We may earn a commission if you make a purchase through the links on our website.
The Best Phishing Protection Tools for 2025

UPDATED: July 15, 2024
Protect your users from fraudulent email activity with these phishing protection tools
Integrating phishing protection tools into your environment is one of the most reliable and comprehensively secure ways to protect your email infrastructure. Phishing protection tools then use a range of mechanisms to keep your end users safe from phishing-related fraud. The most basic service they give is simply checking your inbound and outbound emails for dangerous content like predatory URLs or malware files. These technologies often interface with your system via a pre-defined setup for platforms like Office 365 or Google Workspace, or via an API with various integration options for your bespoke email system.
Other features could include phishing simulations, which send simulated phishing scams to your end users to assess their grasp of email security, which is a useful tool for educating your users about the risks associated with email communication.
Here is our list of the best phishing protection tools:
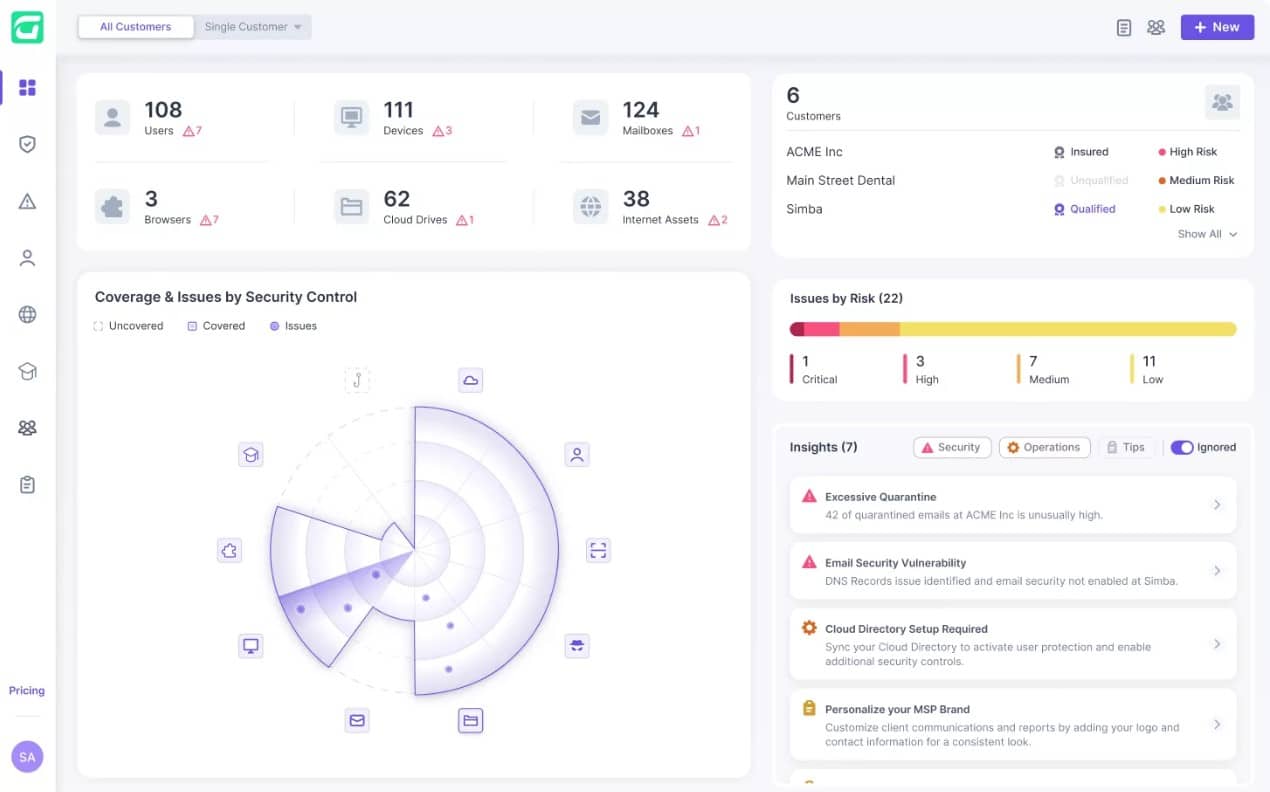
- Guardz – EDITOR’S CHOICE This cloud platform of security systems provides phishing protection and also blocks spam, malware, and impersonation scams. The package also includes a phishing simulator and user awareness training. Get a 14-day free trial.
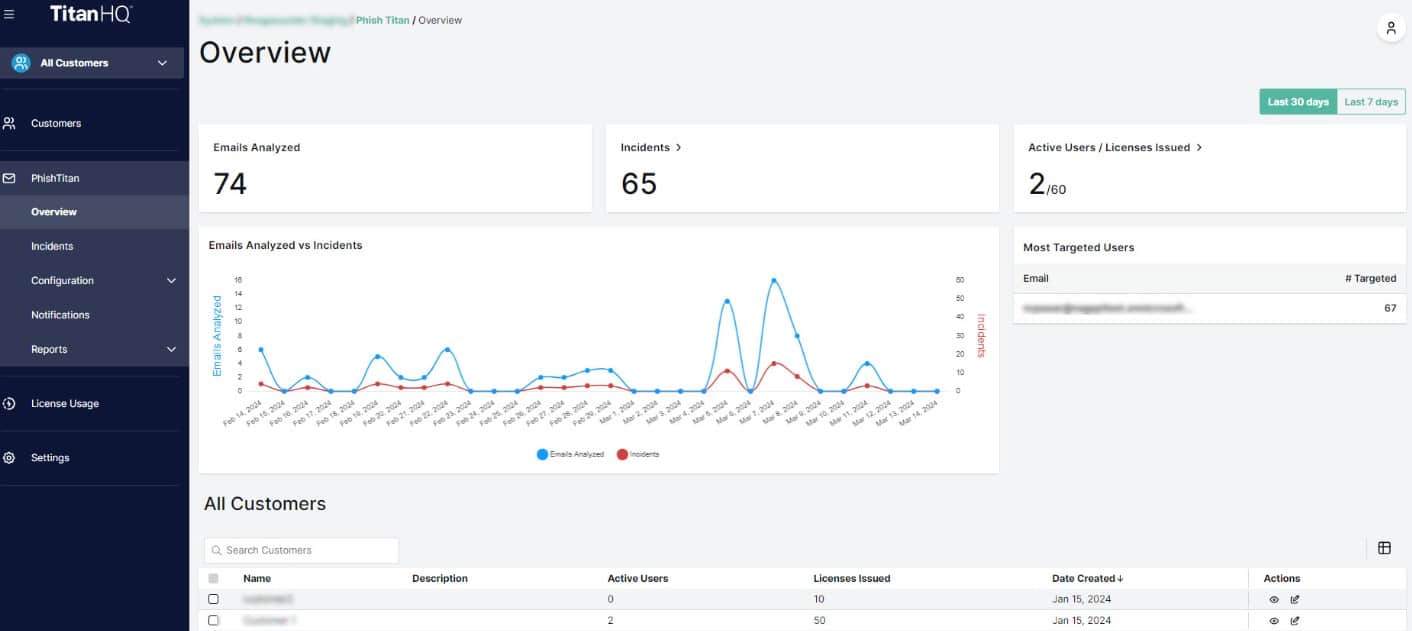
- TitanHQ PhishTitan – GET DEMO This protection system for emails in Microsoft 365’s online Exchange Server and Outlook services scans inbound emails for phishing threats and examines outbound emails as part of a data loss prevention strategy. Access the free demo.
- Avanan With its vast defense capabilities, the Avanan Cloud Security Platform is one of the most comprehensive cloud-based email security solutions on the market, ensuring the safety and compliance of your network's whole email infrastructure. The solution includes three distinct techniques for directly handling malware and anti-phishing attacks within the platform.
- Abnormal Security Abnormal may recognize instances in which a vendor has a high risk of fraud, indicating when an email should be thoroughly checked for signs of malicious behavior. Abnormal looks for deviations from the standard by analyzing massive amounts of data and building profiles of accepted behavior in your area.
- Trustifi Detects viruses that spread malware and ransomware, protects your email traffic from BEC attacks and switches authorized technicians using a great notification system. The system includes whitelisting and blacklisting options to boost overall security.
- Barracuda Sentinel The firm employs a ground-breaking API-based design that enables its AI engine to review previous emails and learn about customers' distinct communication habits. In the multi-layered email security system Barracuda Total Email Protection, Sentinel provides AI-based defense against spear phishing, account takeover, and hacked corporate emails.
- Proofpoint Essentials Delivers full protection against email-borne threats with a multi-layered anti-virus, anti-spam, and phishing detection engine. The system provides you with a sophisticated system interface to help you comprehend the entire hazard picture.
- BrandShield Offers a variety of specialized security solutions aimed at protecting the identities of your organization and its employees, one of which is its robust phishing protection solution.
A substantial amount of phishing protection tools marketed towards larger businesses cover a wider scope of features including email encryption technology. Email encryption systems secure your email data behind walls of protection to ensure only your intended destination receives the critical information held within email communications. Also, brand fraud detection systems that scan the internet to determine if your data has been compromised often go hand-in-hand with phishing protection tools. It is feasible that if your public data gets into the wrong hands, they may try to use your business identity against your own employees or customers to steal data and money.
More advanced modern systems employ machine learning and AI-driven systems to improve the security posture and usability of the product. They employ these systems to scan the activity of your users and monitor behavioral patterns—they can then compare this historical data to current behavioral patterns and quickly identify when an account is acting suspiciously.
The ultimate deciding factor in your chosen phishing protection tool is likely going to be the comparison of these extra peripheral features. All of the solutions on this list provide excellent phishing protection, but they all also provide a variety of different extra functions. Make sure you look through the article and check out which extra features sound useful to your business security.
The Best Phishing Protection Tools
1. Guardz – FREE TRIAL
Guardz is a system-wide security monitoring service that is delivered from the cloud. The package protects endpoints and data held on cloud platforms with email scanning as one of its main defense mechanisms. The email protection system detects phishing attempts. It also identifies theft attempts that use impersonation, spam, and malware. This system is offered on a subscription.
Key Features:
- Blocks malicious emails
- Moves emails to quarantine
- Option to restore
- Delivered from the cloud
- For Outlook and Gmail
The cloud-based scanner integrates into Microsoft Exchange Server/Outlook or Google Gmail through a plug-in. The system will move a malicious email to a quarantine area and post an alert in the management console. Technicians have the option to review a blocked email and restore it to the intended recipient’s mailbox if they have been flagged in error.
The Guardz package also includes a phishing simulator that helps to test the email filter. The simulator could also be used to educate users, but in that case, the security monitoring filter would have to be turned off. There is an extensive library of employee awareness training courses in the Guardz platform. An administrator can allocate a course to an individual or a group of users. The dashboard then tracks progress through the course and registers completion.
Guardz stresses that its system needs to be administered by a managed service provider (MSP). Companies that don’t have an agreement with an MSP in place can select one from the Guardz list of recommended suppliers. The top plan of Guardz is a managed security service.
The lower two plans of Guardz are subscription editions with a rate per user. There is no minimum team size for a plan, so the package will cater to even the smallest business. You can investigate Guardz further with a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for a phishing protection tool because it provides full protection for an IT system against email-based attacks. As well as blocking phishing emails, this tool will filter out spam and identify theft attempts that involve manager impersonation. The tool also scans attachments for malware. Responses are automatic and involve moving suspicious emails to quarantine – they are not deleted and so can be restored. The plan is available for all sizes of businesses but it must be run by a managed service provider. The Guardz package includes a Dark Web scanner that alerts if company email accounts or up for sale on hacker forums. It also provides a phishing simulator and employee security awareness training.
Download: Get 14-day FREE Trial
Official Site: https://guardz.com/free_trial
OS: Cloud-based
2. TitanHQ PhishTitan – GET DEMO
PhishTitan, from TitanHQ, protects emails and data in Microsoft 365. As well as scanning inbound emails to detect impersonators, BEC, credentials theft attempts, and malicious links, the tool scans outbound emails as part of a data loss prevention system. This is a cloud-based system and it acts as a proxy, acting as the delivery point for all of your emails and forwarding validated mails to your Exchange Server.
Key Features:
- Designed for use with Microsoft 365
- A proxy service that stands between the world and your Exchange Server instance
- Detects BEC, phishing, and whaling
- Scans contents, looks for spoofing, and examines embedded links
The phishing detection service was originally part of the functions of SpamTitan, which now specializes in detecting and blocking spam and malware. The separation of phishing protection into a separate module gives buyers options. It is still possible to get the full range of email protection by signing up to both SpamTitan and PhishTitan. Other email security services on the TitanHQ platform include ArchTitan for email archiving and EncryptTitan, which offers an encryption service for emails.
The PhishTitan service intercepts emails on their way to Exchange Server. SpamTitan does that too and in the description of that service, TitanHQ explains how to apply the protection to Gmail. There is no mention of the use of PhishTitan to protect Gmail or block data theft from Google Workspace. TitanHQ explicitly links the use of PhishTitan to Microsoft 365.
The TitanHQ system uses AI methods for both its SpamTitan and PhishTitan systems. The platform deploys machine learning, which adjusts its detection rules over time. This enables the TitanHQ products to tailor their service to a specific company without needing to write custom code.
The PhishTitan service looks at the technical features of an email, such as the domain shown in the header and the IP address that the mail was sent for. It also scans for URLs and checks that they are valid. Content scanning looks for common credentials theft wording and verifies the originator of the email in order to confound business email compromise through impersonation. Gain access to a free demo.
3. Avanan
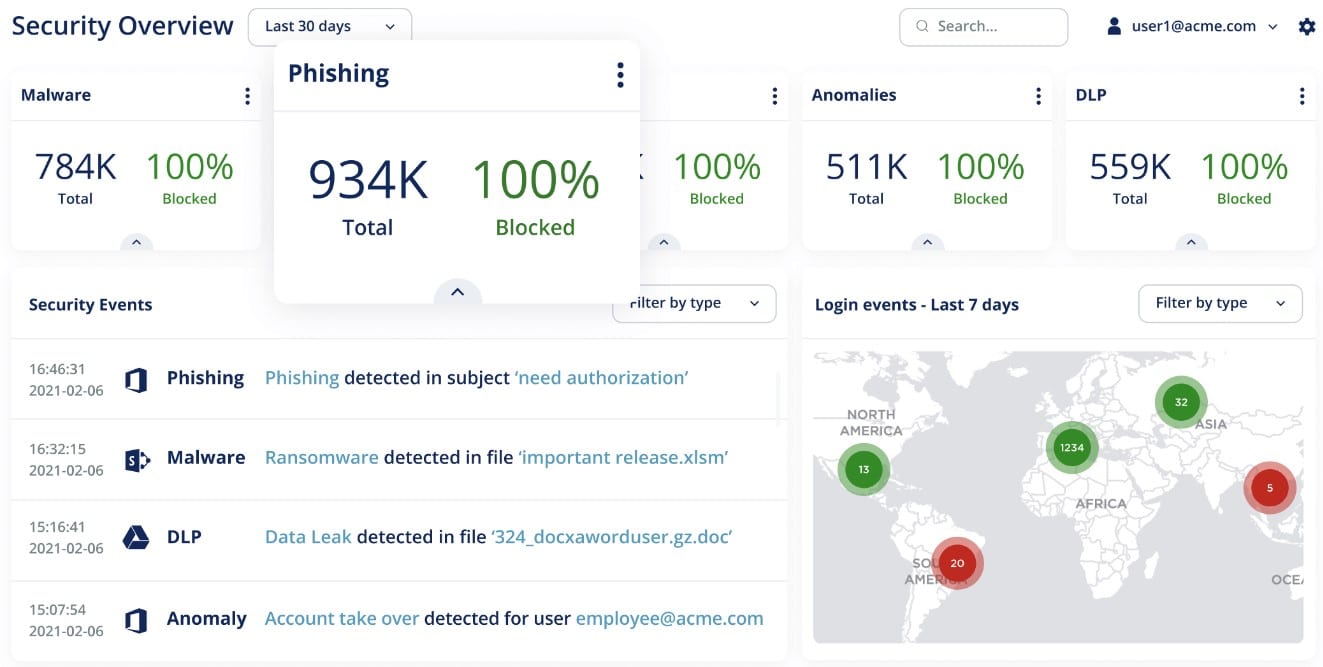
The Avanan Cloud Security Platform, with its extensive defense capabilities, offers one of the most comprehensive cloud-based email security solutions on the market, assuring the safety and compliance of your network's whole email infrastructure. The solution provides three unique procedures for managing malware and anti-phishing attacks directly within the platform. After an email is given to the user, the ‘Detect and Prevent' system checks it and corrects any problems before the transmission is complete. This technology makes certain that your end users are never exposed to potentially harmful attacks.
Key Features:
- Security workflows
- Detect and Prevent system
- Quarantine Mailbox
- In-depth alerting
- Distinct user policies
Unlike a variety of other solutions, which exclusively secure incoming email, Avanan protects email in both directions (internal, external, outgoing), which provides total defense against all threats, including insider threats. Machine learning is used by the engine to create a profile based on past data such as login locations, data-transfer behavior, and email message partners. Search and Destroy enables security teams to swiftly identify the threat in a phishing attack that may have resulted in a breach. Admins can remove those emails from users' inboxes with a simple click, and email Recheck verifies harmful emails twice to ensure accuracy.
Deploy a cutting-edge security stack via the detect and protect mode, which provides an automatic policy action to quarantine malware, phishing attacks, and so on. You can set up a special quarantine mailbox to hold any emails or attachments that are quarantined during the scanning process due to policy or human activities.
Avanan offers a 14-day free trial of their services, during which you may test out features like configurable security workflows and fast deployment. The entire solution is divided into three distinct SaaS models, each with its own set of features and pricing. The basic Guard package includes all the basic capabilities and costs $4.30 per user per month; the Advanced Protect package includes file sandboxing to protect against zero-day malware attacks and costs $5.50 per user per month. Finally, the Complete Protection plan includes encryption and data loss prevention, which may be required for certain compliance needs; it costs $7.20 per user each month.
4. Abnormal Security
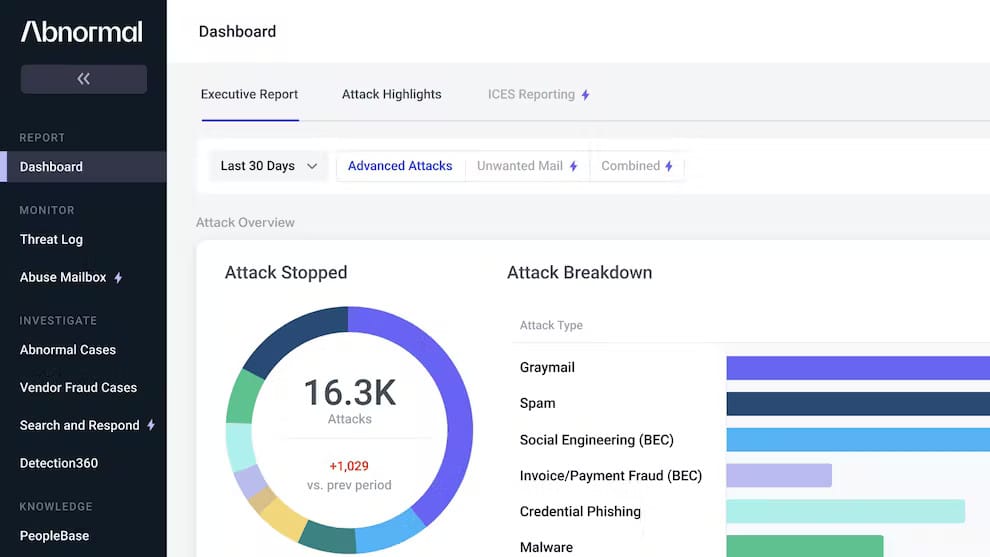
Abnormal may detect scenarios in which a vendor may provide a high risk of fraud, indicating when an email should be extensively examined for indicators of malicious behavior. Abnormal searches for departures from the usual by evaluating a large amount of data and creating profiles of recognized acceptable behavior in your area.
Key Features:
- Behavioral analysis
- Broad integrations
- API deployment
- Email automation
- In-depth reporting
The technology is meant to interface with Microsoft 365 and Google Workspace fast and without disrupting mail flow, by connecting natively with these spaces to build a behavioral profile of your people, business, and vendors. Tens of thousands of indicators across identity, behavior, and content are evaluated for anomalies and malicious conduct, including never-before-seen attacks with no traditional indicators of compromise. To assist analysts in responding to security incidents, Abnormal also integrates with incident response protocols and tools. It initiates playbooks, generates tickets, and transmits logs and information to SOAR, SIEM, and ITSM platforms.
Abnormal produces automatic profiles of your personnel after integration to create baselines, secure your organization, and get you up and running rapidly. The software instantly identifies all the vendors in your ecosystem, allowing you to assess their level of risk. The solution centralizes data, insights, actions, and the management of global block lists across hundreds of tenants in a single location for both Microsoft and Google environments. Abnormal behavioral analysis algorithms may also work for its users, and the program learns their preferences when they move emails between folders in their mailbox.
Abnormal is a SaaS platform designed for scalability and flexibility; the solution may also be integrated directly through Microsoft's Azure marketplace. While there is no free trial or publicly visible pricing, you may contact Abnormal directly to schedule a demo and receive a personalized rate based on your business's needs.
5. Trustifi
Trustifi identifies viruses that transmit malware and ransomware, protects your email traffic from BEC assaults, and changes authorized technicians via an excellent alerting system. To improve overall security, the system features whitelisting and blacklisting options. You can be confident in the security of your internal and external email traffic since it includes email encryption as well as full DLP with an extensive rules engine to meet every use case. The solution also offers secure mobile relays for whole device safety, as well as the ability to recall, block, change, and set custom expiration dates for emails.
Key Features:
- Malware and ransomware detection
- Email encryption
- White/blacklisting tools
- AI-driven safeguarding
- Compliance assurance
General features such as integrated spam filtering, spoofing, phishing, and fraud detection significantly increase network security. To protect your email from malicious links and attachments, the Inbound Shield combines specialized AI and multiple dynamic and comprehensive engines
Trustifi also contains several data-loss prevention measures, such as real-time email delivery, opening, and reading times, as well as tracking and certified delivery. You can implement system-wide two-factor authentication for all users or group-specific user groups to allocate security choices for improved system verification. HIPAA/HITECH, PII, GDPR, FSA, FINRA, LGPD, and CCPA compliance regulations are all met by the system.
Trustifi is meant to interface simply with Office 365 or Google Workspace, but it also contains a full integration API to support a wide range of email systems. To acquire a tailored price quote based on your specific business requirements, contact Trustifi directly. There is no trial version of the product available, however, you can request a demo of the platform to gain a better understanding of the system's inner workings.
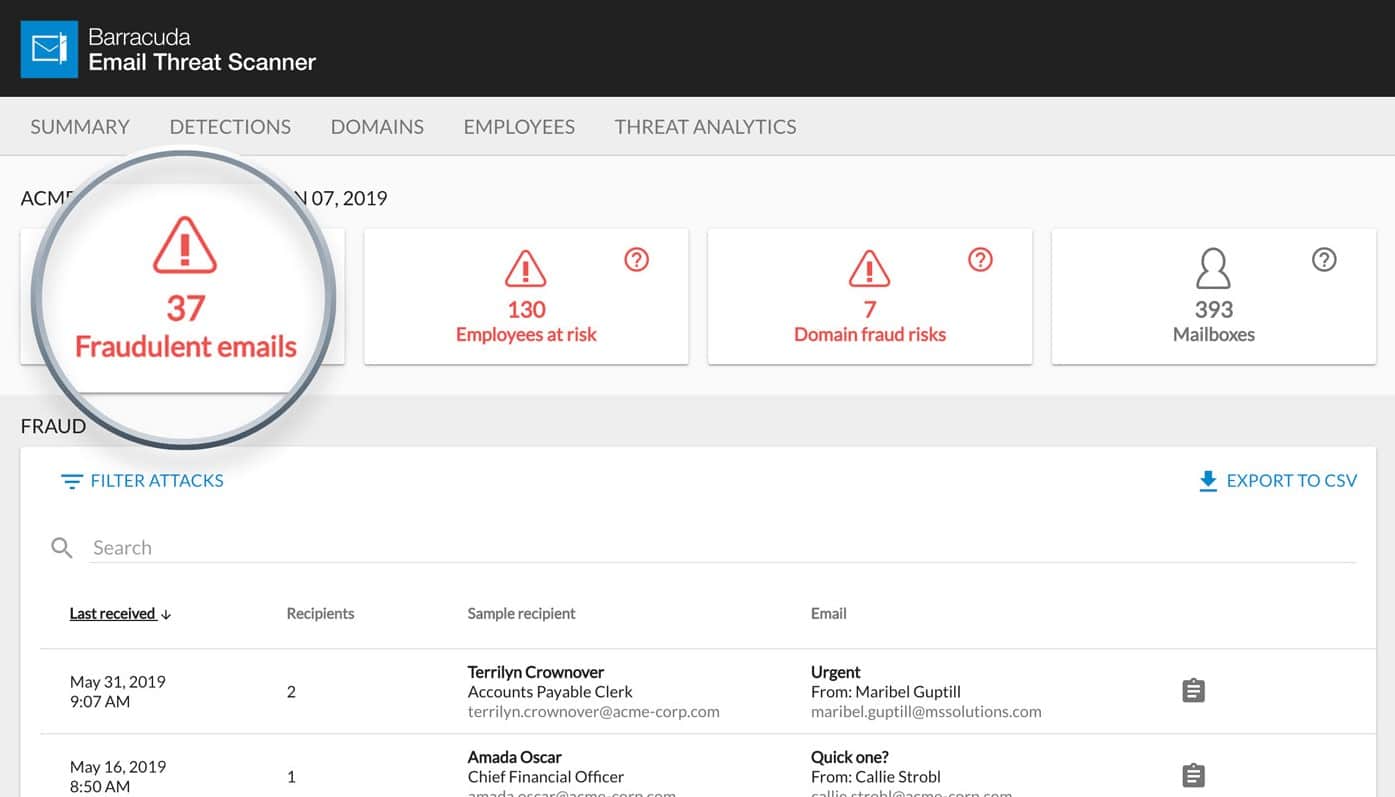
6. Barracuda Sentinel
The startup uses a revolutionary API-based design that allows its AI engine to examine past emails and learn about customers' unique communication habits. Sentinel provides AI-based defense against spear phishing, account takeover, and compromised corporate emails in the multi-layered email protection system Barracuda Total Email Protection.
Key Features:
- AI-Driven Behavior analysis
- Account Takeover Protection
- Domain Fraud Protection
- Detailed reporting
- API-based Architecture
Through DMARC (Domain-based Message Authentication Reporting and Conformance) reporting, analysis, and visibility, Barracuda Sentinel delivers total protection from email domain fraud. DMARC authentication is set up with the help of Barracuda Sentinel, which allows you to view and analyze reports at a detailed level to help you eliminate false positives, protect real emails, and prevent spoofing.
Furthermore, the system is meant to resist phishing efforts that gather login information to take over an account. After detecting abnormal email behavior and notifying IT, it detects and deletes all fraudulent emails sent from compromised accounts. It can then detect abnormalities in communication metadata and content to uncover and thwart socially engineered attacks in real-time.
Barracuda Sentinel is available for license purchase from a variety of associated shops. Each license costs roughly $3.99 per user per month, however, prices vary depending on where you get the licenses. The solution is intended to function alongside any email system, but it has been specifically created for Office 365 environments, and it will be readily integrated into your Microsoft email suite via pre-established plugins. Other email solutions can be accessed using the API.
7. Proofpoint Essentials
Proofpoint offers a multi-layered anti-virus, anti-spam, and phishing detection engine that provides comprehensive protection against email-borne threats. The system gives you an advanced system interface that aids in your understanding of the overall danger picture. You may also immediately get a full breakdown of specific threat types and attack frequency using the system, providing you with all the knowledge and resources you need to make sound security decisions.
Key Features:
- Fully integrated AI-driven solution
- URL and attachment scanning
- Targeted attack protection
- Malware quarantine
- Simulated phishing
Proofpoint Email Fraud Defense aids in the security of your email channel and the restoration of trust in corporate communications, which helps to prevent email fraud and protect your trusted domain by simplifying DMARC authentication. Additionally, Proofpoint Threat Response Auto-Pull (TRAP) allows messaging and security administrators to assess emails after delivery and shift malicious or undesirable emails to quarantine, by tracking forwarded mail and distribution lists and generating an auditable activity log.
The system combines targeted threat protection, as well as a superior email analysis solution, to help protect your employees. You can sandbox URLs and attachments with the help of this revolutionary technology. Every email is scanned by the system's strong AI-driven detection engines, and all known viruses are accurately and successfully identified and quarantined. Proofpoint offers dependable heuristics screening for enhanced defense, identifying unknown email threats and assisting in your instant protection from them.
Proofpoint offers a 30-day trial upon request, which begins with a meeting with one of their cybersecurity specialists and ends with the system being deployed to your infrastructure within 24 hours.
The email security package of the Essentials package is separated into four separate tiers, with the most basic Beginner plan costing $1.65 per user per month. More advanced tiers raise the price while adding exponentially more features to the offered package.
8. BrandShield
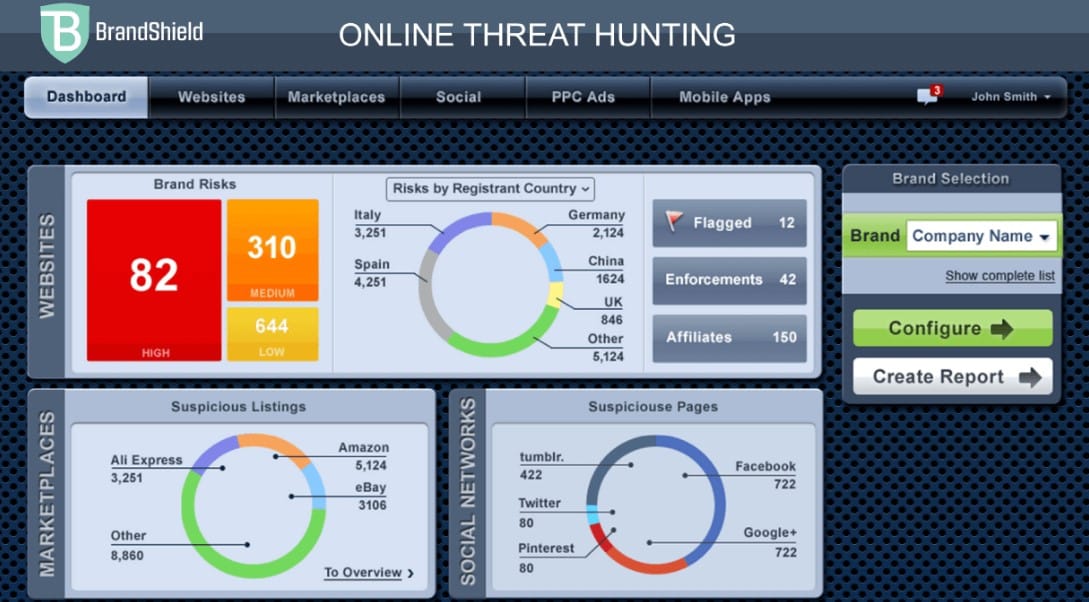
BrandShield includes various specialized security solutions aimed at protecting your company's and its employees' identities, one of which is its strong phishing protection solution. BrandShield provides a comprehensive digital threat map by monitoring the Internet, including social media, for phishing sites and pages, impersonation, and online fraud. You can also use the system's built-in threat dashboard to quickly discover and eradicate dangers to your organization.
Key Features:
- Advanced Anti-Phishing
- Identity theft protection
- Social Media protection
- Anti-Counterfeiting
- Brand Protection
The solution allows you to keep control by sending you regular updates on your enforcement operations and takedowns. The anti-phishing solution also includes new capabilities such as the website duplicate checker, automated takedown notifications, blacklists, and more. Modernized procedures, such as the ability to monitor prominent social networking sites for executive impersonation attempts and phishing scams that could expose members of your firm, are also included in the platform.
You may request a demo of the product directly from BrandShield, which also includes an online threat map of your present outward-facing brand identity. Requesting the demo is worthwhile even if you have no intention of purchasing the product. For a price on the entire product, you must contact the company directly for a personalized quote.