We may earn a commission if you make a purchase through the links on our website.
Device42 Insights+ Review & Alternatives

UPDATED: May 1, 2024
Device 42 is software for IT asset management. It offers users a visual representation of their assets and their relationships with other system components. The program displays them on an attractive dashboard. Additionally, the program produces digestible reports. The program enables IT administrators to monitor networks, software, and hardware.
Password management, service administration, data center management, and asset labeling are some of its most important features. Additionally, Device 42 enables IT administrators to coordinate the asset lifetime. It allows administrators to issue rights and provides authorized team members with access. Its data center visualization helps enterprises to establish an orderly data repository.
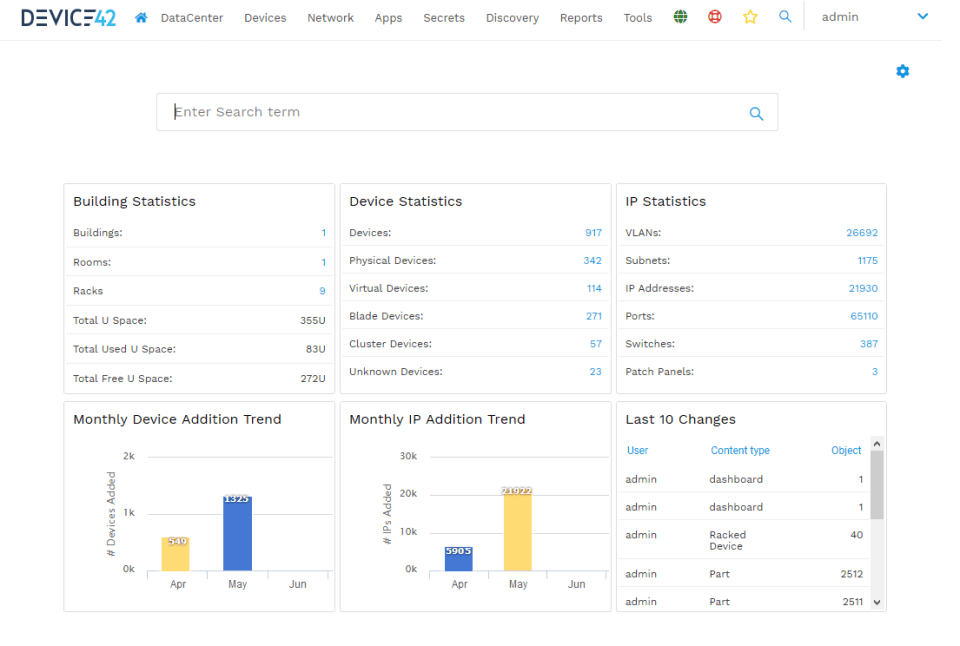
With its automated capabilities, Device42 avoids enterprises from manually updating their inventory and systems as new assets and devices are acquired.
Key Features:
- System Automation Device42 provides automation capabilities that can rapidly detect new IT asset inventory additions. In addition, firms have the option to involve an agent in the process of locating remote assets for accurate inventory management.
- Multi-Asset Monitoring IT team members may concurrently monitor, track, and add cloud-based, virtual, and physical installations using Device42. This allows users to support more than two infrastructures with the tool. The inventory includes all hardware and software components, allowing organizations to utilize their assets.
- Third-Party Assistance Device42 may be simply deployed on widely used operating systems, including Linux, macOS, Windows, BSD, and UNIX. The program facilitates links with third-party applications. This is possible via its RESTful API, which includes pre-configuration for Cherwell, JIRA, and others.
- Contract Management Device42 includes automated contract administration capabilities. This ensures contracts with current vendors for vital systems are updated and the infrastructure is effectively handled. The application will notify businesses of expired contracts so they may renew or enter into new arrangements.
In addition, the program enables users to monitor each piece from a single window, which greatly increases workflow and overall productivity. The password management module enables organizations to organize and store passwords in a single, safe area. Device42 provides superior technical assistance. From deployment through aftercare, their staff of skilled and trained agents strives to assist users with technical challenges in a professional manner.
The best Device42 Insights+ Alternatives
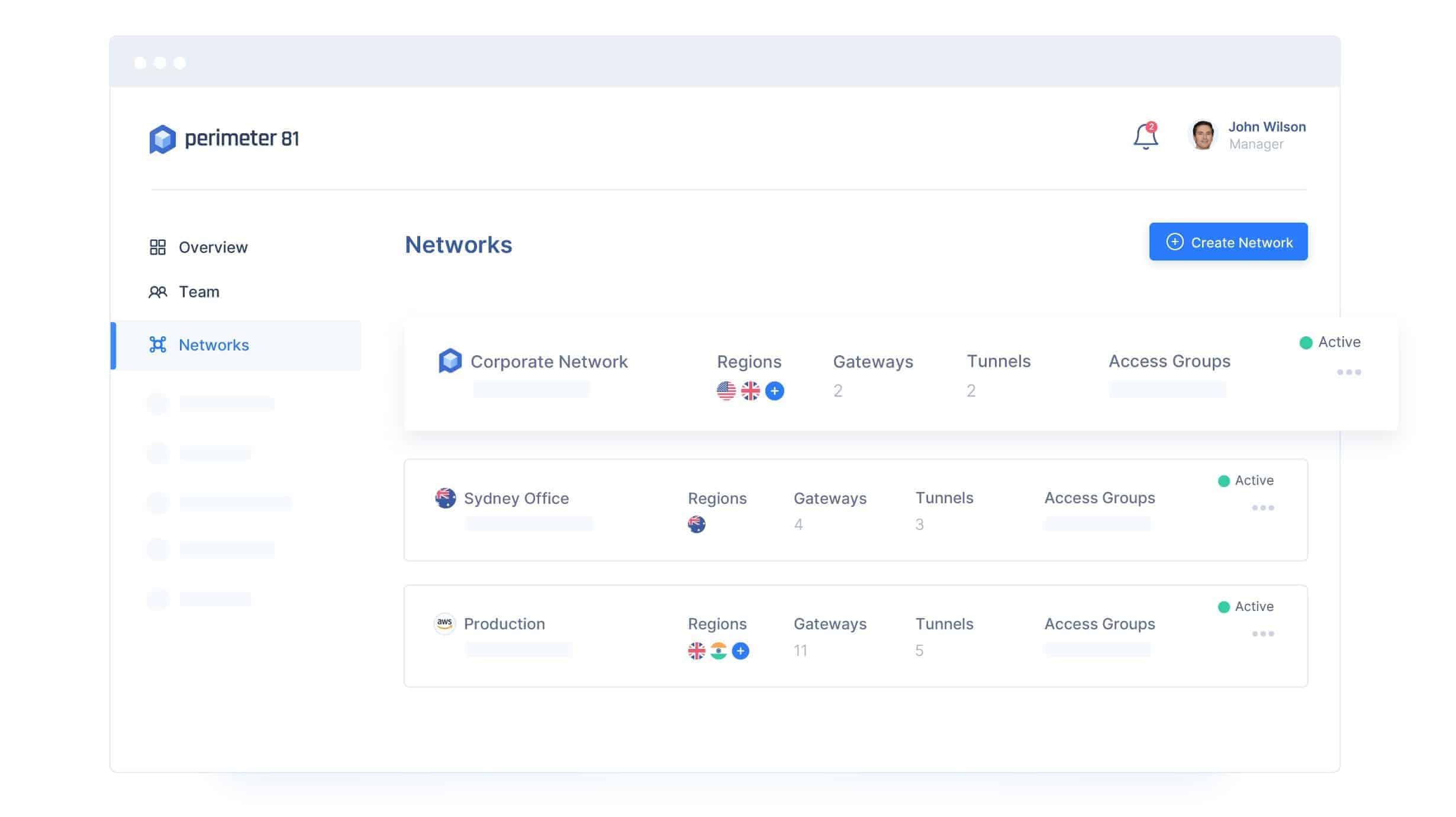
1. Perimeter 81 – EDITOR'S CHOICE
Perimeter 81 is a cloud-based VPN solution that enables enterprises of all sizes to give remote and onsite employees secure access to cloud environments, software, and on-premises services. Among the features are two-factor authentication, split tunneling, permission management, and DNS filtering.
Key Features:
- HIPAA Compliance for Healthcare Perimeter 81 facilitates HIPAA compliance for healthcare businesses by safeguarding ePHI using end-to-end encryption and two-factor authentication (two-factor authentication).
- Data Security for Financial Perimeter 81 safeguards sensitive financial data from cyberattacks for finance businesses by securing on-site and mobile access to secret data and company resources while hiding them from the public Internet.
- Multi-Tenant Cloud Perimeter 81's user-friendly web interface enables the implementation of several networks, each with its own set of rights. Using IP whitelisting, these networks may be readily connected to a central office, to one another, or to cloud services such as Google Cloud, Amazon Web Services (AWS), Microsoft Azure, and several SaaS platforms.
- Integration of Single Sign-On Using the online interface, which combines Active Directory, Okta, GSuite, and Azure AD, individuals or groups may manage access to organizational resources.
The technology, which is powered by the renowned SaferVPN, makes internet security simpler, enabling employees to access work remotely while being secure.
The service alters the typical corporate VPN experience by ensuring that they give this powerful approach regardless of what your employees are doing or from where they operate, employing a next-generation sophisticated Cloud VPN solution and trustworthy hardware-free cybersecurity solutions.
This service is also great for customers with many devices, especially those who constantly transition between devices.
Perimeter 81 has more than simply a defense component. Now, business owners and IT security professionals have unparalleled network visibility.
Register here for a free demo.
EDITOR'S CHOICE
Perimeter 81 is our top choice! As a result of the adaptable cloud management software's 360-degree view of your network's security, you will be able to quickly identify any suspicious activity. This guarantees that you have control over the settings of your team and server, as well as network and service access for your employees.
Download: Access FREE Demo!
Official Site: https://www.perimeter81.com/solutions/perimeter-81-vs-competitors
OS: Cloud-based
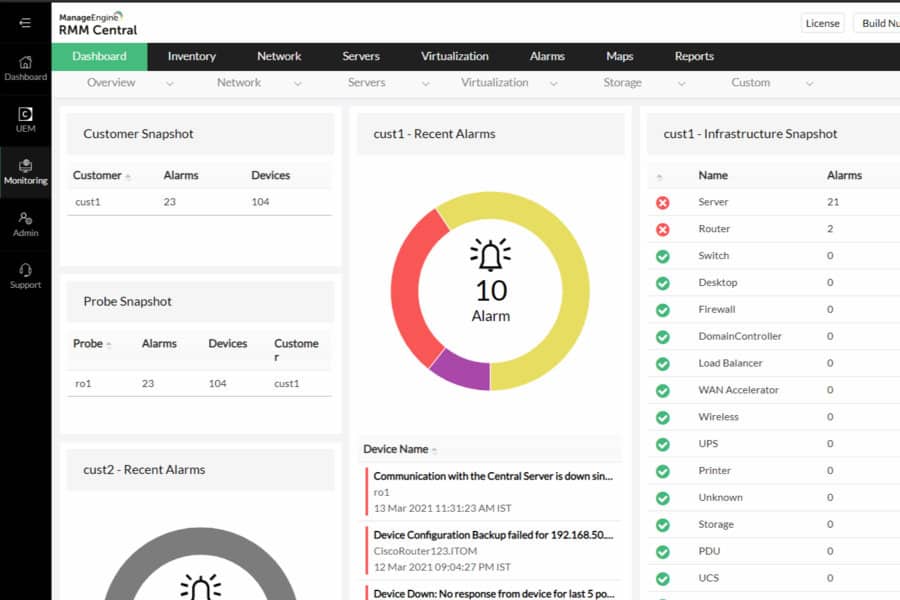
2. ManageEngine RMM Central – FREE TRIAL
ManageEngine RMM Central implements network discovery. The package creates a hardware inventory that lists network devices and endpoints. The discovery process repeats continuously, keeping the asset inventory up to date.
Key Features:
- Network discovery: This cycles continuously, checking on the availability of all devices and getting reports on their statuses.
- Endpoint monitoring: This service provides constant performance monitoring for workstations and servers. It notes the utilization of resources, such as CPU, memory, and disk space.
- Software management: The system generates a software inventory for each endpoint. This enables license management and controls to identify and remove unauthorized software.
- Patch management: The Software inventory forms the basis for an automated patching service. This will update Windows, Linux, macOS, and more than 1,000 third-party software packages.
- Remote control: A remote access package that provides a remote desktop utility and the option to take control of the remote endpoint.
- Mobile device management: This can manage mobile devices running iOS, Android, and Windows. It includes onboarding, tracking, locking, and wiping services.
The RMM Central package is designed for use by managed service providers. There is another package available for IT departments instead of RMM Central. That is called Endpoint Central. This package has a multi-tenant architecture, which allows MSPs to set up sub-accounts. These keep the data of each client separate.
The mobile device management service in the package is very comprehensive. It includes routines for managing fleet devices and also BYOD. As well as managing devices this system provides many security services. For example, it is possible to block users from installing their own preferred apps. The package also has a content security mechanism.
ManageEngine RMM Central is a software package that will run on Windows Server, AWS, or Azure. There is a Free edition for the package, which has all of the features of the paid edition but it is limited to managing 20 endpoints and five network devices. You can examine the RMM Central system with a 30-day free trial.
3. Total Network Inventory
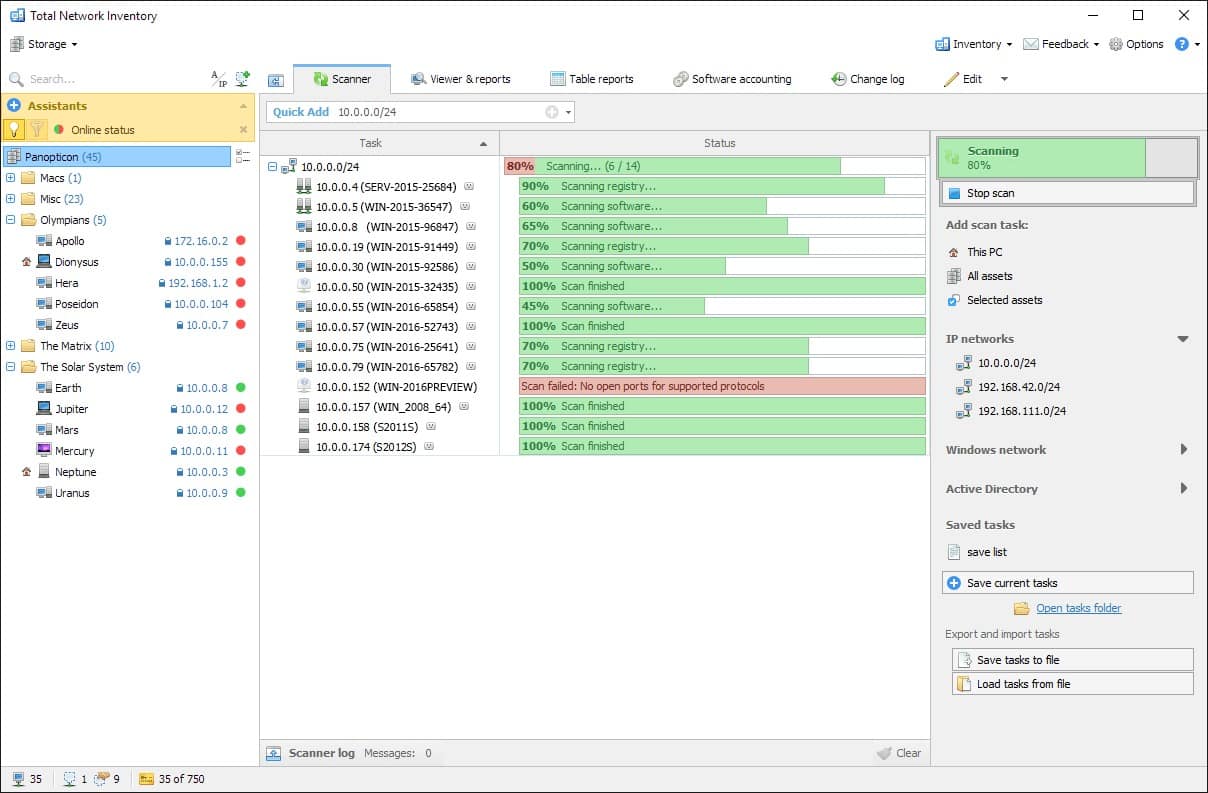
It might be difficult to discover and inventory network devices, gear, and software. Total Network Inventory is a solution that facilitates the discovery and management of network hardware and software assets.
Key Features:
- Inventory Inventory and network scanning go hand in hand. It provides asset tracking in the environment. You may utilize TNI's tracking tools and capability to track assets and attach necessary supplementary data.
- Reports Reports are crucial in the majority of workplaces. With TNI reporting, you can gather data harvested by the network scanning and inventory functions and feed it into bespoke reports that may be used for compliance audits and other purposes.
- Software accounting When done manually, keeping track of all the software in your environment may be a huge undertaking. TNI provides a sophisticated method for keeping track of all installed software and associated license information. You may search and filter by individual software packages, as well as store information on licensing keys, expiration dates, and other data.
- Live license status Licensing is synonymous with Keeping track of licenses is a challenging task. This is particularly true if your environment has several program installs. TNI permits software tracking and reporting on many elements of software licensing inside an environment.
Total Network Inventory is a software inventory and PC audit management solution developed for organizations of all sizes. It enables users to scan devices on a network and generates a report containing information on active operating systems, current processes, hardware, software, and hotfixes.
Total Network Inventory facilitates inventory management, software accounting, and log management for users. The solution categorizes and connects comments or other accessible information to network assets. The created reports can be copied, printed, or exported for additional usage. It also has a search tool that displays real-time results as the user types.
Users can manage and see the inventory log, which contains information on application installation, hardware connection, and disc space utilization. It enables users to specify the exact time and date for repeated scans of various asset kinds. Users can specify unique passwords for distinct asset categories to boost protection.
4. IT Asset Management
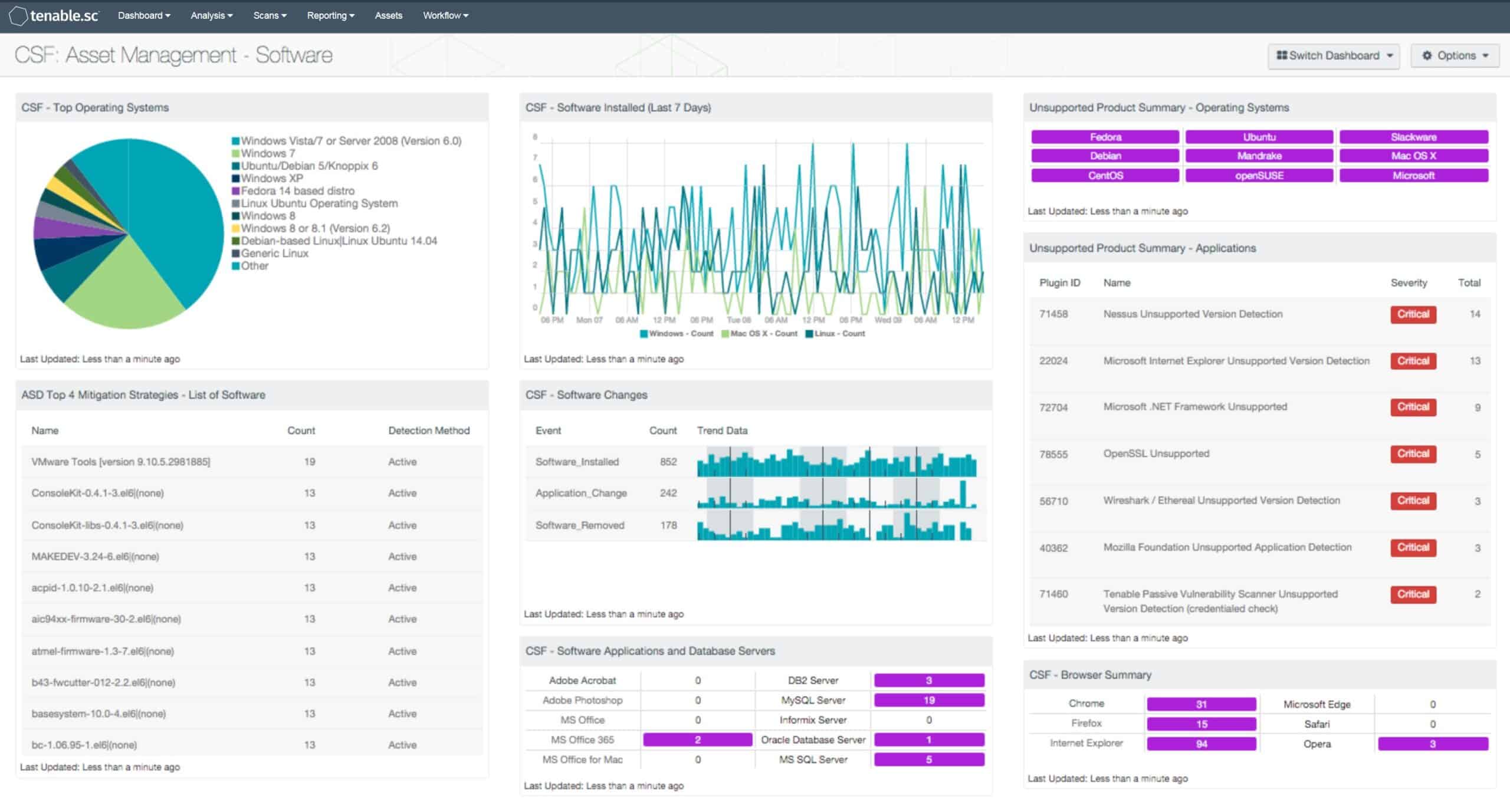
IT Asset Management (ITAM) is the process of collecting inventory, financial, and contractual information to manage an IT asset during its life cycle. IT Asset Management is an integral component of every business's strategy. It involves the collecting of asset/inventory data that is then utilized to make business choices on future software and hardware purchases and redistributions. This method of making data-driven business choices helps IT asset managers to decrease waste and increase efficiency by preventing the procurement of superfluous assets.
Key Features:
- Evaluation of new assets All components should be documented and checked when adding new assets to the inventory. For instance, when adding a new MacBook, you should record its model, serial number, and accessories.
- Evaluation of asset usage Once asset utilization has been identified, assessing and taking action regularly allows for the enhancement of return on investment. It also reveals challenges associated with assets being in stock but unavailable when personnel require them.
- Determine missing assets on the ground It is essential to carefully document asset allocations. Thus, you will be able to detect any unreported or unchecked-in assets.
- Licenses and contracts Licenses for software should be examined often. A frequent practice is to establish alerts on your system to notify you when a license is close to expiring.
IT Asset Management is in no way a one-time endeavor. It is a persistent and continual endeavor that pays off in the long term. An efficient ITAM solution must have a repository for IT asset management, utilization statistics on both hardware and software components, connection with neighboring IT and business systems, and the capacity to import data.
5. Miradore Management Suite
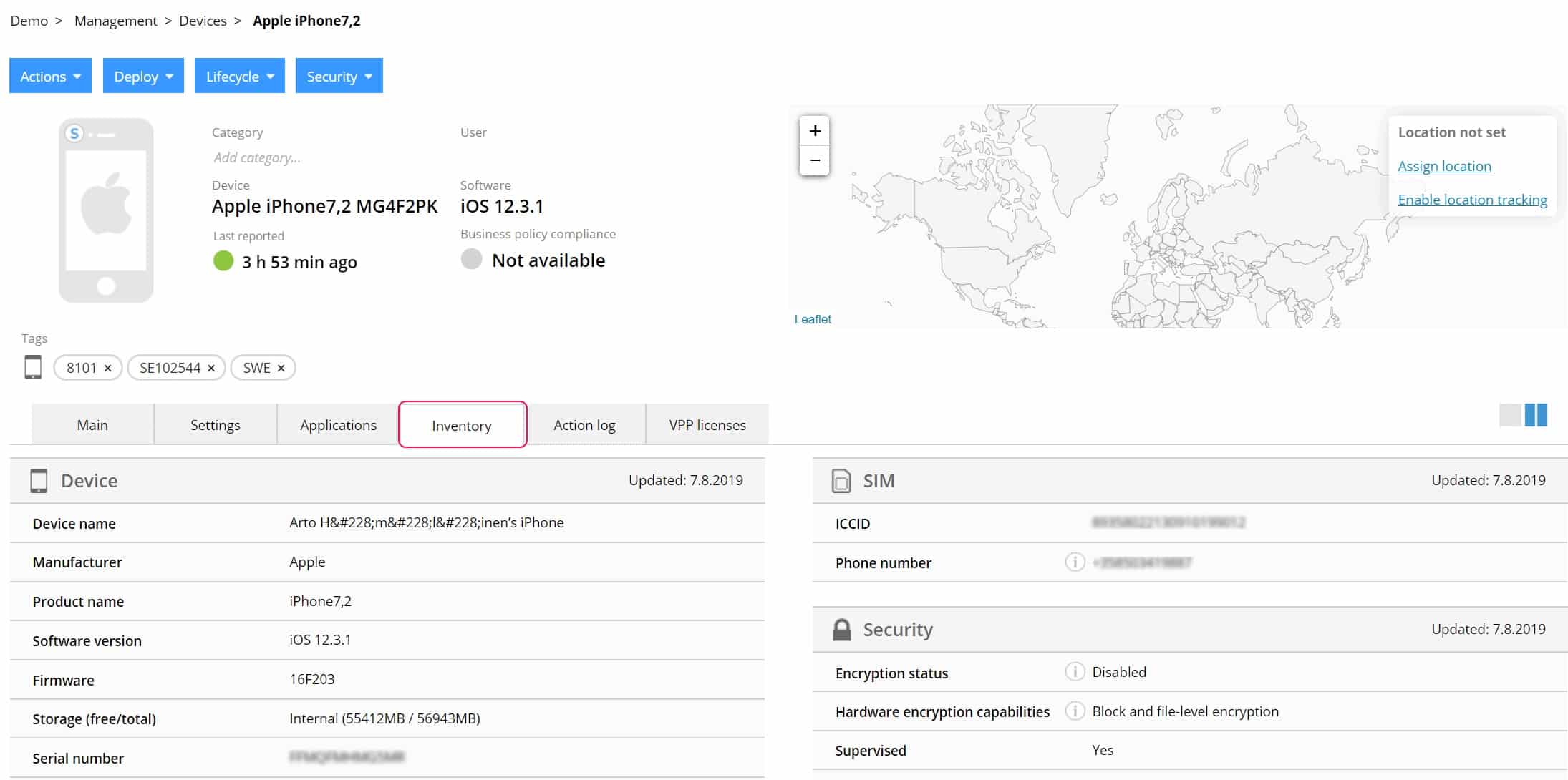
Miradore Management Suite is built primarily for managing heterogeneous IT systems comprising PCs, laptops, servers, and POS devices. The Management Suite has combined the management operations for many hardware and software platforms into a single, unified solution that supports Windows, macOS, and Linux. When integrated into a client's operations, Miradore enables the creation of automated workflows to deliver reports, resolve issues, and provide immediate value. Miradone offers administration for mobile devices and PCs. This encompasses aspects such as security, compliance, device inventories, and configuration settings. It is a cloud-based solution that ensures all data remains on the device without the need for further software installs.
Key Features:
- Miradore is user-friendly and accessible from any device With its user-friendly and basic layout, Miradore is simple to use. Since it is accessible via the cloud. Additionally, you may manage your device inventory and settings from any device.
- You can exchange data simply You may effortlessly transmit data with your staff, customers, and partners with Miradone. Including access to applications, contacts, and devices, as well as anything else required for other employees.
- The Platform is secure With built-in encryption of all supported devices, Miradore is safe for your data, secure by design, and simple to administer.
- Storage With Miradore, you need not be concerned about the number of files and messages that end-users save on their devices.
This cloud-based solution is compatible with any on-premise or SaaS technology stack, such as Windows Active Directory Servers (AD), Mac OS X Server's Open Directory servers, Microsoft Exchange Email Servers, Office 365, etc.
6. Pulseway
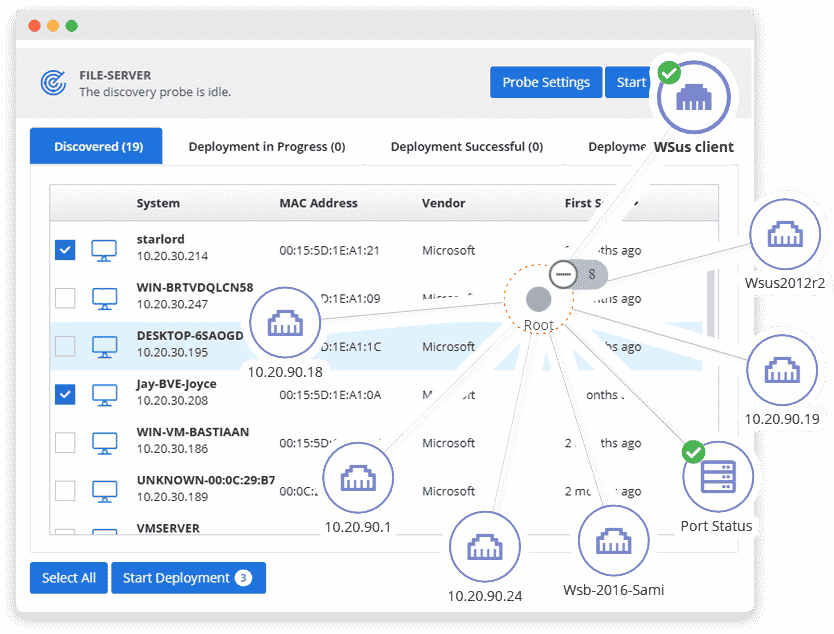
Pulseway is a Remote Monitoring and Management system that offers you complete management of your IT infrastructure from any smartphone or tablet. Receive fast notifications of major IT system problems and take immediate action from any mobile device. You may also design intelligent rules to fine-tune alert situations and activate certain activities. Monitoring system resources, logged-in users, network performance, essential updates, IIS, SQL Server, Exchange, Active Directory, VMware, Hyper-V, and SNMP-enabled devices in real-time. Fix issues on the move by sending instructions from any mobile device. Execute commands at the terminal, control ongoing processes, restart services, apply important updates, and restart systems, among many other operations. With mobile applications accessible for all mobile platforms, you may access your whole IT infrastructure from anywhere at any time. You are welcome to leave your workstation.
Key Features:
- Mobile-First Work from anywhere, on any device, with instantaneous and potent access to the essential tasks. Pulseway's native Mobile Apps (Android & iOS) were designed from the ground up to provide you with complete control over all your vital IT systems.
- Asset Discovery A simple-to-use Network Discovery and Deployment engine enables immediate productivity out of the box. With no necessary onboarding or training to get you operational. You may quickly and easily identify all IT endpoints and then install the Pulseway solution with pre-configured policies in bulk within minutes.
- Automation With Pulseway's simple-to-use Automation engine, you may accomplish repetitive jobs and automated fixes by enabling Tasks to be conducted according to the criteria and timetables you establish.
- Endpoint Security Pulseway guarantees that your IT systems are always completely secured. Manage, monitor, configure, and deploy Pulseway Antivirus throughout your IT infrastructure in a matter of minutes.
Using any smartphone, tablet, or laptop, you can now monitor, manage, and control your IT systems and apps in real-time. Pulseway has done for System Administration what cellphones did for email: you receive a notification, view the problem, and resolve it in a matter of seconds. Monitoring is no longer a hassle; you just monitor and respond immediately to server issues as they happen. It is similar to carrying a NOC in your pocket.