full WYSIWYG editor for customized notifications.
Pros:
- Scalable Plan Options: Multiple service levels accommodate organizations of all sizes and needs.
- Built-In Vulnerability Tools: Includes patching and exposure scanning in premium packages.
- Cloud Resource Coverage: Protects both SaaS storage systems and hosted email platforms.
- Fast On-Device Defense: Local threat detection stops attacks immediately without needing cloud lookup.
- Advanced Central Analytics: Offers powerful insights and response tools in the central server.
Cons:
- License Volume Requirement: Entry into any plan requires purchasing a minimum number of seats.
The lower three plans cover a minimum of five devices and the top plan needs at least 26. The price for the minimum order quantity of each plan with one year of support is:
- Entry – $211.00
- Advanced – $220.00
- Complete – $338.50
- Elite – Contact Sales
Start with a 30-day free trial.
7. Sophos Endpoint Protection
Sophos Endpoint Protection is a set of endpoint security tools that combine anti-malware, web and app control, URL blocking, firewall, HIPS, ransomware protection, and analysis and forensics.
Key Features:
- Automated Threat Detection: Quickly identifies and neutralizes emerging threats.
- Efficient Quarantine Process: Isolates suspicious files to prevent further harm.
- Exploit Blocking: Stops web and application-based exploits effectively.
- Risky URL & App Filtering: Blocks access to dangerous websites and apps.
- Behavioral Analysis: Monitors usage patterns to uncover anomalies.
- Suspicious Traffic Monitoring: Tracks unusual network activity in real time.
Why do we recommend it?
Sophos Endpoint Protection is well-known for its cutting-edge security solution. It provides unparalleled protection to prevent advanced attacks before they affect your systems. With robust EDR and XDR tools, organizations can actively investigate and respond to suspicious activities and indicators of attacks, ensuring comprehensive security measures.
The software provides a simplified and central management web-console that helps keep track of all endpoints. The Intercept X Endpoint, a tool from the Sophos Endpoint Protection, is one of the most popular for malware detection and removal. It uses machine learning technology to identify threats by analyzing its behavior and not by its signature.
There are two deployment methods, the Sophos Central is the unified console that runs on the cloud and the Sophos Enterprise Console, which must be installed on-premises. The software works with the agent that communicates with the server, but it can also be deployed as a standalone for offline computers.
Who is it recommended for?
Sophos Endpoint Protection is used by cyber experts as it gives instant critical attack warnings. This feature notifies administrators in Sophos Central about adversary activity across multiple endpoints or servers, providing detailed attack information. Users can respond using Sophos XDR, seek assistance from partners, or engage the Sophos Incident Response team.
Pros:
- Machine-Learning Advantage: Uses AI to counter emerging threats.
- Comprehensive Ransomware Defense: Protects against fileless malware and ransomware attacks.
- Automated Threat Mitigation: Enables rapid response and escalation of issues.
- External Device Scanning: Automatically scans connected devices for threats.
Cons:
- Limited Enterprise Scalability: Best suited for small to medium-sized companies.
The product can be purchased through different Endpoint Protection and Intercept X Endpoint software editions. For more information on their prices, get a quote. Sign up for a Sophos Central free 30-days trial, including Intercept X Advanced and more.
8. Bitdefender GravityZone Elite
Bitdefender GravityZone Elite is an advanced endpoint security solution that prevents, detects, remediates, and displays threats that could harm your network.
Key Features:
- Machine Learning Threat Detection: Uses predictive AI to identify threats before they execute.
- Pre-Execution Hyper Detection: Intercepts attacks in early stages to prevent damage.
- Sandbox Analysis: Runs suspicious files in a virtual environment for safe examination.
- Behavioral Anomaly Detection: Identifies unusual activity using real-time monitoring via Process Inspector.
- Centralized Console Management: Controls cloud and on-premises endpoints from one unified interface.
Why do we recommend it?
We recommend Bitdefender GravityZone Elite for its robust protection against advanced cyber attacks, including APTs and ransomware. It is powered by machine learning and has multiple layers of security. It is easy to install and manage, because no specialized security knowledge is needed. The solution covers diverse endpoints and email, both in the cloud and on-premise, all manageable from a single console.
It is an excellent endpoint solution that can detect attacks right from the pre-execution phase. It doesn’t rely on conventional signatures to detect attacks; instead, it uses advanced Machine Learning (ML) and behavioral analysis to find sophisticated and unknown threats. Bitdefender GravityZone Elite provides excellent control and protection for endpoints. It can manage systems patching, encrypt disks, protect from web threats, push firewall policies, and control specific apps and devices.
Who is it recommended for?
Bitdefender GravityZone Elite specializes in comprehensive threat insight and attack analysis. The tool offers Attack Forensics and Visualization, allowing users to gain valuable insights into their threat environment. It facilitates forensic analysis, visualizing the attack kill chain and effectively stopping potential threats.
Pros:
- Beginner-Friendly Interface: Simplified UI speeds up deployment and reduces the learning curve.
- Dual Detection Methods: Combines behavioral analysis with traditional signature detection.
- Integrated Disk Encryption: Adds data protection by encrypting drives alongside malware defense.
- Device Access Controls: Restricts USB and peripheral access to prevent unauthorized data transfers.
Cons:
- Lacks Setup Guidance: Needs better documentation and onboarding materials for faster adoption.
The price varies according to the number of monitored devices; for one device, the price starts at $78; for ten, the price is $260. Download a fully-functional Bitdefender GravityZone Elite free trial for a limited time.
9. Symantec Endpoint Protection
Symantec Endpoint Protection is an advanced security solution designed to protect endpoints such as laptops, mobiles, and servers within a network. It keeps all clients protected from sophisticated attacks, malware, trojans, viruses, and even adware. The software can run on-premises, on hybrid environments, or through its cloud-based service.
Key Features:
- Cloud-Based Central Management: Streamlines security oversight through a unified console.
- App and Device Control: Manages permissions for software and hardware to prevent unauthorized use.
- Comprehensive Malware Defense: Protects endpoints from viruses, Trojans, and exploits.
- Firewall & Intrusion Prevention: Blocks suspicious network traffic before it reaches the endpoint.
- Behavioral Analytics & Forensics: Tracks attack behavior to support in-depth threat analysis and response.
Why do we recommend it?
We recommend Symantec Endpoint Protection for its versatile protection across on-premises, hybrid, or cloud environments. The single-agent platform secures traditional and mobile endpoints, utilizing artificial intelligence to enhance security decisions. With a unified cloud-based management system, it simplifies protection, detection, and response against various advanced threats targeting endpoints.
Symantec Endpoint Protection uses a holistic security approach to safeguard your IT environment for the entire attack chain, from pre-attack, attack, breach, and the post-breach phases. It uses AI to help make optimal decisions and protect your endpoint at the device, application, or network level.
Who is it recommended for?
Recommended for those seeking efficient management, Symantec Endpoint Protection is used by experts leveraging intelligent automation and AI-guided policy management. This enhances administrator productivity and fortifies SOC teams, meeting customer needs without requiring additional headcount. The Integrated Cyber Defense Manager (ICDm) offers a unified cloud management console, streamlining overall endpoint security posture.
Pros:
- Forensic-Level Threat Insight: Tracks and documents attack behaviors for deep security investigations.
- Deployment Flexibility: Available for on-premise, cloud, or hybrid infrastructures.
- Network-Wide Threat Detection: Integrates with SIEM tools to identify issues from any part of the system.
- Advanced Manual Investigation Tools: Offers granular analysis features ideal for security operations teams.
Cons:
- Limited Visualization Options: Dashboard could benefit from more robust graphical data displays.
Sign up for a Symantec account and get access to Symantec Endpoint Security free trial.
10. Trend Micro Apex One
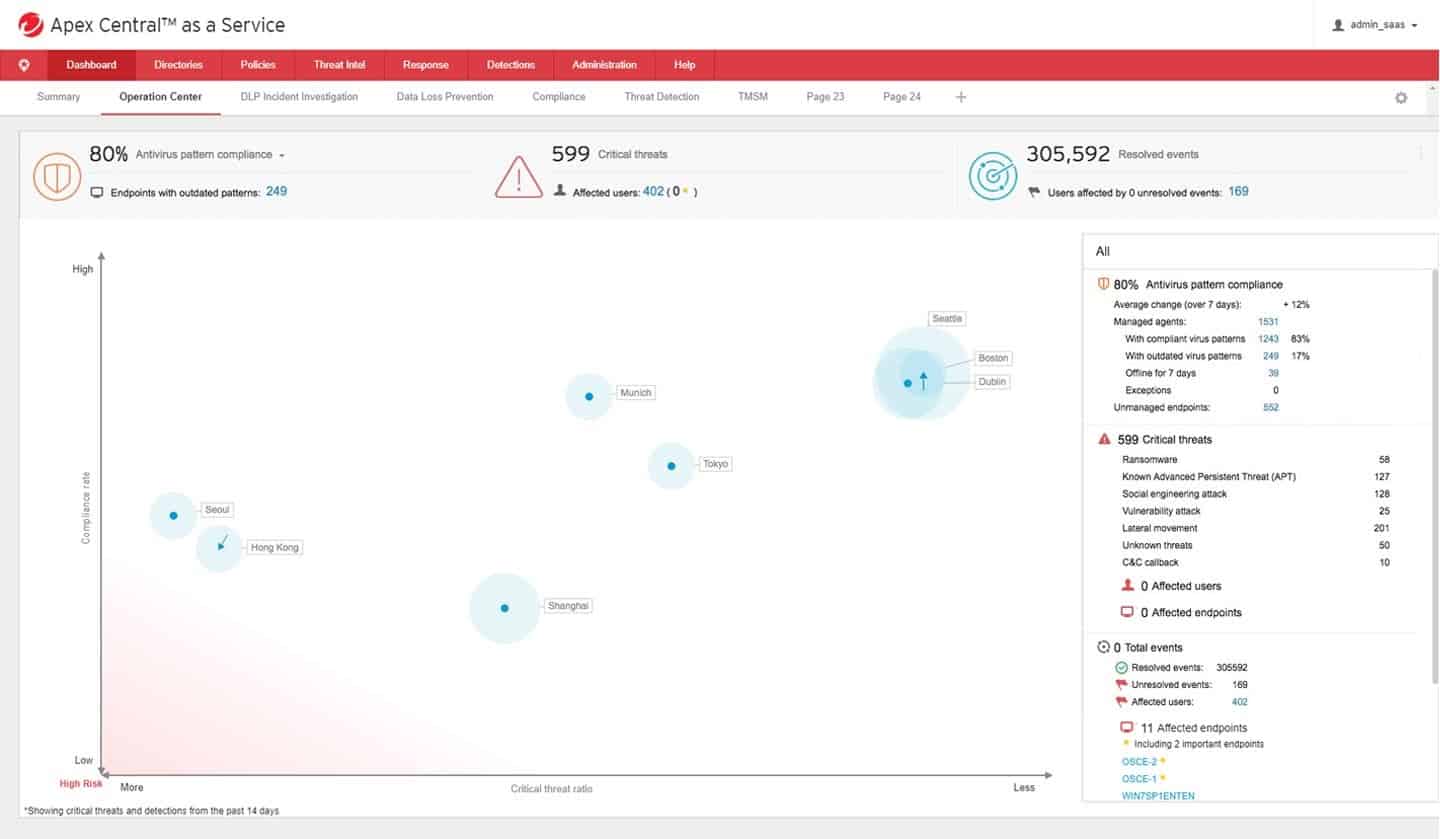
Trend Micro Apex One is an advanced automated security solution for endpoints. It performs automatic detection and response for a wide variety of threats. The software runs on-premises or through its SaaS-based solution, and the clients only need a single agent.
Key Features:
- Centralized visibility and control
- Vulnerability protection
- Application and device control
- Open API set
Why do we recommend it?
We recommend Trend Micro Apex One for its precise detection of advanced malware, including fileless, living off the land, and ransomware threats. The tool supports noise-canceling techniques like census and safe listing across every layer of detection, significantly reducing false positives. It offers effective protection against scripts, injection, ransomware, memory, and browser attacks through innovative behavior analysis.
Apex One provides full protection against sophisticated and new malicious scripts, malware, ransomware, crypto-mining, and more. The software can detect and respond to almost any threat with the help of Trend Micro Endpoint Sensor and the Managed Detection and Response (MDR), which are available as add-ons.
Who is it recommended for?
Trend Micro Apex One is used by IT experts and big companies due to its Vulnerability Protection. This feature utilizes a host-based intrusion prevention system (HIPS) to virtually patch both known and unknown vulnerabilities before official patches are available. It helps eliminate risk exposure, extends protection to critical platforms and physical and virtual devices, and reduces recovery and emergency patching downtime.
Pros:
- Can detect system vulnerabilities as well as threats based on behavior
- Includes HIDs features for additional protection
- Can isolate unpatched applications and systems until fixes are deployed
- Stops browser-based threats such as crypto mining, and clickjacking
Cons:
- Is only available as a cloud-based solution
Sign up for a SaaS-based free Trend Micro Apex One 30-days trial.
11. CrowdStrike Falcon
Falcon by CrowdStrike is a platform compromised by a unified set of cloud-native security technologies that prevent and remediate a wide range of cyber-attacks and malware.
Key Features:
- Zero-Day Attack Prevention: Stops unknown threats using AI and behavioral analysis before execution.
- Offline Endpoint Protection: Secures devices even when disconnected from the internet.
- Automated Asset Discovery: Identifies unmanaged devices and applications across the network.
- Threat Hunting & Forensics: Enables deep investigation into incidents with real-time data and expert tools.
- Unified Cloud Console: Manages antivirus, EDR, threat intel, and more from a single, web-based interface.
Why do we recommend it?
CrowdStrike Falcon is trusted by over 23,000 customers. It's known for stopping cloud breaches through a unified agent and agentless protection, providing unrivaled visibility with USB device control. The tool also simplifies host firewall management, ensuring robust protection for what matters most to its users.
The solution unifies a next-generation antivirus, EDR, threat intelligence, and managed threat hunting into a single cloud-managed console. Falcon provides full visibility into all endpoints and uses proprietary technology and services to protect them from breaches. It also uses a single lightweight agent on each endpoint powered by AI/ML and behavioral analytics instead of the traditional signature-based defense.
Who is it recommended for?
Cyber security experts used CrowdStrike Falcon for comprehensive training to defend against sophisticated threat actors. The tool helps in responding to attacks quickly and recovers the issue with perfection. It also offers actionable recommendations to enhance cybersecurity practices and controls, making it valuable for organizations seeking robust defense strategies.
Pros:
- Great for Hybrid Environments: Performs consistently across Windows, Linux, Azure, and multi-cloud setups.
- Streamlined Cloud Interface: Easy-to-use admin console simplifies deployment and daily operations.
- Behavioral Intelligence Grows Over Time: Learns patterns to improve threat detection accuracy with prolonged use.
- Low-Impact Agent Design: Lightweight agents offer powerful protection without slowing down systems.
Cons:
- Short Evaluation Period: Trial timeframe is limited, which may restrict comprehensive testing.
Falcon comes in four different editions, Pro ($8.99/endpoint/month), Enterprise ($15.99/endpoint/month), Premium ($18.99/endpoint/month), and Complete (request a quote). Sign up for a free trial of CrowdStrike Falcon Prevent Next-Gen Antivirus. Note that this is not the Falcon Complete, but the Next-Gen AV can give you a good idea of how the software works.
12. Webroot Business Endpoint Protection
Webroot Business Endpoint Protection is a cloud-based endpoint security solution that leverages Machine Learning (ML) to prevent, detect, and respond to threats. The software can predict and stop multi-vector attacks in real-time. Webroot uses a server-client communication model. The server, which is SaaS-based, runs a single integrated management console that gives full visibility and control over every single endpoint with the installed agent.
Key Features:
- Contextual Threat Intelligence: Analyzes real-time data to block threats based on behavior and context.
- Third-Party Tool Integration: Seamlessly works with RMM, PSA, and BI platforms for streamlined operations.
- Dynamic Risk Prevention: Uses infrared technology to adapt protection based on endpoint activity.
- Smart Firewall Protection: Monitors and filters network traffic with intelligent rules.
- Identity & Privacy Safeguards: Protects user data and privacy across devices and networks.
Why do we recommend it?
We recommend Webroot Business Endpoint Protection for its innovative use of cloud computing and real-time machine learning. This enables continuous monitoring and adaptation of endpoint defenses, ensuring robust protection against ransomware, phishing, malware, zero-day threats, and other cyberattacks. It helps businesses safeguard critical systems, intellectual property, customer data, employees, and guests.
The software can automatically protect endpoints against malware, ransomware, phishing, and more, without the need for signatures. All the protection occurs in real-time and from the cloud. The software also offers protection for offline devices.
Who is it recommended for?
Webroot Business Endpoint Protection is widely used by experts due to its collective threat intelligence. It includes advanced machine learning and predictive analytics; it offers automated defense against zero-day threats, requiring minimal human interaction. Ideal for businesses seeking efficient and proactive cybersecurity measures.
Pros:
- Innovative Ransomware Defense: Uses decoy files to lure and trap ransomware for safe mitigation.
- Proactive Zero-Day Protection: Blocks both known and unknown malware with cloud-based analysis.
- Flexible Cloud Deployment: Easily scales across businesses with minimal on-site setup.
- Lightweight Agent: Minimizes system impact while maintaining full protection.
Cons:
- Limited Enterprise Reporting: Larger organizations may find the analytics and reporting features less comprehensive.
Webroot Business Endpoint Protection offers a one-year protection for five seats for $150. Sign up for a free unlimited trial of Webroot Business Endpoint Protection for 30 days.
13. CylancePROTECT
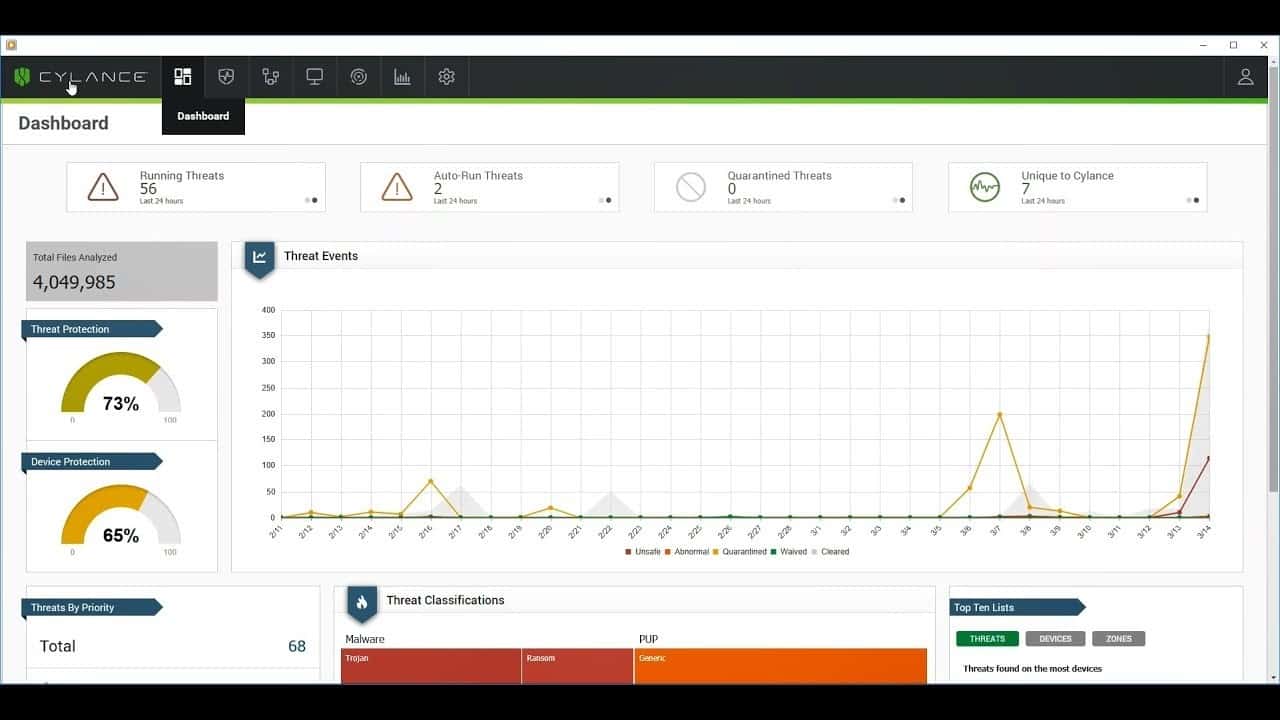
CylancePROTECT is an advanced AI-driven endpoint security solution. It leverages AI and ML to predict, prevent, detect, and protect from all sorts of threats. The software can analyze and categorize multiple characteristics of each file at the atomic level and distinguish from good or bad. CylancePROTECT does not use signatures, instead it combines AI mechanisms to block unknown malware from infecting endpoints.
Key Features:
- App & Script Control: Blocks unauthorized applications and scripts from executing on endpoints.
- Enforced Device Policies: Applies consistent security policies across devices to limit vulnerabilities.
- Root Cause Analysis: Traces back incidents to identify how threats entered and spread.
- Automated Threat Response: Detects and remediates threats in real time using AI-driven logic.
- AI-Based Malware Detection: Uses machine learning instead of signatures to block both known and unknown threats.
Why do we recommend it?
We recommend CylancePROTECT for its comprehensive endpoint protection. This tool is useful for incident prevention, root cause analysis, smart threat hunting, and automated detection and response capabilities, enhancing overall threat prevention measures for robust cybersecurity.
It also uses additional security controls to protect from advanced attacks like malicious scripts, ransomware, fileless, memory, and weaponized documents. CylancePROTECT can even reduce the risk of attacks exploiting a zero-day using the same AI model.
Who is it recommended for?
CylancePROTECT is used by experts who are involved in AI and Machine Learning. It uses risk score factors like geographic location, time, network trust, and usage patterns to dynamically determine the appropriate access level at any given moment. It is the best choice for organizations prioritizing adaptive and intelligent endpoint security.
Pros:
- AI-Driven Threat Prevention: Continuously stops evolving threats without needing signature updates.
- Deployment Flexibility: Available as both a cloud solution and on-premise software.
- Intuitive Dashboards: Simple interfaces allow easy monitoring for individuals and SOC teams alike.
- Supports Full Automation: Automatically mitigates threats or escalates incidents for technician review.
Cons:
- Lacks Onboarding Resources: Needs better documentation and tutorials for first-time users.
No free trial available, but you can request a demo
14. ESET Endpoint Protection Standard
The ESET Endpoint Protection Standard is a security management and anti-malware software used for endpoint and file server security. The software runs on-premises but also uses advanced cloud-based scanning and device control applications. ESET Endpoint Protection Standard comes with a powerful anti-phishing engine that protects users from entering sensitive information such as passwords, users, banking information, or more, to fake websites, masquerading as valid ones.
Key Features:
- Firewall & Web Controls: Blocks unauthorized traffic and manages access to risky or non-compliant websites.
- Automated Security Management: Applies security policies and updates without manual intervention.
- Live Endpoint Visibility: Tracks endpoint status and activity whether devices are online or offline.
- Optional Disk Encryption: Offers full disk encryption as an add-on to protect sensitive data at rest.
- Anti-Phishing Engine: Prevents users from submitting private data to fake or malicious websites.
Why do we recommend it?
We recommend ESET Endpoint Protection Standard for its multi-layered protection, with 16 layers securing over 1 billion internet users globally. The tool offers personalized recommendations tailored to your lifestyle and requirements, enhanced by a new chatbot feature for user-friendly assistance. You must choose this tool for robust and customizable endpoint security.
Who is it recommended for?
Experts use ESET Endpoint Protection Standard for its minimal system footprint, excellent malware accuracy, and easy deployment and management. Overall, it is ideal for organizations seeking efficient and effective endpoint security solutions with minimal operational impact.
Pros:
- Customizable Dashboards: Visual-rich interface allows tailored monitoring for admins.
- Behavior-Based Threat Detection: Uses Host Intrusion Prevention Systems to identify threats by behavior rather than signature.
- Botnet and C&C Detection: Stops command-and-control traffic to prevent bot-related infections.
- Flexible Deployment Options: Available as both cloud-based SaaS and on-premises software.
Cons:
- Geared Toward Larger Networks: Feature set may be excessive for small home or personal use.
Request to download a 30-days free trial of ESET Endpoint Protection Standard.
15. FortiClient
FortiClient is an endpoint security solution developed by Fortinet. It provides full visibility and proactive security to computers and mobiles through a variety of security controls such as antivirus, firewall, web filtering, app and device control, and more. When FortiClient detects a vulnerability, it deploys the necessary patching or immediately quarantines the risk.
Key Features:
- Pattern-Based Malware Detection: Identifies known threats using signature-based scanning techniques.
- Behavioral Exploit Protection: Detects abnormal activity to block zero-day and fileless attacks.
- Web Filtering & App Firewall: Controls access to websites and monitors applications for malicious behavior.
- USB Device Control: Restricts usage of external storage devices to prevent unauthorized data transfers.
- Cloud Sandbox Integration: Analyzes suspicious files in an isolated cloud environment before allowing execution.
Why do we recommend it?
FortiClient is loved by experts because of its robust Endpoint Protection. The Unified FortiClient agent offers advanced security features, including AI-based next-generation antivirus (NGAV), endpoint quarantine, application firewall, cloud sandbox support, USB device control, and ransomware protection.
The software also uses policy-based automation to control outbreaks and contain threats. It integrates all of its agents with the Fortinet Security Fabric to provide endpoint telemetry and automatic threat response. To test the waters, Fortinet offers a fully-featured free version of the Enterprise Management Server (EMS), which is the central console of FortiClient. The free version lets you manage up to ten clients.
Who is it recommended for?
FortiClient is used by organizations that use ML anti-malware and behavior-based anti-exploit features. Additionally, the tool offers app firewalls and web content filtering for enhanced security. It is ideal for organizations valuing secure remote access; FortiClient includes encrypted tunnels supporting posture checks, conditional admission, and ongoing verification of users and devices.
Pros:
- Smooth Deployment Process: Simple setup with strong endpoint visibility makes management easy.
- Built-In VPN Security: Adds encrypted tunnels for safe remote connections and identity protection.
- Remote Access Capability: Allows users to securely retrieve files and systems from any location.
- Strong Web Filtering Controls: Blocks malicious and unauthorized sites using customizable rules.
Cons:
- Limited Free Client Management: The free EMS version only supports up to ten clients, which may not be enough for growing teams or larger organizations.
16. Palo Alto Networks Traps

Palo Alto Networks Traps is an advanced AI/ML-driven endpoint protection and response software. It provides security from sophisticated exploits, ransomware, zero-day threats, and unknown malware attacks to laptops, desktops, and servers.
Key Features:
- Behavior-Based Threat Prevention: Detects suspicious activity and stops malware before execution.
- WildFire Threat Intelligence: Leverages real-time cloud-based analysis to detect and block emerging threats.
- Threat Data Sharing: Automatically sends and receives threat intelligence to stay ahead of evolving attacks.
- Exploit & Fileless Malware Defense: Protects against zero-day, ransomware, and non-signature-based attacks.
- Full Exploit Chain Protection: Blocks all stages of an exploit attempt, from delivery to execution.
Why do we recommend it?
We recommend Palo Alto Networks Traps for its advanced features, including AI-driven local analysis that assesses thousands of file attributes to accurately detect and block malware. It uses up-to-date ML models powered by WildFire threat intelligence to provide a high-performance machine learning framework to effectively thwart emerging threats.
The software prevents endpoints from getting infected or attacked by malware using multiple methods. It starts by gathering intelligence from WildFire Threat Analysis service. When Network Traps knows what’s out there, it can autonomously reprogram itself. It can also analyze hundreds of files at an atomic level and scan without using any signatures.
Who is it recommended for?
Palo Alto Networks Traps is designed to lower the attack surface of endpoints. The single endpoint agent not only blocks attacks but also provides a comprehensive suite of protection features. It also includes Device Control to manage USB devices securely and safeguard endpoints from malware and data loss.
Pros:
- Layered Threat Defense: Offers end-to-end protection against a wide range of advanced threats.
- Predictive Threat Analysis: Automates threat detection and reduces the need for manual updates or scans.
- Seamless Integration with Panorama: Enhances visibility and threat mitigation across the Palo Alto ecosystem.
- Efficient Data Correlation: Analyzes complex data points like hashes and DNS queries for forensic insights.
Cons:
- Restrictive Default Policies: Pre-configured rules may interfere with normal operations or custom software setups.
No free trial available, but you can request a Network Traps free demo.
17. Malwarebytes Endpoint Protection
Malwarebytes Endpoint Security is an advanced cloud-managed security solution that provides threat prevention, detection, and remediation for endpoints. Malwarebytes Endpoint Protection uses multiple detection techniques to protect endpoints from the entire attack chain from threats like malware, ransomware, and zero-day attacks.
Key Features:
- Cloud-Based Management Console: Controls all security settings and actions through a centralized, web-accessible dashboard.
- Linking Engine Remediation: Tracks and removes all elements of infections, preventing re-infection.
- Behavioral Web & App Protection: Monitors application and website activity for suspicious behavior.
- Machine Learning Anomaly Detection: Uses AI to identify new threats based on unusual patterns.
- Multi-Layered Defense Stack: Combines seven technologies in a single lightweight agent for complete endpoint protection.
Why do we recommend it?
We recommend Malwarebytes Endpoint Protection for its robust features because it is a combination of seven detection and remediation technologies in a single cloud-managed agent. It offers complete malware protection and remediation, precise threat detection, proactive blocking, and thorough remediation. It is cloud-driven and user-friendly, meaning it is perfect for organizations of all sizes seeking comprehensive endpoint security solutions.
According to Malwarebytes, their antivirus solution is used and installed over 500,000 clients daily, and it helps detect and remediate over three million infections daily. That massive number gives Malwarebytes Endpoint Security enough data to collect and analyze threat intelligence.
The Malwarebytes Endpoint Security uses a single agent to communicate with the server. The solution includes asset management, web protection, exploit and ransomware remediation, and more.
Who is it recommended for?
ThreatDown Endpoint Protection offers a user-friendly interface that controls the full suite of endpoint protection software. Users can easily prioritize remediation through filters like threat severity and physical location. With a click-based approach, it simplifies threat blocking for efficient security management.
Pros:
- Powerful Malware Removal: Excels at finding and fully removing deeply embedded threats.
- Lightweight Performance Impact: Runs quietly in the background with minimal resource consumption.
- All-In-One Endpoint Coverage: Offers protection from malware, ransomware, exploits, and more in one package.
- Easy Threat Prioritization: Filters threats by severity and location for quicker decision-making.
Cons:
- Higher Cost for Smaller Teams: Pricing may be steep for small businesses when compared to leaner alternatives.
The price for cloud-based Malwarebytes Endpoint Protection starts at $699.90 per year for ten devices. Request a free download of Malwarebytes Endpoint Protection trial.
18. VMware Carbon Black Defense
Carbon Black (CB) Defense is a cloud-native endpoint security platform, recently purchased (Oct 2019) by VMware. The software is a cloud-based console that provides full visibility and management for all the endpoints on a network. And from the endpoint side, CB uses a single lightweight agent that gives complete protection against known and unknown threats. The endpoint CB clients collect raw data and use the cloud-based streaming AI analytics to detect, identify, and model potential threats.
Key Features:
- Next-Gen AV & EDR Integration: Combines modern antivirus and endpoint detection for real-time threat prevention.
- Data Center Security Integration: Extends protection to virtual environments alongside physical endpoints.
- Live Query & Remediation: Enables real-time investigation and direct response to endpoint issues.
- Advanced Threat Hunting Tools: Supports proactive searching for threats across the network.
- Alerting & Monitoring Platform: Delivers real-time alerts and comprehensive visibility into threat activity.
Why do we recommend it?
Carbon Black can help you save 7.5 hours per security incident. The tool combines Next-Gen Antivirus and Behavioral EDR, analyzing attacker behavior patterns to detect and prevent never-before-seen attacks, including malware, fileless, and living-off-the-land attacks. It is a suitable fit for organizations seeking time-saving and advanced threat-detection capabilities.
The CB Predictive Security Cloud platform is the one that provides endpoint protection against the most sophisticated and powerful threats.
Who is it recommended for?
VMware Carbon Black Defense is ideal for organizations seeking 24-hour visibility. It is used by security operations analysts to offer validation, context into root causes, and automated monthly executive reporting. This ensures a proactive approach to security incidents, enhancing overall threat visibility and response capabilities.
Pros:
- Live Response Capabilities: Allows immediate access to affected endpoints to view and neutralize threats.
- Built-In MDR Services: Offers continuous monitoring and expert suggestions through managed detection and response.
- Cloud-Native Management: Reduces infrastructure complexity while improving data handling and control.
- Behavioral Analytics Engine: Tracks attacker behavior patterns to stop fileless and unknown attacks.
Cons:
- Noisy Alerts & Complex Deployment: May generate excessive false positives and faces challenges with SCCM-based software deployment.
No free trial available, but you can request a demo.
19. VIPRE Endpoint Security Cloud
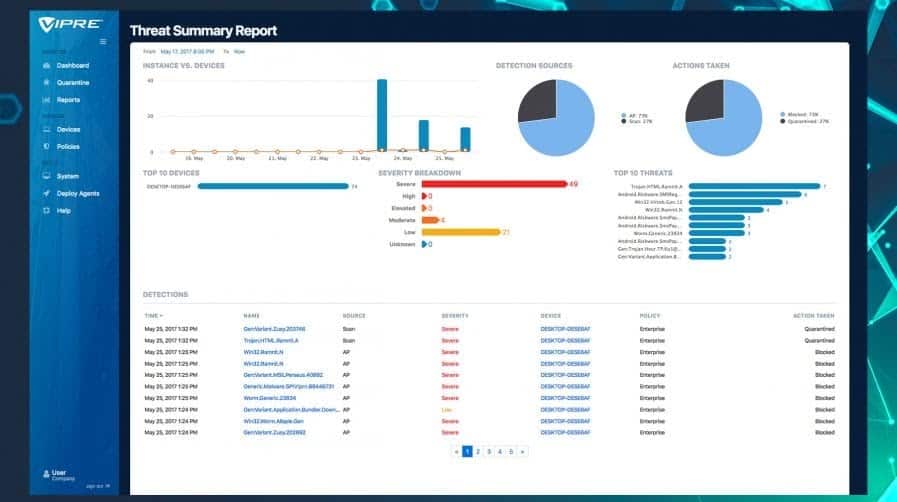
The VIPRE Endpoint Security Cloud is an advanced ML-powered threat intelligence solution that provides robust malware protection for SMBs. VIPRE can safeguard endpoints against several threats, such as ransomware, zero-day attacks, phishing, malicious scripts, exploit kits, and mobile threats. Instead of the traditional signature-based antivirus, the software provides real-time behavior analysis. With this analysis, VIPRE can detect hard-to-catch zero-day attacks and prevent harm from unknown threats.
Key Features:
- Ransomware Prevention Engine: Stops encryption-based attacks using behavior monitoring and rollback features.
- Phishing & Spam Defense: Blocks malicious emails and suspicious links before they reach the inbox.
- Network Traffic Inspection: Analyzes packets for signs of malware, data exfiltration, and exploit attempts.
- Exploit Protection for Apps & Browsers: Shields common apps and web browsers from exploit-based attacks.
- Cloud-Based Management Console: Admins can manage and respond to incidents from any connected device.
Why do we recommend it?
We recommend VIPRE Endpoint Security Cloud for its simplified administration. It is easily accessible through a cloud console from any device and allows users to effortlessly navigate common management and incident response tasks. The thoughtful and intuitive UI enhances the overall user experience.
Who is it recommended for?
VIPRE Endpoint Security is used by experts who work with machine learning to identify and block malicious activity. With comprehensive monitoring of process activity, network traffic, and file behavior, it efficiently identifies and thwarts attacks targeted at endpoints.
Pros:
- Comprehensive Threat Coverage: Protects against email threats, ransomware, and even mobile malware.
- Automated Software Patching: Ensures applications stay up to date across all endpoints.
- Always-On Background Scanning: Runs daily scans and alerts users of hidden threats in real time.
- User-Friendly Cloud Console: Simple, intuitive UI makes endpoint administration efficient and easy.
Cons:
- Laggy Server Interface: Some users report delays and glitches when managing endpoint lists or accessing settings
The VIPRE Endpoint Security Cloud subscription starts at $150 per year for five seats. Sign up for a fully-featured 30-day free trial of VIPRE Endpoint Security Cloud.
Final Words & Conclusion
Endpoint protection software is not an ordinary everyday antivirus. It goes well beyond the signature-based threat detection that traditional anti-malware provide. The best endpoint protection out there uses a mix of AI and ML models to analyze behaviors from every endpoint.
These tools can collect raw data from each client or agent and send information to the cloud for advanced threat analysis. The server acts quickly by detecting the anomaly and by sending a remediation solution. Some of these software and services, also have extensive databases with threat intelligence that help them as a base to find more and unknown threats.
All of the above tools apply sophisticated behavior analytics to detect and respond to all sorts of threats. Some of the tools like ManageEngine Desktop Central or FortiClient offer 100% freeware, so you can test the waters for an unlimited time.
Others like N-able N-sight and Sophos Central offer the fully-featured enterprise-solution trial for free, so you can go all into protecting your endpoints.
Endpoint Protection Software & Services FAQs
What types of threats can endpoint protection software protect against?
Endpoint protection software can protect against a range of threats, including malware, viruses, phishing attacks, ransomware, and zero-day exploits.
What are some key features of endpoint protection software?
Some key features of endpoint protection software include antivirus and anti-malware protection, firewall protection, intrusion detection and prevention, email security, web filtering, and device control.
How does endpoint protection software work?
Endpoint protection software works by monitoring the activity on endpoints and using various techniques to detect and block threats. These techniques may include signature-based detection, behavioral analysis, machine learning, and artificial intelligence.
What factors should be considered when choosing endpoint protection software?
When choosing endpoint protection software, factors such as the level of protection offered, ease of use, compatibility with existing systems and applications, support and maintenance, and cost should be considered.
4. NinjaOne Endpoint Security – FREE TRIAL
NinjaOne Endpoint Security is an antivirus management system that is part of a platform of remote monitoring and management (RMM) tools for use by managed service providers. The NinjaOne package includes a choice of AV systems – Bitdefender and Webroot. Both of these systems are on-device software instances that are coordinated through a cloud-based console.
Key Features:
Why do we recommend it?
We recommend NinjaOne Endpoint Security for ultimate control over end-user devices, establishing a robust foundation for security. It helps you to manage applications, edit registries remotely, deploy scripts, and configure devices at scale. It is easy to install and prevents unauthorized agent removal to have continuous visibility and control over endpoint security.
A device inventory in the NinjaOne system keeps track of which endpoints are connected to the system. This enables the identification of rogue devices and it also records which endpoints have had the antivirus system installed on them and which are still running it – it could be that the endpoint user might remove the AV system.
All technician activities are controlled and logged, which ensures that your employees are only allowed to access specific client devices and perform authorized actions. The NinjaOne Endpoint Security service also includes the ability to encrypt computer drives and peripheral devices to control access to data. This encryption is performed with Bitlocker or FileVault.
Who is it recommended for?
NinjaOne is used by experts managing user permissions at scale. A role-based system allows defined access to organizations, features, and functionalities. You can use permissions to personalize technician access with options from “no access” to “view, update, create, and delete” across various areas.