We may earn a commission if you make a purchase through the links on our website.
The Best VPNs For Enterprises

UPDATED: February 28, 2025
VPNs for enterprises are an essential cybersecurity tool, not only for providing a private browsing experience for employees, but also for interconnecting remote offices and mobile users. An enterprise VPN should be scalable and flexible enough to accommodate a hybrid workforce, and give secure remote access to all employees (regardless of location) to company resources and apps.
This article will go through the best VPNs for enterprises (along with VPN alternatives) with outstanding performance, security, scalability, pricing, and robust features. Not all the products featured here are solely VPNs, but they do perform a more suitable job tailored for the enterprise.
Here is our list of the best VPNs for enterprises:
- Perimeter 81 – EDITOR'S CHOICE Leading secure remote access software provider based on zero-trust architecture. Access the free demo.
- NordLayer – GET DEMO Robust network access solution with various types of VPNs, such as remote access VPNs, business VPNs, and cloud VPNs.
- Twingate – FREE TRIAL Provider of remote access solutions based on zero-trust access controls. It is a fantastic alternative to an enterprise VPN.
- UTunnel – GET DEMO Business VPN package offers a range of plans that provide zero-trust authentication.
- Cisco AnyConnect VPN Mobility VPN client that provides secure access for the mobile and remote workforce to an internal network.
- Fortinet FortiClient VPN Client offers both SSL and IPSec VPN technology (with AES-256 and 3DES encryption) to protect all endpoint data in transit.
- GoodAccess Leading cloud VPN solution with optimal remote access security and access to a global VPN server network.
- Citrix Gateway (formerly NetScaler Gateway) Secure remote access on-premises solution.
- Pulse Connect Secure VPN is a zero-trust secure access-based VPN service.
- Palo Alto Networks GlobalProtect Secure remote access solution (ZTNA) for the hybrid workforce.
- Zscaler Private Access Next-generation and cloud-native ZTNA service —an excellent replacement for a VPN.
Consumer VPN vs. Enterprise VPN
The core function of the enterprise VPN is the same as that of a consumer VPN: establishing a secure virtual tunnel to a remote trusted network across unsecured networks, such as the internet. This core function has various byproducts: removing geographic boundaries, hiding IP addresses, and improving network security. Individual consumers, as well as enterprises, can benefit from these byproducts.
So what are the differences between them?
Individual or home-based VPN consumers are generally looking to hide their IP address or change their geolocation, so they get VPNs with limited capabilities tailored to that type of use. Enterprises, on the other hand, are generally looking for secure remote access to their applications and data, so enterprise VPN services offer the whole package (VPN server-client), including more features, dedicated resources, and more tailored customer support.
- Enterprise VPNs are tailored for business use. It can help enterprises set up a VPN server in the network and allow authorized remote users (employees, partners, suppliers, etc., with VPN clients) access to the network (including apps or data). Another clear distinction is that enterprise VPNs allow multiple user accounts, where all accounts can be managed centrally. An enterprise VPN service also offers access and account management tools to help network admins have a clear view of all users with VPN access. They also get granular access controls for monitoring and managing all user activity and configuring allow/deny access to certain network areas.
- Consumer-grade VPNs are targeted at individuals or small office home offices (SOHO), usually only allowing a handful of users (commonly 1-8) under one account. In addition, consumer-grade VPN also provides the service through shared resources (including IP and server) for various users. Sharing resources usually entails less privacy, speed, and overall VPN performance. Another clear distinction between consumer-grade and enterprise VPNs is that consumer VPNs do not offer site-to-site connectivity.
Factors To Consider When Choosing A VPN For Enterprises
Although you could find more “cost-efficient consumer-grade VPN services” allowing multiple users per account, we recommend using an enterprise VPN service for your company as it provides the right vital business-exclusive features. Consider the following factors when choosing a VPN for your business:
- Scalability An enterprise VPN should be able to scale and accommodate an increasing number of users. If scalability is on your mind, avoid VPN-shared resources at all costs. Scalability also entails management, which should be held through a simple account and access management as networks grow.
- Hosting In many cases, choosing a cloud-based VPN service instead of a self-hosted one is better. A cloud VPN service (through a VPN gateway) offers more convenience when connecting to remote resources. An exception to this rule could be if your industry hosts sensitive data such as health, financial, or military. Specific compliance rules won't allow using any third-party hosting services.
- Security Always choose a VPN with a strong security portfolio regardless of your industry or business size. Strong encryption, two-factor authentication, no-logs policy, and open-source VPN protocols are some of the most vital features. In addition, also consider ZTNA technologies (outside the scope of a VPN).
- Access management Choose a VPN for the enterprise that allows fine granular access controls. Having access to detailed access control levels will give you the flexibility to keep certain network areas (systems, users, apps) secured with policies and filters.
- Site-to-site If your company uses a distributed network; headquarters connecting with multiple remote or branch offices, go for a VPN that offers site-to-site connectivity. This feature installs a VPN server on the headquarters to allow various “off-site” offices to connect via unsecured or public networks (i.e., the internet) through a VPN. This feature is a good replacement for the MPLS approach to WAN.
Why is a VPN not always an optimal solution for an enterprise? Nowadays, a VPN is not the only solution to grant secure access to remote resources. A VPN can fall short when the enterprise's workforce is hybrid (mobile, on-premises, remote). VPNs deployed in such environments may only enlarge the attack surface, as they may “virtually” place the attacker on the network. VPNs may also backhaul traffic (bring internet-targeted traffic back to headquarters and back to the internet), adding lots of latency and delays to third-party cloud-based apps. VPNs, in such cases, won't scale easily and will be costly and complex.
There are alternative technologies (alternatives to VPNs), such as ZTNA, remote access, secure service edge, etc., which will help solve such challenges.
Our methodology for selecting the best VPNs for enterprises
We reviewed the market for the best VPNs for enterprises and analyzed tools based on the following criteria:
- Number of users, user locations, types of devices, bandwidth requirements, security needs, and compliance regulations.
- Comprehensive research on various VPN providers available on the market.
- Reputation, years of experience, customer reviews, and industry recognition.
- Security features such as encryption protocols, authentication methods, data logging policies, and compliance with industry standards.
- Robust and geographically-dispersed network to meet the needs of your organization.
- Ease of use of their client/interface for both administrators and end-users alike.
- Speed tests on each VPN provider's network performance before selecting one with 24/7 support services.
- Scalable VPN solutions to grow and expand according to your organization's needs.
- Licensing models and consider user numbers or bandwidth consumption as part of its pricing scheme.
- Demos or trials so you can gain hands-on knowledge before making your final choice.
- Collaborate closely with your VPN provider to deploy and configure their solution.
- Regularly patch or update any security vulnerabilities or performance issues in their software.
The Best VPNs For Enterprises
The following are the best VPNs for enterprises (and alternatives) that offer the above-mentioned features and provide the most cost-efficient pricing.
1. Perimeter 81 – GET FREE DEMO
Perimeter 81 uses a cloud-based platform (fully managed and hosted) but also an on-premise solution to protect users in any environment, including hybrid. Perimeter 81 provides secure remote access to office resources by restricting network access using zero-trust technology. Perimeter 81 is more than a VPN; it is rather zero-trust access, which also allows you to encrypt traffic with VPN technology such as WireGuard, IPSec, and OpenVPN. Perimeter 81’s business VPN belongs to the integrated SASE solution (along with SD-WAN, ZTNA, and other tools).
Key Features:
- Comprehensive Visibility: Provides detailed and exact user access regulation guaranteeing secured sharing and use of network resources.
- Proactive Monitoring: Known for its ability to continuously monitor network traffic and user behavior as well as to automatically identify and respond to threats, contributing to building a safer environment.
- Combined Software: Combines Software-Defined Perimeter with Secure Access Service Edge to optimize connectivity and security across all environments.
- Artificial Intelligence-Based Monitoring: Used to maintain the health of the network and identify possible future crises before they are high-grade.
Why do we recommend it?
We recommend Perimeter 81 because it encrypts all traffic and protects corporate data from unapproved access and potential breaches. It is equipped with support for IPSec, OpenVPN, and WireGuard protocols and offers zero-trust approaches, which restrict network access, including web applications and cloud environments, for added protection. If you are searching for a VPN tool that offers all-round security, Perimeter 81 is recommended. Ultimately, it offers organizations an additional layer of data protection while simultaneously increasing network security measures.
The solution also offers a single console for account access and management. With this, network admins can control and monitor user access, track network activity and logins, and ensure all VPN clients are up to date — all from a central dashboard.
Who is it recommended for?
Perimeter 81 offers organizations looking for an all-in-one VPN solution an excellent cloud-based option without the hassle and complexity of traditional deployment and hardware requirements. Compatible across Windows, MacOSX, iOS, Android, Linux and Chromebook devices, ensure secure network access via Perimeter 81's cloud infrastructure platform. We highly recommend Perimeter 81 as an ideal modern VPN alternative if you are a business that wants to manage remote access without complicated deployment strategies or lengthy hardware requirements.
Pros:
- Collection of Security Tools: Offers a wide array of security tools in one platform, including network, endpoint, and cloud security.
- Quick Setup: Cloud-based nature allows users to set up and deploy quickly.
- Automatic Protection: Protects users automatically when they connect to new Wi-Fi networks.
- Suitable for Handling Multiple Businesses: Manage multiple businesses or departments using this tool.
Cons:
- Expensive for organizations with a Limited Budget: users with small businesses or startups find this tool costly to use.
Price and Demo: Perimeter 81 is available through Essential ($8/user/month), Premium ($12/user/month), Premium Plus ($16/user/month), and Enterprise (contact Perimeter 81). Perimeter 81’s VPN is available in all plans except Essential. Request a demo.
2. NordLayer – GET DEMO
NordLayer (previously known as NordVPN Teams) is considered the business-class extension of the popular consumer-grade NordVPN service. NordLayer, however, focuses on the entire network access spectrum (SASE), including VPN, access control, and other features. When it comes to the VPN for the enterprise, NordLayer offers various solutions to suit your needs, including Remote Access VPN, Business VPN, and Cloud VPN.
Key Features:
- Automatic Blocking Feature: Automatically restricts access to untrusted websites and users, protecting against malware, ransomware, and other threats.
- Effective Cloud Migration: Establishes functionality through support on the big cloud service providers, with cloud migration done more securely and simply.
- AI-Generated Threat Detection: Embraces AI-generated threat detection robot whose purpose is to spot malware and eliminate it before the virus gets to the network.
- Adjustable Bandwidth: Instantly readjusted, and even the bandwidth and resources that are completely reserved so that the team size increases, enabling the perfect performance.
Why do we recommend it?
NordLayer is highly recommended because of its straightforward installation process and zero additional hardware requirements, which are perfect for businesses that constantly evolve. NordLayer ensures your online connections stay safe when browsing from remote work setups, helping ensure data remains protected while browsing remotely. Furthermore, it serves remote teams well by making sure everyone can work together efficiently and safely.
As with any enterprise VPN, NordLayer also offers industry-standard AES-256 encryption, along with other vital features like auto-connect, tracker blocking, kill-switch, unlimited bandwidth, and access features like SSO and 2FA. Enterprises can also leverage NordLayer’s central management dashboard, where network admins with dedicated manager accounts can create accounts, control access permissions, monitor activity, and generate detailed reports about users.
Who is it recommended for?
NordLayer is ideal for businesses that need to secure and control remote workforce access to internal company resources. It is helpful for IT admins to easily control and customize access permission, ensuring employees can safely connect from any location with all resources needed from within their organization. Furthermore, NordLayer supports clients looking for compliance certifications by offering technological solutions that meet regulatory requirements – regardless of whether your organization is a small startup or a large corporation, NordLayer provides the tools and support necessary for increasing cybersecurity and regulatory compliance efforts.
Pros:
- Intuitive Interface: Designed to be intuitive, even for those without technical expertise, making VPN management simpler.
- Scalable According to Business Size: Adapts to business size changes, making it ideal for growing companies.
- Strong Encryption Methods: Includes strong encryption and two-factor authentication to safeguard data.
- Budget-Friendly Price: Competitive pricing makes it accessible for businesses on a budget.
Cons:
- Lacks Detailed Settings: May not offer enough detailed settings for larger enterprises with complex needs.
Price and Demo: NordLayer is available in different subscription plans, including Basic ($7 user/month), Advanced ($9 user/month), and Custom (contact NordLayer). Prices are yearly. You can see the product in action by scheduling a demo.
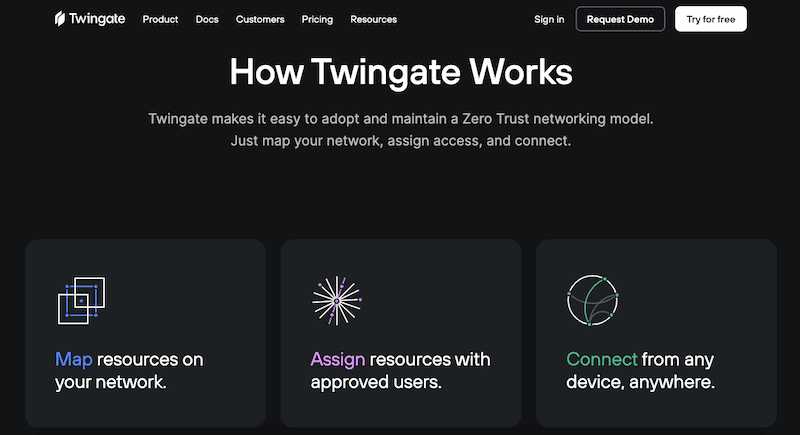
3. Twingate – FREE TRIAL
Twingate is a provider of security solutions based on zero-trust access controls. They provide an outstanding enterprise-grade remote access solution for mobile workers to access corporate resources without compromising network security. Twingate is a fantastic alternative to an enterprise VPN, as it also provides secure access to internal and sensitive resources.
Key Features:
- Network Segmentation: Implementation of network segmentation guarantees every application connection is holistically cylindered, offering massive security with lateral movement risks.
- Robust Security and Access: Assures secure access to organizational assets like files, servers, and gateways using a coordinated system of connectors, controllers, relays, and apps.
- Machine Learning: Analyzes user activity patterns and spots anomalies, enhancing threat detection and response.
- Use of Robust Mobile Applications: Effective and robust mobile applications, aiming at having a secure access environment for mobile employees working from home or from a remote place.
Why do we recommend it?
Twingate is easy to set up, taking less than 15 minutes to ensure everything runs smoothly. Twingate saves hours in maintenance tasks by enabling precise assignment of access levels for employees, contractors, and vendors, so only those needing access receive it. Plus, it offers enhanced visibility so you can easily track who is using company resources or any unusual activity quickly – streamlining security while improving efficiency seamlessly.
Twingate employs an easy-to-deploy Zero-Trust Network Access (ZTNA) solution. It allows admins to keep up a zero-trust networking model on all their access. It maps all resources in your network, assigns them to any approved users, and allows them to connect anywhere and from any device.
Who is it recommended for?
Twingate is ideal for businesses that seek secure remote access without public subnets or risky port forwarding, whether their network is hosted in the cloud, on-premises, or even home networks. Twingate seamlessly integrates with identity provider tools as well as device inventory tools, enabling easy provision/revoke access control using user directory/device inventory systems. It is an essential solution for organizations prioritizing secure, flexible, yet centralized remote access management.
Pros:
- User Verification: Enhances network security by treating all users as potential threats until verified.
- Easy Integrations: Easily integrates with existing tech stacks, minimizing disruption.
- Highest Optimal Performance: Designed to maintain high performance and speed despite encryption processes.
- Modern UI: Provides a clean and modern UI that enhances user experience.
Cons:
- Lack of Advanced Options: As a relatively new player, it might lack some features found in more established solutions.
Price and Trials: Free, Teams ($5 user/month), Business ($10 user/month), Enterprise (contact sales). To start with the free version, create an account. You can also register to Twingate to start a 14-day free trial of Teams or Business.
4. UTunnel – GET DEMO
UTunnel is a secure and scalable VPN service designed for businesses that need reliable remote access and advanced network security. The service can provide site-to-site secure links and also remote access protection for distant workers.
Key Features:
- Zero Trust Security continuously verifies users and devices before granting access
- Adaptable to meet business requirements
- Compatible with Windows, macOS, iOS, Android, and Linux devices
- Provides dedicated IP addresses for improved security and stable connections
- Easy-to-use dashboard for managing users, security policies, and connections
Subscribers can access hosted VPN servers or install their own on their premises or cloud accounts. UTunnel caters to companies looking to protect sensitive data and ensure secure communication for remote teams. The platform supports a range of devices and operating systems. Strong encryption, DNS leak protection, and a customizable configuration help businesses safeguard their data, ensure secure communications, and comply with stringent security policies.
Price and trial: UTunnel offers three plan levels, all are priced per user. There are Basic for $6 per month, Standard for $8 per month, and Custom, which is priced by negotiation. Both Basic and Standard cater to teams with between 5 and 50 members. Schedule a free demo.
5. Cisco AnyConnect
Cisco AnyConnect VPN is a mobility client that provides secure access for mobile and remote employees to an internal organization’s network and resources over the public network. Cisco AnyConnect is quite popular for its stable connection and high speed, even when multiple devices are connected simultaneously.
Key Features:
- Advanced Analytics: Predicts network issues based on rising trends and historical data.
- Secure MFA Options: Offers more flexible and secure MFA options to accommodate diverse enterprise needs.
- Intuitive Dashboard: Provides a consolidated dashboard for managing all connected devices and applications, enhancing security oversight.
- Advanced Encryption Technologies: Uses cutting-edge encryption technologies to ensure data is protected across all transmitted networks.
Why do we recommend it?
Cisco AnyConnect VPN is recommended by many experts, and we suggest this tool as it is the market leader when it comes to enabling and protecting remote work. Their comprehensive suite of products, from digital conferencing tools to internet access security, safeguards organizations' communications. Their policy-driven VPN solution, AnyConnect, ensures secure network access for remote workers across wired, wireless, and VPN connections while offering complete visibility into network usage.
Cisco AnyConnect VPN is suitable for businesses that rely on a significant remote workforce. The solution provides a central endpoint security console for allowing network admins to configure remote access controls and VPNs. This single management portal allows admins to check who is accessing the network and tracks the activity. When it comes to VPN technology, Cisco AnyConnect offers robust encryption mechanisms, such as AES-256 and RSA-4096, and high-end security protocols, including SSL and IKEv2, to encrypt the data in transit.
Who is it recommended for?
This tool meets the demands of organizations of all sizes seeking a secure yet flexible means for remote access to network resources. It is suitable for businesses that rely on remote or mobile workers and multiple office locations that require secure links between offices. AnyConnect is ideal for sectors requiring strict security, such as healthcare, finance, or government, as well as enterprises looking for comprehensive VPN solutions complete with policy-driven access controls and central management capabilities.
Pros:
- Highly-Reputed Tool: Backed by Cisco's long-standing reputation in the industry.
- Multi-OS Compatibility: Works seamlessly across Windows, macOS, Linux, and mobile devices.
- Offline Protection: Provides persistent protection, even when users are offline.
- Logs and Reports: Offers extensive logs and reports for network administrators.
Cons:
- Most Users Need IT Support During Setup: Can be challenging to set up and manage without adequate IT support.
Price and Trials: To find out more about Cisco AnyConnect pricing, contact the Cisco sales team via Email or schedule a call with sales. You can also register with Cisco to get a 30-day evaluation of AnyConnect.
6. Fortinet’s FortiClient VPN

Fortinet FortiClient is an advanced endpoint security solution that offers endpoint protection, endpoint compliance, remote access control, Zero Trust Network Access (ZTNA), and a built-in VPN client. Fortinet FortiClient VPN offers both SSL and IPSec VPN-based clients (with AES-256 and 3DES encryption) to protect all endpoint data in transit.
Key Features:
- Advanced Endpoint Protection: Combines VPN access with advanced endpoint protection capabilities to guard against malware and other threats.
- Tests for Malicious Objects: Allows files and applications to be tested in a safe environment to prevent malicious software from entering the network.
- Updated Security and Compliance: Ensures all connected devices are up to date, and are in accordance with the latest security patches and updates.
- Multiple VPN Servers: Users can chain multiple VPN servers for enhanced privacy and security.
Why do we recommend it?
FortiClient VPN is recommended because of its advanced security features and intuitive management, including SSL/IPSec VPN protocols that ensure secure remote access from any location to organizational networks. It can be easily integrated and deployed, while real-time central management through an Enterprise Management Server (EMS) streamlines administration tasks. Admins can configure VPN settings, monitor attack surfaces, manage vulnerabilities, enforce compliance, and track changes from one centralized location, simplifying network management while strengthening security posture. In addition, remote deployment capabilities help expedite onboarding processes when new employees are onboarded into organizations.
This solution also provides secure remote access via Multi-Factor Authentication (MFA) for both SSL VPN and IPSec VPN. To enable centralized management of endpoints (including VPNs), FortiClient provides the Endpoint Management Serves (EMS), where admins can monitor access details, enforce policies, and allow or deny any location or device.
Who is it recommended for?
This tool can be used by a wide range of industries, including finance, government, healthcare, or IT, that need secure access to their organization's network from any location – be it home or away. Thanks to its two-factor authentication process, you can trust that your connection is safe. Furthermore, FortiClient works quietly in the background so as to minimize interruptions while remaining protected. FortiClient doesn't just protect VPN connections either – its two-way protection shields Microsoft Office apps and PDF readers from exploits as well as monitoring for vulnerabilities across systems and apps in real time. Admins can also find patch management simple with its central management console.
Pros:
- Security Integration: Part of the Fortinet ecosystem, offering broader security integration.
- Automation: Utilizes automation to identify and respond to threats quickly.
- Detailed Controls: Users can use detailed controls for web content filtering.
- Free Version Available: Provides a robust free version suitable for many small businesses.
Cons:
- Poor UI and Graphics: Some users find the interface less intuitive compared to competitors.
Price and Editions: You can download FortiClient’s VPN-only version for free (without support). But to get the full FortiClient VPN (with support), you’ll need to get in touch with the FortiClient team and look into the (full ZTNA edition). You can also request a free product demo to see the product in action.
7. GoodAccess
GoodAccess is a market-leading cloud VPN solution with a fantastic remote access solution. Although GoodAccess is explicitly designed for SMBs, it has fantastic scaling potential for larger businesses. GoodAccess uses IKEv2 and OpenVPN with strong encryption (AES-256 bit) to protect your network traffic from external threats. In addition, it also brings useful VPN features like public Wifi protection, branch connectivity, and port forwarding.
Key Features:
- Cloud-Native Firewalls: Easily interacts with current cloud-native firewalls, increasing security without adding complexity.
- Real-Time Threat Assessments: Automatically updates access controls based on real-time assessments of threats and user behavior.
- Detailed Reports: Offers tools to easily generate detailed reports for compliance with industry regulations.
- Scalable: Expands its network edge closer to users for reduced latency and improved performance.
Why do we recommend it?
We suggest GoodAccess because it is a simple, 100% Software-as-a-Service platform that allows remote access to resources while protecting users, apps, and networks. It enables organizations to quickly establish a VPN connection by connecting to a gateway located anywhere in the world. GoodAccess provides secure and efficient remote access for enterprises of all sizes by including features such as static IP whitelisting, a secure web gateway against online threats, split tunneling for traffic control, and robust encryption.
GoodAccess offers decent global coverage with 35 different global server locations, which is low compared to other more popular VPNs. But, the difference is that you can instantly deploy a private “virtual” gateway anywhere with a dedicated and static IP address and assign it to your team, and they will get instant fast connections. In addition, GoodAccess provides a global virtual network in the cloud (Cloud VPN) and connects to remote sites without any hardware or old WAN technologies like MPLS.
Who is it recommended for?
GoodAccess VPN is proven helpful to all business sizes who always needs secure remote access. This enterprise is ideal for small businesses, startups, remote teams and IT administrators – as well as IT admins and cybersecurity specialists – looking for an easy-to-use remote access security and compliance solution. Cybersecurity experts and network admins alike appreciate its value when managing remote teams or protecting company data. With GoodAccess you can rest easy knowing your connections are safe and your data protected.
Pros:
- Suitable for Non-Tech Users: Aimed at non-technical users, it's easy to configure and use.
- Dedicated Static IP: Each subscription comes with a dedicated static IP.
- Affordable Plans: Offers cost-effective plans for small to mid-sized businesses.
Cons:
- Lacks in Advanced VPN Functions: Users find a lack of some of the advanced functionalities of more comprehensive VPN solutions.
Price and Trials: GoodAccess offers four different editions: Starter (Free), Essential ($4/user/month), Advanced ($8/user/month), and Premium ($10/user/month). All these plans are billed annually. To get a 14-day free trial with all premium features, create a free account right now.
8. Citrix Gateway

Citrix Gateway (former NetScaler Gateway) is a secure remote access on-prem solution. It is a cybersecurity appliance (physical or virtual) that provides a secure access point for remote employees to access apps and resources. It acts as a proxy, securing all traffic, including Citrix Workspace traffic, with the SSL/TLS encryption standard. Citrix Gateway (leveraging ZTNA technology) is a great alternative to an enterprise-level VPN.
Key Features:
- Tailored Access Based: Provides tailored access based on user context, enhancing security without sacrificing user experience.
- Single-Interface Access: Consolidates access to all apps (both in-cloud and on-premise) through a single interface, simplifying user access.
- Risk Session Recording: AI is used to selectively record sessions that exhibit risky behavior, improving oversight and compliance.
- Isolated Web Browsing: Keeps web browsing isolated from internal networks, protecting against browser-based threats.
Why do we recommend it?
Citrix Gateway includes robust security features and guarantees to deliver a user-friendly experience. You don't have to worry if your password is cracked; it has two-factor authentication which will put an extra layer of protection against hackers and keeps your account secure. You also don't need to do repeated logins because it has single sign-on access for all applications, which will eliminate the hassle of repeated logins. With role-based access, you can control access by allowing and blocking it.
Citrix Gateway provides a VPN solution based on SSL, giving users full “clientless” access to internal network resources using their browser. It is usually best deployed in a DMZ and can be installed with multiple instances. It offers both solutions, either a full tunnel VPN or clientless VPN access, giving users different ways to access resources securely, including applications or data deployed on-premises or in the cloud.
Who is it recommended for?
Citrix Gateway is an essential solution for anyone needing remote desktop access via mobile devices, particularly active client relationships. Citrix Gateway makes an especially strong case when working across time zones to access work resources seamlessly from anywhere—eliminating physical office presence as necessary. IT and remote work experts trust Citrix Gateway to keep teams productive regardless of physical proximity.
Pros:
- Manages Virtual Desktops and Apps: Exceptional at managing secure access to virtual desktops and applications.
- Control-Based Access: Provides flexible access control based on user context.
- Compatible to Use with Various OS: Supports a wide range of devices and operating systems.
- Powerful Monitoring and Analytics: Includes powerful monitoring and analytics tools.
Cons:
- Lots of Features Could Confuse Inexperienced Users: Its wide array of features can make it daunting for new users or small IT teams.
How to start with Citrix Gateway?
Locate a nearby partner or contact Citrix’s customer service.
9. Pulse Connect Secure VPN
Pulse Connect Secure (now Ivanti Connect Secure) is an endpoint secure access solution for enterprise applications running on-premises or in the cloud. Pulse Secure has a fantastic range of products, including Pulse ZTNA, Pulse Policy Secure, Pulse Virtual Traffic Manager, and Pulse Connect Secure (a Zero Trust Secure Access-based VPN).
Key Features:
- Virtual Desktop Environment: Provides immediate, secure remote desktop access with disparate functionality through a feature-rich virtual desktop environment for teleworkers.
- Thorough Compliance Check: Compliance check on the devices is performed, and the network access is only given after granting the network securing device breaches.
- Automatic Error Repairing: Automatically repairs the connectivity errors detected at the user connection stage.
- Comprehensive Web Control: Gives full controllership web portal for users, allowing a company to maintain its branding and user experience.
Why do we recommend it?
Pulse Connect Secure is now Ivanti Connect Secure, which can help you with an excellent cost-cutting option with its drag-and-drop design that simplifies workflow creation and user interface design, automating processes to reduce total cost of ownership while streamlining operations to reduce ticket resolution time while expanding team capacity without additional staff requirements. Organizations looking to optimize resources while increasing productivity without breaking their budget should consider Ivanti Connect Secure as a cost-efficient solution.
The Pulse Connect Secure platform provides all remote and mobile employees with a secure, private SSL-VPN connection to the company's network via a ZTNA solution. Employees can access remote resources anytime using a web-enabled device through the Secure Unified Client. Pulse Connect Secure also gives system admins a centralized management and visibility platform to manage policies, track users and devices, and monitor all the state and access activity.
Who is it recommended for?
Pulse Connect Secure is an ideal remote access solution for organizations, offering personalized self-service portals tailored to each user's specific needs and enhancing their experience and satisfaction. IT administration and cybersecurity specialists benefit from its omnichannel engagement capabilities, which allow employees across various industries quick resource access. By increasing Net Promoter Scores (NPS) and satisfaction (xSAT), Pulse Connect Secure ensures seamless connectivity and increased productivity within teams spanning various industries.
Pros:
- Fulfills Security Standards: Ensures that all devices meet security standards before network access is granted.
- Environment Compatibility: Works well in environments with both cloud and on-premises components.
- In-Depth Access Control: Offers detailed control over who accesses what within the network.
Cons:
- Unsatisfied with the UI: Users have reported that the interface is somewhat outdated and clunky, impacting the user experience and productivity.
Price and Trials: Start a Free Trial of the Ivanti Connect Secure VPN. You can download the full Ivanti Connect Secure Virtual Appliance server (free trial for a limited time) and test it with the free Secure Unified Client. For pricing information, contact sales.
10. Palo Alto Networks GlobalProtect
Palo Alto Networks GlobalProtect is a secure remote access solution for the hybrid (distributed, on-premise, or mobile) workforce. It extends the security from Palo Alto Networks Prisma and Access and NextGeneration Firewalls to all these users. This platform is a full ZTNA solution (more than an enterprise-grade VPN solution). It provides not only secure ‘clientless’ access for this hybrid workforce to their corporate network but also gives admins a broad visibility into the network’s activity. GlobalProtect also allows admins to understand application usage, identify traffic’s “top talkers,” and enforce security policies.
Key Features:
- Behavioral Analysis: Machine learning is used to recognize malevolent traffic behavior and automate behavior replies.
- Discrete Traffic Control: Allows an admin to have more discrete control over traffic transmitted through the VPN, increasing the throughput and performance.
- Automatic Security Updates: Automatically update settings according to the applied security posture on the network.
- Superior Vulnerability Protection: Provides a set of protection mechanisms for IoT devices connected to a network that are meant to bring about superior protection from single points of vulnerability of IoT.
Why do we recommend it?
Palo Alto Networks GlobalProtect is our top recommendation due to its robust security features. It allows users to securely connect to networks using either SSL or IPsec VPN connections and is supported by next-generation firewall capabilities, with load distribution across portals and gateways to manage heavy traffic efficiently. It features user and device identification along with multi-factor authentication for admins and provides advanced firewall insights, ensuring secure access across various devices, making GlobalProtect an excellent choice for organizations prioritizing network security and user privacy.
When it comes to the VPN connection, GlobalProtect provides a clientless SSL or IPsec VPN for secure access to resources and sensitive data in the cloud or data center. It can also protect mobile devices with a per-app VPN on Android or iOS devices.
Who is it recommended for?
It is used as a useful asset for organizations seeking to secure network access on mobile devices running Android or iOS systems, particularly from teams spread out over different time zones or with flexible work hours, enabling employees to stay in contact with clients and partners even outside normal office hours. IT administrators appreciate its ease of deployment and configuration – accessible both to technical as well as non-technical users – making sure connectivity and productivity remain secure across diverse work environments.
Pros:
- Corporate Security Policy: Extends the corporate security policy to all users, regardless of location.
- Easy VPN Connection: Allows devices to connect to the VPN before user login, enhancing security.
- Uses Machine Learning for Robust Security: Leverages machine learning for dynamic security enforcement.
- Offers Fast Speed: Ensures optimized connection speeds worldwide.
Cons:
- Resource Dependant: May require significant resources to run optimally, which could impact older systems.
Price and Trials: Palo Alto offers custom pricing depending on the subscription, as well as the period, number of devices, and features. Contact a sales rep to get a quote. Unfortunately, there is no free trial available, but you can schedule a live demo to see how the product (specifically SASE and SSE Prisma Access) works in action.
11. Zscaler Private Access
Zscaler is a leader in SSE (Secure Service Edge) and zero-trust technology for cloud security. Their popular product is their Zero Trust Exchange (ZTE)— a cloud-native platform designed to protect enterprises on their cloud migration journey. Zscaler’s ZTE technology covers protection for all its products, including Zscaler Private Access (ZPA).
Key Features:
- Cloud-Native Cloud Access Security Broker: Cloud-native Cloud Access Security Broker (CASB) for unified security without the need for on-premises hardware.
- Real-Time Threat Emulation: Employs real-time threat emulation that comes in handy in blocking any of the malicious materials from the portal.
- Micro-Segmentation: Includes micro-segmentation based on the specific identity of each end user, thereby offering increased protection to the whole perimeter.
- Premium Cloud Infrastructure: Connected with users worldwide to be able to scale as needed without compromising performance or security.
Why do we recommend it?
Zscaler Private Access (ZPA) offers organizations seeking seamless and comprehensive security solutions, such as a zero-trust cloud-based solution, to secure connections between remote devices and private applications. Through ZPA's zero trust approach, applications remain inaccessible to unauthorized users as they're never exposed to the internet – this includes managed and unmanaged devices alike and not just web apps. It supports both managed and unmanaged devices while protecting connections to all kinds of private apps, not just those on the web.
ZPA is a next-generation and cloud-native ZTNA service, an excellent replacement for a VPN in an enterprise environment. ZPA gives remote users secure access to private applications and data using the least privilege approach. This eliminates any unauthorized access or lateral movement attacks.
Who is it recommended for?
Zscaler Private Access is essential for organizations that prioritize granular control and security over their network, especially businesses aiming to reduce ransomware spread by allowing users to access specific private apps without accessing all of them. Administrators have extensive control through the ZPA management portal, which enables them to create policies, select applications associated with them, and configure permissions precisely down to individual user and application levels – giving administrators complete oversight while improving overall network security.
Pros:
- Secure Cloud Access: Built from the ground up for secure cloud access without traditional VPN limitations.
- Highly Scalable: Cloud-based infrastructure makes it easy to scale up or down as needed.
- Optimal Performance: Designed to provide secure access with minimal impact on performance.
- Provides Seamless Integrations: Offers tight integration with Zscaler's security services for added protection.
Cons:
- Dependent on Stable Internet: Being fully cloud-based, Zscaler Private Access needs a stable and fast internet connection to function effectively.
Price and Trials: Pricing for ZPA is not listed on Zscaler’s official site, so you will need to request a quote. Unfortunately, there are no free plans or free trials available, but you can request a Zscaler demo.