We may earn a commission if you make a purchase through the links on our website.
Cloud Compliance Guide

UPDATED: June 11, 2024
This guide provides a comprehensive overview to ensure you remain within compliance regulations while operating in the cloud.
Cloud compliance is becoming increasingly critical as more firms shift their activities to the cloud. Cloud compliance guarantees that enterprises satisfy regulatory standards and best practices for cloud data and infrastructure security. Failing to comply with these criteria can result in serious consequences such as legal penalties, loss of revenue, and reputational damage to the firm.
The goal of this article is to provide an overview of cloud compliance as well as practical tips for achieving cloud compliance. The guide is divided into sections, each of which covers a different area of cloud compliance.
Cloud Compliance Basics
When businesses put their data and apps in the cloud, they frequently confront regulatory and compliance issues. Compliance refers to adhering to legal, regulatory, and industry-specific data protection and privacy standards. Failing to comply with these requirements can result in severe fines and legal ramifications.
Organizations must understand the fundamentals of compliance rules and frameworks to achieve cloud compliance. Compliance standards differ depending on the industry, the type of data held, and the location of the data. Compliance standards such as SOC 2, HIPAA, PCI DSS, and ISO 27001 are some of the most widely used frameworks for assuring data security and privacy.
It is critical to recognize that compliance is a continuous process that necessitates continual monitoring and adherence to regulations. Compliance requirements evolve over time, and firms must stay current on the most recent regulations to ensure compliance.
Understanding the shared responsibility arrangement between the cloud service provider (CSP) and the customer is another critical part of cloud compliance. Customers are responsible for safeguarding their data and applications in the cloud, while CSPs are responsible for guaranteeing the security of the cloud infrastructure. As a result, it is critical to understand the CSP's security policies and to apply additional security measures to secure the data and apps.
Securing cloud-native applications is also part of cloud compliance. These apps are often constructed with a microservices architecture and are intended to run on cloud platforms. As a result, they necessitate distinct security measures from standard applications. Companies must ensure the security and compliance of their cloud-native apps.
Cloud access security brokers can assist enterprises in meeting compliance requirements (CASBs). CASBs offer a variety of security features that enable businesses to monitor and secure their cloud environments. Data loss prevention, threat protection, access control, and compliance reporting are examples of these measures. Organizations can also utilize compliance as code to automate compliance operations. Compliance as code entails writing code that establishes compliance criteria and examines the cloud environment for compliance violations automatically. This method assists organizations in maintaining compliance while lowering the possibility of human mistakes.
Finally, organizations must conduct frequent compliance audits and reporting, guaranteeing that they comply. Compliance auditing entails examining security controls and processes to guarantee their effectiveness, whereas compliance reporting is supplying regulatory agencies with evidence of compliance.
Compliance Frameworks and Regulations
Guidelines for safeguarding data security and privacy in the cloud are provided by compliance frameworks and regulations. Depending on the business, region, and type of data held, enterprises must follow a variety of frameworks and regulations. Some of the most often utilized compliance frameworks and regulations are as follows:
- SOC 2 A framework that provides guidelines for security, availability, processing integrity, confidentiality, and privacy of data. It is designed for service providers that store customer data in the cloud. SOC 2 reports can help organizations assess the effectiveness of their security controls.
- HIPAA A regulation that applies to organizations that handle protected health information (PHI). It requires organizations to implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of PHI.
- PCI DSS A framework that applies to organizations that handle credit card information. It provides guidelines for securing cardholder data and requires organizations to implement security controls such as encryption and access control.
- GDPR A regulation that applies to organizations that store or process the personal data of individuals in the European Union (EU). It requires organizations to obtain explicit consent from individuals before collecting their data and provides guidelines for securing and protecting personal data.
- CCPA A regulation that applies to organizations that store or process the personal data of California residents. It requires organizations to provide consumers with the right to know what personal data is being collected, and the right to have their data deleted.
- ISO 27001 A standard that provides guidelines for information security management systems. It is designed to ensure the confidentiality, integrity, and availability of information by implementing appropriate security controls.
- NIST Cybersecurity Framework This provides guidelines for managing and reducing cybersecurity risks. It is designed to help organizations improve their cybersecurity posture by implementing security controls, detecting and responding to threats, and recovering from cybersecurity incidents.
Compliance frameworks and rules are always evolving, and firms must keep up with the latest changes. Businesses must also ensure that they have the appropriate documentation and evidence to show auditors and regulatory agencies that they comply.
Furthermore, compliance frameworks and legislation frequently have overlapping requirements, and enterprises must ensure that all applicable criteria are met. This can be a difficult undertaking, and businesses might benefit from employing compliance management software to track and handle compliance needs.
Cloud Service Responsibility
When it comes to cloud compliance, it's important to understand the shared responsibility model between cloud service providers (CSPs) and their customers. In this model, the CSP is responsible for the security of the cloud infrastructure, while the customer is responsible for securing the data and applications they store in the cloud.
CSPs are in charge of the physical security of their data centers, which includes environmental controls, access controls, and monitoring. They are also in charge of safeguarding the cloud infrastructure's network and physical components, such as servers, storage devices, and networking equipment. Using firewalls, intrusion detection systems, and other security measures to protect against external threats is part of this.
Furthermore, CSPs are accountable for the availability and reliability of their cloud services. To minimize downtime and data loss, build redundancy, failover mechanisms, and disaster recovery strategies.
Customers are responsible for securing their own data and apps, while CSPs are responsible for the security and availability of the cloud infrastructure. Implementing access controls, encryption, and other security measures to defend against unauthorized access and data breaches is part of this. Customers must also verify that their apps and data are suitably configured to meet applicable rules and best practices.
It should be noted that the shared responsibility model can differ based on the type of cloud service chosen. In a Software as a Service (SaaS) paradigm, for example, the CSP is responsible for securing the application, whilst the client is responsible for safeguarding their own data. The CSP is responsible for safeguarding the platform and infrastructure in a Platform as a Service (PaaS) model, while the customer is responsible for securing their own applications.
Customers must understand their duties and take proactive efforts to secure their data and applications to achieve cloud compliance. Access controls, data encryption, and monitoring and logging tools are all used to detect and respond to security risks.
To summarize, understanding the shared responsibility paradigm between CSPs and their clients is critical for cloud compliance. Consumers must take proactive steps to safeguard their own data and apps, and they must collaborate closely with their CSP to ensure that their shared duties are met. Organizations may ensure compliance with current standards and best practices, as well as protection against the latest security risks, by establishing best practices and continuously monitoring their cloud environment.
Cloud Access Security Brokers (CASBs)
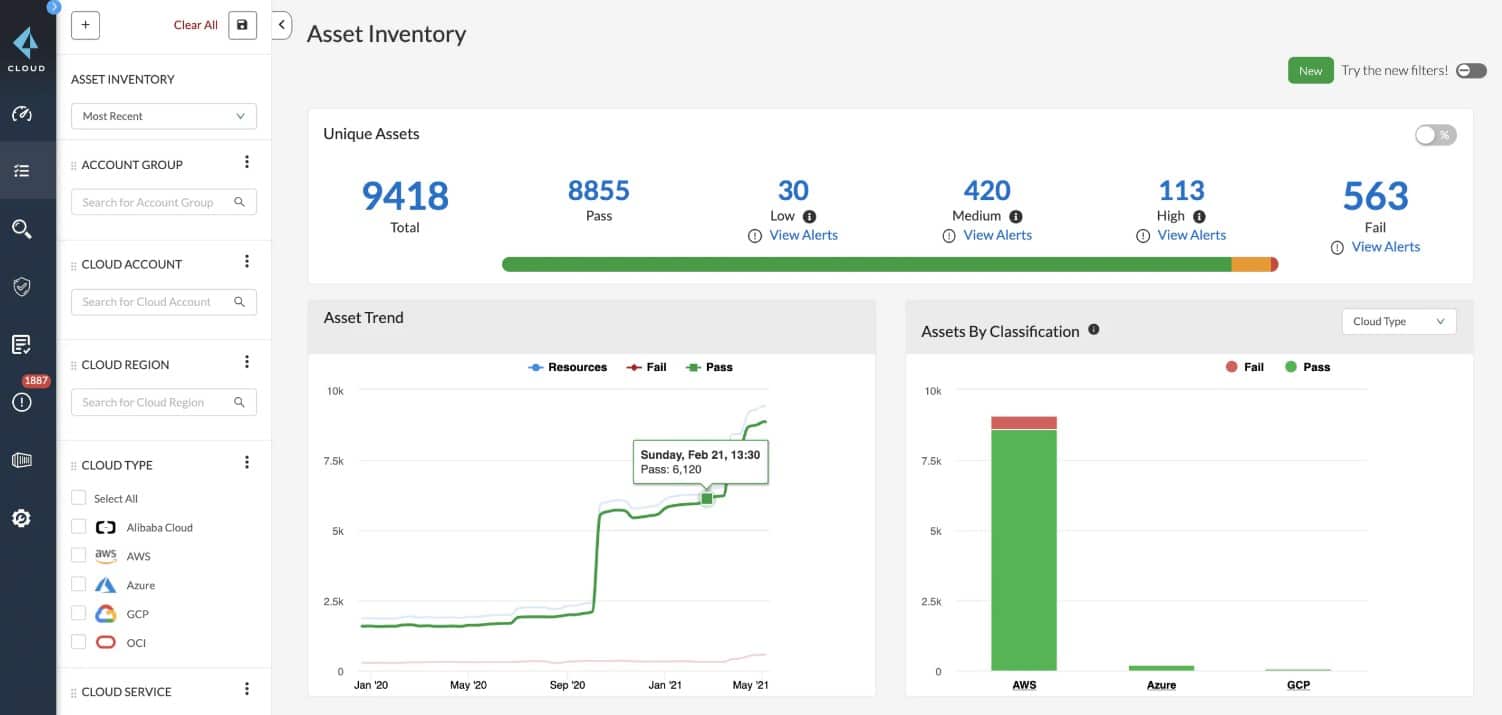
Cloud Access Security Brokers (CASBs) are a form of security solution that gives you insight and control over your cloud-based apps and data. CASBs are meant to meet the particular security difficulties that cloud computing presents, such as the need to encrypt data stored in the cloud and accessed from numerous devices.
Identity and access control, data loss protection, and threat detection are just a few of the security features offered by CASBs. These capabilities assist enterprises in securing their cloud infrastructures and ensuring compliance with relevant legislation and frameworks.
Another significant advantage of employing a CASB is the ability to monitor user activities and detect potential security concerns. CASBs enable enterprises to detect and respond to possible security issues in real-time by providing visibility into user activities in the cloud. This involves identifying and blocking malware and other cyber threats, as well as monitoring for unusual behavior such as multiple failed login attempts.
CASBs can also assist firms in adhering to appropriate legislation and guidelines. Certain CASBs, for example, offer automatic compliance checks and reports to assist firms in ensuring compliance with rules such as HIPAA, PCI DSS, and GDPR. This can assist firms in avoiding hefty fines and reputational damage caused by noncompliance.
- Microsoft Defender for Cloud Apps (formerly Microsoft Cloud App Security) Α type of CASB. This platform has granular access controls, data loss protection, and threat detection among its security features. Microsoft Defender for Cloud Apps works in tandem with other Microsoft cloud services like Azure Active Directory to provide a comprehensive security solution for cloud-based applications and data.
- Cisco Cloudlock Αnother example of a CASB. This platform includes security capabilities such as real-time visibility into user activities, threat detection and response, and compliance management. Cisco Cloudlock works in tandem with other Cisco security technologies, such as Cisco Umbrella, to give a comprehensive cloud security solution.
Cloud-Native Application Security
Cloud-native applications are built to take advantage of cloud computing's scalability and flexibility. This, however, poses additional security challenges for enterprises to solve. Organizations can solve these security concerns by utilizing cloud-native application security platforms (CNAPPs) that are specifically intended for cloud-native apps. These platforms offer a variety of security functions such as vulnerability assessment, threat detection, and compliance management. Cyscale, which provides a comprehensive security solution for cloud-native apps, is one example of a CNAPP.
Cyscale provides several security capabilities, such as container security, microservices security, and API security. It also offers DevSecOps features like automated security testing and continuous compliance monitoring. Cyscale is user-friendly and interfaces with common cloud platforms like AWS and Google Cloud Platform.
CNAPP Options In-Depth
CNAPPs, or cloud-native application security platforms, are platforms that are specifically built to handle the security concerns that cloud-native apps provide. These systems include security features like vulnerability assessment, threat detection, and compliance management.
- Prisma Cloud by Palo Alto Networks An example of a CNAPP. Prisma Cloud offers a comprehensive cloud-native application security solution, including container security, host security, and network security. It also includes capabilities for compliance management, such as automated compliance checks and reporting.
- Aqua Security Provides container security and compliance management for cloud-native apps, and is another example of a CNAPP. Aqua Security delivers capabilities like vulnerability assessment, runtime protection, and network segmentation to protect against cyber threats. Another CNAPP that offers cloud compliance management services, such as automated compliance inspections and remediation, is Cygilant. To deliver real-time compliance monitoring and notifications, Cygilant interacts with popular cloud platforms such as AWS and Azure.
- Cyscale As previously mentioned, Cyscale is a full-service CNAPP that offers container security, microservices security, API security, and compliance management for cloud-native applications. To assist enterprises in securing their cloud-native apps, Cyscale provides DevSecOps features such as automated security testing and continuous compliance monitoring.
Ultimately, several CNAPPs on the market provide a variety of security features and compliance management capabilities for cloud-native apps. These platforms assist enterprises in addressing the specific security concerns offered by cloud-native apps while also ensuring compliance with applicable legislation and frameworks.
Cyscale: Features and Benefits
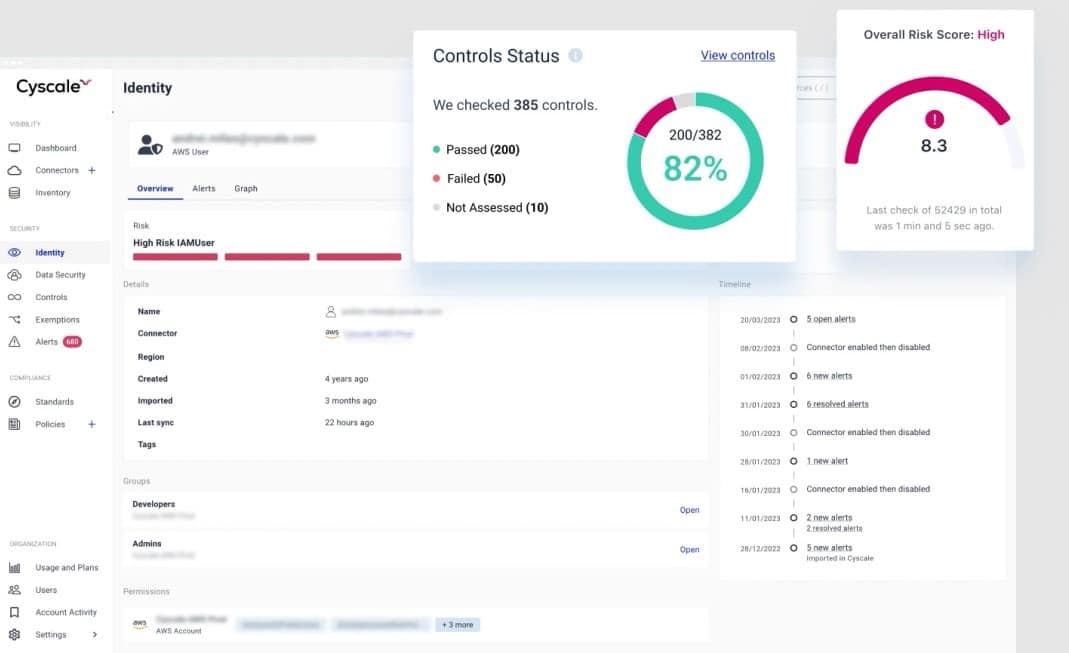
Cyscale is a cloud-native application security platform that offers a complete solution for cloud-native application security. It provides several features and benefits that assist enterprises in dealing with the specific security problems provided by cloud computing.
Cyscale's capacity to provide visibility and control over cloud environments is one of its primary characteristics. Organizations can use Cyscale to discover and assess security threats in their cloud systems, including containers, microservices, APIs, and serverless activities. This enables enterprises to uncover flaws and potential security problems before attackers can exploit them.
Cyscale's automated security testing capabilities are another essential feature. Organizations can use Cyscale to automate security testing across the software development lifecycle, including development, testing, and deployment. This assists enterprises in ensuring the security and compliance of their cloud-native apps with relevant rules and standards.
Cyscale also offers full container security solutions. Organizations can use it to secure container images, monitor container runtime activity, and detect and respond to container-based attacks. This enables enterprises to prevent unwanted access to containerized apps and ensure that only authorized users have access to their data.
In addition to container security, Cyscale delivers microservices security capabilities. It enables enterprises to detect and respond to possible security threats in real time by identifying and assessing security risks throughout their microservices architecture. This aids enterprises in the security of their microservices-based systems and the prevention of unauthorized access to sensitive data.
Cyscale also offers API security features. It allows businesses to safeguard APIs, track API usage, and detect and respond to API-based attacks. This assists enterprises in preventing unwanted API access and ensuring that their data is only accessed by authorized individuals.
One of the most significant advantages of employing Cyscale is its DevSecOps capabilities. Organizations can use Cyscale to incorporate security testing into their DevOps workflows, allowing them to discover and remediate security issues throughout the software development lifecycle. This enables enterprises to deliver secure and compliant cloud-native apps at a faster and larger scale.
Compliance as Code
Compliance as Code is a novel concept that seeks to overcome the difficulties of guaranteeing compliance in fast-paced, cloud-native environments. It entails automating compliance checks and controls with software code and integrating compliance into the software development lifecycle.
One of the most important advantages of Compliance as Code is the ability to conduct continuous compliance monitoring. Organizations may ensure that their applications stay compliant throughout the development process by incorporating compliance checks into the software development lifecycle. This reduces the risk of non-compliance and can assist firms in avoiding costly fines and reputational harm.
CaC allows businesses to incorporate compliance testing into their DevOps workflows, allowing them to discover and fix compliance concerns earlier in the software development lifecycle. This enables enterprises to deliver cloud-native applications at scale and at a faster rate. CaC enables enterprises to consistently enforce compliance requirements across their cloud environments. Organizations may ensure that their controls are applied consistently across all of their cloud environments, including containers, microservices, and serverless activities, by treating compliance controls as code.
To implement CaC, enterprises must follow a set of best practices. To begin, they must approach compliance requirements as code and include them in the software development lifecycle. Second, they must employ solutions such as Cyscale to automate compliance testing and monitoring. Finally, they must verify that their compliance rules are implemented consistently across all of their cloud environments. Fourth, they must assess and update their compliance controls regularly to ensure that they remain relevant and effective.
Conclusion
Cloud compliance is critical for firms that operate in the cloud. Failing to comply with regulatory standards and best practices can have serious implications, including legal penalties, loss of business, and reputational damage.
Organizations must develop a complete approach to accomplish cloud compliance, which includes data protection, access control, risk management, and compliance monitoring. They must also be knowledgeable of the most common compliance frameworks and regulations that apply to their business, as well as ensure the security and compliance of their cloud infrastructure and apps.
Cloud-Native Application Protection Platforms (CNAPPs) and Cloud Access Security Brokers (CASBs) can assist enterprises in achieving cloud compliance by offering sophisticated security capabilities, real-time monitoring, and threat information. One such platform is Cyscale, which provides an all-in-one solution for cloud compliance that includes automated security assessments, ongoing compliance monitoring, and comprehensive reporting.
A promising solution for establishing continuous compliance in the cloud is the emerging notion of Compliance as Code. Organizations can achieve compliance more efficiently and accurately by automating compliance tests and incorporating them into the development process.
In summary, establishing cloud compliance necessitates a holistic approach that combines security measures, regulatory compliance, and constant monitoring. Organizations may assure the security, compliance, and protection of their cloud infrastructure and applications by applying best practices and employing sophisticated technologies such as CNAPPs, CASBs, and Compliance as Code.