We may earn a commission if you make a purchase through the links on our website.
The Best SIEM Tools

UPDATED: March 28, 2025
SIEM stands for Security Information and Event Management. It is a blend of technologies that uses live data and log records to identify malicious activity. The purpose of SIEM is to provide a second line of defense against intrusion and insider threats. This technology is not intended to replace firewalls but it aims to catch activity that firewalls miss.
The SIEM philosophy combines two pre-existing security strategies. SIM and SEM. SIM is security Information Management and it focuses on scanning log files for indicators of suspicious activity. SEM stands for Security Event Managements and it works on live data, particularly network activity. SEM also encompasses incident response to shut down the access paths used by malicious actors.
Here is our list of the best SIEM tools:
- ManageEngine Log360 – EDITOR'S CHOICE An on-premises SIEM system that collects log data from network endpoints and cloud platforms. Runs on Windows Server.
- ManageEngine EventLog Analyzer – FREE TRIAL An on-premises SIEM system that includes log file protection. Available for Windows Server and Linux.
- Datadog Security Monitoring A cloud-based SIEM service that includes log management services and AI-based threat assessments. This service is able to integrate with other systems to coordinate system defense.
- Exabeam A next-gen SIEM that has integrated AI processes to identify normal patterns of behavior and deviations from that standard.
- Logpoint A cloud-based SIEM that includes log management, SOAR for orchestration, and UEBA for anomaly detection baselining.
- Heimdal Threat Hunting and Action Center This cloud service gathers data from on-premises Heimdal systems and searches for threats, sending back response instructions.
- Rapid7 InsightIDR A combination of specialist packages that build up into a NextGen SIEM with added SOAR for threat mitigation. This is a cloud-based service.
- SolarWinds Security Event Manager A highly-respected on-premises SIEM package that offers excellent analytical features as well as live protection. It installs on Windows Server.
- UnderDefense SIEM A managed SIEM service that is delivered from the cloud and includes the experts to watch over the tool and make decisions over protection strategies.
The SIEM industry is diverse and offers different solutions that cater to all types of businesses. Because there are many different requirements for SIEM configurations, we haven’t recommended one single SIEM package. Instead, we have identified the best options in a number of different categories. From this list, you will be able to narrow down your choice of SIEM, filtering out the platforms that don’t suit your preferences.
The difference between SIEM and IDS
The terminology of SIEM overlaps with that of Intrusion Detection Systems (IDSs). Intrusion detection systems aim to smoke out Advanced Persistent Threats (APTs). An APT is a situation where a hacker team gains access to a system and repeatedly revisits that system, exploring its facilities, using its resources, tampering with its records, and stealing its data.
When APTs were first discovered it was revealed that in many cases, hackers had been regular users of victimized systems for years. The purpose of these intrusions is not always to steal data. The resources of a network can be monetized by hackers. Servers can be appropriated to mine cryptocurrency and network gateways can be used as VPN proxies by hackers to front for intrusion into other networks.
APT hackers are able to adjust log file records to hide evidence of their presence or their use of resources. Highly organized and well-funded hacker teams behave like managed service providers, regularly logging in to the system and assigning around-the-clock systems administrator teams to watch over network services and ensuring that activities remain hidden.
IDS systems were created to combat APTs. There are two types of IDS. One is a Host-based Intrusion Detection System (HIDS). This looks through log files and also examines metadata about the log file to detect tampering. The other type of IDS is a Network-based Intrusion Detection System (NIDS). This scans through network traffic looking for unusual activity that doesn’t fit into the regular pattern of staff actions. The SIM part of SIEM is a HIDS and the SEM part of SIEM is a NIDS.
SIEM blends the two types of IDS into one package. This is because SIM has the benefit of spotting malicious activity by identifying a series of seemingly valid and unrelated actions that, as a chain of events, indicate an intrusion. This strategy catches threats that live monitors can’t spot. However, HIDS systems can take time to work. SEM systems operate on live data, so they can implement remediation immediately. However, there are many hacker strategies that are structured to avoid detection and so SIM doesn’t spot them.
By combining HIDS and NIDS, SIEM systems offer the best of both worlds. You can hope to catch intrusion as quickly as possible by all available methods. So, a SIEM system is the same as an IDS.
There is one more term that you need to know, which is IPS. With Intrusion Prevention Systems (IPS), prevention refers to threat remediation actions, such as blocking all connections from a specific IP address in the firewall and also interacting with Active Directory or other access rights management systems to suspend a user account.
These actions are not always implemented in SIEM systems. This type of remediation activity is called SOAR – Security Orchestration, Automation, and Response. This service interacts with other services on the network in order to shut down intrusion.
The Βest SIEM Τools
1. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a SIEM that installs on Windows Server and can gather log data from endpoints around the network from a series of endpoint agents. These are available for a list of operating systems, not just Windows. The tool will also take in logs sent by agents installed on cloud platforms, such as AWS and Azure.
Key Features:
- Threat Intelligence Feed: Integrates a threat intelligence feed, providing details on the latest hacker campaigns and enhancing threat detection capabilities.
- On-Premises for Windows Server: Designed to install on Windows Server, ManageEngine Log360 offers seamless integration with Windows environments, ensuring efficient log management and threat detection.
- Standardizes Log Formats: Standardizes Windows Events, Syslog, and software logs into a common format, facilitating uniform log management and analysis.
- Data Viewer with Manual Analysis Tools: Includes a data viewer with tools for manual log analysis, enabling security teams to identify and investigate suspicious activities effectively.
- Compliance Reporting: Offers compliance reporting for standards such as HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA, ensuring adherence to regulatory requirements and industry standards.
- Monitors Network Endpoints and Cloud Platforms: Monitors network endpoints and cloud platforms, providing comprehensive visibility into network activity and security events.
Why do we recommend it?
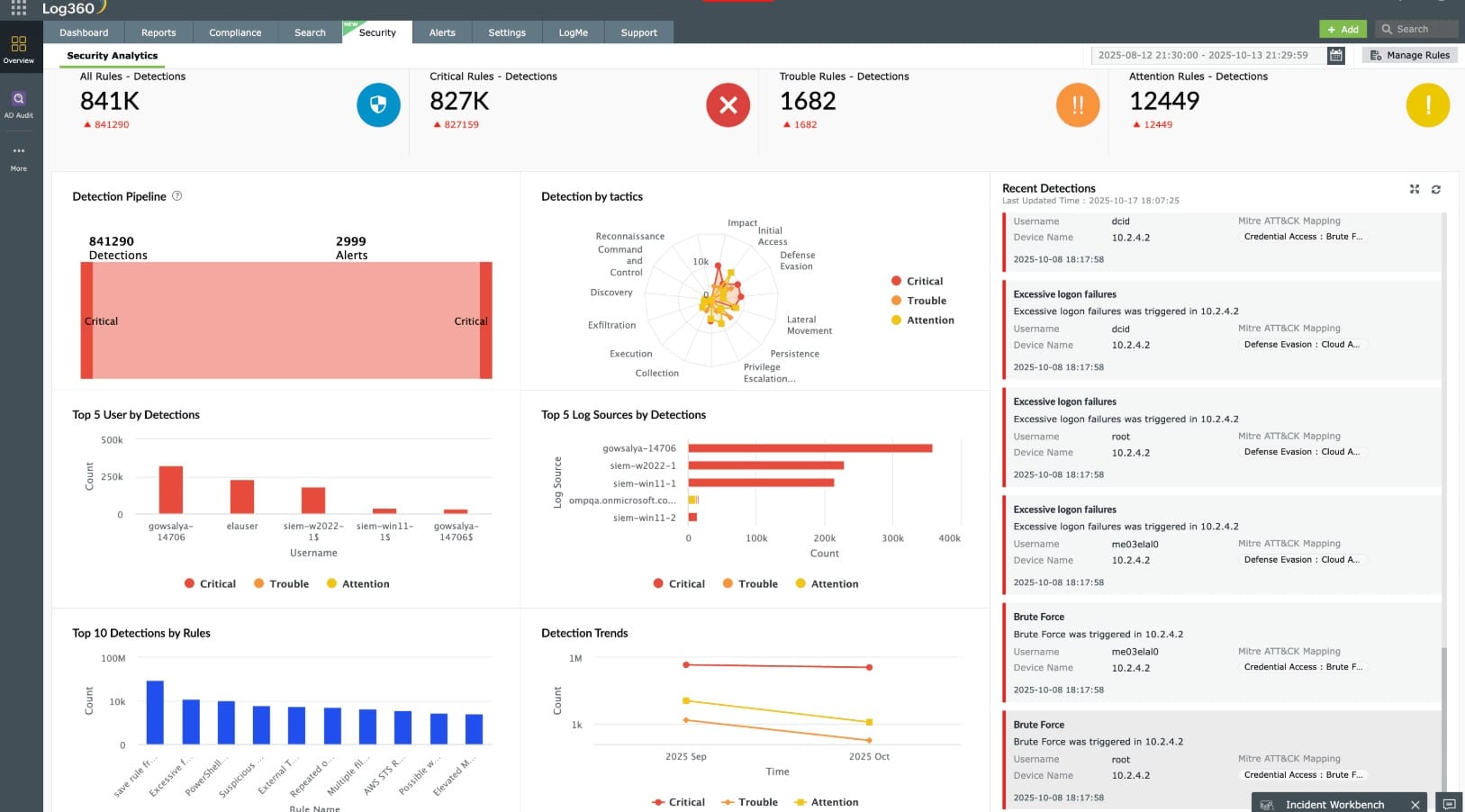
ManageEngine Log360 is highly recommended for organizations seeking a comprehensive SIEM solution with robust log management and threat detection capabilities. This solution, designed to install on Windows Server, offers seamless log data gathering from endpoints across the network, including various operating systems and cloud platforms. Our experience with ManageEngine Log360 has highlighted its effectiveness in threat intelligence feed integration, log standardization, and compliance reporting, ensuring proactive threat detection and regulatory compliance. With its user-friendly dashboard visualizations, robust searching capabilities, and cross-platform monitoring, ManageEngine Log360 provides invaluable support for security operations centers (SOCs), managed service providers (MSPs), and organizations of all sizes.
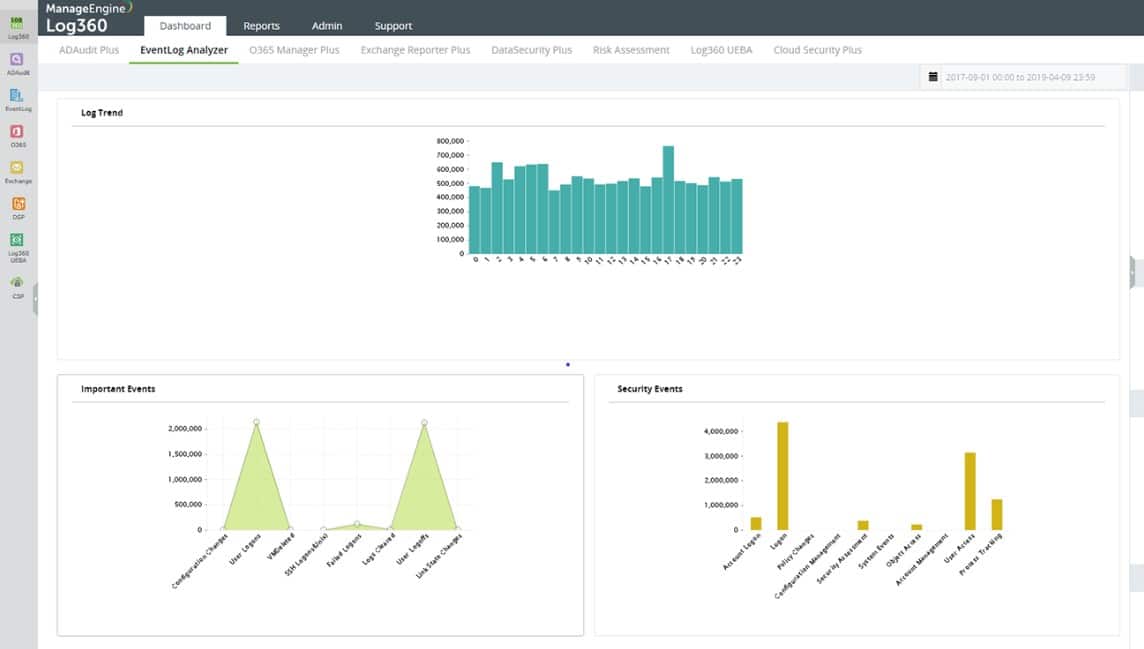
The SIEM is partnered by a log server that consolidates arriving logs messages into a standard format. This enables them to be stored together in files and also loaded into a data viewer. Arriving messages are displayed in the dashboard and files can also be opened and read in for analysis.
Threat hunting is performed on arriving records on a sliding window basis. The detection algorithm is enhanced by a threat intelligence feed, which provides details on the latest hacker campaigns. Notifications about suspicious activities are displayed in the dashboard and sent through service desk systems.
Who is it recommended for?
ManageEngine Log360 is recommended for organizations requiring a robust SIEM solution with comprehensive log management and threat detection capabilities. Ideal for security teams, network operations centers (NOCs), and managed service providers (MSPs), this solution offers seamless integration with Windows Server environments and supports endpoint agents across multiple operating systems and cloud platforms. Whether you're monitoring Windows, Linux, or Unix systems, ManageEngine Log360 provides the tools and capabilities necessary for live and historical event analysis, compliance reporting, and threat hunting. While it may require some time to explore and test out the suite of advanced services and features offered by ManageEngine, its intuitive interface and extensive documentation make it accessible and adaptable to various organizational needs and security requirements.
Pros:
- Creates a Private Corporate Threat Intelligence Platform: Enables organizations to proactively identify and respond to security threats.
- Blocks Lateral Movements by Malware and Intruders: Effectively blocks lateral movements by malware and intruders, minimizing the spread of infections and mitigating potential damage.
- Implements Data Loss Prevention: Safeguards sensitive information from unauthorized access and exfiltration.
- Flexible Package with On-Premises Elements: Seamless integration of on-premises elements and the cloud platform, ensuring comprehensive threat management and cybersecurity resilience.
- Options to Implement User Activity Tracking: Enables organizations to monitor and manage user interactions effectively.
Cons:
- Not a Standalone Product: Requires a minimum of three different Heimdal products to be installed for full activation, making it dependent on other Heimdal cybersecurity systems for functionality.
There are three editions of Log360: Free, Standard, and Professional. You need to get a quote for the Standard and Professional versions. Register for a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a SIEM tool because it offers a comprehensive, user-friendly solution for monitoring, analyzing, and responding to security threats across your network. With its extensive log management capabilities, Log360 can collect, store, and analyze logs from a wide range of devices and applications. It also provides real-time alerts and detailed reports, helping organizations quickly detect and respond to potential security incidents. The most important SIEM service in the Log360 package is its integrated threat intelligence capabilities, which allow for proactive identification of emerging threats and vulnerabilities. This helps prevent attacks before they can impact your organization. The tool also includes advanced search functionality, simplifying incident investigation and streamlining security auditing processes. Log360’s scalability makes it ideal for both small and large organizations, and its automated compliance reporting helps ensure adherence to regulatory standards like GDPR, HIPAA, and PCI DSS. This large package offers an attractive dashboard and powerful analytics, providing a holistic view of your network’s security posture.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/log-management/download.html
OS: Windows Server or SaaS
2. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer is a log manager and SIEM system. It offers automated intrusion detection plus utilities for manual security analysis. This is another on-premises option that can be installed on Windows Server or Linux. The EventLog Analyzer is the only option on our list for businesses that are all Linux and want to run a SIEM onsite.
Key Features:
- Collects Log Messages and Files: Collects log messages, manages a log file directory structure, and protects files against tampering, ensuring the integrity and security of log data.
- Auditing for Compliance: With standards such as PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001, ensuring adherence to regulatory requirements and data security.
- Gathers Logs from Various Sources: Gathers logs from Windows Events, Syslog, and application log messaging systems, providing comprehensive visibility into network activity and security events.
- Performs Live Anomaly Detection: Identifies abnormal behavior and potential security threats in real time, enabling prompt incident response.
- Generates Alerts and Notifications: Generates alerts when security events are detected, and forwards them as notifications via email or SMS, ensuring timely response to security incidents.
- Supports Manual Security Analysis: Provides utilities for manual security analysis, empowering security teams to investigate and respond to security incidents effectively.
Why do we recommend it?
ManageEngine EventLog Analyzer comes highly recommended for organizations seeking a robust log manager and SIEM system with comprehensive automated intrusion detection capabilities and utilities for manual security analysis. Whether installed on Windows Server or Linux, this on-premises option offers versatile log message collection, management, and protection against tampering. Our experience with ManageEngine EventLog Analyzer has demonstrated its effectiveness in auditing for compliance with standards such as PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001, ensuring regulatory compliance and data security. With its live anomaly detection, alert generation, and support for manual security analysis, ManageEngine EventLog Analyzer provides a holistic approach to threat detection and incident response.
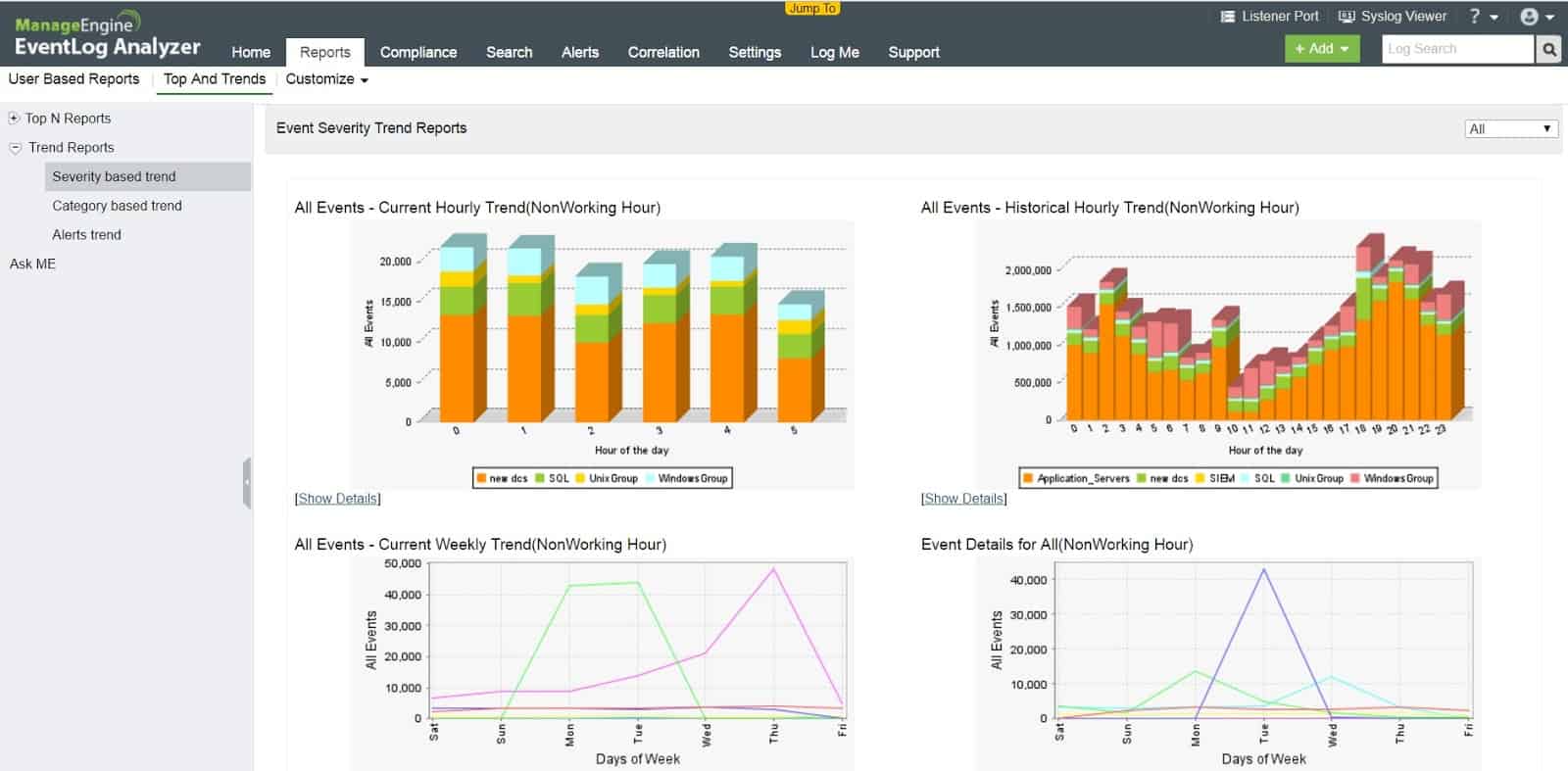
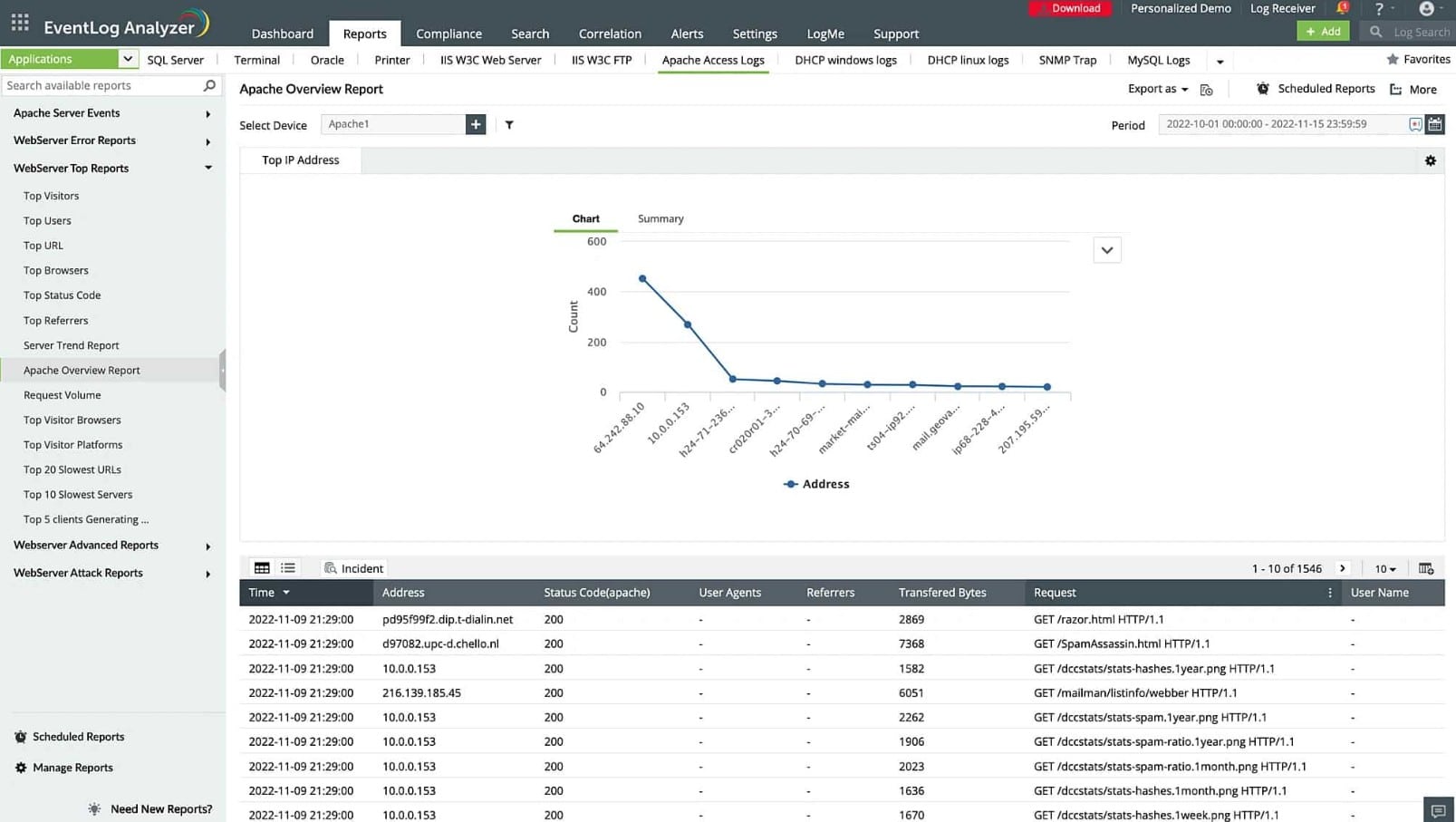
The EventLog Analyzer collects, consolidates, and files log messages from windows Events, Syslog, and a range of application log messaging systems. It isn’t restricted to just managing the log messages generated by its host. The system also protects log files against tampering. The EventLog Analyzer blends log file searches with live performance tracking to create both sides of the SIEM strategy.
Who is it recommended for?
ManageEngine EventLog Analyzer is recommended for organizations requiring a robust log manager and SIEM system with support for both Windows and Linux environments. Ideal for businesses seeking on-premises SIEM solutions, ManageEngine EventLog Analyzer offers comprehensive log message collection from a variety of sources, including Windows Events, Syslog, and application log messaging systems. Whether you're a small business or a large enterprise, this solution provides customizable dashboards, multiple alert channels, and forensic log audit features to meet the diverse needs of security teams and network operation centers (NOCs). While it may take time to fully explore all the features and tools on the platform, ManageEngine EventLog Analyzer offers extensive documentation and support resources to assist administrators and security professionals in maximizing the value of the solution.
Pros:
- Customizable Dashboards: Offers customizable dashboards that work great for network operation centers (NOCs), providing comprehensive visibility into security events and network activity.
- Multiple Alert Channels: Supports multiple alert channels, ensuring that security teams are notified across SMS, email, or app integration, enabling timely response to security incidents.
- Anomaly Detection: Uses anomaly detection to assist technicians in their day-to-day operations, enhancing proactive threat detection and incident response capabilities.
- File Integrity Monitoring: Supports file integrity monitoring, acting as an early warning system for ransomware, data theft, and permission access issues, enhancing overall data security.
- Forensic Log Audit: Includes forensic log audit features, enabling administrators to create reports for legal cases or investigations, ensuring compliance and accountability.
Cons:
- Time Consuming to Fully Explore All Features: Fully exploring and leveraging these capabilities may require time and effort for administrators and security professionals.
EventLog Analyzer is available in three editions:
- Free – manages up to five log sources
- Premium – for a single site, the price starts at $595
- Distributed – for multi-site implementations, price starts at $2,495
ManageEngine offers EventLog Analyzer on a 30-day free trial.
3. Datadog Security Monitoring
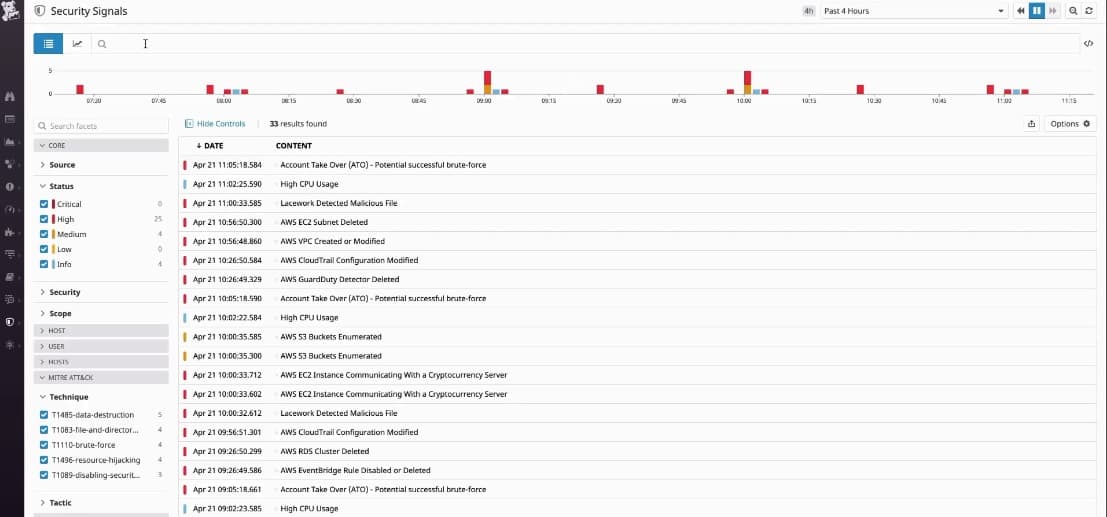
Datadog Security Monitoring is a SaaS system that can monitor networks anywhere. The service operates on log files and also collects live network traffic data, making it a SIEM system. The system looks for “signals” of malicious activity and lists all of these in the console as it detects them.
Key Features:
- SaaS System: Monitor networks from anywhere, providing organizations with flexibility and accessibility.
- Log File and Live Network Traffic Monitoring: Operates on log files and collects live network traffic data, enabling comprehensive threat detection and security monitoring.
- Threat Hunting Capabilities: Offers advanced threat hunting capabilities, powered by AI, to identify and mark signals of malicious activity and minimize false alarms.
- Comprehensive Overview Screen: Overview screen in the dashboard provides a comprehensive view of event data from across the IT system, facilitating quick insights and informed decision-making.
- Retention of Log Messages: Retains log messages for 15 months, making it suitable for standards compliance and security analysis.
- Scalable Pricing: Scalable pricing based on data processing volume, ensuring cost-effective security monitoring tailored to organizational needs.
Why do we recommend it?
Datadog Security Monitoring comes highly recommended for organizations seeking a robust SaaS SIEM system capable of monitoring networks from anywhere. This cloud-based service operates on log files and collects live network traffic data, enabling comprehensive threat detection and security monitoring. Our experience with Datadog Security Monitoring has highlighted its advanced threat hunting capabilities, powered by AI, which helps identify and mark signals of malicious activity while minimizing false alarms and alert fatigue. With its scalable pricing based on data processing volume and over 450 integrations to fit nearly any network environment, Datadog Security Monitoring provides organizations with a lightweight yet powerful solution for enhancing their security posture.
Fortunately, the Datadog service doesn’t just show those signals, it marks them within its threat hunting module and then looks out for further signs of intrusion. This means you can see evolving investigations but you don’t need to do anything about them until the Datadog system identifies a certain chain of events that amount to indications of compromise.
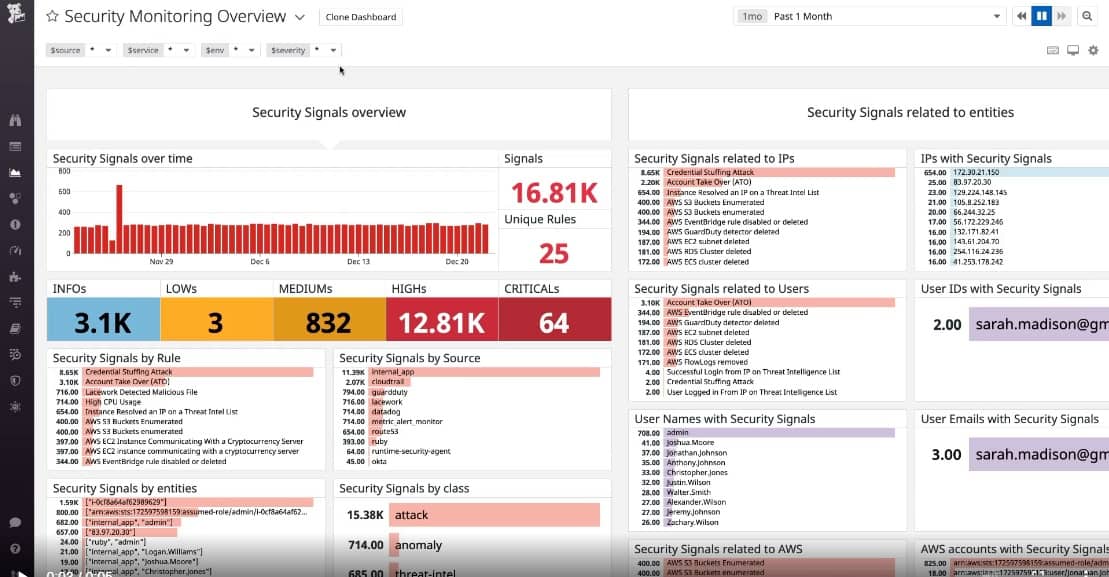
The overview screen in the dashboard for the Datadog Security Monitoring service shows you exactly how comprehensive this tool is, grabbing event data from all across your IT system. The service retains log messages for 15 months, which makes it a great service for standards compliance, that requires log data access for auditing. These logs are also available for security analysis.
Who is it recommended for?
Datadog Security Monitoring is recommended for organizations of all sizes and industries seeking a comprehensive SaaS SIEM system with advanced threat detection and security monitoring capabilities. Ideal for organizations with distributed IT environments, Datadog Security Monitoring offers the flexibility to monitor networks from anywhere and provides live reports for quick insights into high-level metrics. Whether you're a small business or an enterprise, Datadog Security Monitoring's scalable pricing model ensures cost-effective security monitoring tailored to your organization's needs. While the 14-day trial period may be considered short, the value provided by Datadog Security Monitoring's lightweight cloud-based tool and AI-powered alerts makes it a compelling choice for organizations prioritizing security and compliance.
Pros:
- Lightweight Cloud-Based Tool: Offers flexibility and accessibility for organizations seeking scalable security monitoring solutions.
- AI-Powered Alerts: Leverages AI-powered alerts to cut down on false alarms and alert fatigue, enhancing threat detection accuracy and efficiency.
- Live Reports: Provides live reports, making it easy to see high-level metrics and drill down quickly into security incidents for timely response.
- 450+ Integrations: With over 450 integrations, Datadog Security Monitoring fits nearly any network environment, ensuring compatibility and seamless integration with existing tools and systems.
- Scalable Pricing: Scalable pricing model based on data processing volume allows organizations to adjust their security monitoring costs according to their needs and budget.
Cons:
- Short Trial Period: The 14-day trial period may be considered short for organizations looking to fully evaluate the capabilities and effectiveness of Datadog Security Monitoring.
Datadog Security monitoring is offered on subscription, which effectively is a pre-paid service that gets you credits for the system. The charge rate is based on the volume of data ingested per month with a rate of 20 cents per Gigabyte of analyzed logs. There is also a metered pay-as-you-go service, which is charged at a rate of 30 cents per Gigabyte of data. Download a fully functional 14-day free trial.
4. Exabeam
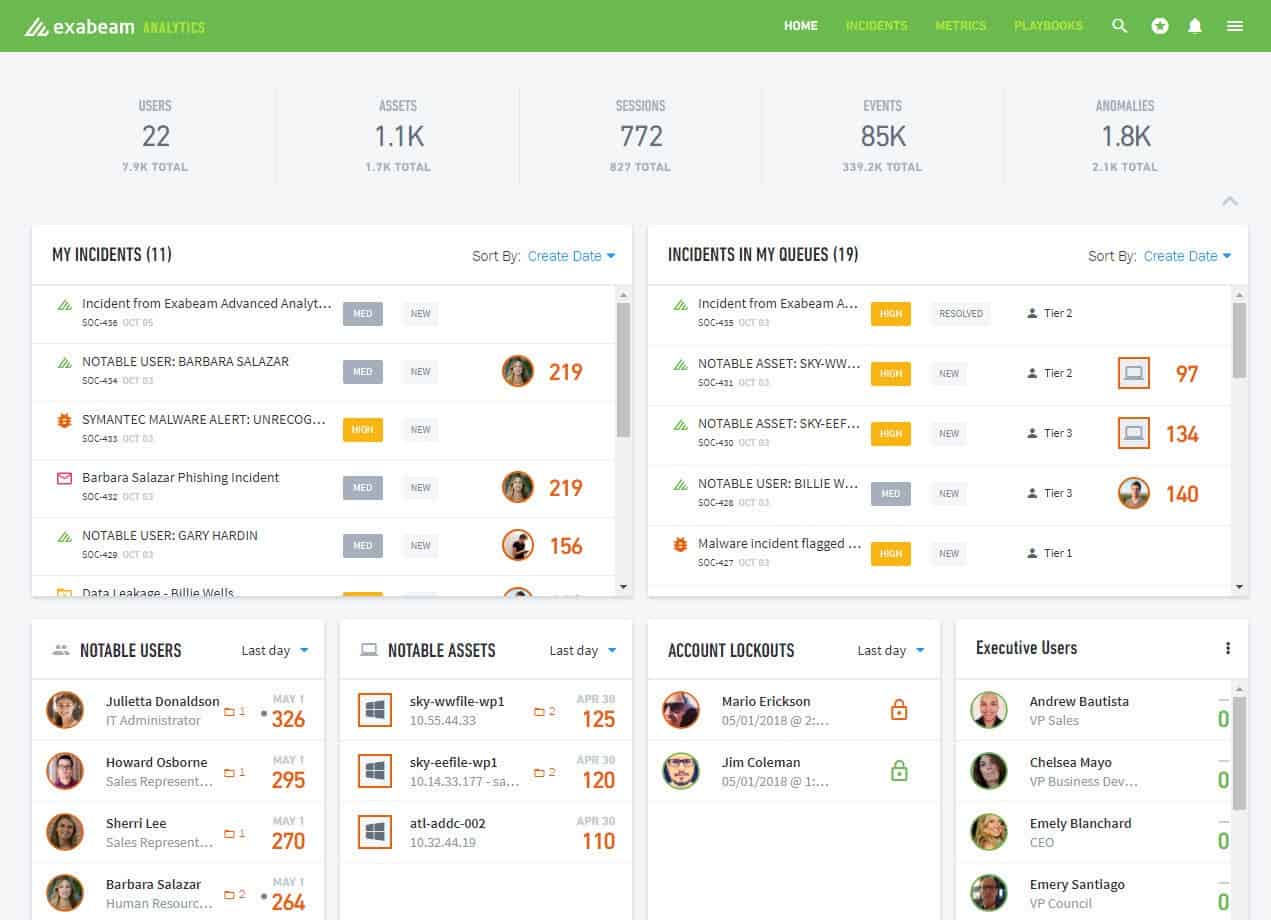
Exabeam is a NextGen SIEM service and includes threat hunting that deploys User and Entity Behavior Analytics (UEBA). This is an AI-based system that works out what is normal activity on your system and then identifies deviations from that standard, earmarking them for deeper investigation.
Key Features:
- Machine-Learning UEBA: Avoids false-positive reporting and identify deviations from normal activity for deeper investigation.
- SkyFormation Threat Intelligence Feed: Pulls its threat intelligence feed from more than 30 cloud platforms, providing immediate protection against emerging threats and zero-day attacks.
- High-Speed Threat Hunting: Performs high-speed threat hunting on its servers, enabling proactive threat detection and incident response.
- Secure Uploads for Log Messages: Offers secure uploads for log messages from your site to the Exabeam server, ensuring data integrity and confidentiality.
- Incident Responder SOAR Mechanism: Provides an Incident Responder SOAR mechanism for automated threat remediation, enabling organizations to automate response actions and mitigate threats effectively.
- Support for Manual Analysis: Empowers security teams to investigate and respond to security incidents effectively.
Why do we recommend it?
Exabeam is highly recommended for organizations seeking a NextGen SIEM service with advanced threat hunting capabilities and User and Entity Behavior Analytics (UEBA). This AI-based system leverages machine learning to identify deviations from normal activity and earmark them for deeper investigation, minimizing false-positive reporting. Our experience with Exabeam has highlighted its high-quality Cyber Threat Intelligence (CTI) feed, which provides immediate protection against emerging threats and zero-day attacks. With its Incident Responder SOAR mechanism for automated threat remediation and support for manual analysis of threat data, Exabeam offers a comprehensive solution for enhancing cybersecurity posture and threat detection capabilities.
The Exabeam service is notable for the very high quality of its Cyber Threat Intelligence feed (CTI). This is a notification of new attacks that are emerging around the world – once hackers develop a new strategy, they implement it with a series of attacks on many businesses. The Exabeam feed gives you immediate protection as soon as a new (zero-day) attack is experienced elsewhere.
Exabeam also offers a SOAR system that will interact with other security products on your site, such as firewalls, to automatically shut down attacks.
Who is it recommended for?
Exabeam is recommended for organizations of all sizes and industries seeking a NextGen SIEM service with advanced threat hunting and UEBA capabilities. Ideal for organizations prioritizing proactive threat detection and incident response, Exabeam offers support for incident response workflows, playbooks, and automation, enabling organizations to streamline their security operations and enhance their cybersecurity posture. Whether you're a small business or a large enterprise, Exabeam provides usefully query features for filtering large datasets and can be used for compliance reporting and internal audits for regulations such as HIPAA, PCI DSS, and more. While it may lack live network monitoring capabilities, the value provided by Exabeam's advanced threat detection and incident response capabilities makes it a compelling choice for organizations looking to strengthen their security defenses.
Pros:
- Supports Incident Response Workflows and Automation: Offers support for incident response workflows, playbooks, and automation, streamlining security operations and enhancing incident response effectiveness.
- Usefully Query Features: Provides useful query features for filtering large datasets, enabling organizations to extract actionable insights from their security data.
- Compliance Reporting and Internal Audits: Used for compliance reporting and internal audits for regulations such as HIPAA, PCI DSS, and more, ensuring regulatory compliance and data security.
Cons:
- Lacking Live Network Monitoring Capabilities: May lack live network monitoring capabilities, limiting real-time visibility into network activity and potential threats.
Exabeam doesn’t publish its prices. Instead, it enters into a conversation with potential customers that request a demo of the system. You don’t need to perform a download to access Exabeam. However, you can access a demo version online.
5. Logpoint
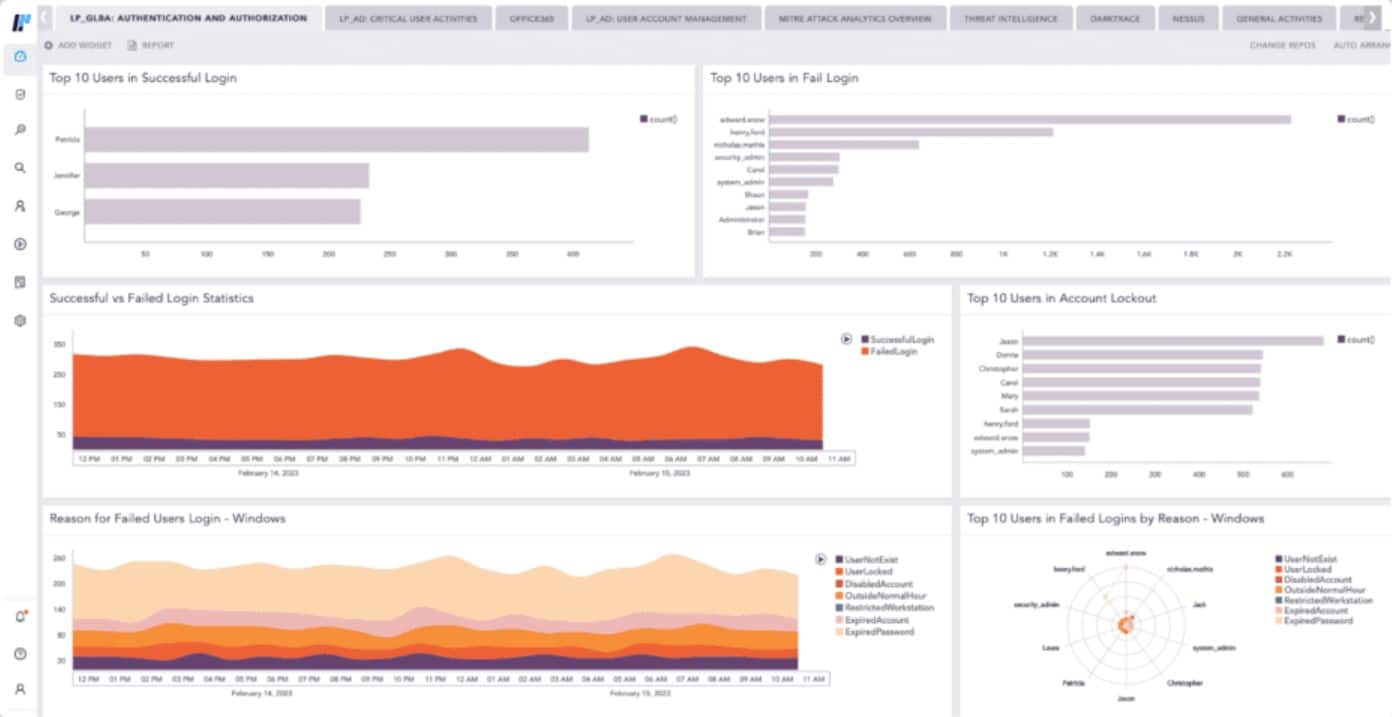
Logpoint offers a converged SIEM – that term refers to a combined SIEM, UEBA, and SOAR package. UEBA refers to behavior baselining by tracking the regular activity of each user account and device. The threat-hunting service in Logpoint is an anomaly detection system that looks for deviations from the established norm.
Key Features:
- Anomaly Detection with AI-Based Baselining: Offers advanced anomaly detection capabilities with AI-based baselining, enabling proactive threat detection by identifying deviations from the established norm.
- Log Collection and Application Activity Report Gathering: Provides comprehensive log collection and gathers application activity reports, enabling organizations to gain insights into user and entity behavior.
- Log Management: Offers robust log management capabilities, ensuring the integrity and security of log data while facilitating efficient log analysis.
- Cloud Storage Space for Log Files: Provides organizations with scalable and secure storage solutions for their log data.
- Log Analysis Tools: Offers powerful log analysis tools, enabling organizations to extract actionable insights from their log data and facilitate informed decision-making.
- Compliance with GDPR, CCPA, and SCHREMS-2: Ensures compliance with regulations such as GDPR, CCPA, and SCHREMS-2, helping organizations meet regulatory requirements and avoid potential fines and penalties.
- Hosted System with Software Maintenance Included: Includes software maintenance, ensuring organizations receive timely updates and support to maintain optimal performance and security.
Why do we recommend it?
Logpoint comes highly recommended for organizations seeking a converged SIEM solution, combining SIEM, UEBA (User and Entity Behavior Analytics), and SOAR (Security Orchestration, Automation, and Response) capabilities. This comprehensive package offers advanced anomaly detection with AI-based baselining, log collection, management, and analysis, making it a powerful tool for proactive threat detection and incident response. Our experience with Logpoint has highlighted its effectiveness in compliance with regulations such as GDPR, CCPA, and SCHREMS-2, ensuring organizations meet regulatory requirements while bolstering their cybersecurity posture. With its hosted system and included software maintenance, Logpoint provides a hassle-free solution for organizations looking to enhance their security operations.
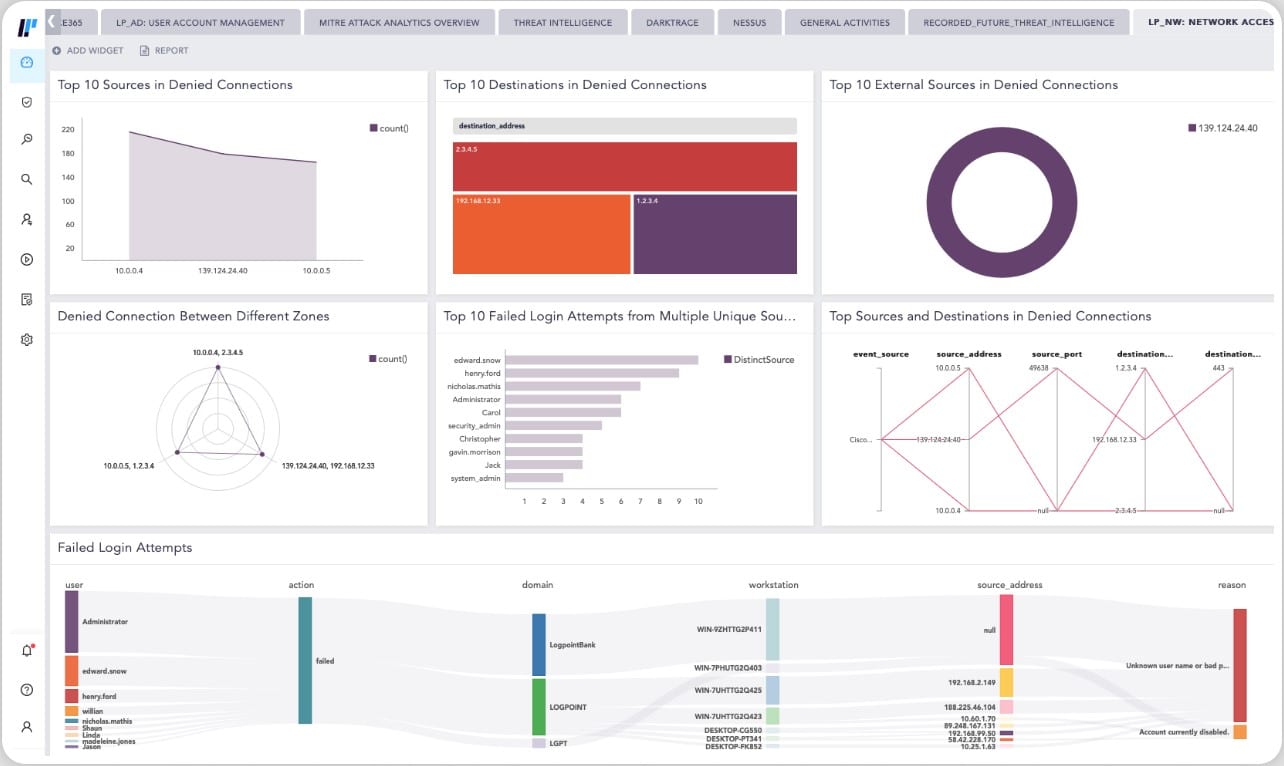
The SOAR part of the Logpoint package is a security orchestration, automation, and response service. This uses integrations and APIs to communicate with third-party trolls. Actions taken by this system include the gathering of activity data directly from applications and automated responses that are implemented by sending instructions to other security tools.
The main package of Logpoint is hosted in the cloud. On-site actions are implemented by an agent that needs to be installed on one of your servers. This system collects data that is uploaded for threat hunting and it also communicates instructions to this-party tools in order to mitigate detected threats.
Who is it recommended for?
Logpoint is recommended for organizations requiring a comprehensive SIEM solution with advanced UEBA and SOAR capabilities. Ideal for organizations of all sizes and industries, Logpoint offers automated data collection, threat hunting, and mitigation, making it suitable for organizations seeking to streamline their security operations and enhance their incident response capabilities. Whether you're monitoring applications, servers, or networks, Logpoint provides comprehensive coverage and alert prioritization, ensuring that security teams can focus on the most critical threats. While it may not have a price list readily available, the value provided by Logpoint's integrated SIEM, UEBA, and SOAR capabilities makes it a compelling choice for organizations prioritizing cybersecurity and compliance.
Pros:
- Automated Data Collection, Threat Hunting, and Mitigation: Streamlines security operations and enhances incident response effectiveness.
- Monitors Applications, Servers, and Networks: Provides comprehensive coverage, monitoring applications, servers, and networks to identify and mitigate security threats across the entire IT environment.
- Includes Cloud Platform Monitoring: Enables organizations to gain visibility into their cloud infrastructure and ensure security across hybrid environments.
- Special Integration with SAP for Monitoring: Provides organizations with enhanced visibility and security for their SAP environments.
- Alert Prioritization: Prioritizes alerts, ensuring that security teams can focus on addressing the most critical threats and vulnerabilities first.
Cons:
- No Price List: Does not have a readily available price list, which may require organizations to request a quote for pricing information.
The Logpoint service is priced on data throughput volumes so the process of finding out the cost of the system is interactive. You need to get a quote to find out the price for your implementation. Start by registering for a free demo.
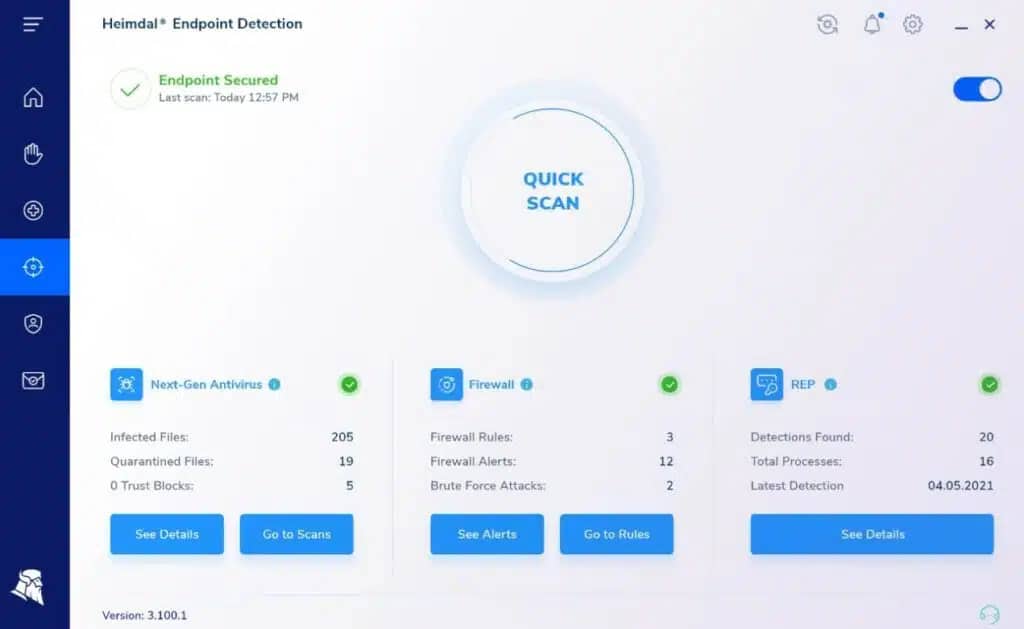
6. Heimdal Threat Hunting and Action Center
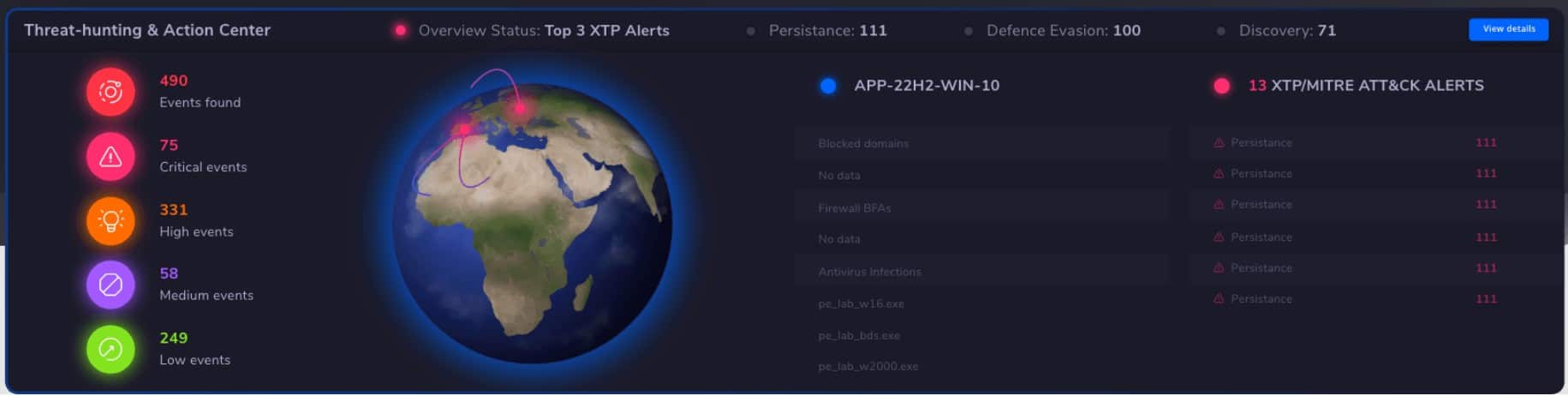
Heimdal Threat Hunting and Action Center is a cloud-based SIEM package that receives activity reports from on-premises Heimdal tools, searches that consolidated data for threats, and sends back response instructions. This tool also performs vulnerability scanning.
Key Features:
- Coordinates Activities of On-Premises Cybersecurity Systems: Consolidates activity reports from on-premises Heimdal tools, coordinating their activities to identify and mitigate potential security threats.
- Searches Uploaded Activity Data for Insider Threats and Intrusion: Performs advanced threat searches on uploaded activity data, enabling proactive threat detection and response.
- Performs Vulnerability Scanning and Advises for System Hardening: Provides recommendations for system hardening, enhancing overall cybersecurity posture.
- Sends Response Instructions to On-Premises Systems: Upon detecting security threats, this solution sends response instructions to on-premises systems, facilitating rapid incident response and mitigation.
- Warns Other Devices on a Network of a Detected Threat: Alerts other devices on the network of detected threats, preventing lateral movements by malware and intruders.
- Dashboard Provides Overviews of System Activity: Enables administrators to monitor and manage security events effectively.
Why do we recommend it?
Heimdal Threat Hunting and Action Center is highly recommended for organizations seeking a comprehensive cloud-based SIEM package with advanced threat detection and response capabilities. This solution offers seamless coordination with on-premises Heimdal cybersecurity systems, consolidating activity reports and performing threat searches to identify and mitigate potential security risks. Our experience with Heimdal Threat Hunting and Action Center has highlighted its effectiveness in performing vulnerability scanning, advising for system hardening, and sending response instructions to on-premises systems, ensuring proactive threat mitigation and incident response. With its private corporate threat intelligence platform, data loss prevention measures, and flexible package options, Heimdal Threat Hunting and Action Center provides a robust and adaptable solution for organizations prioritizing cybersecurity and threat management.
The Threat Hunting and Action Center will only activate if the site has at least three different Heimdal products installed. One of these three must be the Next-Generation Anti-Virus system, which includes a mobile device management (MDM) system and runs on Windows, macOS, Linux, Android, and iOS. The other two services can be selected from Network Security, Email Security, Patching & Asset Management, and Endpoint Security.
Who is it recommended for?
Heimdal Threat Hunting and Action Center is recommended for organizations requiring a cloud-based SIEM solution with integrated threat detection and response capabilities. Ideal for enterprises and businesses of all sizes, this solution offers comprehensive protection against insider threats, intrusion attempts, and malware infections. To fully activate the Threat Hunting and Action Center, a minimum of three different Heimdal products must be installed, including the Next-Generation Anti-Virus system, which encompasses mobile device management (MDM) and supports multiple operating systems. The other two services can be selected from Network Security, Email Security, Patching & Asset Management, and Endpoint Security, providing flexibility to meet specific security requirements and operational needs. While it may not be a standalone product, Heimdal Threat Hunting and Action Center's seamless integration with on-premises elements and cloud platform ensures holistic threat management and cybersecurity resilience.
Pros:
- Creates a Private Corporate Threat Intelligence Platform: Enables organizations to proactively identify and respond to security threats.
- Blocks Lateral Movements by Malware and Intruders: Minimizes the spread of infections and mitigating potential damage.
- Implements Data Loss Prevention: Safeguards sensitive information from unauthorized access and exfiltration.
- Flexible Package with On-Premises Elements: Seamless integration of on-premises elements and the cloud platform, ensuring comprehensive threat management and cybersecurity resilience.
- Options to Implement User Activity Tracking: Enables organizations to monitor and manage user interactions effectively.
Cons:
- Not a Standalone Product: Requires a minimum of three different Heimdal products to be installed for full activation, making it dependent on other Heimdal cybersecurity systems for functionality.
Heimdal doesn’t publish a price list. There is no free trial of the Threat Hunting & Action Center but you can request a demo.
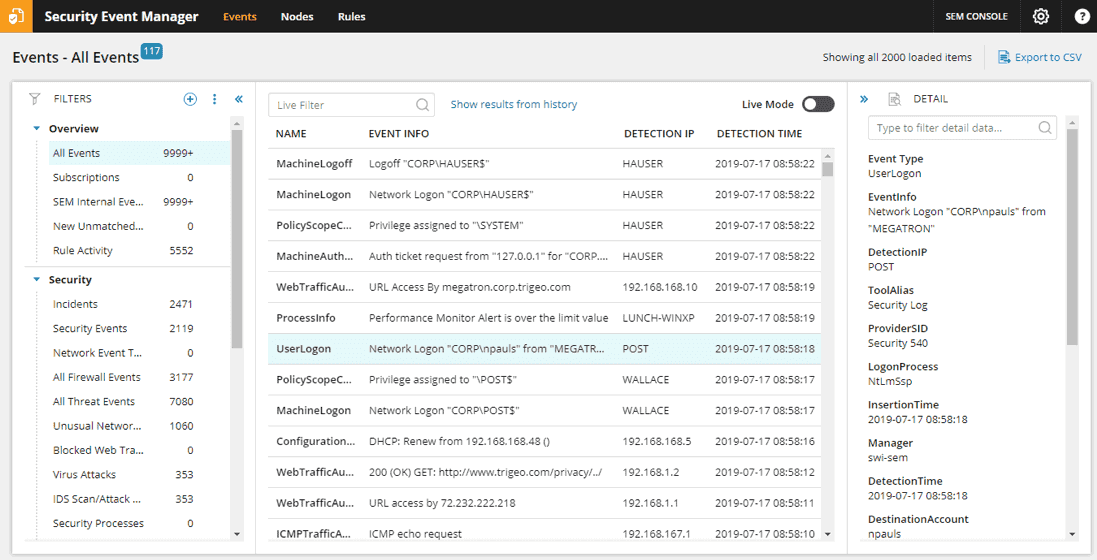
7. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a very good solution if you particularly want an onsite software package. This system installs on Windows Server.
Key Features:
- Log Message Collection and Consolidation: Provides a centralized repository for easy access and analysis.
- Logfile Management and Protection: Robust logfile management and protection features, ensuring the integrity and security of log data against tampering.
- Live Network Monitoring Data Feed: Integrates live network monitoring data into log searches, enhancing anomaly detection capabilities and facilitating real-time incident response.
- Analytical Tools for Manual Data Exploration: With its analytical tools, users can manually explore log data to identify security threats and suspicious activities, empowering proactive security measures.
- System Alerts and Notifications: Generates system alerts to identify suspicious events and notifies administrators via email or SMS, enabling prompt incident response and resolution.
- Compliance Reporting: Offers compliance reporting features for standards such as PCI DSS, HIPAA, SOX, GLBA, and NERC SIP, ensuring adherence to regulatory requirements and industry standards.
Why do we recommend it?
SolarWinds Security Event Manager is highly recommended for organizations seeking an onsite software package for comprehensive log management and security operations. Particularly suited for Windows Server environments, this solution offers robust features tailored to meet the needs of enterprise-level security management. Our experience with SolarWinds Security Event Manager has demonstrated its effectiveness in log message collection, logfile management, and live network monitoring, providing invaluable insights for anomaly detection and security incident response. With its analytical tools, system alerts, and compliance reporting capabilities, SolarWinds Security Event Manager offers a comprehensive solution for organizations prioritizing data protection and regulatory compliance.
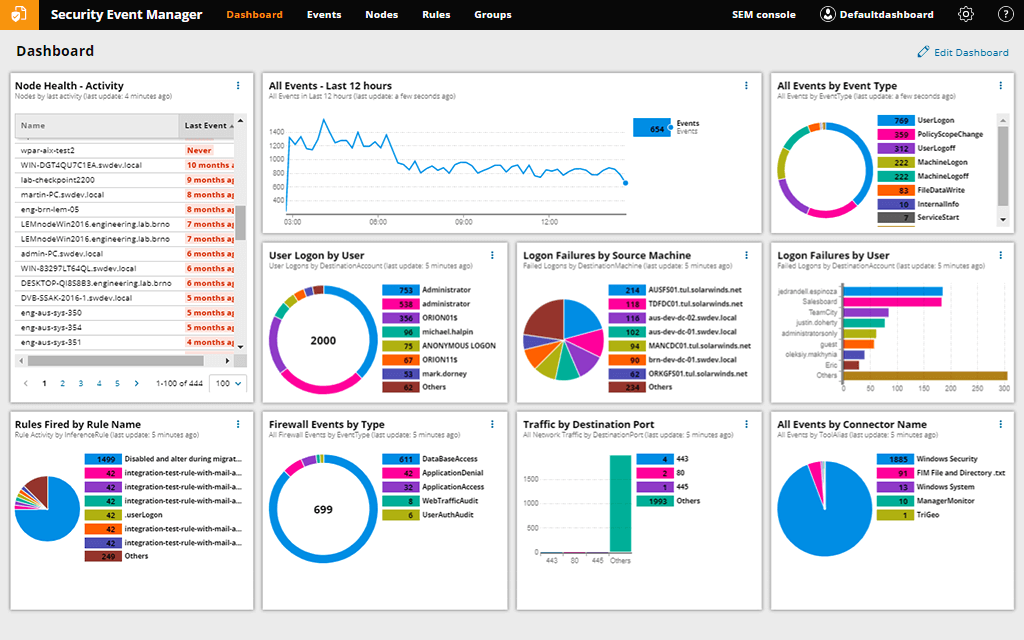
This is a very strong log file management system as well as a security operation. The Security Event Manager collects log messages and stores them in a meaningful directory structure for easy access. It then protects those directories and files from tampering. This is a vital requirement for any site-based SIEM.
The log management and security built into this system is important if you need to comply with data protection standards. The Security Event Manager will help you with compliance to HIPAA, PCI DSS, GLBA, NERC SIP, and SOX accreditation, plus other standards.
As well as logs the Security Event Manager pulls in regular reporting messages, such as SNMP reports on network device activities, so it works on live monitoring information, providing the NIDS part of SIEM as well as the HIDS functions of log analysis.
Who is it recommended for?
SolarWinds Security Event Manager is recommended for organizations requiring a strong log file management system combined with robust security operations. Ideal for compliance-driven industries such as healthcare, finance, and energy, this solution ensures adherence to data protection standards such as HIPAA, PCI DSS, GLBA, NERC SIP, and SOX accreditation. Whether you're an IT professional responsible for network security or a compliance officer ensuring regulatory compliance, SolarWinds Security Event Manager provides the tools and capabilities necessary to effectively manage security events and protect sensitive data. While it may require some time to fully learn the platform, its wide range of integrations and customizable templates make it accessible and adaptable to various organizational needs and environments.
Pros:
- Enterprise-Focused SIEM with a Wide Range of Integrations: Designed for enterprise-level security management and offers extensive integrations with third-party tools and services.
- Simple Log Filtering: Users can easily filter log data without the need to learn a custom query language, enhancing usability and efficiency.
- Dozens of Templates: Allows administrators to quickly start using the solution with minimal setup or customization.
- Historical Analysis Tool: Helps identify anomalous behavior and outliers on the network, facilitating proactive threat detection and mitigation.
Cons:
- Requires Time to Fully Learn the Platform: Advanced SIEM product that may require time for professionals to fully learn and utilize its capabilities effectively.
Access the online quote engine to get a price. SolarWinds offers a 30-day free trial of the Security Event Manager.
8. Rapid7 InsightIDR
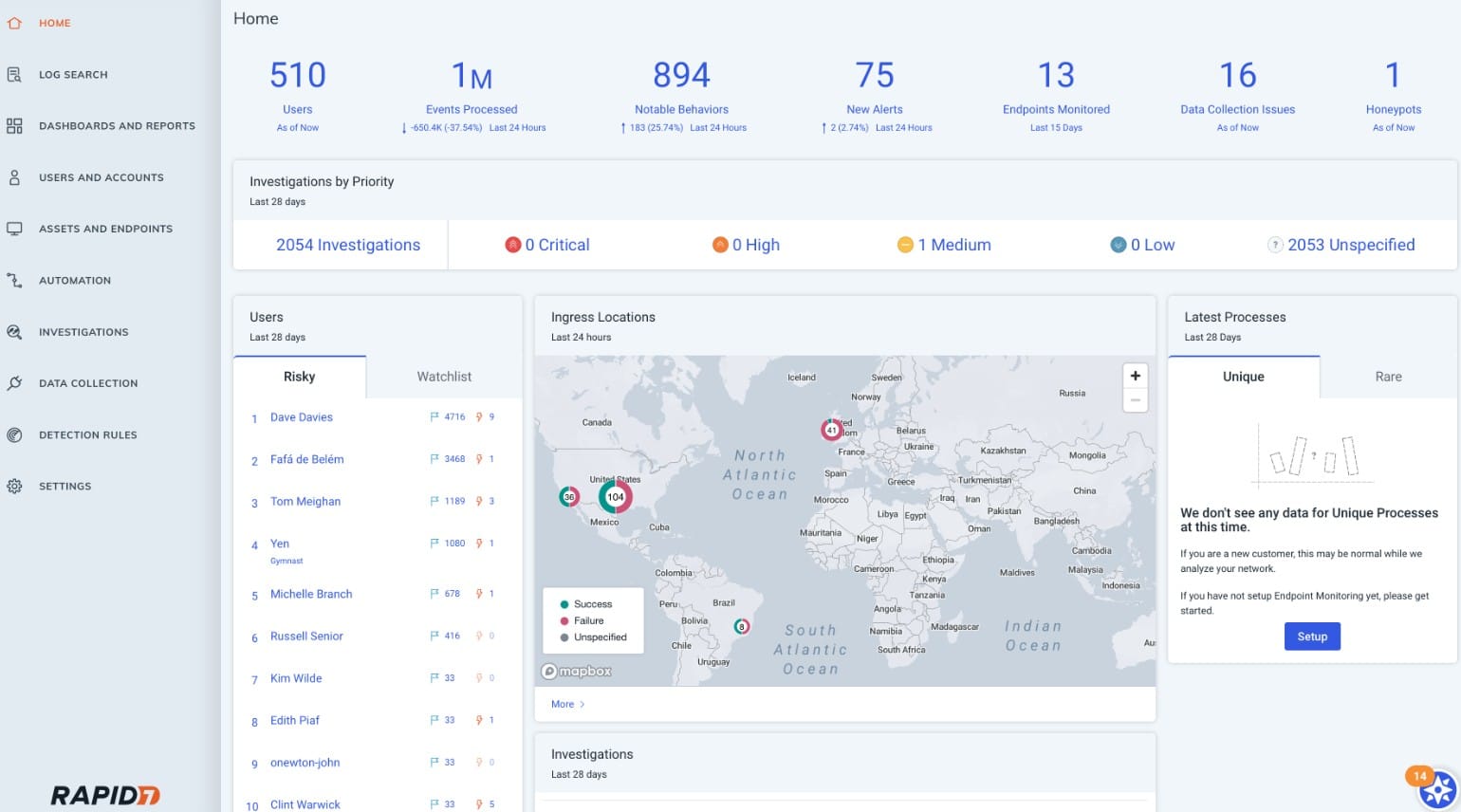
Rapid7 InsightIDR is a cloud-based SIEM that also includes network monitoring and Endpoint Detection and Response (EDR). This service is advertised as an XDR, which stands for Extended Detection and Response, however, it is still a SIEM – and a NextGen SIEM at that.
Key Features:
- On-Site Log Collector and Cloud-Based Log Consolidator: Enables centralized log management and analysis.
- Live Threat Intelligence Feed: Offers threat hunting informed by a live threat intelligence feed, providing real-time threat analysis and updates for proactive threat detection and response.
- UEBA for Accurate Activity Baselining: Includes UEBA functionalities for accurate activity baselining and threat detection, enhancing cybersecurity posture and reducing false positives.
- Processing and Log File Storage: InsightIDR cloud service includes all the processing power and log file storage space needed, ensuring scalability and performance.
- Deception Technology: Enhances onsite protection with deception technology, creating honeypots and traps to detect and divert intruders and keep valuable data secure.
Why do we recommend it?
Rapid7 InsightIDR is highly recommended for organizations seeking a cloud-based SIEM solution with advanced threat detection capabilities and comprehensive network monitoring and Endpoint Detection and Response (EDR) functionalities. As an Extended Detection and Response (XDR) platform, InsightIDR offers an integrated approach to threat detection and response, combining SIEM, UEBA, and threat intelligence feed functionalities. Our experience with InsightIDR has highlighted its ability to leverage behavioral analytics to detect threats that bypass signature-based detection, providing organizations with advanced threat detection capabilities and enhancing cybersecurity posture. Additionally, InsightIDR's threat intelligence service, termed “attacker behavior analytics,” provides real-time threat analysis and updates, ensuring organizations are equipped to respond effectively to evolving threats.
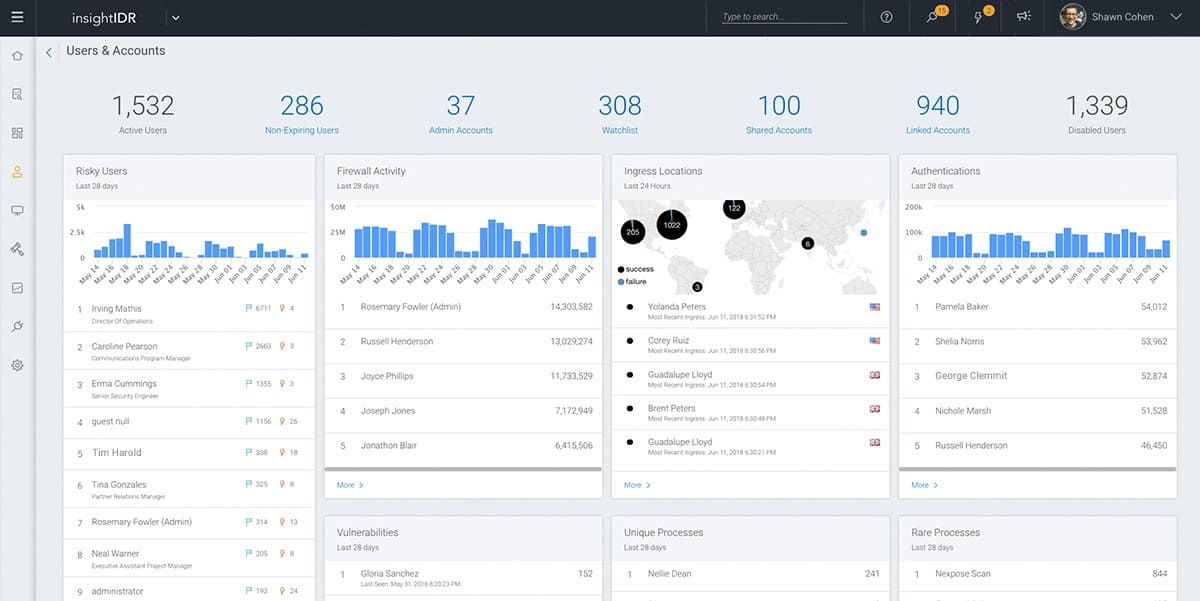
InsightIDR has all of the classic elements of a next-generation SIEM, notably, a UEBA system and an intelligence feed. The threat intelligence service is termed “attacker behavior analytics.” This is a database of indicators of compromise that gets constantly updated as the operating SIEM instances running for all Rapid7’s customers report into a common intelligence pool.
Rapid7 cloud service includes all of the processing power and log file storage space you need. Onsite protection is enhanced by deception technology that creates honeypots to force data thieves into the open and traps to keep intruders away from valuable data.
Who is it recommended for?
Rapid7 InsightIDR is recommended for organizations of all sizes and industries seeking a cloud-based SIEM solution with comprehensive threat detection and response capabilities. Ideal for organizations prioritizing proactive threat detection and automated remediation, InsightIDR offers robust UEBA functionalities for accurate activity baselining and threat detection. Whether you're a small business or a large enterprise, InsightIDR provides communications over encrypted connections, ensuring data confidentiality and integrity. While pricing may be higher than similar tools on the market, the value provided by InsightIDR's advanced threat detection capabilities and automated remediation features makes it a compelling choice for organizations looking to strengthen their security defenses.
Pros:
- Leverages Behavioral Analytics: Detects threats that bypass signature-based detection, enhancing threat detection capabilities.
- Real-Time Threat Analysis: Uses multiple data streams to provide the most up-to-date threat analysis methodologies, enabling organizations to respond effectively to evolving threats.
- Automated Remediation: Enables organizations to respond quickly and effectively to security incidents.
Cons:
- Higher Pricing: Pricing may be higher than similar tools on the market, which could be a consideration for organizations with budget constraints.
- Paid Plugins for Some Features: Some features may require paid plugins, potentially adding to the overall cost of implementation and use.
The InsightIDR package is a subscription service with a price starting at $2,157 per month. Rapid7 Insight IDR is accessed online and you can get it on a 30-day free trial.
9. UnderDefense SIEM
UnderDefense SIEM is a managed service. That is one step up from a SaaS system because it includes the services of analysts and technicians to watch over the SIEM and act on its reports. Surprisingly, the package doesn’t include the SIEM software.
Key Features:
- Security Management Team on Call: Provides access to a dedicated security management team on call around the clock, ensuring organizations can respond effectively to security alerts and incidents.
- Choice of SIEM Systems: Allows organizations to select the system that best fits their requirements.
- Flexible Hosting Options: Offers the option to host the SIEM software on your servers or in the cloud, providing flexibility and scalability.
- Vulnerability Prioritization: Enables organizations to prioritize and address critical security vulnerabilities effectively.
- Free Trial: New users get their first month free, allowing organizations to evaluate the service before committing to a subscription.
Why do we recommend it?
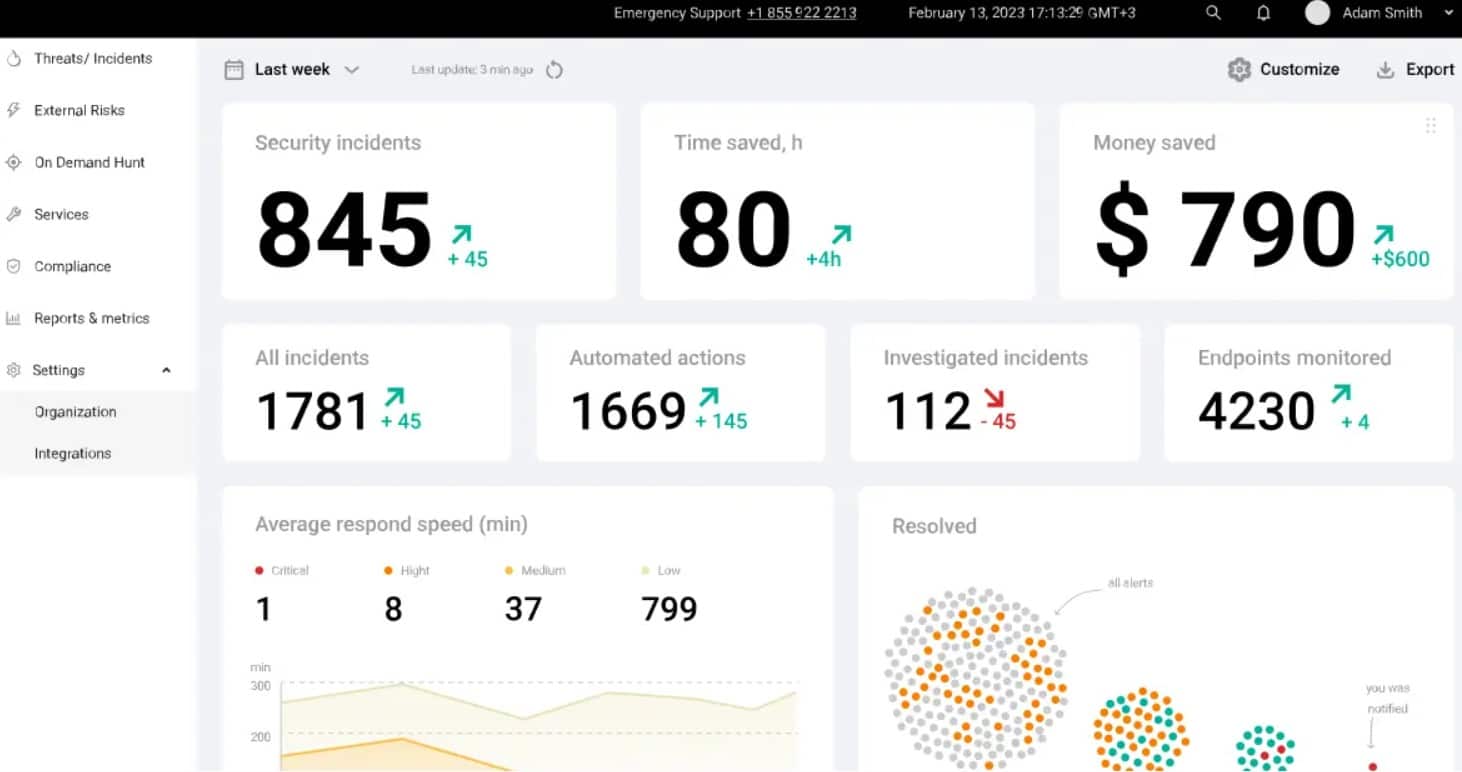
UnderDefense SIEM is highly recommended for organizations seeking a managed SIEM service with access to a dedicated security management team. As a co-managed service, UnderDefense SIEM offers the expertise of analysts and technicians to monitor and respond to security alerts, relieving organizations of the burden of building larger cybersecurity teams. Our experience with UnderDefense SIEM has highlighted its highly customizable and elegant dashboard, which provides organizations with actionable insights and visibility into their security posture. Additionally, UnderDefense SIEM offers vulnerability prioritization and access to on-call experts, ensuring organizations can respond effectively to security incidents and mitigate risks.
UnderDefense offers you a choice of SIM software to work with. It will then install your chosen system and manage it. You can decide whether to host the software on your own server, in which case, the UnderDefense technicians will get remote access.
Who is it recommended for?
UnderDefense SIEM is recommended for enterprises and organizations of all sizes seeking a managed SIEM service with access to dedicated security expertise. Ideal for organizations that don't want to build larger cybersecurity teams, UnderDefense SIEM offers a co-managed approach, providing access to on-call experts and a dedicated security management team. Whether you're a small business or a large enterprise, UnderDefense SIEM offers a choice of SIEM systems and hosting options, ensuring compatibility and scalability. While better suited for enterprises and large networks, UnderDefense SIEM also offers a free trial for new users, enabling organizations to evaluate the service before committing to a subscription.
Pros:
- Co-Managed Service: Ideal for businesses that don't want to build larger cybersecurity teams and prefer access to dedicated security expertise.
- Access to On-Call Experts: Ensures organizations can receive timely assistance and guidance in responce to security incidents.
- Highly Customizable and Elegant Dashboard: Provides organizations with actionable insights and visibility into their security posture.
- Vulnerability Prioritization: Enables organizations to prioritize and address critical security vulnerabilities effectively.
- Free Trial: New users get their first month free, enabling organizations to evaluate the service and its capabilities before committing to a subscription.
Cons:
- Better Suited for Enterprises and Large Networks: While suitable for organizations of all sizes, UnderDefense SIEM may be better suited for enterprises and large networks due to its co-managed approach and access to dedicated security expertise.
Fees start at $6 per month per endpoint plus the cost of your chosen SIEM package. Contact UnderDefense for a quote. There is no download for this service but you can request a demo.