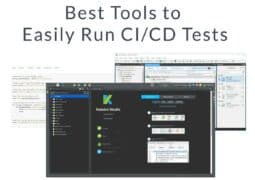
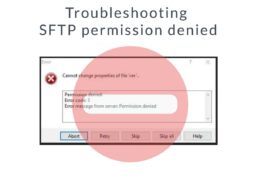
How to Configure a Cisco Switch
Cisco switches are targeted at businesses or enterprises that need flexibility, power, and security to connect medium-to-large networks. As opposed to plug-n-play, administrable switches require and allow configuration via an…