We may earn a commission if you make a purchase through the links on our website.
The Best File Integrity Monitoring Tools

UPDATED: February 28, 2024
File integrity monitoring tools work to protect systems safe after an intrusion. Let’s take a look at some of the best tools for the job.
Even with the best firewalls and security policies in place, files can still be lost or damaged. Whether that’s from a ransomware attack or simply an accidental deletion, file integrity monitoring can help save the day in a pinch.
Here is our list of the best File Integrity Monitoring (FIM) tools:
- ManageEngine ADAudit – EDITOR'S CHOICE Plus System activity tracking per user account as listed in Active Directory. Runs on Windows Server. Access the 30-day free trial.
- ManageEngine EventLog Analyzer – FREE TRIAL Monitor both files, as well as end-user behavior to detect compromised accounts proactively. Access the 30-day free trial.
- Datadog Security and Compliance Monitoring Offers a flexible cloud-based monitoring system that can encompass files, infrastructure, applications, and servers
- CrowdStrike Falcon FileVantage A system-wide file activity monitor that can be enhanced by threat intelligence. This is part of a cloud platform.
- SolarWinds Security Event Manager Offers forensic level auditing, automated file restoration, and compliance reports for all major standards.
- OSSEC An open-source HIDS and file integrity monitoring system
- Netwrix Auditor Can monitor files for changes as well as assist admins in demonstrating compliance and auditing access controls internally
How does file integrity monitoring work?
File Integrity Monitoring (FIM) software protects files from accidental changes, deletion, or attack by monitoring their state consistently for any changes you specify. As you can imagine, this can have a range of benefits in helping avoid downtime from lost or damaged files.
On a technical level, this is achieved by either calculating a checksum for each file or storing and comparing a live backup of the file to the current file in real-time. Both techniques work and can help networks fortify themselves against both internal and external threats.
FIM tools can be configured to detect many different changes, not just deletions. For instance, you can configure the FIM tool to automatically detect when a file is being encrypted and then tie that alert to a series of escalations and proactive countermeasures to remediate the attack automatically.
File integrity monitoring can also treat different types of files differently, which is helpful for organizations that adhere to compliance standards such as HIPAA or PCI DSS. Individual files or entire directories can be monitored for unauthorized access and help ensure those files do not leave certain areas of the network.
One of the most powerful features of file integrity monitoring is the automatic restore feature. This immediately can recover the last known ‘good’ state of a file before it was tampered with. On an enterprise level, this can help save sysadmins tons of time manually recovering files. Some FIM tools can even save different incremental backups that reflect changes of a document over a longer time.
If nothing else, file integrity monitoring can be an early warning system that something is amiss in your network. When you combine alert notifications with an automatic file restore policy, you can simultaneously escalate the issues internally and prevent end-user downtime at the same time.
What to look for in a file integrity monitoring tool
Not all FIM tools are created equal. The best FIM tools will be able to send alerts across various channels and to explore and utilize fully restored files automatically when they are changed or deleted. This proactive feature is one of the essential features you’ll want to keep in mind when looking for the best file integrity monitoring tool for your organization.
If your organization follows compliance guidelines, make sure that your FIM tool supports the level of monitoring needed to help aid in compliance. Some FIM tools can detect when unauthorized access is attempted internally. Logging this information can help paint whether inappropriate access was an accident or intentional.
Many tools nowadays offer more than one method of protection. When looking for an FIM tool, keep an eye out for a tool that can do more. For example, many monitoring solutions can now monitor multiple environments, servers, and applications all under one tool.
File integrity monitoring tools can be resource-intensive, meaning their logs can take up a lot of disk space, especially on more extensive networks. Think about where you want your FIM tool to live. If you have servers with adequate space, the solution can be hosted on-site. If you lack server infrastructure or simply want to take advantage of a more scalable solution, a cloud-based FIM tool will be a better choice.
The best File Integrity Monitoring tools
Now that we’ve explored how FIM tools work and what they can do. Let’s look at our top picks for the best file integrity monitoring tools on the market.
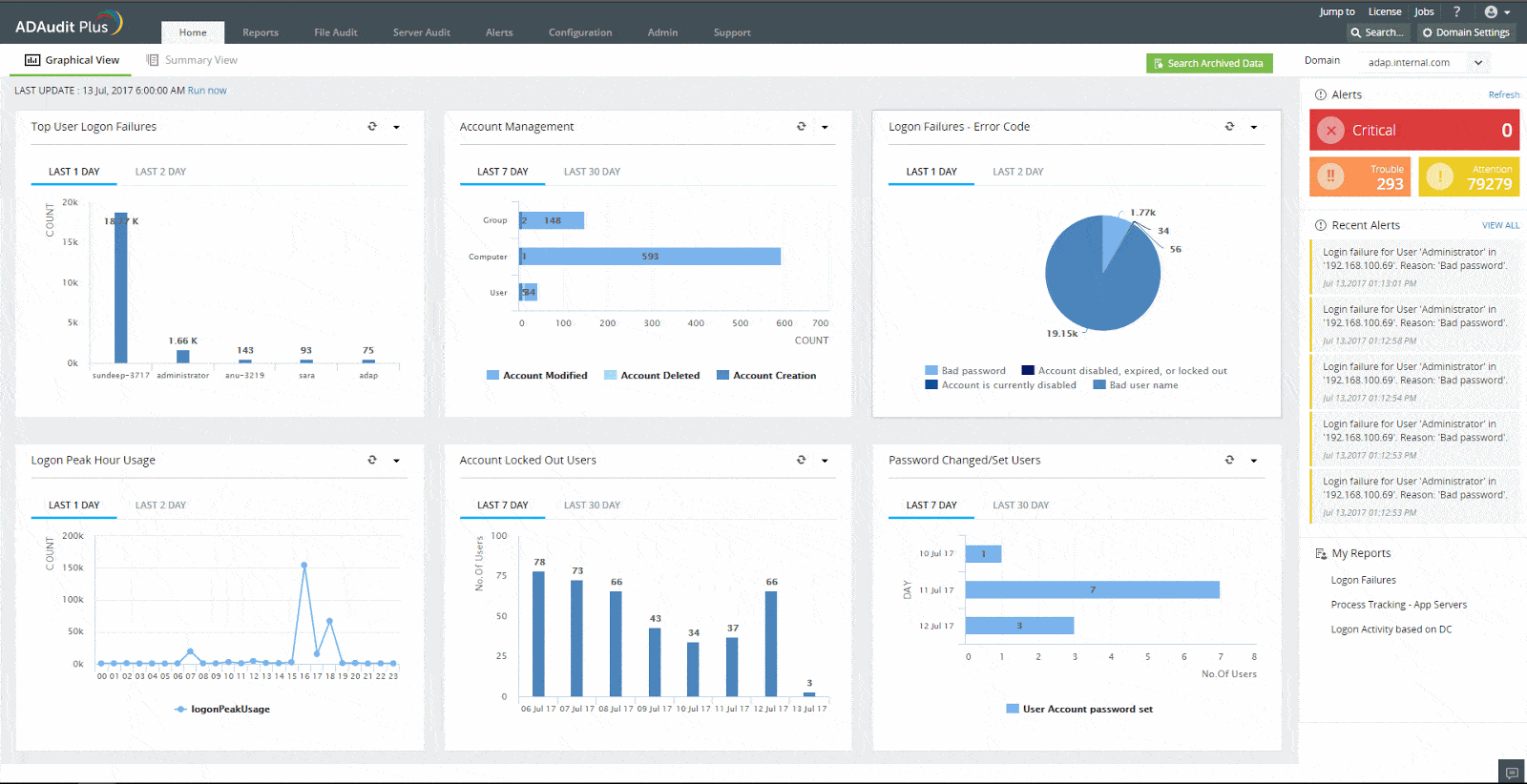
1. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus tracks all user activities and establishes a pattern of normal behavior for each account listed in Active Directory. This is a user behavior analytics strategy that waits for deviations from standard behavior that could indicate account takeover or an insider threat. The tool practices file integrity monitoring by logging all data access events.
Key Features
- Compliance Reporting: Generates comprehensive reports for GDPR, GLBA, HIPAA, PCI DSS, and SOX compliance, ensuring adherence to regulatory requirements.
- User Behavior Analytics: Tracks user activities and establishes patterns of normal behavior to detect anomalies indicative of security threats.
- Active Directory Auditing: Monitors Active Directory accounts, including inactive user accounts, to identify and address security vulnerabilities.
- Location-Based Activity Monitoring: Identifies unusual login locations and raises alerts for excessive failed login attempts, enhancing threat detection capabilities.
- Access Control Auditing: Examines file access events and access controls within Active Directory to enforce security policies and prevent unauthorized access.
Why do we recommend it?
ManageEngine ADAudit Plus earns our recommendation for its robust user behavior analytics capabilities coupled with comprehensive Active Directory auditing features. By tracking all user activities and establishing patterns of normal behavior, ADAudit Plus provides a proactive approach to detecting potential security threats, such as account takeovers or insider risks. Through file integrity monitoring and access control auditing, ADAudit Plus offers organizations a powerful tool to safeguard their sensitive data and mitigate security risks effectively. Our recommendation is based on thorough testing, affirming ADAudit Plus's effectiveness in enhancing overall security posture and compliance readiness.
The system doesn’t lock files with encryption to guard access. However, it relies on the access controls of Active Directory to limit the user who can log in to file servers and explore the contents of the files that they store.
The tool also includes methods for auditing Active Directory accounts, such as the inactive user accounts report that lets you know the vulnerable abandoned accounts that you need to delete.
The system is able to identify the actual people associated with each account, including their location. This is an important detail because if a user account is used from a location other than that user’s usual workplace, there will be a high probability that the user account has been hijacked. Other location-related activity is also examined such as if a user logs in from illogically distance locations. The tool raises an alert if excessive failed login attempts occur with an account – this could indicate a brute force credentials cracking attempt.
Who is it recommended for?
ADAudit Plus is recommended for organizations seeking a comprehensive solution to monitor and secure their Active Directory environments. Small to large enterprises across various industries can benefit from ADAudit Plus's robust features, including user behavior analytics and compliance reporting capabilities. IT administrators, security professionals, and compliance officers can leverage ADAudit Plus to gain insights into user activities, detect suspicious behavior, and ensure regulatory compliance with standards such as GDPR, GLBA, HIPAA, PCI DSS, and SOX. Additionally, organizations looking to streamline Active Directory management and enhance security practices will find ADAudit Plus to be a valuable asset in identifying and addressing security vulnerabilities effectively.
Pros:
- Comprehensive Compliance Reporting: Provides compliance reporting for various regulatory standards, ensuring organizations meet legal requirements.
- Advanced User Behavior Analytics: Offers insights into user activities and detects suspicious behavior for proactive threat detection.
- Effective Active Directory Auditing: Monitors and audits Active Directory accounts, including inactive accounts, for enhanced security.
- Location-Based Activity Monitoring: Alerts for unusual login locations and excessive failed login attempts, enhancing threat visibility.
- Access Control Auditing: Examines file access events and access controls to enforce security policies and prevent unauthorized access.
Cons:
- Limited Data Store Identification: Does not identify sensitive data stores, potentially limiting visibility into data security risks.
ManageEngine ADAudit Plus runs on Windows Server and it is available for a 30-day free trial.
2. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer is another SIEM tool that uses file integrity monitoring as its cornerstone feature. The platform can automatically protect files, audit their access, and monitor permission changes that have taken place on that file.
Key Features
- File Integrity Monitoring: Automatically protects files, audits access, and monitors permission changes, serving as an early warning system for security threats.
- Compliance Auditing: Provides compliance auditing tools and reports for standards such as FISMA, SOX, HIPAA, or PCI DSS, facilitating regulatory adherence.
- Customizable Dashboards: Offers customizable dashboards suitable for network operation centers, enhancing visibility and operational efficiency.
- Multiple Alert Channels: Supports SMS, email, and app integration for notifying teams, ensuring timely response to security incidents.
- User and Entity Behavior Analytics (UEBA): Identifies insider attacks and compromised accounts by analyzing user behavior, enhancing threat detection capabilities.
Why do we recommend it?
ManageEngine EventLog Analyzer earns our recommendation for its robust file integrity monitoring capabilities coupled with comprehensive compliance auditing features. As a cornerstone feature, file integrity monitoring ensures the automatic protection of files, audit of access, and monitoring of permission changes, bolstering data security measures. Through customizable dashboards and multiple alert channels, EventLog Analyzer facilitates effective monitoring and notification processes, enhancing overall operational efficiency and threat response capabilities. Our recommendation is based on extensive testing, confirming EventLog Analyzer's effectiveness in providing actionable insights and mitigating security risks proactively.
The tool uses two primary features to keep track of file integrity. It first takes a snapshot of files in their ideal state if changes to explore and utilize entirely need to be reversed. Alerts can then be configured to trigger when changes are made and offer a side-by-side before and after look.
Included in the file monitoring is a series of compliance auditing tools and reports that can aid in adhering to standards such as FISMA, SOX, HIPAA, or PCI DSS. Reports can be run via one of the templates provided or customized to your liking. Export options include both PDF and CSV, allowing reports to be used for presentations as well as spreadsheets.
On top of file integrity monitoring, the system goes a bit deeper and provides an extra layer of monitoring on the end-user level. This is called User and Entity Behavior Analytics (UEBA) and helps sysadmins identify insider attacks and compromised accounts. This feature goes beyond file or log monitoring by understanding how users behave daily and then alerting them to strange behavior when detected.
Who is it recommended for?
EventLog Analyzer is recommended for organizations seeking a robust SIEM solution with a focus on file integrity monitoring and compliance auditing. It caters to a wide range of industries and organizational sizes, from small businesses to large enterprises, offering scalable options to meet diverse security needs. IT administrators, security professionals, and compliance officers can leverage EventLog Analyzer to ensure adherence to regulatory standards such as FISMA, SOX, HIPAA, or PCI DSS. Additionally, organizations concerned about insider attacks and compromised accounts can benefit from its User and Entity Behavior Analytics (UEBA) feature, enhancing threat detection capabilities. With customizable dashboards and comprehensive reporting options, EventLog Analyzer is ideal for organizations prioritizing data security and regulatory compliance.
Pros:
- Customizable Dashboards: Enhances visibility and operational efficiency, particularly suitable for network operation centers.
- Multiple Alert Channels: Facilitates timely response to security incidents by notifying teams across various channels.
- Anomaly Detection: Uses anomaly detection to assist technicians in identifying and addressing potential security threats.
- File Integrity Monitoring: Acts as an early warning system for ransomware, data theft, and permission access issues.
- Forensic Log Audit Features: Enables admins to create reports for legal cases or investigations, enhancing compliance and security measures.
Cons:
- Lack of Mobile App: Currently does not offer a mobile app for convenient access and monitoring.
- Interface Complexity: Could benefit from a more intuitive interface to streamline user experience.
- Learning Curve: May pose challenges during setup due to its steep learning curve, requiring time and effort to fully utilize its capabilities.
The platform comes in three different pricing options, Free, Premium, and Distributed. The free tier allows companies to monitor up to five log files but does not include file integrity monitoring. The tool is available for Windows and Linux and can be tested for free through a 30-day free trial.
3. Datadog Security and Compliance Monitoring
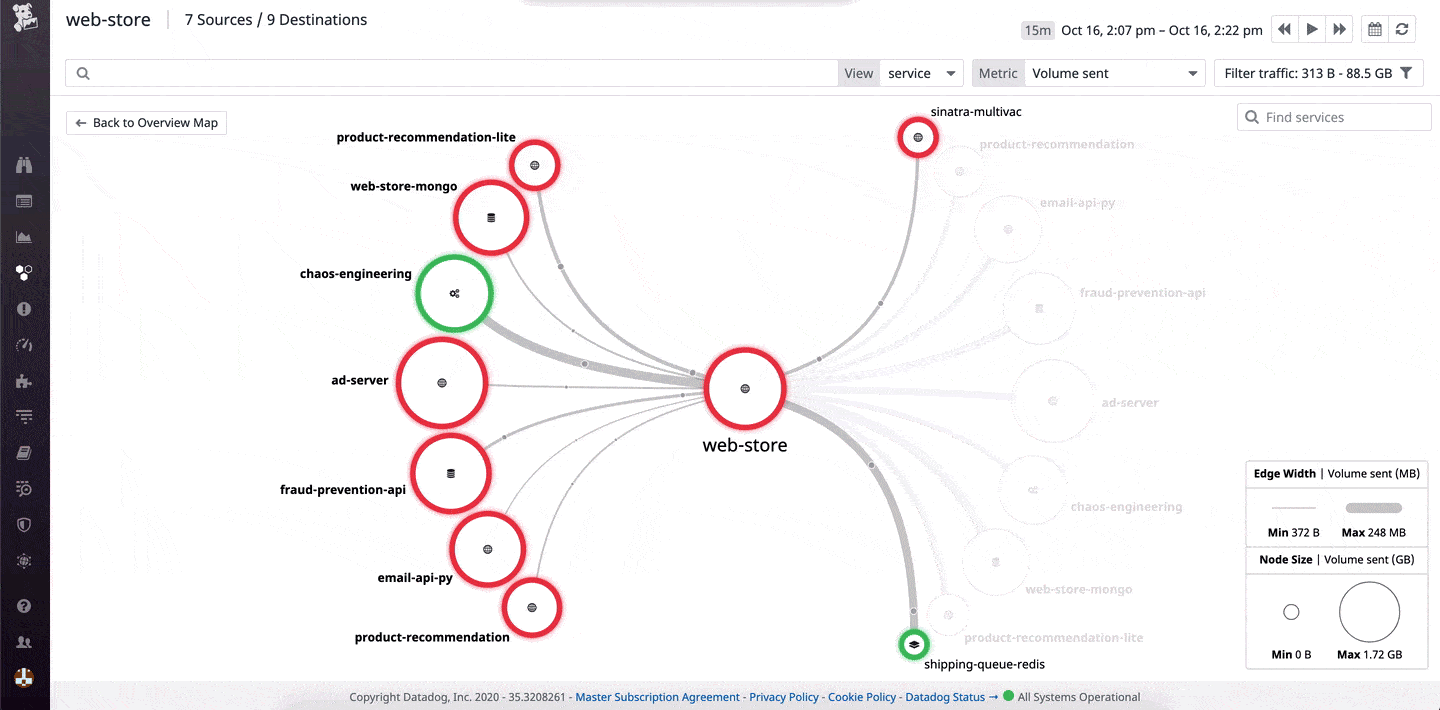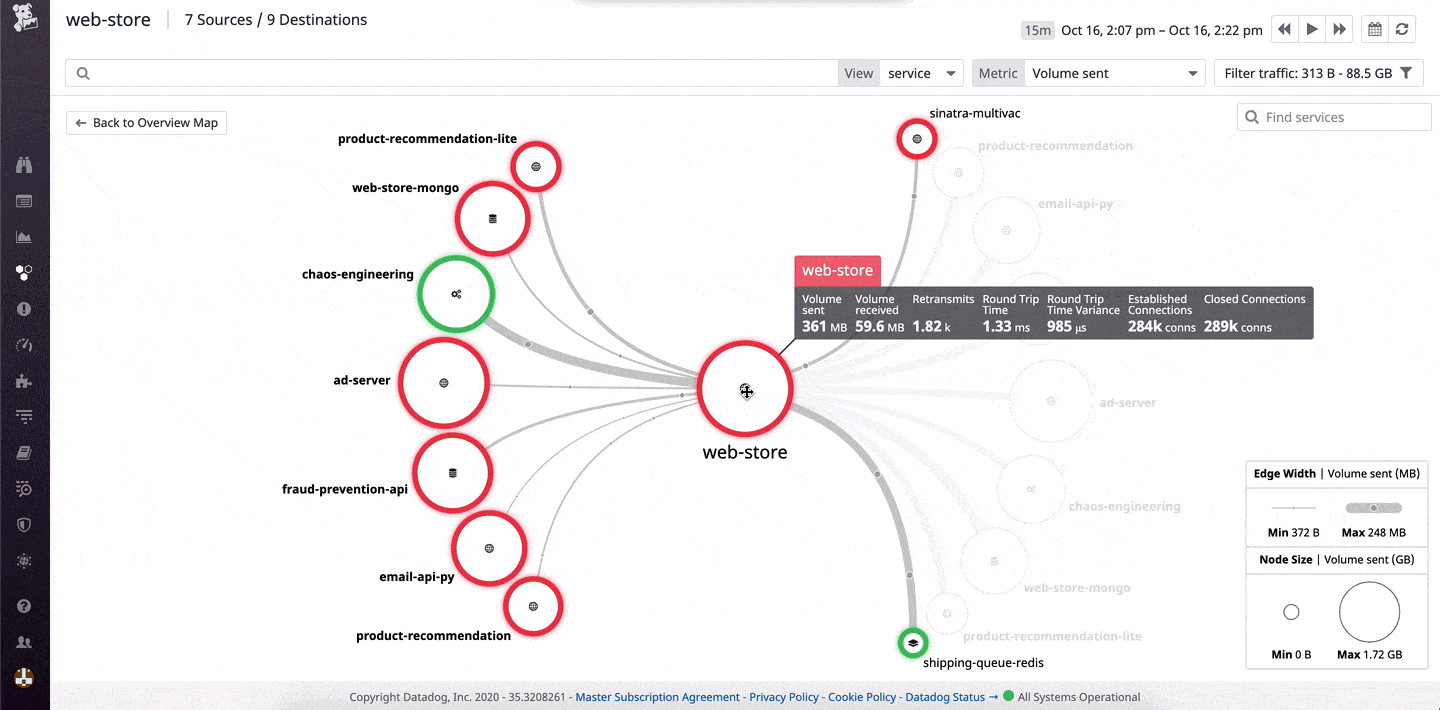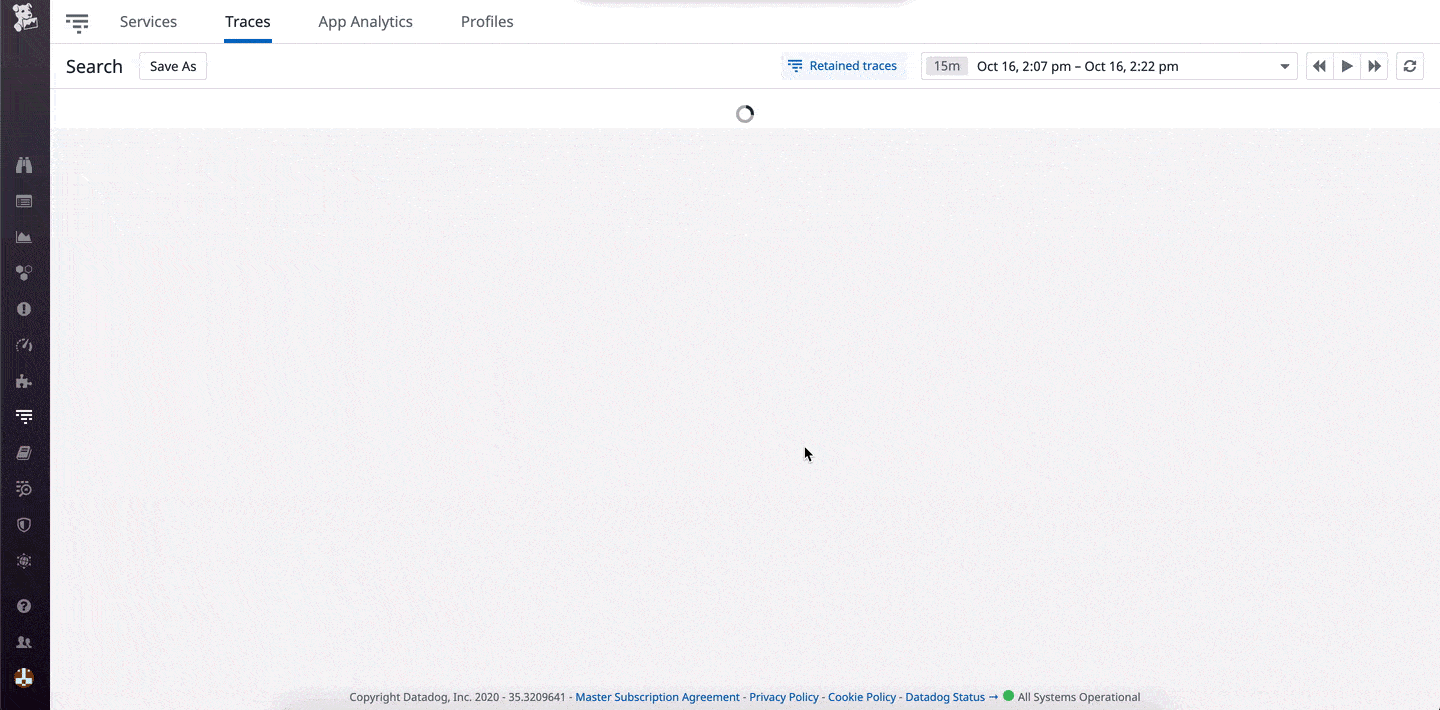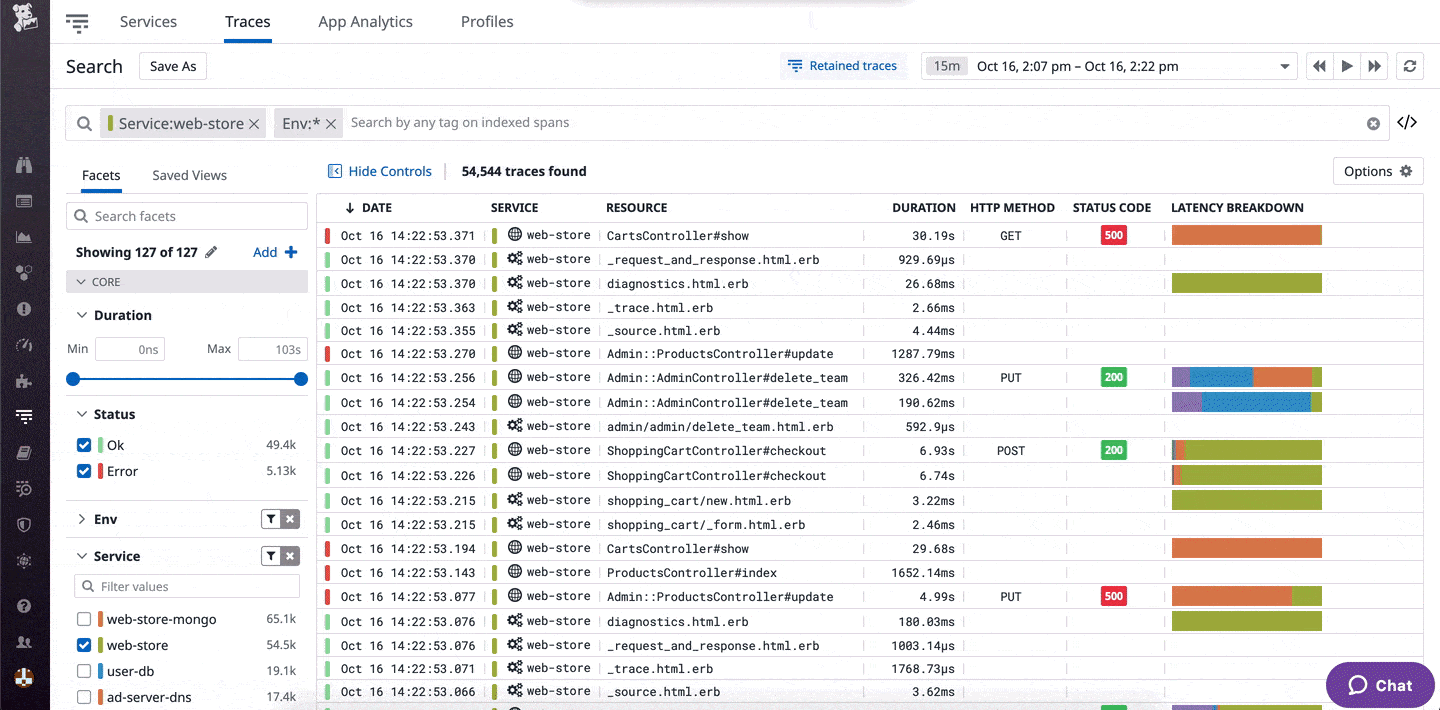
Datadog Security and Compliance Monitoring is a cloud-based set of monitoring tools that can aid in monitoring files, as well as monitoring servers, applications, and infrastructure. By offering this monitoring in the cloud, it allows organizations who don’t have the infrastructure to support heavy monitoring a chance to leverage file integrity monitoring that was once only available to the enterprise.
Key Features
- Cloud-Based Monitoring: Offers monitoring tools in the cloud, providing accessible file integrity monitoring and infrastructure monitoring capabilities.
- Customizable Dashboard: Highly customizable dashboard for easy visualization and analysis of live and historical data.
- Live Network Mapping: Utilizes live network mapping to pull in new devices and reflect changes in the network in real-time.
- Ruleset Editor: Allows users to build customized alerts and automated incident response based on event log data with ease.
- Wide Range of Integrations: Offers over 450 integrations into different applications and tools, supporting a comprehensive monitoring strategy.
Why do we recommend it?
Datadog Security and Compliance Monitoring earns our recommendation for its cloud-based monitoring tools, offering accessible file integrity monitoring and comprehensive infrastructure monitoring capabilities. By leveraging the cloud infrastructure, organizations of all sizes can benefit from advanced monitoring features previously only available to large enterprises. Datadog's standout feature lies in its user interface, which is highly customizable and intuitive, enabling easy visualization and analysis of live and historical data. Our recommendation is backed by extensive testing, highlighting Datadog's effectiveness in providing scalable and user-friendly monitoring solutions for enhanced security and compliance.
Where Datadog shines is in the user interface. Even when monitoring thousands of applications or files, the Datadog dashboard can be fully customized and easy to view for live and historical data analysis.
Like SolarWinds Security Event Manager, the platform monitors syslog files of different applications and servers to detect threats early on and ideally before impacting the network's performance. Upon installation, there are a series of detection rules that are designed to work immediately, so you won’t have to spend a ton of time configuring basic monitoring features.
For more customized alerts and automated incident response, users can use the ruleset editor to build their series or triggers, conditions, and actions based on event log data. This rule editor is surprisingly easy to use, especially compared to other SIEM tools on the market.
For organizations who think they want to expand their monitoring capabilities beyond just files, Datadog has over 450 integrations into different applications and tools that can help support a monitoring strategy with omnipresence.
Who is it recommended for?
Datadog Security and Compliance Monitoring is recommended for organizations seeking cloud-based monitoring solutions to enhance their security and compliance posture. Small businesses, as well as large enterprises, can leverage Datadog's monitoring tools to monitor files, servers, applications, and infrastructure with ease. IT administrators, security professionals, and compliance officers can benefit from Datadog's intuitive dashboard and customizable alerts for proactive threat detection and incident response. With over 450 integrations into different applications and tools, Datadog offers versatility and omnipresence in monitoring capabilities, making it suitable for organizations looking to expand their monitoring strategy effectively.
Pros:
- Intuitive Interface: Boasts one of the best interfaces for file/application monitoring, enhancing user experience.
- Live Network Mapping: Provides real-time updates on network changes, ensuring accurate monitoring of devices.
- Comprehensive Features: Offers a large number of templates, out-of-the-box features, and advanced tools for effective monitoring.
- Subscription Model: Accessibility to businesses of any size with a subscription model, ensuring affordability and scalability.
Cons:
- Short Trial Period: The 14-day trial period may be insufficient for thorough testing; a more extended 30-day trial period would be preferable.
You can test out Datadog utterly free through a 14-day trial.
4. CrowdStrike Falcon FileVantage
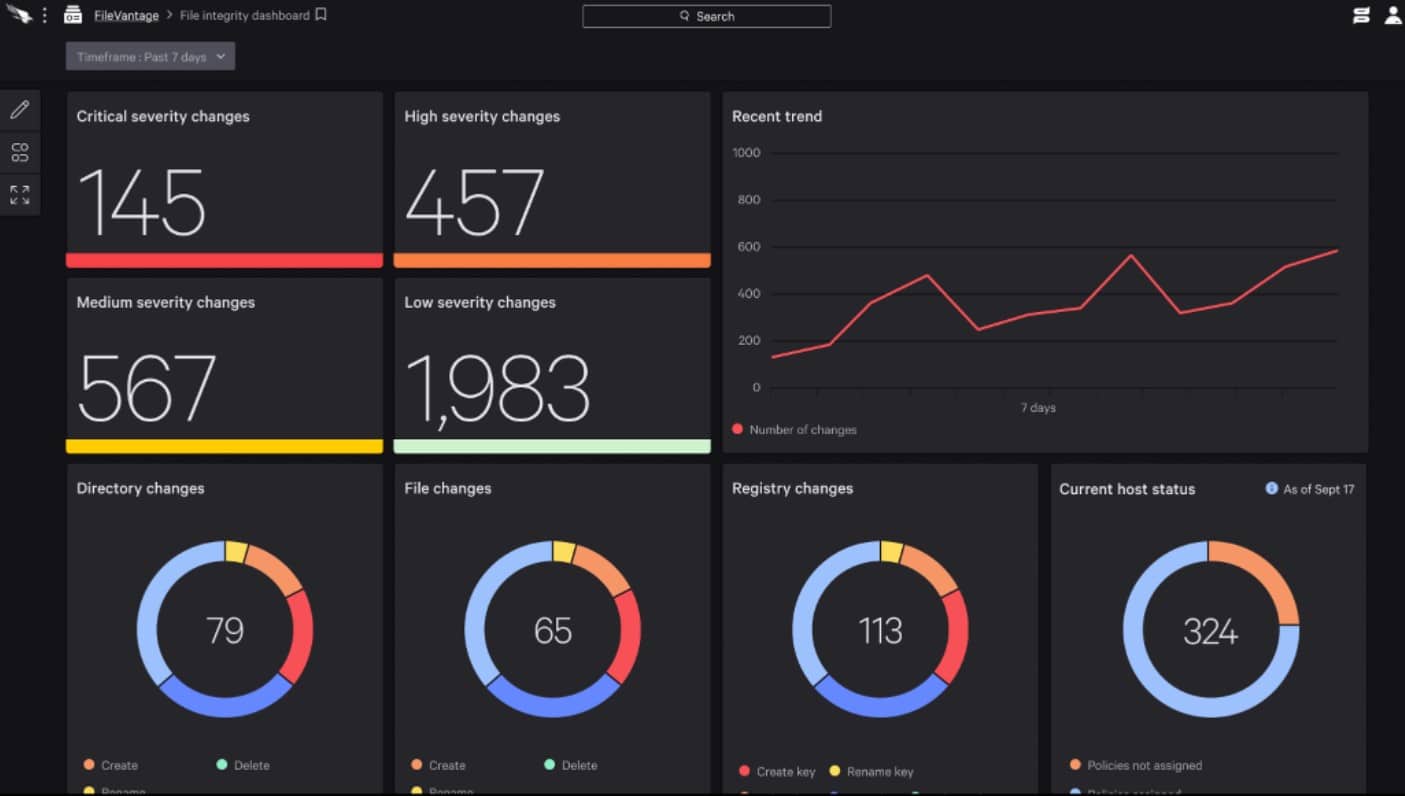
CrowdStrike Falcon FileVantage is part of a cybersecurity platform, called Falcon. This tool specializes in file integrity monitor. As it is a cloud-based service, its activities are not limited to one network or one server. You can enroll servers in many different locations, enabling you to centralize the security monitoring of file activities in one security operations center.
Key Features
- Cloud-Based Service: Enables centralized security monitoring across multiple servers and locations, offering unparalleled flexibility.
- Comprehensive Logging: Logs all file activities and records user account involvement, providing detailed insights into file changes.
- Customizable Monitoring: Allows administrators to tailor monitoring to specific files and criteria, reducing unnecessary notifications.
- Threat Intelligence Integration: Enhances monitoring with threat intelligence feeds, highlighting potential intruder or malware actions.
- Accessible Console: Hosted in the cloud, accessible from any standard web browser, providing ease of access and management.
Why do we recommend it?
CrowdStrike Falcon FileVantage earns our recommendation for its specialized file integrity monitoring capabilities integrated into the comprehensive Falcon cybersecurity platform. As a cloud-based service, FileVantage offers unparalleled flexibility, allowing organizations to centralize security monitoring across multiple servers and locations. With the ability to log all file activities and refine monitoring based on specific criteria, FileVantage provides actionable insights for threat detection and response. Our recommendation is grounded in extensive testing, highlighting FileVantage's effectiveness in enhancing overall security posture and facilitating proactive threat mitigation.
The Falcon FileVantage system logs all activities on all files resident on enrolled servers. The logs record the user account that was involved in each file change event. Administrators can refine the activities of the tool by excluding specific files. This reduces the number of notifications that appear in the system dashboard.
The console for Falcon FileVantage is hosted in the cloud and you can access it through any standard Web browser from anywhere. The console shows overall activity statistics on its home page and these are interpreted into graphs and charts. You can get a threat intelligence feed added to the monitor, which will highlight which file activity is more likely to be the result of intruder or malware actions. Alerts can also be managed by creating policies that specify specific files, directories, and actions that constitute an event that causes concern.
Who is it recommended for?
Falcon FileVantage is recommended for organizations seeking a robust file integrity monitoring solution as part of their cybersecurity strategy. Its cloud-based nature makes it suitable for businesses of all sizes and industries, enabling centralized security monitoring regardless of network or server location. IT administrators, security analysts, and SOC teams can benefit from FileVantage's intuitive console and customizable alerting capabilities for efficient threat detection and response. Additionally, organizations looking to bolster their threat intelligence capabilities can leverage FileVantage's integration with threat intelligence feeds to enhance their security posture further.
Pros:
- Comprehensive Activity Logging: Records all file activities, providing detailed visibility into changes and user interactions.
- Tailored Monitoring: Can be customized to monitor specific files and criteria, reducing noise and focusing on relevant events.
- Threat Intelligence Integration: Enhances monitoring with threat intelligence feeds, aiding in the detection of malicious activities.
- Cloud-Based Accessibility: Accessible from any standard web browser, offering flexibility and ease of management.
- Scalable Solution: Suitable for businesses of all sizes, from small organizations to large enterprises, ensuring scalability and adaptability.
Cons:
- Lack of Sensitive Data Classification: Does not include sensitive data classification capabilities, potentially limiting visibility into data security risks.
The FileVantage package is useful for compliance with PCI DSS, CIS, and SOX. The system doesn’t include risk assessment or sensitive data discovery. So, you will need to buy an additional tool to classify data that needs to be protected. You can start with a 15-day free trial.
5. SolarWinds Security Event Manager
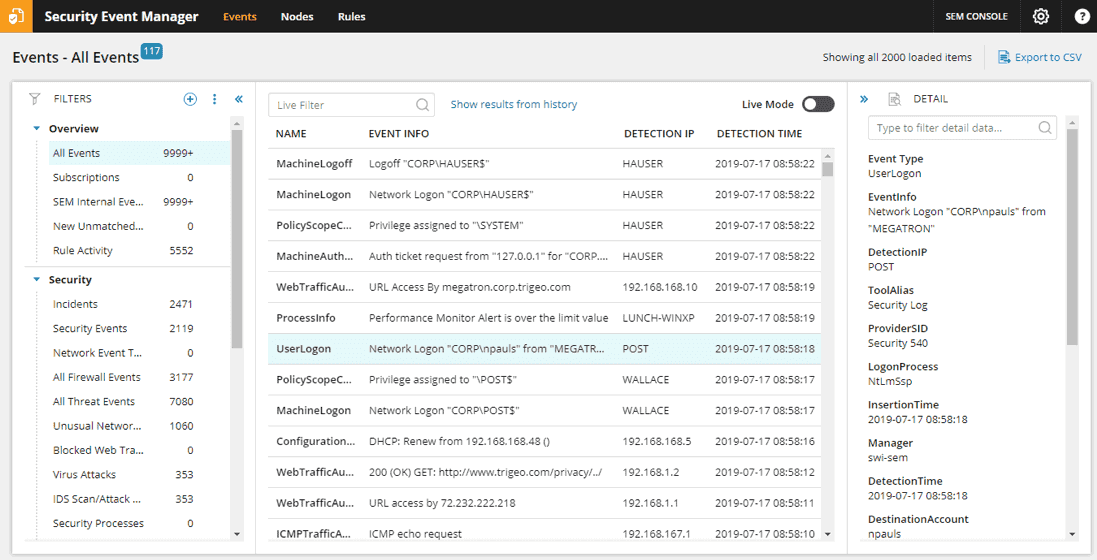
SolarWinds Security Event Manager (SEM) is a SIEM tool that leverages file integrity monitoring as a core feature to help secure data. SEM does much more than just file integrity monitoring, making it a more powerful tool to help keep your files safe. FIM tools act as an early warning system that something is wrong; this tool takes that a step further by monitoring both the integrity of your files, along with the syslogs of every server and network device on the network.
Key Features
- File Integrity Monitoring (FIM): Offers comprehensive monitoring of file integrity, bolstering network security measures.
- Centralized Dashboard: Provides a single interface for monitoring events across the network, ensuring scalability and ease of use.
- Automated Incident Response: Empowers administrators with customizable responses to security events, enhancing proactive threat mitigation.
- Compliance Checks: Facilitates quick compliance assessments and offers templates for detailed reporting, aiding adherence to regulatory standards such as PCI DSS, HIPAA, and SOX.
- Forensic-Level Auditing: Enables thorough auditing for legal purposes and in-depth investigations, enhancing overall security posture.
Why do we recommend it?
SolarWinds Security Event Manager (SEM) earns our recommendation due to its comprehensive approach to data security, with a strong emphasis on file integrity monitoring (FIM) alongside an array of supplementary features. Through rigorous testing, we have found SEM to be an indispensable tool for fortifying files and identifying potential network threats, providing peace of mind to organizations concerned about data integrity. By offering proactive monitoring of both file integrity and system logs, SEM empowers users to stay ahead of emerging security risks, contributing to a robust defense strategy. Additionally, SEM's intuitive interface and customizable features make it accessible to users of varying technical expertise, ensuring its suitability for diverse organizational needs.
A minor agent can be installed in every environment that you wish to monitor. That agent reads the security logs of that application or server and then forwards them to a centralized dashboard for review. This allows organizations to monitor both their files and unauthorized attempts at accessing the network, allowing you to be even more proactive in stopping attacks.
Events for all of these logs can be searched within a single dashboard, making it a scalable option no matter how extensive your network is. Events can be analyzed in real-time and historically, allowing you to keep track of security events for months or even years. One of the most potent parts of the solution is the ability for automatic remediation.
Automated incident response is at the heart of the system and gives sysadmins a wide range of options for responding to specific events. This works not just for file integrity monitoring but also unauthorized access, failed login attempts, and more. The platform does an excellent job of giving administrators the freedom to build their solutions while also providing a helpful library of templates that allows the product to be used out-of-box for immediate results.
SolarWinds Security Event Manager can monitor the integrity of files and other areas of the network, including servers, applications, and infrastructure. This flexibility, along with its easy-to-implement agents for data collection, secures its spot at number one on our list.
Who is it recommended for?
SEM is highly recommended for businesses and enterprises seeking sophisticated yet accessible solutions to bolster their data security posture. Small businesses, as well as large enterprises, can benefit from SEM's scalable options and automated incident response capabilities, tailoring its use to suit their specific requirements. Whether safeguarding sensitive data, ensuring compliance with industry regulations, or mitigating potential threats, SEM offers a versatile solution adaptable to various organizational contexts. Furthermore, SEM's extensive documentation and support resources make it particularly suitable for organizations with limited cybersecurity expertise, facilitating seamless implementation and ongoing management.
Pros:
- Comprehensive Security: Integrates file integrity monitoring with log monitoring for a holistic approach to network security.
- Configurable Automated Remediation: Offers highly customizable response options with detailed documentation and templates.
- Compliance Support: Facilitates compliance checks and detailed reporting for regulatory standards like PCI DSS, HIPAA, and SOX.
- File Restoration and Tracking: Automatically restores files and tracks changes over time, enhancing data recovery capabilities.
- Forensic-Level Auditing: Provides extensive auditing capabilities for legal cases and investigations, ensuring thorough security measures.
Cons:
- Learning Curve: SEM's advanced features may require time to fully explore and utilize effectively.
You can test out SolarWinds Security Event Manager completely free for yourself through a 30-day free trial.
6. OSSEC
OSSEC is a free and open-source Host-based Intrusion Detection (HIDS) tool with a dedicated community of users who continuously provide configuration settings, scanning templates, and bug fixes to the platform. File integrity monitoring is a core feature of OSSEC, making it a solution for FIM.
Key Features
- Free and Open-Source: Cost-effective solution with a dedicated community providing continuous support and contributions.
- Comprehensive File Integrity Monitoring: Core feature offering detection of unauthorized changes to critical files and directories.
- Cross-Platform Compatibility: Supports a wide range of operating systems, including Linux, Windows, Unix, and Mac, ensuring versatility and compatibility.
- Customizable Interface: Offers an easy-to-customize and highly visual interface, enhancing user experience and flexibility.
- Community-Built Templates: Access to a library of community-built templates for quick deployment and configuration.
Why do we recommend it?
OSSEC earns our recommendation as a robust and versatile Host-based Intrusion Detection (HIDS) tool with comprehensive file integrity monitoring capabilities. Being free and open-source, OSSEC boasts a dedicated community continuously contributing to its improvement, ensuring access to configuration settings, scanning templates, and bug fixes. With file integrity monitoring (FIM) as a core feature, OSSEC offers a cost-effective solution for detecting unauthorized changes to critical files and directories. Our recommendation is rooted in the platform's reliability, flexibility, and active community support, making it a valuable asset for enhancing security posture.
The platform collects log data, and file integrity metrics from the network in real-time and analyzes that data for any attacks or attempted attacks. The file integrity monitoring feature in this tool is called Syscheck, and it's just a tiny part of what the entire platform is capable of monitoring.
The FIM features scans on a cycle, checking for changes every six hours by default. This is done intentionally to limit the size of the logs generated and reduce the number of system resources consistently being used. While there is a tradeoff between real-time monitoring and this delay, sysadmins can customize this option to monitor more sensitive files in a short time.
Who is it recommended for?
OSSEC is recommended for organizations seeking a free and open-source solution for host-based intrusion detection and file integrity monitoring. Suitable for a wide range of operating systems, including Linux, Windows, Unix, and Mac, OSSEC offers versatility and compatibility for diverse environments. IT administrators, security professionals, and system administrators can benefit from OSSEC's combination of SIEM and HIDS capabilities, providing comprehensive security monitoring and threat detection. Additionally, organizations looking for a customizable and visually intuitive interface, coupled with community-built templates for quick deployment, will find OSSEC to be a valuable addition to their security toolkit.
Pros:
- Cross-Platform Compatibility: Supports a wide range of operating systems, ensuring versatility and compatibility across diverse environments.
- Combination of SIEM and HIDS: Functions as a comprehensive solution for security monitoring and threat detection.
- Customizable Interface: Provides an easy-to-customize and visually intuitive interface, enhancing user experience and flexibility.
- Community Support: Access to a dedicated community providing continuous support, configuration settings, and bug fixes.
- Quick Deployment: Community-built templates allow for quick deployment and configuration, speeding up implementation.
Cons:
- Additional Tool Requirements: Requires secondary tools like Graylog and Kibana for further analysis, adding complexity to the setup.
- Lack of Paid Support: The open-source version lacks paid support options, potentially limiting access to dedicated support resources.
OSSEC can be run on Windows, Linux, Mac, and Unix.
7. Netwrix Auditor
Netwrix Auditor was designed to monitor files and help sysadmin maintain compliance on their networks through a series of reports, audits, and tools. The platform can monitor and report changes to files, with countermeasures including new files created, permission changes, modifications, and deletions.
Key Features
- File Monitoring and Reporting: Tracks changes to files, permissions, modifications, and deletions, providing detailed auditing and reporting capabilities.
- Compliance Management: Helps organizations maintain regulatory compliance by offering a detailed log of file changes and access attempts.
- Selective File Monitoring: Allows customization to monitor specific files or directories, safeguarding sensitive files and conserving system resources.
- Automated Remediation: Enables sysadmins to implement automated remediation via scripts, enhancing operational efficiency and threat response.
- Integration Capabilities: Integrates with popular help desk platforms for automatic ticket creation and support for hardware and device monitoring.
Why do we recommend it?
Netwrix Auditor earns our recommendation for its robust file monitoring capabilities tailored to help sysadmins maintain compliance and bolster network security. Designed to provide detailed auditing and reporting, Netwrix Auditor assists organizations in maintaining the chain of custody for sensitive files, ensuring regulatory compliance. With the ability to monitor and report changes to files, including permissions, modifications, and deletions, Netwrix Auditor offers valuable insights into file activity to mitigate security risks effectively. Our recommendation is based on the platform's reliability, comprehensive auditing features, and integration capabilities, making it a valuable asset for organizations prioritizing compliance and security.
The tool cannot restore files in real-time, but it can help organizations demonstrate compliance by offering a detailed log of file changes and access attempts. Rather than monitoring all the files on a network, Netwrix Auditor can detect sensitive files or be told exactly what to watch. This helps safeguard your most sensitive files while also protecting system resources.
Who is it recommended for?
Netwrix Auditor is recommended for organizations seeking a comprehensive solution to monitor and maintain compliance on their networks. Ideal for sysadmins and IT teams, Netwrix Auditor offers detailed auditing and reporting tools to track file changes and access attempts, ensuring regulatory adherence. Additionally, organizations concerned about protecting sensitive files and system resources can benefit from Netwrix Auditor's ability to detect and monitor specific files or directories. With integration options for popular help desk platforms and support for hardware and device monitoring, Netwrix Auditor is suitable for organizations looking to streamline compliance management and enhance network security.
Pros:
- Detailed Auditing and Reporting: Provides detailed auditing and reporting tools to maintain the chain of custody for sensitive files.
- Hardware and Device Monitoring: Offers monitoring capabilities for hardware and devices to track device health alongside security.
- Automated Remediation: Allows sysadmins to implement automated remediation via scripts, enhancing operational efficiency.
- Integration Capabilities: Integrates with popular help desk platforms for automatic ticket creation and seamless workflow management.
Cons:
- Short Trial Period: The trial period could be extended to allow for thorough testing and evaluation.
- Issues with Cisco Devices: May encounter difficulties in supporting Cisco network devices, potentially limiting compatibility.
- Alerting Complexity: Alerting could be made more intuitive to improve usability and effectiveness.
The auditing functionality can help assist administrators in internal audits of permissions by displaying a simple side-by-side look at permissions and offering a more visual look into file access rights and permissions. Netwrix Auditor is available for free through a 20-day trial.
Which file integrity monitoring tool is best for you?
We’ve listed our top five picks for best integrity monitoring tools, but which one is best for you?
In almost all cases, ManageEngine ADAudit will be the best choice for both medium and large-size networks that need a customizable FIM tool that will help demonstrate compliance, as well as offering automatic remediation. The tool can automatically restore files and provide an audit trail of changes, making it both a proactive and reactive solution to file security.
Datadog offers an excellent cloud-based solution that doesn’t require any server hardware or compliance onboarding procedure for businesses that want file integrity monitoring but don’t have the infrastructure or in-house IT staff.
Lastly, for small businesses that can’t budget for an enterprise FIM tool, OSSEC offers a free and open-source HIDS/FIM tool that can be used to monitor file access and proactively identify network intrusion attempts. Just make sure you have a strong team of talented technicians to configure and manage the tool.
Do you have a favorite file integrity monitoring tool? Tell us about it in the comments below.