We may earn a commission if you make a purchase through the links on our website.
16 Best Event Log Monitoring Tools for Analyzing SIEM

UPDATED: September 6, 2024
Event log monitoring has two distinct halves, both of which are invaluable to maintaining a smooth and reliably functioning environment.
One half is troubleshooting – whenever there's an issue, the event log is the best place to look to ferret out exactly where the problem lies. Just as important as repairing, however, is prevention!
Accurate monitoring and real-time analysis of event logs can provide clues to upcoming problems well before they strike. Even strict regulatory needs, such as HIPAA, can be carefully monitored and audited using event logs. There's almost no part of a computer environment that cannot be better maintained or, when the time comes, repaired than with the avid use and management of event logs.
Here is our list of the top event log monitoring tools:
- SolarWinds Security Event Manager – EDITOR’S CHOICE This software package is a log manager as well as a security monitoring system. It collects Event messages from Windows and its applications, Syslog, and logs data from a wide range of packages, including AVs and firewalls, and then scans them for signs of attack. Runs on Windows Server. Start a 30-day free trial.
- Datadog Log Management – FREE TRIAL Two log management services from a cloud platform – one for log collection and the other for log archive management.
- ManageEngine Log360 – FREE TRIAL A SIEM service that is able to integrate with many applications to collect log messages as well as using Windows Event and Syslog records to search for threats. Runs on Windows Server.
- ManageEngine EventLog Analyzer – FREE TRIAL An log manager that includes a consolidator and a data viewer that includes analysis tools. Runs on Windows Server and Linux.
- Barracuda SKOUT Managed XDR – ACCESS DEMO A cloud-based XDR system that comes fully equipped with a team of experts to monitor it.
- LogFusion A basic log file viewer that is available in free and paid version. Both editions run on Windows and Windows Server.
- Netwrix Event Log Manager A free log server, consolidator, and log file manager. This tool specializes in Windows Event Logs and it runs on Windows Server.
- Splunk A highly respected free log manager that has paid add-ons for specific functions, such as security analysis.
- WhatsUp Gold Log Management Suite A log manager that collects Event Log, Syslog, and IIS messages. It also manages files and includes a data viewer and analyzer. Runs on Windows Server.
- Tripwire Log Center A collector and manager for Event Log messages that feeds through to Tripwire’s full SIEM systems. Installs on Windows Server.
- Quest InTrust This collector, manager, and viewer for Event Logs and Syslog messages adds compression to reduce storage size. Runs on Windows Server.
- Corner Bowl Server Manager This tool collects Syslog, Event Log, and Azure AD logs. It then consolidates and manages the messages in files. This is also a log analyzer with HIPAA and PCI-DSS reporting capabilities. Runs on Windows and Windows Server.
- LogRhythm A very comprehensive log manager that is designed to participate in a wider security platform. Installs on a bare metal server.
- SumoLogic Primarily a cloud-based tool that can be operated remotely making it ideal for technicians that work on the go.
- Logscape Powerful yet specialized Event Log Tool tool but it makes up for that by merit of being quite powerful. Visualize, analyze, and search log information of nearly any size.
What you Need in an Event Log Monitoring Tool
Event logging is not a thorn without its rose, and that's why event log monitoring tools and programs are powerful.
Systems, both client and server, generate a huge number of events, and it's incredibly easy for the useful information to be completely lost in the signal to noise ratio; there's quite a lot of noise.
Too often important information can be lost in the sea of superfluous errors without the help of management software to sift through it all.
On the software-focused side of things, event logging is incredibly useful when applications just aren't cooperating with the user.
Whether it's a program faulting on a client machine, in which cause the event log will quickly point you to the offending DLL or other failure point, or an unhappy Exchange server that isn't transmitting the way you'd expect, at which point the event log will get you zeroed in quickly on where to put your troubleshooting efforts.
Ultimately event logs tend to be just too unwieldy and time consuming to peruse in their raw state.
That's where event log monitoring makes any technician's life, and job, easier – software that can quickly, intelligently, and reliably make the proverbial needle in a haystack search far easier while simultaneously monitoring in real-time for hints of issues to come.
The Best Event Log Monitoring Tools
Our methodology for selecting event log monitoring tools and software
We reviewed the event log monitoring market and analyzed the options based on the following criteria:
- Support for multi-tenant use
- SIEM integration and support
- Operating system support
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
With these selection criteria in mind, we have found a number of good event log monitoring tools and systems that will handle Windows Events messages. Some of these services are software packages, while others are cloud-based SaaS platforms.
For people looking for event log monitoring tools and software, here's a list of the best tools:
1. SolarWinds Security Event Manager – FREE TRIAL
Pros:
- Risk-Free Trial: Offers risk-free trial options, enabling organizations to assess its effectiveness and suitability for their security needs.
- File Monitoring: Supports file monitoring to help organizations maintain compliance with regulations such as HIPAA and PCI.
- Simple Yet Highly Customizable Dashboards and Reports: Provides intuitive dashboards and customizable reports, allowing users to tailor the interface to their specific requirements.
- Proactive AI-Assisted Threat Detection: Leverages AI-powered threat detection capabilities to proactively identify and mitigate security threats before they escalate.
Cons:
- High-Level Tool that Requires Trained Technicians: May require trained technicians to fully utilize its capabilities, potentially posing a learning curve for inexperienced users.
Price: The price depends on whether you want a perpetual license or would prefer to pay an annual subscription. Another factor in the pricing is the number of data sources you want to use for the SIEM. Prices start at $1,622 for a subscription and $2,995 for a perpetual license. Start a 30-day free trial.
EDITOR'S CHOICE
SolarWinds Security Event Manager is our top pick for a SIEM-supporting log manager because this package manages log messages from many incompatible sources and merges them into a common format, ready for analysis by a SIEM tool. On top of that, the system includes the SIEM software as well. This service performs application dependency mapping to better understand how intruders manipulate related services to pass through a target system.
Download: Start 30-day Free Trial
Official Site: solarwinds.com/server-event-manager/registration
OS: Windows Server
2. Datadog Log Management – FREE TRIAL
Datadog is a cloud platform that offers a range of system monitoring and management tools, including log management functions.
Key Features
- Log Collection and Storage: Collects and stores log messages from various sources, including Syslog and Event Log messages, providing a centralized repository for log data.
- AI-Powered Alerts: Utilizes AI-powered alerts to help reduce false alarms and alert fatigue, enabling users to focus on critical events and anomalies.
- Live Reports: Offers live reports that provide high-level metrics and allow users to drill down quickly into specific log data for detailed analysis.
- Scalable Pricing: Offers cost-effective log management solutions for organizations of all sizes.
Why do we recommend it?
Datadog Log Management provides a comprehensive solution for collecting, storing, and analyzing log messages, offering valuable insights into system performance and security. With its lightweight, cloud-based architecture and advanced features such as AI-powered alerts and live reports, Datadog Log Management is a valuable tool for organizations looking to streamline their log management processes. Our recommendation is based on its scalability, ease of use, and robust integration capabilities, making it suitable for organizations of all sizes.
There are two log management systems available from Datadog. The first is called Ingest, which collects log messages, stores them in a meaningful format and enables log message viewing and analysis. The log collector is able to take in messages from a long list of systems, including Syslog and Event Log messages. The second system is called Retain or Rehydrate, that enables archived logs to be brought back live on demand.
Who is it recommended for?
Datadog Log Management is recommended for IT professionals, system administrators, and DevOps teams seeking a centralized log management solution. Ideal for organizations with complex network environments, Datadog Log Management offers over 450 integrations to accommodate diverse infrastructure requirements. Whether you're monitoring a small-scale deployment or managing a large-scale enterprise environment, Datadog Log Management provides the flexibility and scalability needed to meet your logging needs.
Pros:
- Lightweight Cloud-Based Tool: Ensures seamless deployment and minimal resource overhead.
- 14-day Free Trial: Offers a 14-day free trial, allowing organizations to evaluate its capabilities and suitability for their logging needs.
- 450+ Integrations: Supports over 450 integrations, ensuring compatibility with a wide range of systems and applications.
- Scalable Pricing: Offers scalable pricing based on data processing volume, providing cost-effective log management solutions for organizations of all sizes.
Cons:
- Other Event Managers Offer Longer 30-Day Trial Periods: Some competitors may offer longer trial periods, potentially limiting the evaluation period for prospective users.
Price: The Ingest service is priced at a rate of $0.10 per GB of processed data per month. The Retain or Rehydrate price depends on your preferred retention period. A 7-day retention period costs $1.27 per million log events per month. Options extend up to a 60-day retention period, which costs $4.10 per million log events per month.
Official site: https://www.datadoghq.com/dg/logs/log-monitoring/
3. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is an on-premises SIEM service that is able to collect Windows Events, Syslog, and application status messages for a threat hunting data pool.
Key Features:
- Log Collection and Normalization: Collects and normalizes log data from various sources, including Windows Events, Syslog, and cloud platforms, enabling centralized threat hunting and analysis.
- Threat Intelligence Feed: Primes the threat detection system to identify malicious activity, enhancing security posture and incident response capabilities.
- Dashboard visualizations: Log360 provides visually rich dashboard visualizations, ideal for NOCs and MSPs to gain insights into security events and trends.
- Cross-platform monitoring: With support for Windows, Linux, and Unix systems, Log360 offers comprehensive monitoring capabilities across diverse IT environments.
- Configuration change monitoring: Log360 monitors configuration changes to prevent privilege escalation and ensure compliance with security policies.
Why do we recommend it?
ManageEngine Log360 offers a comprehensive on-premises SIEM service tailored for threat hunting and security monitoring. With its ability to collect log data from various sources, including Windows Events, Syslog, and cloud platforms such as AWS, Azure, and Salesforce, Log360 provides organizations with a centralized solution for detecting and responding to security threats. The inclusion of a threat intelligence feed enhances threat detection capabilities, making Log360 an ideal choice for organizations prioritizing proactive security measures.
This software installs on Windows Server, but it is able to collect data from AWS, Azure, and Salesforce cloud platforms plus other on-site packages. Agents send in log messages to a central server, where records are converted into a common format. This tool includes a threat intelligence feed, which primes the threat detection system to look for malicious activity.
Who is it recommended for?
ManageEngine Log360 is recommended for organizations seeking an on-premises SIEM solution with robust threat detection capabilities. Suitable for security operations centers (SOCs), managed service providers (MSPs), and network operation centers (NOCs), Log360 offers intuitive dashboard visualizations and advanced searching capabilities for live and historical event analysis. Additionally, its cross-platform monitoring support for Windows, Linux, and Unix systems makes it versatile for diverse IT environments.
Pros:
- Great Dashboard Visualizations: Offers visually appealing dashboard visualizations, making it easy for NOCs and MSPs to monitor security events effectively.
- Multiple Threat Data Integrations: Integrates multiple threat data streams, enhancing threat detection and response capabilities.
- Robust Log Searching: Provides robust searching capabilities for live and historical event analysis, enabling efficient threat hunting and incident investigation.
- Cross-Platform Monitoring: With support for Windows, Linux, and Unix systems, Log360 offers versatile monitoring capabilities for diverse IT environments.
Cons:
- Suite of Advanced Services: ManageEngine offers a suite of advanced services and features, which may require time to explore and fully test out for optimal utilization.
Price: Standard and Professional editions – you need at arrange a quote for custom pricing.
Get a 30-day free trial: https://www.manageengine.com/log-management/download.html
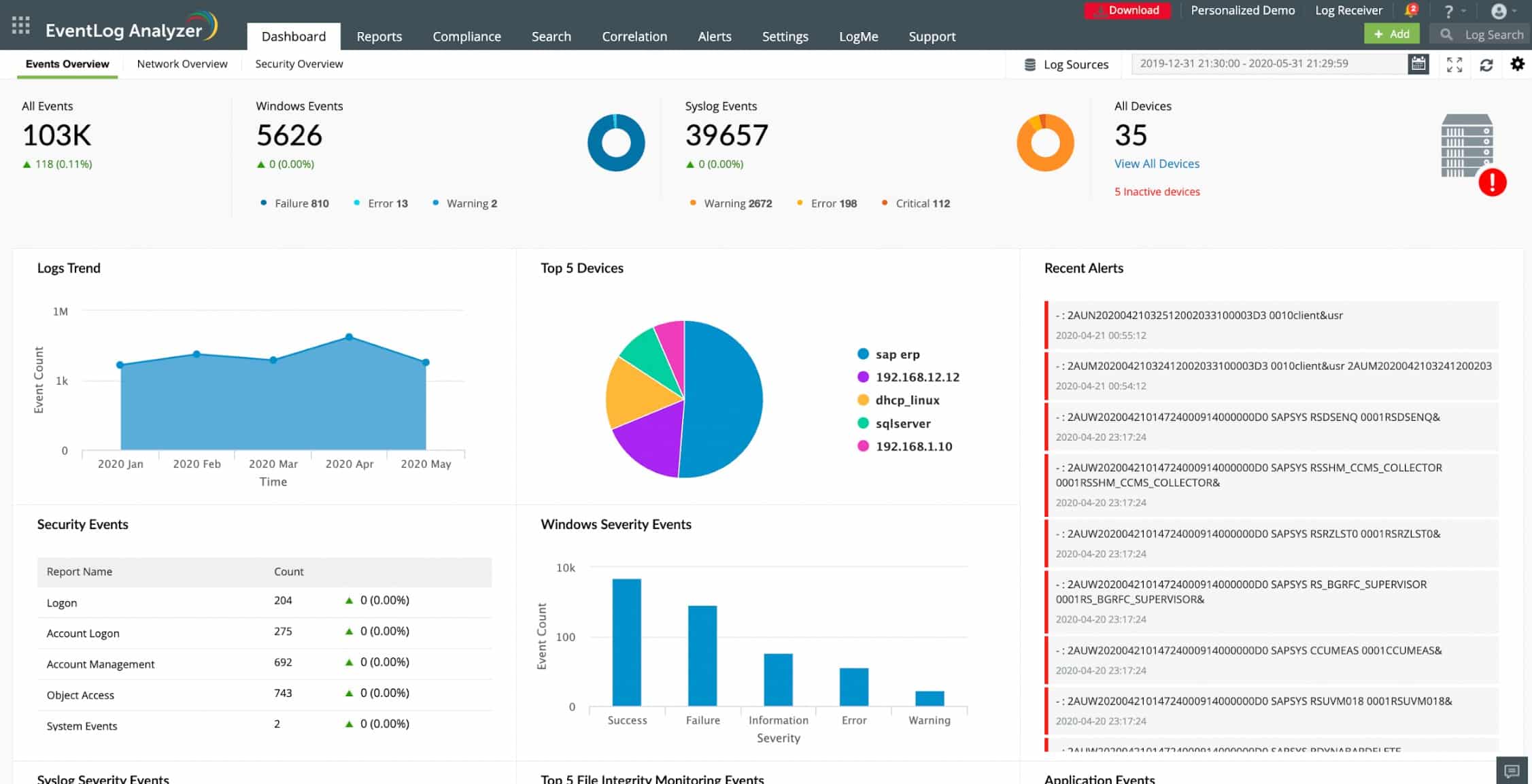
4. ManageEngine Event Log Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer installs on Windows Server and Linux and provides a log collection and management service. The system is a software package for installation on your site. It installs an agent on the other devices on your network and these collect log messages and sends them to the central server system. The system is able to collect Windows Event messages and also Syslog messages generated by the Linux operating system.
Key Features:
- Log Collection and Management: Collects and manages log messages from Windows and Linux systems, providing centralized visibility into security events and system activities.
- Customizable Dashboards: Offers customizable dashboards that are well-suited for network operation centers, providing visual insights into log data and security events.
- Multiple Alert Channels: Supports multiple alert channels, including SMS, email, and app integration, ensuring timely notification of security incidents to relevant teams.
- Anomaly Detection: Utilizes anomaly detection to assist technicians in identifying unusual patterns or behaviors in log data, facilitating proactive incident response.
- Files Integrity Monitoring: Includes files integrity monitoring capabilities to detect unauthorized changes and potential security threats, such as ransomware and data theft.
- Forensic Log Audit: Enables administrators to perform forensic log audits and generate reports for legal cases or investigations, ensuring compliance with regulatory requirements.
Why do we recommend it?
ManageEngine Event Log Analyzer offers a comprehensive log collection and management service, making it an essential tool for maintaining network security and compliance. With support for both Windows Event messages and Syslog messages from Linux systems, Event Log Analyzer ensures centralized log monitoring across heterogeneous IT environments. The platform's customizable dashboards, multiple alert channels, and anomaly detection capabilities enhance visibility and enable proactive incident response.
Who is it recommended for?
ManageEngine Event Log Analyzer is recommended for organizations seeking a robust log management solution to enhance security and compliance. Suitable for network operation centers (NOCs), security operations centers (SOCs), and compliance teams, Event Log Analyzer provides customizable dashboards and alerting mechanisms to streamline log monitoring and incident response processes. Additionally, its support for files integrity monitoring and forensic log audit features makes it suitable for organizations with stringent security and compliance requirements.
Pros:
- Customizable Dashboards: Provides customizable dashboards that are highly suitable for NOCs, offering visual insights into log data and security events.
- Multiple Alert Channels: Supports multiple alert channels, ensuring that relevant teams are notified promptly of security incidents via SMS, email, or app integration.
- Anomaly Detection: Utilizes anomaly detection to assist technicians in identifying unusual patterns or behaviors in log data, enhancing proactive incident response capabilities.
- Files Integrity Monitoring: Includes files integrity monitoring capabilities to detect unauthorized changes and potential security threats, such as ransomware and data theft.
- Forensic Log Audit: Enables administrators to perform forensic log audits and generate reports for legal cases or investigations, ensuring compliance with regulatory requirements.
Cons:
- Learning Curve: Like many comprehensive log management solutions, Event Log Analyzer may require time to fully explore all its features and tools to maximize its benefits.
Price: Standard and Professional editions – you need at arrange a quote for custom pricing.
Get a 30-day free trial: https://www.manageengine.com/products/eventlog/download.html
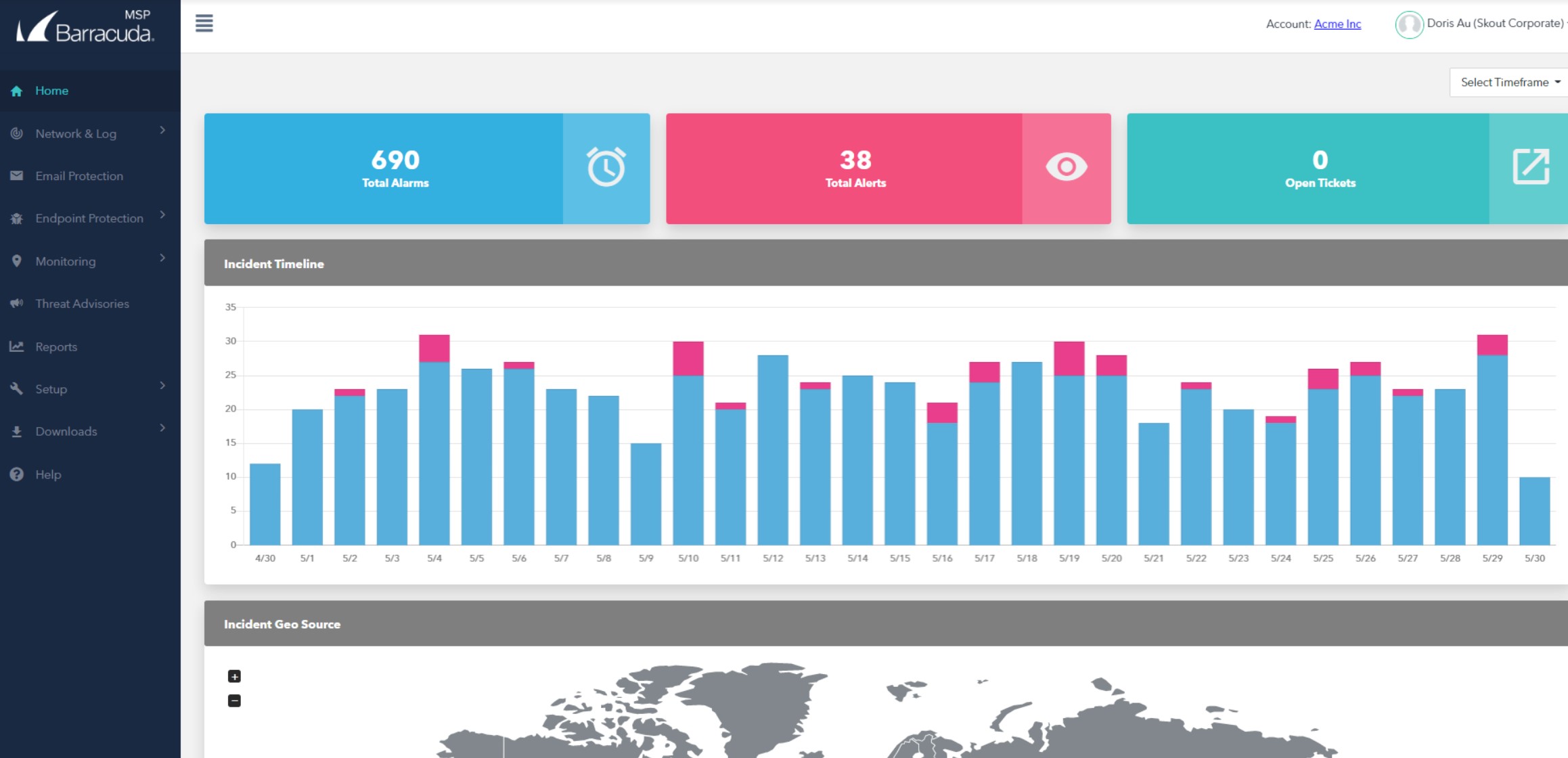
5. Barracuda SKOUT Managed XDR – ACCESS DEMO
Barracuda SKOUT Managed XDR is aimed at managed service providers and it is intended as a managed security service that MSPs can offer to their clients without the seller needing to hire its own team of security experts to run the XDR.
Key Features:
- Managed Security Service: Provides a managed security service tailored for MSPs, offering proactive threat detection and automated responses without the need for hiring dedicated security experts.
- Self-Service Portal: Subscribing clients gain access to a self-service portal that guides them through the setup process, reducing the need for manual intervention and minimizing support tickets.
- SIEM Functionality: The core of the service is a powerful SIEM that analyzes uploaded logs for indicators of threats, enabling proactive threat detection and automated responses.
- Visual Data Representation: Offers highly visual data representation, allowing MSPs and clients to visualize security data at scale and identify potential threats quickly.
- Customizable Alerting and Reporting: Includes customizable alerting and reporting templates, enabling MSPs and clients to tailor alerts and reports to their specific requirements.
- Designed for MSPs and Enterprise: Designed specifically those seeking enhanced security capabilities and proactive threat detection.
Why do we recommend it?
Barracuda SKOUT Managed XDR offers a comprehensive managed security service tailored for managed service providers (MSPs). By providing access to a self-service portal, Barracuda SKOUT simplifies the setup process for subscribing clients, reducing the need for manual intervention and minimizing support tickets. The core of the service is a powerful SIEM that analyzes uploaded logs for indicators of threats, enabling proactive threat detection and automated responses. With its focus on visual data representation and customizable alerting and reporting templates, Barracuda SKOUT Managed XDR is well-suited for MSPs and enterprise companies seeking enhanced security capabilities.
Subscribing clients get access to a self-service portal that guides them through the setup experience. That involves installing log collectors to provide the data for the system.
The core of this service is a SIEM that searches through uploaded logs for indicators of threats. One anomaly switches the search service over to scrutiny of specific devices and user accounts to see if further evidence arises. If it does, the system raises an alert and implements automated responses.
Who is it recommended for?
Barracuda SKOUT Managed XDR is recommended for managed service providers (MSPs) and enterprise companies looking for a comprehensive managed security service to protect their networks and data. The self-service portal and visual data representation make it ideal for MSPs seeking to streamline their security offerings and minimize manual intervention. Additionally, its advanced threat detection capabilities and automated responses make it suitable for organizations with stringent security requirements.
Pros:
- Managed Service Provider Focus: Designed with managed service providers in mind, offering a comprehensive managed security service tailored for their requirements.
- Self-Service Portal: Includes a self-service portal that guides subscribing clients through the setup process, reducing the need for manual intervention and minimizing support tickets.
- Visual Data Representation: Offers highly visual data representation, enabling MSPs and clients to visualize security data at scale and identify potential threats quickly.
- Customizable Alerting and Reporting: Includes customizable alerting and reporting templates, allowing MSPs and clients to tailor alerts and reports to their specific requirements.
Cons:
- Trial Option: It would be beneficial to have a trial option available for potential subscribers to test the platform's capabilities before committing to a subscription.
Price: Get a quote https://barracudamsp.com/extended-detection-and-response-xdr-plans/
Download link: As this is a service rather than a software package, there is no download. However, you can request a demo.
6. LogFusion
LogFusion is somewhat basic in what it does, but it does it in a way that's clean and concise. It handles text-based log dumps, event logs, remote logging, and even event and remote event channels as well!
Key Features:
- Text-Based Log Management: Efficiently handles text-based log dumps for comprehensive monitoring and analysis.
- Event Log Integration: Seamlessly integrates with event logs for easy access and management.
- Remote Logging Support: Allows for monitoring and managing logs remotely, enhancing flexibility and accessibility.
- Folder Monitoring: Monitors specified folders for changes, providing real-time updates on log activities.
- Automation Capabilities: Offers automation features to streamline log management tasks and workflows.
Why do we recommend it?
LogFusion may seem basic at first glance, but its simplicity is its strength. With a clean and concise interface, it efficiently handles various types of logs, including text-based dumps, event logs, and remote logging. We've extensively tested LogFusion and found it to be reliable and effective in managing logs, providing a seamless user experience. While the free version offers essential features, upgrading to the licensed versions unlocks additional convenience and ease-of-use functionalities, such as search-as-you-type filtering and customizable columns, enhancing overall productivity.
The free version has much of the same features as the licensed versions, but many of the convenience and ease-of-use features are locked from free, such as search-as-you-type filtering, customizable columns, tabbed interface, and other more quality-of-life based functionality.
Who is it recommended for?
LogFusion is ideal for system administrators, IT professionals, and developers working with servers and workgroups. Its lightweight design makes it particularly suitable for monitoring logs in these environments, ensuring smooth operation and timely issue resolution. Additionally, individuals or teams seeking efficient folder monitoring and automation capabilities will find LogFusion to be a valuable asset in their toolkit.
Pros:
- Lightweight Monitoring Tool: Ideal for servers and workgroups, ensuring minimal resource consumption.
- Pro and Freemium Versions: Provides flexibility with options for both free and licensed versions to suit different needs.
- Supports Folder Monitoring and Automation: Enables efficient management of log files through folder monitoring and automation features.
Cons:
- Windows Compatibility Only: Limited to Windows operating systems, restricting accessibility for users on other platforms.
Price: Free version is available, Pro version also available starting as low as $9 per license
Download link: https://www.logfusion.ca/Download/
7. Netwrix Event Log Manager
The Netwrix Event Log Manager can be considered a simpler and light version of their Auditor software. The Log Manager is freeware and handles all the basic needs such as consolidation of events from an entire network in a single place for review, real-time email alerting of critical events, some limited amount of alert criteria filtering, and some archiving ability (limited to one month.)
Key Features:
- Freeware Log Consolidation: Consolidates events from across the network into a centralized repository for efficient review and analysis.
- Real-Time Email Alerting: Provides immediate notification of critical events via email, enabling prompt response to potential threats.
- Basic Alert Criteria Filtering: Allows for limited filtering of alert criteria to focus on relevant events and reduce noise.
- Limited Archiving Capability: Offers basic archiving functionality, although limited to a one-month timeframe.
- Designed for Windows Server: Specifically designed to run on Windows Server environments, ensuring compatibility and seamless integration.
Why do we recommend it?
Netwrix Event Log Manager offers a simplified yet effective solution for event log management, serving as a lighter version of their comprehensive Auditor software. We've tested the Log Manager extensively and found it to be a reliable tool for consolidating events across an entire network, providing real-time email alerts for critical events, and offering basic filtering and archiving functionalities. While the freeware version meets basic needs, we recommend it particularly for smaller networks or environments where prompt alerting and efficient log consolidation are essential.
A larger network of systems or one where security and prompt alerting are key would have a hard time getting by on the freeware version alone, however.
Who is it recommended for?
Netwrix Event Log Manager is recommended for organizations, particularly smaller networks, seeking a straightforward yet powerful tool for event log management. It is well-suited for environments where prompt alerting of critical events and centralized log consolidation are priorities. Additionally, businesses looking to optimize their Windows Server environments will find the Log Manager to be a valuable asset in enhancing security and operational efficiency.
Pros:
- Completely Free Log Consolidation: Offers comprehensive log consolidation capabilities at no cost, making it accessible to organizations of all sizes.
- Windows Server Compatibility: Designed to run on Windows Server environments, ensuring seamless integration and optimal performance.
- Lightweight Tool: Ideal for smaller networks seeking efficient event log management without excessive resource consumption.
Cons:
- Outdated Interface: The interface may feel outdated, reminiscent of older Windows Server versions, potentially affecting user experience and aesthetics.
Price: Freeware, Netwrix also has a trial for a more robust Auditor software for event logs
Download: http://www.netwrix.com/event_log_archiving.html
8. Splunk
Splunk is a log management program which does a great job encapsulating data from an entire range of devices across a network. It also has the ability to be expanded via add-ons and plugin apps to increase its already powerful core functionality!
Key Features:
- Comprehensive Log Management: Captures data from a wide range of devices across networks for thorough analysis and monitoring.
- Extensibility through Add-ons: Allows for expansion of core functionality via add-ons and plugin apps, enhancing versatility and customization.
- Flexible Deployment Options: Can be deployed on-site, in a hybrid environment, or fully in the cloud, offering remote management flexibility.
- Scalability: Scales excellently from small offices to multiple data centers, catering to varying organizational needs and growth.
- Behavior Analysis for Threat Detection: Utilizes behavior analysis to detect threats beyond traditional log monitoring, enhancing security measures.
Why do we recommend it?
Splunk stands out as a robust log management program renowned for its ability to comprehensively capture data from diverse devices across networks. Our own testing has confirmed its effectiveness in consolidating and analyzing logs, offering invaluable insights into network activity. One of its notable strengths lies in its extensibility through add-ons and plugin apps, enhancing its already powerful core functionality. Whether deployed on-site, in a hybrid environment, or fully in the cloud, Splunk excels in remote management, catering to a wide range of organizational needs and scaling seamlessly from small offices to large data centers.
Splunk is also unusually flexible by merit of being able to work fully on-site, hybrid on-site/cloud, or fully in a cloud environment to ease remote management, all while scaling excellently all the way from small offices to multiple data-centers!
Who is it recommended for?
Splunk is highly recommended for enterprises seeking advanced log management capabilities and comprehensive threat detection. Its flexibility in deployment options makes it suitable for organizations of various sizes, from small offices to large data centers. Additionally, businesses prioritizing user-friendly interfaces, visual data representation, and customizable options will find Splunk to be an invaluable tool in optimizing operations and enhancing security.
Pros:
- Advanced Threat Detection: Utilizes behavior analysis to detect threats not captured through conventional log monitoring, enhancing security posture.
- User-Friendly Interface: Boasts an excellent user interface with highly visual data representation and easy customization options, facilitating efficient data analysis.
- Easy Event Prioritization: Simplifies event prioritization, allowing organizations to focus on critical issues promptly.
- Enterprise Focus: Designed with enterprise needs in mind, catering to the requirements of large-scale deployments and complex environments.
- Cross-Platform Compatibility: Available for both Linux and Windows environments, ensuring compatibility with diverse IT infrastructures.
Cons:
- Pricing Contact Required: Requires contacting sales for pricing information, potentially causing delays in procurement and budget planning.
- Enterprise-Centric Cost Structure: More suitable for large enterprises due to its cost-prohibitive nature for small businesses, potentially limiting accessibility.
- Steep Learning Curve for Query Language: Utilizes a custom Search Processing Language (SPL) for queries, which may steepen the learning curve for users unfamiliar with the language.
Price: Free
Download: https://www.splunk.com/en_us/devops.html
9. Progress WhatsUp Gold Log Management Suite
WhatsUp Gold, by Progress Software Corporation, is a well-known system monitoring tool. However, the product line also includes a less-well-known log file manager, called the Log Management Suite, which installs on Windows Server.
Key Features:
- Comprehensive Log Management: Captures and stores event logs, Syslog messages, and IIS log files in a structured manner for efficient analysis and compliance.
- Archiving and Protection: Offers capabilities for archiving, restoring, and protecting log files, ensuring data integrity and compliance with industry standards.
- Intuitive File Viewer: Includes a user-friendly file viewer with sorting, grouping, and filtering functionalities to support in-depth log analysis.
- Pre-Written Report Formats: Provides pre-written report formats compliant with various data security standards, facilitating compliance and regulatory requirements.
- Modular Pricing and Flexible Deployment: Supports modular pricing options and flexible deployment choices, including LANs, WANs, and cloud-based applications, enhancing scalability and cost-effectiveness.
Why do we recommend it?
Progress WhatsUp Gold Log Management Suite offers a comprehensive solution for managing event logs and log files with ease. Our testing confirms its efficiency in capturing and storing event logs, including Syslog messages and IIS log files, in a structured manner. Notably, the suite provides robust capabilities for archiving, restoring, and protecting log files, ensuring data integrity and compliance with industry standards. Its intuitive file viewer with sorting, grouping, and filtering functionalities facilitates in-depth analysis, while pre-written report formats cater to various data security standards, enhancing overall operational efficiency and compliance.
The Log Management Suite is an Event Log server. It captures Event logs as they circulate around the system and stores them in rotated files held in a meaningful directory structure. The service also acts as a Syslog server and it is capable of managing IIS log messages as well.
In addition to its capture and log file creation capabilities, the Log Management Suite can archive, restore, and protect log files. The suite includes a file viewer that has sorting, grouping, and filtering abilities to support analysis. The pack includes pre-written report formats that can be applied to log data stores. These are available in editions to comply with HIPAA, SOX, FISMA, PCI, MiFID, Basel II and other data security standards.
Who is it recommended for?
Progress WhatsUp Gold Log Management Suite is recommended for organizations seeking a reliable and scalable solution for event log management on Windows Server environments. It is particularly suitable for businesses requiring comprehensive log management capabilities, including archiving and compliance support. Additionally, companies looking for modular pricing options and flexible deployment choices, including LANs, WANs, and cloud-based applications, will find the suite to be a valuable asset in optimizing network monitoring and security.
Pros:
- Simple Visualizations: Utilizes simple visualizations for at-a-glance insights, enhancing ease of use and understanding.
- Modular Pricing: Offers modular pricing options, allowing companies to pay only for the features they intend to use, ensuring cost-effectiveness.
- Versatile Monitoring Capabilities: Can monitor LANs, WANs, and cloud-based applications such as container environments, providing flexibility and adaptability to diverse network environments.
Cons:
- Limited to Windows Server: Available only for Windows Server environments, limiting accessibility for organizations with different operating system preferences.
- Modular Upgrades Consideration: Modular upgrades might not be suitable for organizations intending to utilize all aspects of a networking monitor, potentially leading to inefficiencies in feature utilization.
- No Cloud-Based Version: Lacks a cloud-based version, limiting deployment options for organizations preferring cloud-based solutions.
Price: Progress doesn’t publish its prices for the Log Management Suite.
Official site: https://www.whatsupgold.com/log-management
10. Tripwire Log Center
TripWire Log Center is focused more on the security-minded with tools that excel at identifying and responding to threats while swiftly assuring that all devices and traffic meet proper compliance, even for the most strict regulatory needs!
Key Features:
- Threat Identification and Response: Excels at identifying and responding to threats swiftly, ensuring the security of the environment.
- Compliance Assurance: Stringent regulatory requirements through extensive backup and protection features.
- Real-Time Monitoring: Supports real-time monitoring, enabling proactive threat detection and response.
- Vulnerability Scanning: Capable of scanning for vulnerabilities and detecting/configuring changes, enhancing overall security posture.
- Suitability for Larger Networks: Better suited for larger networks where comprehensive monitoring and security measures are essential.
Why do we recommend it?
Tripwire Log Center is a precision tool designed to meet the rigorous security and compliance needs of organizations. Our evaluation has revealed its exceptional capabilities in identifying and responding to threats swiftly, while ensuring compliance with the most stringent regulatory requirements. Unlike all-encompassing solutions, Tripwire Log Center focuses on log management and analysis, complemented by extensive backup and protection features. This precision approach provides organizations with confidence in the security and compliance of their environments, making it a highly recommended solution for safeguarding sensitive data and infrastructure.
This software is less of an all encompassing tool and is more of a precision one for making sure that your environment is compliant and secure, and helps assure that by merit of extensive backup and protection features on top of log management and analysis.
Who is it recommended for?
Tripwire Log Center is recommended for security-minded organizations seeking a precise solution for ensuring compliance and security across their environments. It is particularly well-suited for larger networks where comprehensive monitoring and rapid threat response are paramount. Additionally, organizations with strict regulatory needs will find Tripwire Log Center invaluable in maintaining compliance and mitigating security risks effectively.
Pros:
- Real-Time Monitoring: Enabling proactive threat detection and response to ensure network security.
- Vulnerability Scanning: Capable of scanning for vulnerabilities and detecting/configuring changes, enhancing overall security posture.
- Suitability for Larger Networks: Designed to meet the needs of larger networks, providing scalability and comprehensive security coverage.
Cons:
- Limited Free Access: Only available as a free demo with no permanent free version, potentially limiting accessibility for organizations seeking a trial before purchase.
- Interface Improvement Needed: The interface could benefit from improvements to enhance user experience and ease of use.
Price: Free demo on website, must request quote for pricing information but ballparks in the $7,000 range for the core with additional cost per server/desktop monitored
Download: https://www.tripwire.com/products/tripwire-log-center
11. Quest InTrust
Quest InTrust aims to help make managing large amounts of information in a broad environment easier and, ultimately, cheaper as well.
Key Features:
- Event Viewer Log Management: Designed for efficient data collection and management from Event Viewer logs, ensuring comprehensive monitoring and analysis.
- Intelligent Compression: Automatically compresses logs to conserve storage space, ideal for environments with limited disk space or storage constraints.
- Security Auditing: Supports auditing of security practices to ensure compliance with regulatory requirements and mitigate security risks effectively.
- Tamper Protection: Provides tamper protection through caching and duplication, enhancing data integrity and security measures.
- Comprehensive Event Log Analysis: Offers broad capabilities for analysis of logged events on various scales, providing valuable insights for troubleshooting and security monitoring.
Why do we recommend it?
Quest InTrust simplifies the management of vast amounts of information across diverse environments, offering cost-effective solutions for data storage and management. Our evaluation confirms its effectiveness in reducing storage and data management costs through intelligent compression and robust auditing features. InTrust ensures regulatory compliance by auditing security practices, while its broad event log analysis capabilities enable comprehensive insights into logged events at any scale. With a focus on data collection and management from Event Viewer logs, InTrust provides valuable tools for optimizing storage efficiency and enhancing security measures.
It helps reduce storage and data management costs with intelligent compression and also has excellent features for auditing security practices to be certain regulatory needs are met. InTrust also has a broad ability to perform analysis on logged events on almost any scale.
Who is it recommended for?
Quest InTrust is recommended for organizations dealing with large volumes of data across diverse environments, seeking efficient and cost-effective solutions for data management and security auditing. It is particularly suitable for businesses requiring compliance with regulatory standards, as InTrust offers robust features for auditing security practices and ensuring regulatory needs are met. Additionally, organizations facing challenges related to storage limitations or data management costs will find InTrust invaluable in optimizing storage efficiency and reducing operational expenses.
Pros:
- Efficient Event Viewer Log Management: Streamlines data collection and management from Event Viewer logs, facilitating comprehensive monitoring and analysis.
- Intelligent Compression: Automatically compresses logs to conserve storage space, making it ideal for environments with limited disk space or storage constraints.
- Robust Security Auditing: Supports auditing of security practices to ensure compliance with regulatory requirements, enhancing overall security posture.
- Tamper Protection Features: Provides tamper protection through caching and duplication, safeguarding data integrity against unauthorized modifications.
Cons:
- Nested Menus Complexity: The presence of too many nested menus can potentially impede user experience, especially during initial installation, requiring additional time to locate desired features.
Price: Free trial, must request quote for pricing information
Download: https://www.quest.com/products/intrust/
12. Corner Bowl Server Manager
Previously under the monikers of SpectorSoft andVeriato's Server Manager, Corner Bowl Server Manager is a very cost-effective tool, even at the enterprise level, that still offers much of the same power and versatility as some of the other options.
Key Features:
- Centralized Management Console: Offers a centralized console for disk monitoring, log management, reporting, and alerts, simplifying server infrastructure management.
- Versatile Log Collection: Supports log collection from both Windows and Azure AD environments, providing comprehensive coverage for diverse server setups.
- Compliance Reporting: Generates compliance reports for HIPAA, PCI DSS, and other regulatory guidelines, ensuring adherence to industry standards and best practices.
- In-depth Consolidation and Search Filters: Provides robust consolidation features and search filters for efficient log analysis and troubleshooting.
Why do we recommend it?
Corner Bowl Server Manager, formerly known as SpectorSoft and Veriato's Server Manager, offers exceptional value and versatility, even for enterprise-level deployments. Our assessment reveals its cost-effectiveness without compromising on power and functionality. With a centralized management console for disk monitoring, log management, reporting, and alerts, Server Manager provides comprehensive tools for managing server infrastructure efficiently. Its ability to generate reports compliant with stringent regulatory guidelines, such as HIPAA and PCI DSS, further enhances its value proposition, making it a highly recommended solution for organizations prioritizing cost-effective server management and regulatory compliance.
It has a centralized management console for disk monitoring, log management, reporting and alerts. The program even boasts reports specifically for meeting HIPAA, PCA, and other tough regulatory guidelines that some software would shy away from.
Who is it recommended for?
Corner Bowl Server Manager is recommended for organizations of all sizes seeking a cost-effective yet powerful solution for server management. It is particularly well-suited for smaller environments where comprehensive monitoring and compliance reporting are essential. Additionally, organizations subject to strict regulatory guidelines, such as HIPAA and PCI DSS, will find Server Manager invaluable in ensuring compliance and mitigating risks effectively.
Pros:
- Multi-Platform Log Collection: Supports log collection from both Windows and Azure AD environments, ensuring comprehensive coverage for diverse server setups.
- Comprehensive Search Filters: Provides in-depth consolidation features and search filters for efficient log analysis and troubleshooting, enhancing productivity and problem-solving.
- Regulatory Compliance Reporting: Generates compliance reports for HIPAA, PCI DSS, and other regulatory guidelines, facilitating adherence to industry standards and regulatory requirements.
Cons:
- Performance Issues in Larger Networks: Better suited for smaller environments, larger networks with 100+ systems may experience slowness, potentially affecting overall performance and user experience.
Price: Free trial, 10 node perpetual license as low as $84
Download: https://www.cornerbowlsoftware.com/ServerManager
13. LogRhythm
LogRhythm is a program that beautifully marries management of logs and events into a single smooth interface. It handles the gathering of log data from applications and databases alike from all sources available and even has automated archival and retrieval for searching. A great deal of the management aspect is fully automated, though still able to be manually adjusted as needed.
Key Features:
- Unified Interface: Seamlessly integrates log and event management into a single interface, simplifying monitoring and analysis tasks.
- Automated Log Gathering and Archival: Automatically gathers log data from various sources and provides automated archival and retrieval for efficient searching.
- User-Friendly Wizards: Utilizes simple wizards for setup and other security tasks, enhancing accessibility for beginners.
- Sleek and Customizable Interface: Features a sleek, visually appealing interface that is highly customizable to meet individual preferences and requirements.
- Artificial Intelligence and Machine Learning: Leverages artificial intelligence and machine learning for behavior analysis, enhancing threat detection and mitigation capabilities.
Why do we recommend it?
LogRhythm seamlessly integrates log and event management into a unified interface, offering a streamlined solution for organizations. Our assessment highlights its ability to gather log data from various sources, including applications and databases, with automated archival and retrieval capabilities for efficient searching. LogRhythm's emphasis on automation simplifies management tasks while retaining manual adjustment options for customization as needed. With user-friendly wizards for setup and a sleek, customizable interface, LogRhythm caters to both beginners and experienced users alike. Leveraging artificial intelligence and machine learning for behavior analysis further enhances its effectiveness in threat detection and mitigation.
Who is it recommended for?
LogRhythm is recommended for organizations seeking a comprehensive log and event management solution with user-friendly features and advanced capabilities. It is suitable for both beginners and experienced users, making it ideal for organizations of varying skill levels. Additionally, businesses prioritizing visual appeal and customization options will appreciate LogRhythm's sleek interface and high level of customization. Furthermore, organizations requiring advanced threat detection and behavior analysis capabilities will find LogRhythm invaluable in enhancing their security posture.
Pros:
- Beginner-Friendly Setup: Uses simple wizards for log collection setup and other security tasks, making it accessible to users with varying levels of expertise.
- Sleek and Customizable Interface: Boasts a visually appealing interface that is highly customizable, providing flexibility and enhancing user experience.
- Advanced Threat Detection: Leverages artificial intelligence and machine learning for behavior analysis, enhancing threat detection capabilities.
Cons:
- Lack of Trial Option: Would benefit from offering a trial option to allow potential users to experience the platform before making a commitment.
- Limited Cross-Platform Support: While highly effective, expanded cross-platform support would enhance accessibility and compatibility for users across different environments.
Price: Online demo available, must request quote for pricing information
Download: https://logrhythm.com/products/log-management/
14. SumoLogic
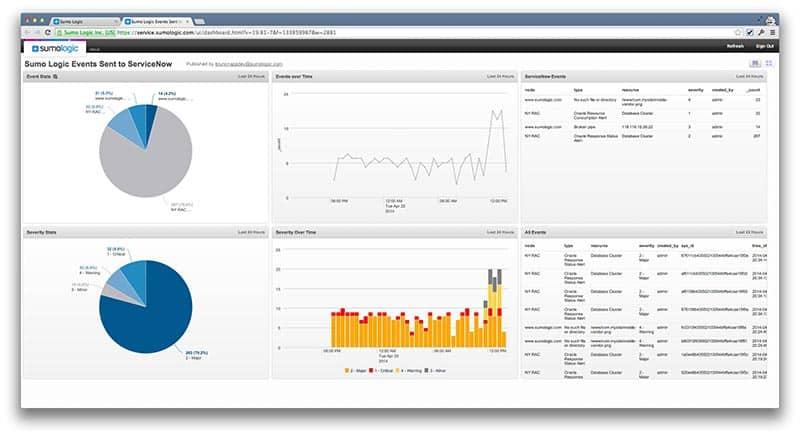
SumoLogic is somewhat unique in that it is a primarily cloud-based tool, which means that access need not be restricted by availability of a particular system or operating environment, and grants a great deal more freedom for a technician often traveling.
Key Features:
- Cloud-Based Flexibility: Primarily cloud-based tool offering unparalleled flexibility and accessibility for technicians, particularly those who frequently travel.
- Unique Forensics Approach: Runs forensics as separate threads to efficiently spread and isolate resource use in cloud space, enhancing performance and scalability.
- Intelligent Segmentation: Easily customizable solution to support the environment's needs without wasting resources, ensuring optimal performance and cost-effectiveness.
- Multi-Environment Support: Supports multiple environments including Linux, Windows, and Mac OS, catering to diverse IT infrastructures.
- Streamlined Installation and Configuration: Utilizes wizards to streamline installation and add-ons, simplifying the setup process and enhancing user experience.
Why do we recommend it?
SumoLogic stands out as a primarily cloud-based tool, offering unparalleled flexibility and accessibility for technicians, particularly those who frequently travel. Our evaluation highlights its unique approach to forensics, running them as separate threads to spread and isolate resource use efficiently in cloud space. SumoLogic's intelligent segmentation makes it exceptionally easy to customize the solution according to the needs of the environment, minimizing resource wastage while ensuring optimal performance. With support for multiple environments, streamlined installation using wizards, and a plethora of templates and premade assets, SumoLogic provides a user-friendly experience tailored to the diverse needs of organizations.
Who is it recommended for?
SumoLogic is recommended for organizations of all sizes seeking a cloud-based log management solution with flexible deployment options. It is particularly well-suited for technicians requiring remote access and flexibility, making it ideal for small to medium-sized businesses with dispersed teams. Additionally, organizations seeking simplicity in installation and configuration, along with a user-friendly experience, will find SumoLogic to be an invaluable tool for optimizing log management and analysis processes.
Pros:
- Supports Multiple Environments: Offers support for Linux, Windows, and Mac OS environments, ensuring compatibility across diverse IT infrastructures.
- Simple Installation and Configuration: Utilizes wizards to streamline installation and add-ons, simplifying the setup process and minimizing configuration complexities.
- User-Friendly Experience: Provides a plethora of templates and premade assets, making the experience user-friendly and accessible to users of all skill levels.
Cons:
- Better Suited for Small to Medium-Sized Businesses: While highly effective, SumoLogic may be more suited for small to medium-sized businesses, potentially lacking some features required by larger enterprises.
Price: Free trial, also data-volume limited version freely available, price starts at $90 per 1GB/day, with an annual pre-pay of $108 on monthly billing; different pricing available for enterprise level
Download: https://www.sumologic.com/pricing/
15. Logscape
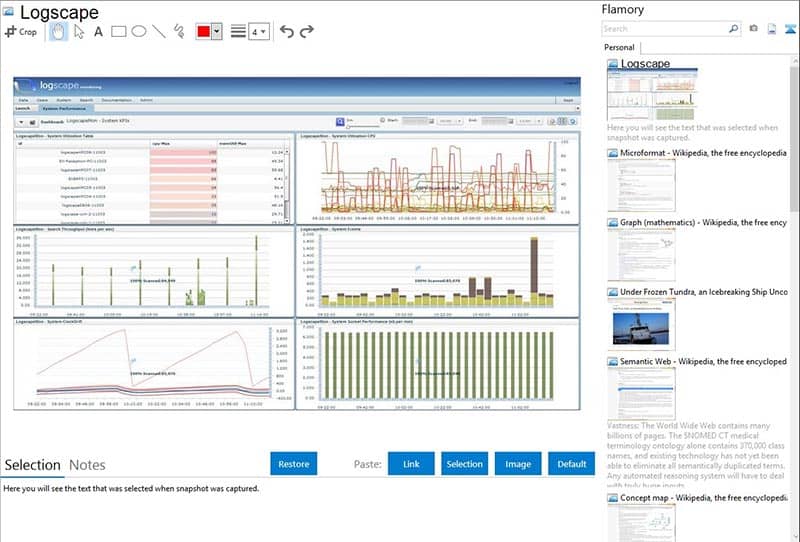
Logscape is a somewhat specialized tool but it makes up for that by merit of being quite powerful. It has almost unlimited ability to visualize, analyze, and search log information of nearly any size, which is something that other programs start to slow down or balk at the prospect of doing! It's front-end is heavily customizable to make it easier to quickly glimpse the information that is only most pertinent to your needs.
Key Features:
- Unlimited Data Visualization and Analysis: Offers almost unlimited ability to visualize, analyze, and search log information of any size, setting it apart from other programs.
- Flexibility in Data Integration: Extremely flexible, enabling users to pull data from virtually anywhere for comprehensive analysis.
- Highly Customizable Dashboard: The dashboard is highly customizable, allowing users to tailor it to their specific needs for quick access to pertinent information.
- Suitability for Processing Large Data: Best suited for companies processing large amounts of data from various sources, owing to its capability to handle substantial data volumes effectively.
Why do we recommend it?
Logscape is a specialized and powerful tool renowned for its unparalleled ability to visualize, analyze, and search log information of almost any size. Our evaluation underscores its exceptional flexibility, allowing users to pull data from virtually anywhere for comprehensive analysis. Logscape's capability to handle large volumes of data sets it apart from other programs, making it an invaluable asset for organizations processing substantial amounts of data from various sources. Additionally, its highly customizable front-end enables users to tailor the dashboard to their specific needs, facilitating quick access to pertinent information.
Who is it recommended for?
Logscape is recommended for organizations requiring a powerful log management solution capable of handling large volumes of data from diverse sources. It is particularly suitable for companies processing significant amounts of data and seeking a flexible tool that can adapt to their evolving needs. While Logscape may require more technical skills compared to competing tools, organizations with experienced IT teams will benefit from its advanced capabilities and customization options. Furthermore, Logscape's free limited version offers an opportunity for users to explore its features and determine suitability for their requirements.
Pros:
- Unparalleled Flexibility: Offers extremely flexibility, enabling users to pull data from virtually anywhere for comprehensive analysis.
- Free Limited Version: Provides a free limited version, allowing users to explore its features before making a commitment.
- Highly Customizable Dashboard: The dashboard is highly customizable, facilitating quick access to pertinent information tailored to users' needs.
Cons:
- Technical Skill Requirement: Requires more technical skills compared to competing tools, potentially limiting accessibility for less experienced users.
- Interface Improvement Needed: While powerful, the interface could benefit from improvements to enhance user experience and ease of use.
Price: Free trial with daily data limit, must request quote for pricing information
Download: http://logscape.com/index.html
Conclusion
Across any environment, the amount of logged information is positively staggered – in smaller offices or lesser enterprise situations it may be possible for a capable team of technicians to stay on top of it all, but even then it's ultimately a waste of time.
Having a solid solution for event management removes all the guesswork and grunt work from sorting through the vast swathes of data, and powerful real-time analytics and forensics cannot be underestimated when it comes to keeping things running smoothly without dramatic outages or security flaws.
Any environment lacking a reliable solution for keeping a close watch on event logs is one that is dangerously unaware of what trouble could already be brewing unseen.
Event Log Monitor Tools for Analyzing SIEM FAQs
What should you look for in Windows Event message management tools?
We reviewed the market for SIEM log managers and analyzed the options based on the following criteria:
- A system that can collect, consolidate, display, file, and manage Windows Event messages
- A service that can integrate Syslog and Event messages
- A dashboard that includes pre-set event analysis
- Automated security breach detection
- The option to load historical records into a data analyzer
- A no-cost assessment period or a free tool
- A good price that offers a bargain for the quality of tools offered or a no-cost tool
What are some common sources of event log data?
Some common sources of event log data include Windows Event Logs, syslog, application logs, and security logs.
How does event log monitoring differ from infrastructure monitoring?
Infrastructure monitoring focuses on the underlying components of a network or IT infrastructure, such as servers, storage devices, and networks, while event log monitoring focuses on the log data generated by these components.
What are some popular tools for event log monitoring?
Some popular tools for event log monitoring include Graylog, SolarWinds Log Analyzer, and LogRhythm.
What are some best practices for event log monitoring?
Some best practices for event log monitoring include regular collection and analysis of log data, integration with other enterprise systems, such as security information and event management (SIEM) systems, and regular review of log data to identify and resolve performance and security issues.
How can event log monitoring help with compliance and security?
Event log monitoring can help with compliance and security by providing a centralized view of log data from multiple sources, allowing organizations to identify and respond to security threats and meet regulatory requirements.
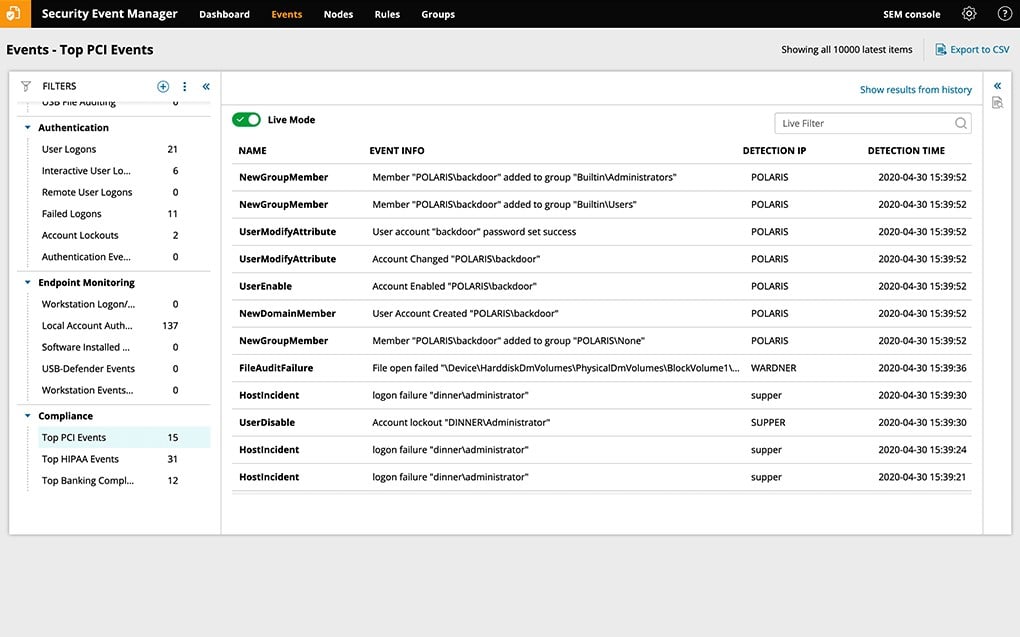
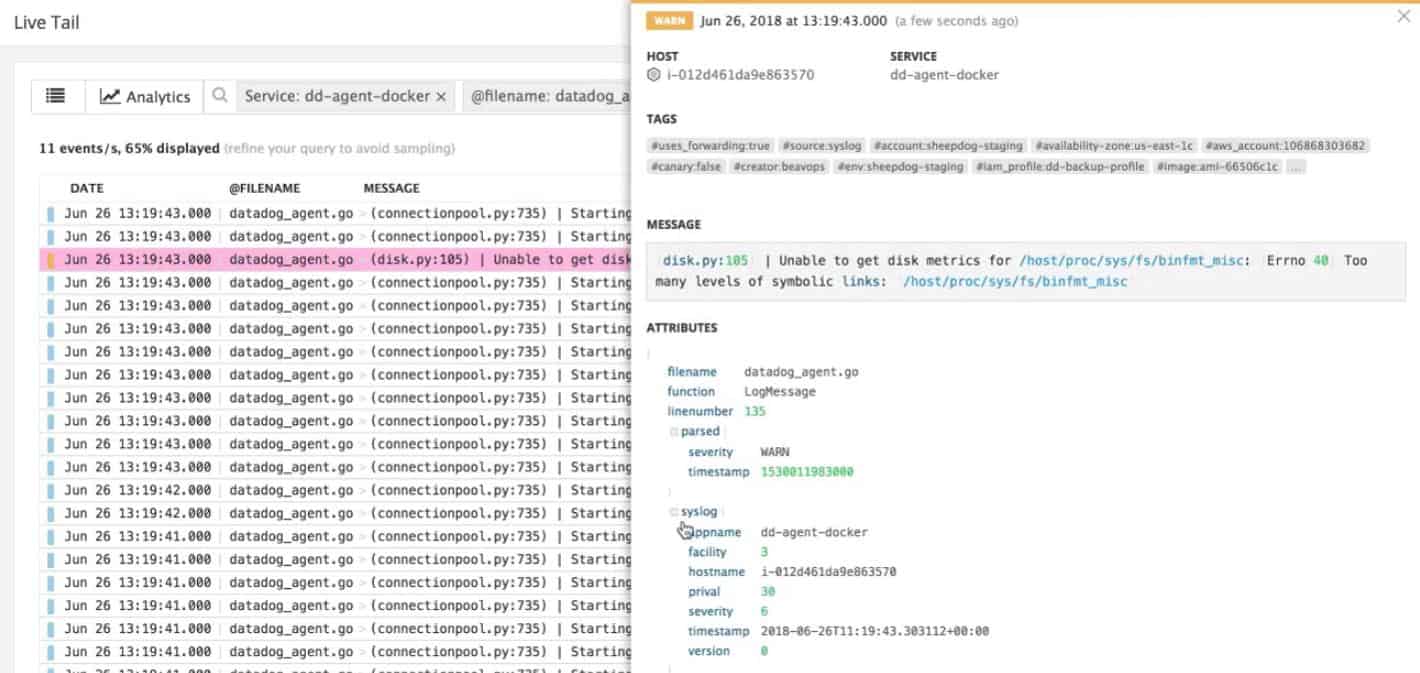
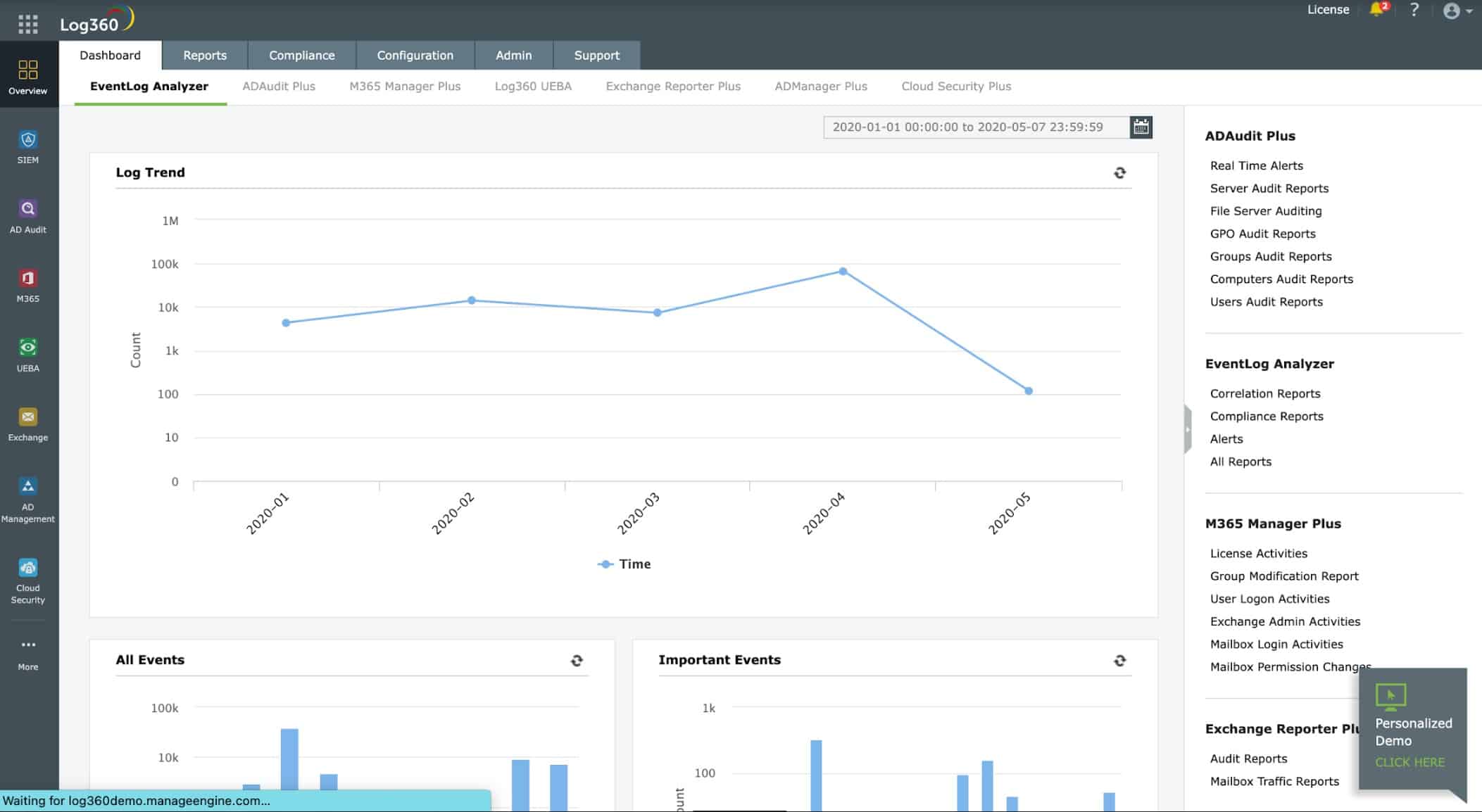
Security Event Manager from SolarWinds acts as a log collector, consolidator, and manager as well as a security monitoring system. You choose from a list of available collector agents and install them on the system that you want to monitor. These are available for Windows Events, Syslog, and software packages, including security systems. These agents then send collected log messages to the Security Event Manager server. The service can be on the same host as collectors. However, you can deploy these collectors on any site, thus centralizing your security monitoring service.
Key Features:
Why do we recommend it?
SolarWinds Security Event Manager offers comprehensive log management, security monitoring, and threat detection capabilities, making it an essential tool for organizations looking to enhance their cybersecurity posture. Our recommendation is based on its ability to collect, consolidate, and analyze log messages from various sources, enabling proactive threat detection and rapid response to security incidents. With risk-free trial options and features designed to facilitate compliance auditing, SolarWinds Security Event Manager provides value and peace of mind to organizations of all sizes.
The security monitoring part of this package checks through consolidated log messages as they arrive, looking for chains of attack. There are typical actions that hackers take when breaking into a system and exploring it, and records of the movements are built into the Security Event Manager. If the system spots one of those indicators, it homes in on that user account or connection source to look for other events in the chain. If one is spotted, the system raises an alert.
The Security Event Manager documents its own actions and the log storage system helps towards compliance auditing.
Who is it recommended for?
SolarWinds Security Event Manager is recommended for organizations seeking an advanced security monitoring and log management solution. Ideal for IT security professionals, compliance officers, and network administrators, this tool is designed to address the complex security challenges faced by modern enterprises. With its simple yet highly customizable dashboards and proactive AI-assisted threat detection capabilities, SolarWinds Security Event Manager is suitable for organizations committed to safeguarding their digital assets and ensuring regulatory compliance.