We may earn a commission if you make a purchase through the links on our website.
The Best User Provisioning Tools
UPDATED: October 23, 2023
In this day and age of the internet, where every user needs to be thoroughly verified, watched continuously, and efficiently controlled, network and server administrators need to keep track of everyone who utilizes their resources. In addition, if a company has a significant number of user accounts, it is in its best interest to implement a user provisioning and governance solution that is among the best available. This is a crucial component of the security system that has to be addressed immediately. Because of this, no company can afford to disregard the significance of user provisioning tools.
Here is our list of the best user provisioning tools:
The following is a list of the software programs that can assist you with the user provisioning for your company:
- SolarWinds Access Rights Manager – FREE TRIAL SolarWinds has a wide variety of features, each of which can assist in enhancing the security posture of your firm and reducing the likelihood of insider attacks coming from within the organization. Get a 30-day free trial.
- ManageEngine ADManager Plus – FREE TRIAL Many useful features are provided by the software to assist Active Directory administrators and help desk personnel in the process of establishing and managing the organization's very own Active Directory. Start a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL This system security bundle provides file integrity monitoring and user behavior analytics to protect Active Directory and sensitive data stores. Available for Windows Server, AWS, and Azure. Access the 30-day free trial.
- Oracle Identity Management The Oracle Identity and Access Management platform allows for the management of all of the groups, rules, and entitlements.
- Okta Helps enterprises to manage the provisioning and deprovisioning of users without breaking any security protocols.
- OneLogin OneLogin provides multilayer security to individuals and the enterprise using multi-factor authentication.
- Microsoft Azure Active Directory It enables users to access their applications from any location via a single sign-on. Because of this, the user has the authority to use all of the services that have been made available to them by the administrator.
Provisioning is an important part of managing the identity life cycle, from the initial onboarding step all the way through to the last exit. A strategy for user provisioning that has been well designed can help ensure that problems, such as granting or canceling access, do not spiral out of your control. In today's business world, businesses have a critical need for an automated user provisioning technology that can expedite and automate the process of user provisioning.
You can automate the process of adding, updating, and deleting users, as well as managing their access, when you utilize a solution that is designed to automate user provisioning. Managing user profiles and permissions manually are made easier and faster as a result of this feature, which also contributes to an overall improvement in operational effectiveness. Increasing work efficiency and productivity, gaining visibility into user access, and strengthening security are all possible outcomes of implementing user provisioning technologies in an organization.
The following is a list of some of the advantages that come with using user provisioning tools:
- User provisioning systems assist in reducing the impact of human mistakes and manual labor, allowing the IT staff to focus on more significant initiatives and increasing overall productivity.
- It decreases the amount of time and money needed for administrative tasks by utilizing automated processes for user provisioning.
- It only grants access to users when it is necessary to do so. This closes any potential security holes that could be exploited by hackers to get unauthorized access to important organization information.
- In addition, it simplifies the process of complying with regulations by providing on-demand reports that are comprehensive and easily illustrate who has access to which resources and when licenses are set to expire. It provides the administrator with more information to better understand who can use which programs
The Best User Provisioning Tools
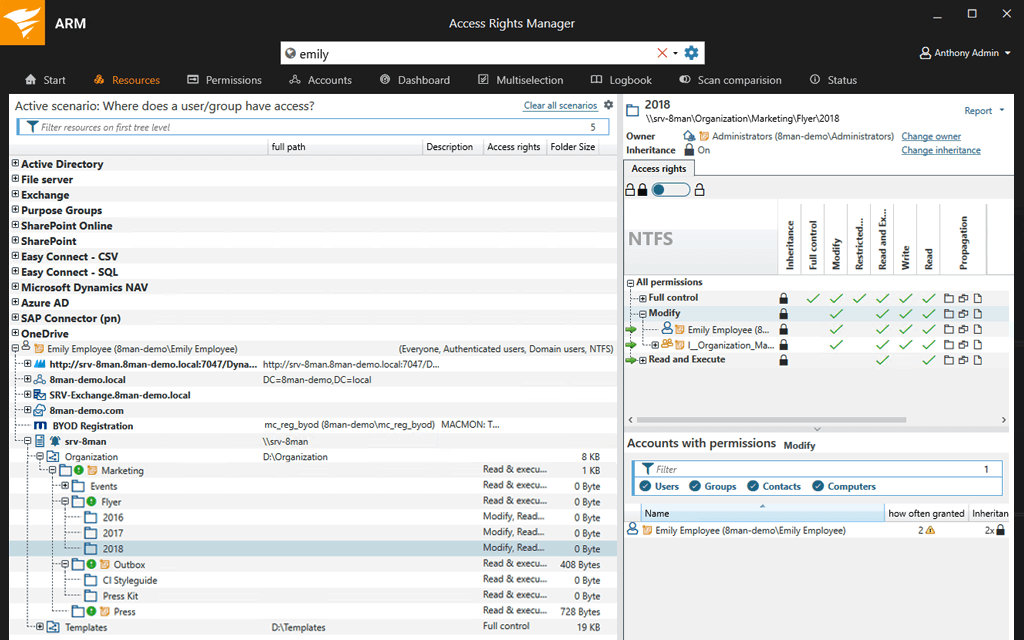
1. SolarWinds Access Rights Manager – FREE TRIAL
The SolarWinds® Access Rights Manager (ARM) software was developed to provide individualized reports from Active Directory (AD) and Azure Active Directory (Azure AD), which detail who has access to what data and when they accessed it. It is responsible for the monitoring and management of user access privileges across your whole IT infrastructure.
Key Features:
- Notifications and alarms in the event of unauthorized changes or access to windows file servers
- Examination of authorizations to access Microsoft exchange
- Manage how users gain access to specific files and services
- Examination of the group's members
It makes it possible to automate certain activities, such as the management and analysis of user access, as well as the enforcement of policies. Audit trails make it possible to identify dormant and questionable accounts and take appropriate action about them.
In addition to this, it helps to prove that your company is compliant and operates by the best practices. Users are granted the ability to easily compile and produce complete reports detailing user access as well as other crucial information for use in audits and reports.
Access Rights Manager is capable of more than just delivering reports; it also provides a straightforward permissions management tool that is straightforward to use. This tool has automated provisioning and de-provisioning capabilities, as well as templates that make it simple to create and remove users. SolarWinds Access Rights Manager comes with a free 30-day trial.
Download: https://www.solarwinds.com/access-rights-manager
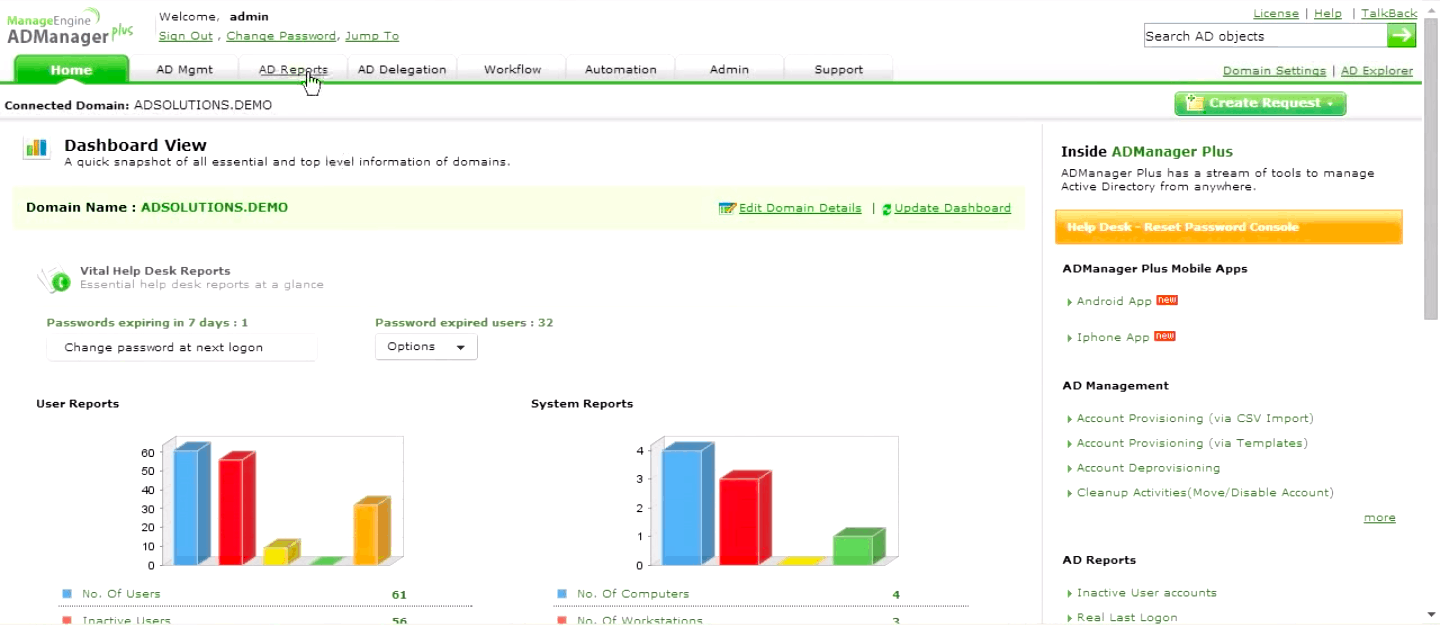
2. ManageEngine ADManager Plus – FREE TRIAL
The Active Directory Management software known as ADManager Plus can be accessed through the web. Many useful features are provided by the software to assist Active Directory administrators and help desk personnel in the process of establishing and managing the organization's very own Active Directory.
Key Features:
- The creation of users in Active Directory (AD), Office 365, Exchange, Skype for Business, and G Suite can all be done in a single step, and the settings may be tailored for each platform
- Facilitates the process of resetting passwords and unlocking accounts through the use of automation
- AD account creation and change based on templates, CSV files, and bulk operations
- Change users' passwords and enable, disable, or delete many accounts at once
- Managing user accounts in the Active Directory, including the creation and modification of accounts
Numerous difficult activities, such as the creation, configuration, and modification of multiple users accounts at the same time (bulk administration), as well as the management of groups and computers, may be carried out effectively and substantially more quickly with the assistance of ADManager Plus. Even for duties that are considered regular, administrators have the option of using automated scripts and delegating AD administrative chores. You will save a significant amount of time on the help desk staff.
The comprehensive reports that are available in ADManager Plus display all of the essential AD settings and attributes, which contribute to the network's increased level of compliance. ADManager Plus makes the use of command line tools and scripts for Active Directory management a thing of the past, allowing administrators to easily manage their directories.
You can start with the 30-day free trial.
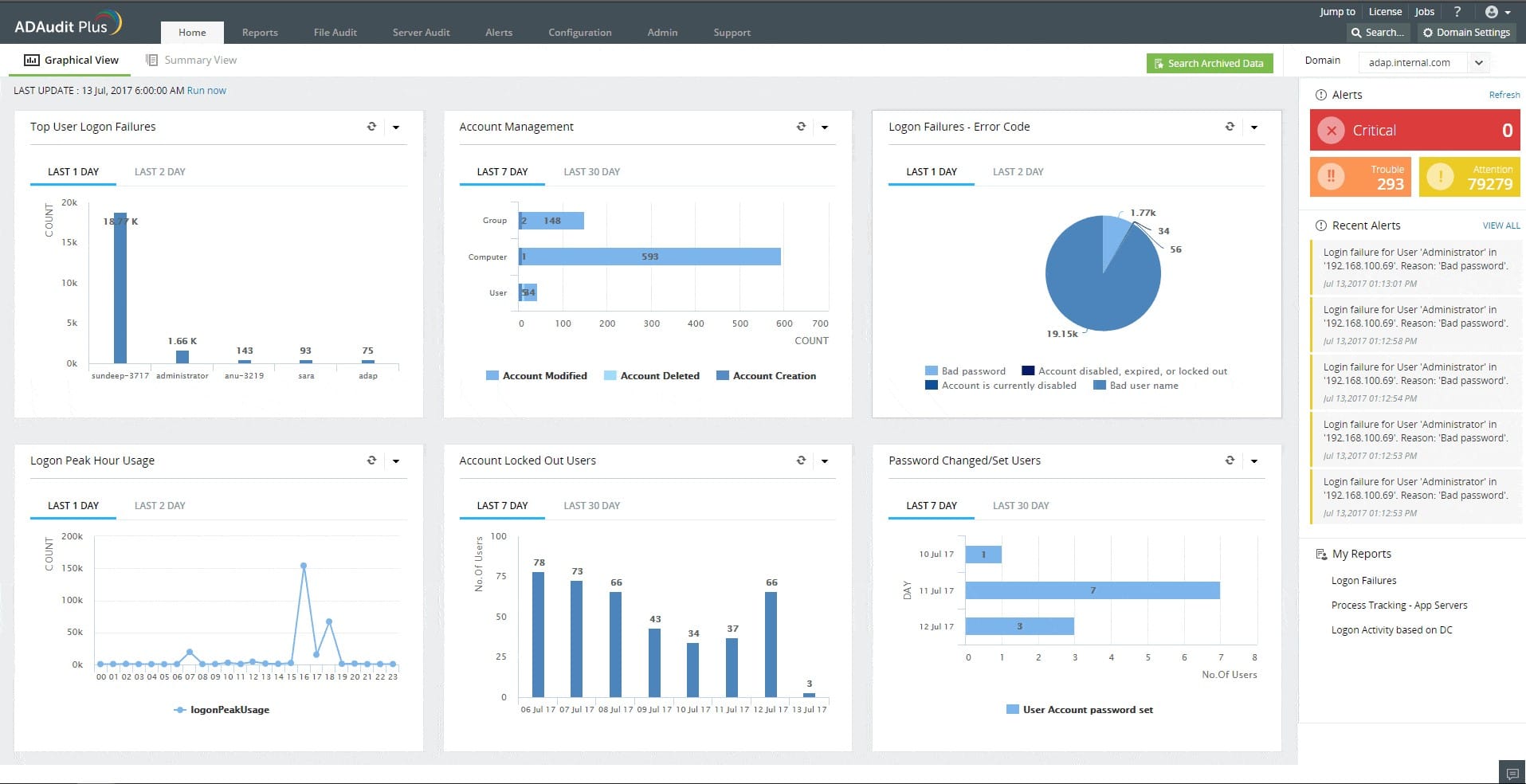
3. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is a data security system that records all of the actions of users when they operate on files. The tool logs each access event and the changes made to files. This is part of a user behavior analytics (UBA) service that is important for data protection standards compliance.
Key Features:
- Collects log files from operating systems and applications
- Records file access events
- Implements compliance auditing and reporting
- Identifies changes to objects in Active Directory
There are two reasons that a user account could be responsible for malicious activity with data, such as theft or tampering – the user is upset, or the user account has been taken over by an intruder. The UBA feature in the ADAudit Plus system gives you an alert if a user account suddenly behaves differently.
By analyzing the activity of each account, you can work out whether an account has been taken over or whether the user has become a threat. Links through to Active Directory data help you generate reports to send to HR for investigation. Meanwhile, ADAudit Plus tracks changes to objects in AD, which could be a sign that a hacker is creating an account.
The reporting tool includes templates for compliance auditing and reporting. The library contains formats that tie in with the regulations of SOX, HIPAA, PCI-DSS, FISMA, GDPR, and GLBA.
ManageEngine offers ADAudit Plus in three editions. The first of these is Free but it is restricted to monitoring 25 workstations and it will only collect log messages. The Standard edition gives you file integrity monitoring and the Professional edition adds Active Directory monitoring and account analysis. You can get the top plan on a 30-day free trial. All versions run on Windows Server and they are also available on AWS and Azure.
4. Oracle Identity Management
Oracle Identity Management gives businesses the ability to manage the whole user identity lifecycle across all company resources, both within and outside of the firewall. Oracle Identity Management allows you to speed up the deployment of apps, apply the most granular level of security to enterprise resources, automatically remove unused access privileges, and do a great deal more besides.
Key Features:
- Oracle Identity Manager's self-service interface lets users change their profiles. Reduces administrative burden and gives users control over identification profiles.
- Oracle Identity Manager's administration interface lets you examine and manage other users' profiles.
- The self-service interface lets customers request fine-grained resource provisioning, profile management, and role membership.
- Oracle Identity Manager's flexible security structure allows delegating most administrative duties to any group or user.
With it, administrators can simply build and manage roles, as well as automate important identity-based controls; once the pieces have been formed and assigned, the tool continues to manage the identities, even as the number of user accounts continues to increase.
Also, employees might easily commit fraud against the organization by issuing themselves bills and paying themselves if they have access to two sets of policies that are opposed to one another (for example, paying and making invoices). In Oracle IAM, a violation is triggered whenever any of these conditions are satisfied. This enables administrators to swiftly delete inappropriate accesses. Every time a user requests specialized access, the system will additionally inquire about a warning signal.
Identity governance provides you with access as well as an efficient structure for managing passwords. Because of a lack of password synchronization, chaos ensues, and the administrator receives hundreds of requests to reset passwords, which leads to administrator overload. You will be able to synchronize and manage the password in a manner that is by the password policy of your business if you implement Oracle Identity and Access Management (IAM).
The Oracle Identity and Access Management platform allows for the management of all of the groups, rules, and entitlements. Users can go to the platform to request an entitlement, and the administrator can view that access and revoke it if necessary.
5. Okta

Organizations can take advantage of Okta's identity and access management services. It assists IT departments in the management of the user authentication process. It provides centralized identities and delivers access to thousands of users, all while keeping the organization's requirements for security and compliance in mind.
Key Features:
- It enables users to sign in to different applications and websites with a single set of credentials, which is referred to as “single sign-on”.
- It supports multi-factor authentication to allow secured access to the users.
- It offers protection for apps running locally as well as those hosted in the cloud.
- It makes the onboarding and offboarding processes completely automated.
- In addition to that, it offers management of API access.
Okta helps enterprises to manage the provisioning and deprovisioning of users without breaking any security protocols. These protocols let users view the data from any device while maintaining their privacy and security. Integration with pre existing directories, identity management systems, and third-party apps is made possible by this feature.
6. OneLogin
OneLogin is a platform for managing identities and access that can be used by companies of any size. It offers a safe, one-click onboarding and offboarding process for users. With OneLogin, when there is a new user, based on their job and responsibilities, they are allowed access to the required applications.
Key Features:
- OneLogin offers single sign-on, which gives each user the appropriate level of secure access to their account.
- It synchronizes the users with your directories and connects with directories such as Active directory, Workday, and Google Workspace, amongst other directories.
- Users can access the organization's apps from any place and on any device, and it enables single sign-on from mobile devices.
- If a user's role has been altered in any way or if they have left the organization, their access should be disabled.
OneLogin provides multilayer security to individuals and the enterprise using multi-factor authentication. It provides real-time account control that enforces access immediately whenever there is any change of roles or any person leaving the organization. It streamlines the procedure for IT teams and end-users.
The open standard for data authentication and authorization known as Security Assertion Markup Language (SAML) is used by OneLogin in its operations. User identities are traditionally stored across several apps, which means that users have to log in individually to each account or program that they need to use at work. This can be a tedious and time-consuming process. These applications can connect thanks to SAML, which enables them to pull trusted security assertions from one application and grant access to another. It provides the foundation for several single sign-on (SSO) products, notably OneLogin, and can be used with web-based applications that are hosted by third parties.
After a user has submitted a request for access to a service provider, the service provider will typically send a request to the identity provider for an authentication assertion. With SAML, the service provider has the power to make judgments regarding access control, including when the service should be performed and whether or not the request should be blocked if it appears to be fraudulent or unlawful. At this point, OneLogin will begin issuing login tokens to the programs that are searching for access. This will eliminate the need for you to repeatedly input your credentials.
7. Microsoft Azure Active Directory
A safe online repository for authentication information, Microsoft Azure Active Directory is capable of housing both individual users and entire groups. Users are provided with a username and a password, both of which are required to log in to an application that makes use of Azure Active Directory's authentication services. Office 365, Dynamics 365, and Azure are all examples of Microsoft Cloud services that use Azure Active Directory as their authentication method. If you have Office 365, then Azure AD is already being used behind the scenes by your organization.
Key Features:
- Strong authentication and risk-based adaptive policies are used by Microsoft Azure to ensure that only authorized users have access to the platform's resources and data.
- It offers a quick sign-in process to keep your users working, cuts down on the amount of time spent managing passwords, and reduces the amount of friction that occurs.
- To improve visibility and control, it centrally controls all of your identities and access to your apps, regardless of whether they are hosted in the cloud or on-premise.
- Through the use of automated identity governance, it ensures that only authorized users can access apps and data for all users and admins in the system.
Microsoft Azure Active Directory is a directory and identity and access management solution that is cloud-based and managed by Microsoft. It enables users to access their applications from any location via a single sign-on. Because of this, the user has the authority to use all of the services that have been made available to them by the administrator. It gives businesses the ability to safeguard account credentials by using stringent authentication procedures and conditional access controls. It offers governance that guarantees the appropriate user gets access to the appropriate resources at the appropriate times, hence fulfilling the requirements for such access.
The goal of Microsoft's Azure Active Directory (AD) is to simplify some of these processes by developing a centralized identity management service that is hosted in the cloud and can be accessed from any device, regardless of the user's location. There is a good chance that you are already utilizing Azure Active Directory without even being aware of it if you make use of Skype, Office 365, OneDrive, or Outlook.
However, Azure Active Directory has a great deal more to offer, including powerful administrative features and the capability to interface with a wide variety of business apps. Azure Active Directory differentiates itself from the competition in the identity and access management (IAM) industry by providing a solution for robust identity management that can be readily connected with other systems, regardless of their size.
SolarWinds Access Rights Manager – Editor’s Choice
SolarWinds Access Rights Manager is our top choice as it works by examining user authorizations and access permissions, you receive a visualization of who has access to what, and when they accessed it. With a few clicks, customized reports may be created to help establish compliance with several regulatory obligations. Provision and deprovision users utilizing role-specific templates to help assure conformity of access privilege delegation, in compliance with security policies.