We may earn a commission if you make a purchase through the links on our website.
7 Best USB Encryption Software Tools
UPDATED: February 21, 2024
Encrypt and protect your USB data while enforcing encryption standards on your network with these 7 USB encryption tools.
USB encryption enables you to safeguard your users and your company from security breaches in businesses where it's normal practice to travel with laptops, external drives, or USBs, as well as in areas where physical device theft poses a risk. To protect your sensitive data, you can prevent people from getting through your unencrypted security measures, such as login passwords, by encrypting your devices.
Within this article, we discuss a variety of USB encryption software tools that can enable you to encrypt USB devices. A number of these options also go above and beyond by providing additional useful features that can help this process—such as blocking unencrypted USB access on your network or providing a centralized location where you can deploy and monitor your encryption status.
Here is our list of the Best USB Encryption Software Tools:
- Endpoint Protector Device Control (EDITOR’S CHOICE) includes a range of security services that block malware from being transferred onto a computer from a USB and prevent data theft through file transfers onto peripheral devices. Get a 30-day free trial.
- Veracrypt Open-source, a well-supported encryption technology that, when combined with their consistently updated development, offers unrivaled endpoint encryption.
- Microsoft Bitlocker An open-source, secure solution that is preinstalled on all Windows 10 and Windows 11 devices—offering straightforward USB encryption with Bitlocker To Go.
- Sophos Central Device Encryption An expert encryption management tool that makes use of Bitlocker to give one of the best endpoint encryption management solutions.
- ESET Endpoint Encryption For the implementation and management of centralized USB encryption, ESET has provided an ideal solution that allows you to specify various authentication standards for individual policies.
- Drivelock Device Control Drivelock utilizes the built-in encryption and antivirus system to safeguard your network from malware and data loss, as well as the drivelock USB lockout functions to demonstrate its superior USB protection capabilities.
- Budulock Despite not allowing you to encrypt data on USB drives, Budulock does allow you to apply an encrypted master password to your USB devices, effectively giving you full-drive encryption.
Our methodology for selecting a USB encryption tool
We reviewed the market for USB encryption services and assessed the tools based on the following criteria:
- A data loss prevention tool that blocks the movement of sensitive files
- Enforced encryption to ensure files are protected
- An encryption system that prevents unauthorized programs from being copied onto a USB stick in order to block malware infection
- A tool that will also block programs on a USB stick from launching
- Identification of each USB stick by serial number
- A free trial or a demo to enable an assessment before buying
- A fair price that is suitable with respect to the utilities provided
The Best USB Encryption Software Tools
1. Endpoint Protector
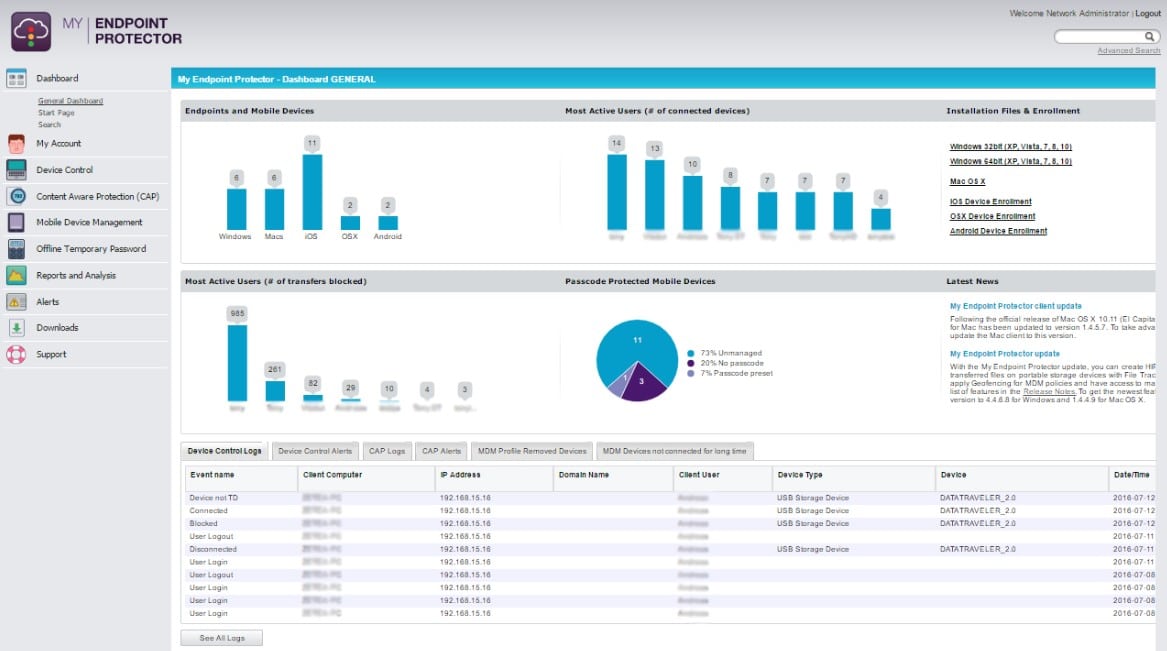
Endpoint Protector by CoSoSys has a feature called Enforced Encryption that protects your network by preventing unencrypted devices from accessing your network and rolling out encryption to all of your external media via a centralized point of control. This means that you can simultaneously encrypt all USBs that access your network while keeping your network safe. It only takes distributing a single, lightweight agent throughout your network to implement the fully cross-platform solution.
Key Features:
- Identify and register USB devices
- Detailed control over USB ports
- Lightweight distributed agent
- Restrict unencrypted USB access
- Enforce encryption across all USB-connected media
Why do we recommend it?
Endpoint Protector Device Control is a centralized endpoint peripheral port controller. All ports are blocked but then the administrator can approve a device for use and then it will function when connected while others remain blocked. Usage can require that encryption software is installed on the device.
In addition to protecting against malware spread via USB, Endpoint Protector offers data loss prevention tools to secure your network against data leaking. Monitoring and configuration are managed through a web-based interface. You can still approve remote USB access for quick connections even when the device is offline. You can create more detailed rules depending on the policy for tighter control, and even employ an extra level of security through password protection.
The solution is available on the company website for a 30-day free trial. To find out the full cost of the software, you must get a quote from CoSoSys. Keep in mind that the cost may differ significantly depending on your unique requirements, but you’ll need to ensure you have access to the Enforced Encryption feature to fully enable remote USB encryption control.
Who is it recommended for?
The Device Control unit is part of the Endpoint Protector platform rather than a standalone product. The main reason that any company would buy the site is for data loss prevention. The package’s routines also provide malware protection. CoSoSys doesn’t publish a price list for the Endpoint Protector system.
Pros:
- Protects computers running Windows, macOS, or Linux
- Manages data movements to printers and other peripheral devices
- Blocks malware from executing while resident on a USB
- Records all file movements onto or from a USB
- Enforces encryption on USBs for data protection
Cons:
- No price list
EDITOR'S CHOICE
Endpoint Protector Device Control is our top pick for a USB encryption tool because it centralizes the control of the USB ports of all endpoints on a protected network. The package provides an administrator with a central console to manage the ports on all endpoints. The system is designed to run on the cloud as a service on the major public platforms but it is also possible to download the code and run it on a VM. CoSoSys also provides a hosted version, which is available for subscription. The rest of the Endpoint Protector package provides malware protection and data loss prevention for all of the endpoints in an enterprise.
Download: Get a 30-day free trial
OS: AWS, Azure, GCP, SaaS, or VM
2. Veracrypt
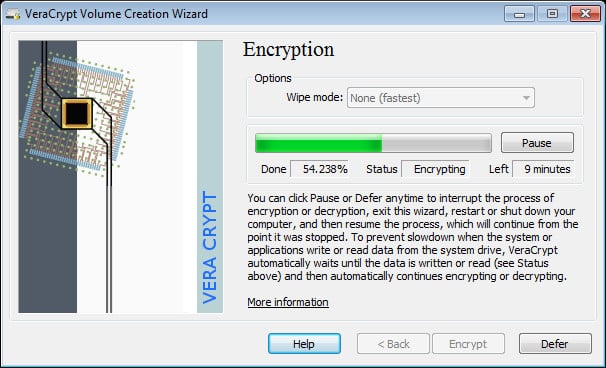
Closed-source solutions and the dangers they present are topics of discussion within the encryption community. The possibility exists that backdoors might be incorporated into the encryption at the direction of governments or organizations because the encryption software is hidden. Therefore, a lot of people use open-source encryption solutions; Veracrypt is the best open-source USB encryption solution.
Key Features:
- Open-source and free
- Full-disk and File/Folder encryption
- Supported on all desktop OSes
- Create hidden volumes
- AES, Serpent, Twofish, and more ciphers
Why do we recommend it?
Veracrypt is a free utility that can create an encrypted vault on a hard drive or encrypt an entire USB stick. The software for this tool will run on Windows, macOS, and Linux. It will encrypt a device that is plugged into the software’s host computer.
Despite being free and open-source, Veracrypt offers in-depth encryption options that make it especially good for a specialized piece of software—though don’t expect additional features that come as standard to some premium solutions like DLP and USB lockdown. Veracrypt offers both a full-disk USB encryption solution and an individual file/folder encryption solution. By adding some human-driven unpredictability to the mix using your mouse movements, Veracrypt additionally strengthens your encryption key.
Veracrypt is free to download and use on Mac, Windows, and Linux, although full-disk encryption is only supported by Windows. Once the program has been installed on your network, you will be responsible for its updating and management, as it provides no centralized point of control.
Who is it recommended for?
This is a nice free tool for personal use or for small businesses. The tool can’t operate across a network and it doesn’t include any data loss prevention mechanisms, so it wouldn’t be suitable for use by businesses that have to comply with data protection standards.
Pros:
- Can create a hidden crypt within the encrypted space
- Encrypts and decrypts in real time
- Deploys steganography to hide files in images
- Fast operations
Cons:
- Not suitable for data loss prevention
3. Microsoft Bitlocker
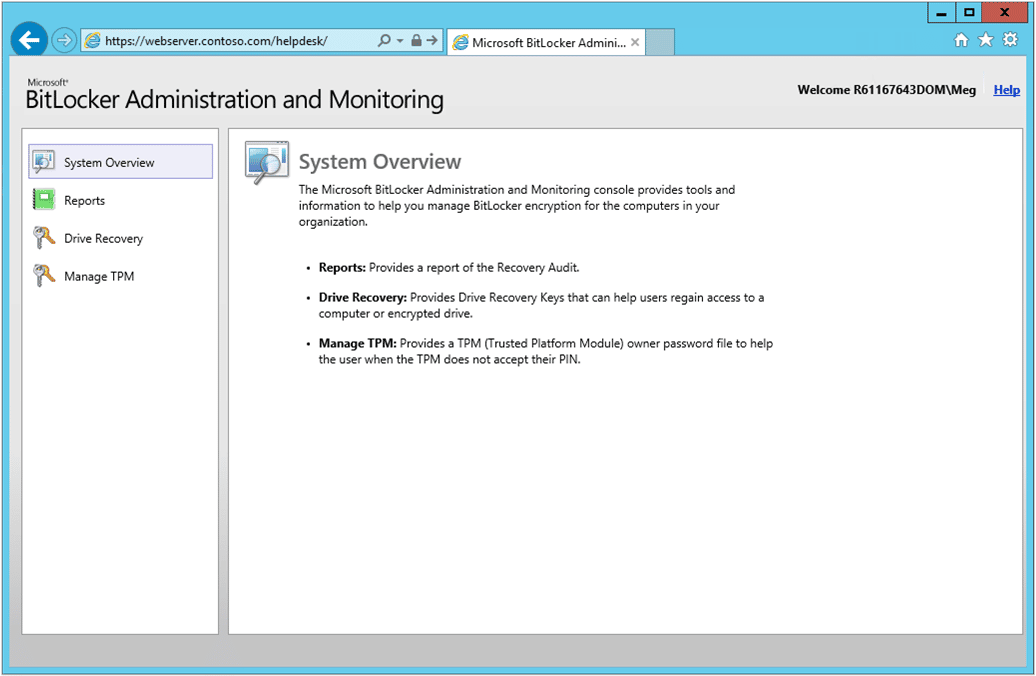
When it comes to endpoint encryption, the simplest approach is probably the best. Microsoft Bitlocker is already installed on Windows Professional or Enterprise editions, as well as Windows Server 2008 and later. Bitlocker typically requires a TPM chip on your system to function properly, but not in the case of solely encrypting USB drives.
Key Features:
- Simple installation
- Included on Windows OS as standard
- Completely free
- AES-128 or 256, with support for XTS-AES
- Windows only
Why do we recommend it?
Microsoft Bitlocker is included in all versions of Windows and Windows Server from Windows 10 and Windows Server 2016. The system can be set up through File Explorer. The user defines a password before encrypting a USB device and this will be required to access the drive once it has been encrypted.
Once installed, Bitlocker encrypts your USBs by utilizing just the OS and the access methods of your choice. Since it will update along with your operating system, there is no need to download additional software or manage separate upgrades. However, do note that Bitlocker is Windows only, and as such may not be viable if your network has Mac or Linux systems as a requirement.
Bitlocker To Go is the specific software branch you’ll need to look for to perform USB encryption, but it also includes full support for SD cards, external hard disk drives, and other drives that are formatted by using the NTFS, FAT16, FAT32, or exFAT file system.
Who is it recommended for?
Bitlocker is a free service in Windows and so anyone who has a computer running Windows or Windows Server already has the tool available. The service doesn’t include any data loss prevention measures in it. The purpose of the BitLocker system is to secure backups or to reduce the risk of data disclosure through the loss of a USB with files loaded onto it.
Pros:
- Password protected secure storage
- Recovery key in case of forgotten password
- Encrypt the entire drive or just use disk space
Cons:
- No data loss prevention measures
4. Sophos Central Device Encryption
Sophos Central Device Encryption may be the ideal option for your network administration requirements if you're seeking a more sophisticated solution while still wanting to use Bitlocker. The maintenance and distribution of Windows Bitlocker are effectively integrated into the Central Device Encryption program. Sophos has created an application to act as an administration and control web interface by delegating the encryption portion of the task to the OS.
Key Features:
- Bitlocker/Filevault-driven encryption
- Pin and Password recovery
- Central USB encryption rollout
- Logs and reporting for compliance proof
- Sophos Endpoint Protection integration
Why do we recommend it?
Sophos Central Device Encryption is an add-on service for the Sophos Central cloud-based range of security products. The tool can be added onto any of the Endpoint Detection and Response units offered by the platform. The tool provides a central controller that interacts with the built-in encryption services of Windows and macOS.
The software has a self-driven pin and password recovery option that enables users to retrieve their lost login information as well as an administrator-managed recovery feature that enables tighter control. Additionally, You may verify the encryption status of any USB device on your network from the management solution and send encryption requests to those devices, asking your users to set up new passwords.
Notably, Central Device Encryption is compatible with Filevault, Mac's version of Bitlocker. As a result, if you're in charge of managing a Mac-using company, you can coordinate the endpoint encryption of both your Mac and Windows devices from a single platform.
Sophos Central Device Encryption costs $20 per user each year (or $40 per person for three years) once there are 100 users. On the website, Sophos also offers a free trial and a comprehensive software demo. Be aware that you are paying for the web application that controls the encryption, not the encryption itself, which is a standard feature of compatible Windows/Mac computers.
Who is it recommended for?
There is a Small Business edition for the package and there is also a Home edition, which is free to use. The company also offers a managed service, which is called Sophos MDR. However, you would probably want to access the USB encryption service yourself.
Pros:
- A Web-based controller for multiple endpoints
- Remote operations
- Operates through an agent installed on each endpoint
Cons:
- No price list
5. ESET Endpoint Encryption
ESET has offered a qualified solution for the deployment and administration of centrally controlled USB encryption. Installation of a management console and synchronization of that console with your active directory are prerequisites for managing the ESET encryption, but the rollout policies can then be set up based on user credentials from within the dashboards.
Key Features
- Encryption management console
- Active Directory sync
- USB restrictions are based on policy
- Remote management
- AES-256 and 128
Why do we recommend it?
ESET Endpoint Encryption is similar to the Sophos system because it gives you a cloud-based controller console for managing multiple endpoints and includes the provision of encryption. The tool reaches out to the native encryption systems of Windows, Windows Server, and macOS. Both Bitlocker and FileVault both encrypt USB drives.
ESET Endpoint Encryption allows you some administrative freedom, allowing you to set different authentication criteria for various departments. This also means you can control USB encryption as they access your network based on the workstation policy, which can be used to limit or regulate access to non-encrypted memory devices. Any removable media device may be used under an “Open” policy, “Blocked” policy, which prevents access to removable devices, or “Read Only” policy, where the devices can be read but not written to.
ESET has a variety of licensing choices, but the full-drive encryption you're likely looking for is only available in the Pro version. The software is available for free trial upon request from the ESET website. Contact the company or one of their resellers to obtain a one-year license for around $60.
Who is it recommended for?
This package is suitable for any size of business. The central controller will centralize the management of multiple endpoints without a limit on the number of units that can be included. The package will block all USB ports, allowing the administrator to allow specific devices to attach for specific users.
Pros:
- Blocks USB ports with administrator power to allow specific devices
- Uses native operating system encryption systems
- Can control endpoints on multiple sites
Cons:
- Doesn’t have a proprietary encryption system
6. Drivelock Device Control

Drivelock Device Control is a standalone product on the Drivelock platform. The tool can also pair with the Application Control unit on the platform. It provides user-transparent encryption for external devices and data media. Encryption is highly safe and reasonably quick with no backdoors and 2FA support. Along with protecting USB flash drives, this software also lets you create security restrictions for several kinds of external storage.
Key Features:
- USB access restrictions
- Inbuilt file encryption and antivirus
- Network access reports
- Basic security monitoring
- Granular control based on file type
Why do we recommend it?
Drivelock Device Control is a centralized manager for multiple endpoints and their USB ports. The tool requires an agent on each of the managed endpoints and that enables the system to block all USB ports. The administrator can then approve specific devices for use on one or any endpoint.
Drivelock establishes itself by totally defending your devices from USB-based malware attacks by utilizing both the drivelock USB restrictions and the integrated encryption and antivirus system. Whatever the size of your business, this solution delivers a simple set of highly optimized functions that make it the best choice for the activity it supports.
The management console for the Drivelock system runs on Windows and Windows Server. The central unit reaches across the network to manage the USB ports on endpoints. Endpoints under management need to be running Windows, Windows Server, or Linux. You can investigate Drivelock Device Control by accessing a 30-day free trial.
Who is it recommended for?
This tool blocks all peripheral devices, not just USB memory sticks. This system can enforce a corporate security policy by implementing controls over which users are allowed to deploy which devices. The system identifies each device by serial number.
Pros:
- USB port control
- Automatic USB drive encryption
- Device allowlisting
Cons:
- No price list
7. Budulock
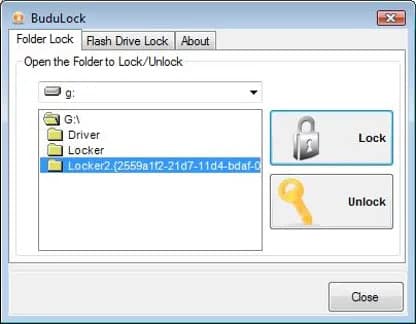
Although Budulock doesn’t allow you to encrypt data on USB drives, it does let you apply an encrypted master password to your USB devices, meaning it effectively provides full-drive encryption. If you’re looking for a free solution, there are a variety available such as Veracrypt or Bitlocker, but Budulock is an option if you’re not looking to encrypt any of the data on your drives, but instead looking to simply apply an encrypted password lock.
Key Features:
- Freeware password-locking solution
- Flash drive locking feature
- Encrypted folder protection
- Windows only
- Limited functionality
Why do we recommend it?
Budulock provides two levels of protection for USB devices. The first is the option to place a password on access to the USB ports on a computer. The second is to password protect the USB device itself. This tool doesn’t encrypt data but blocks access to it through its password requirement.
The software is freeware, incredibly small in size, and simple to use. By eliminating extra stages and concentrating just on the necessary ones, it accomplishes its straightforward goal of imposing password constraints to folders quite well. You require the Flash Drive Lock function, which is the USB password lockdown feature, to restrict USB access on your network.
There are no paid add-ons or features that need to be purchased with Budulock; it is entirely free to download. Many freeware websites, including the one above, offer it for download.
Who is it recommended for?
This tool is an on-device software package for Windows. However, it hasn’t been updated since 2011 so it relies on an older version of the .NET framework than that installed with Windows 10 and 11. The system creates a lock without encrypting data. It is suitable for personal use.
Pros:
- Free to use
- Good for personal use
- Locks USB ports and devices
Cons:
- The software is outdated