We may earn a commission if you make a purchase through the links on our website.
The Best Host-Based Intrusion Detection Systems (HIDS) Tools & Software

UPDATED: September 9, 2025
A Host-Based Intrusion Detection System (HIDS) is a network security system that protects computers from Malware, Viruses, and other harmful attacks. Much like a surveillance or security alarm system installed in your home or office, it watches and alerts for possible break-ins and thieves.
Here is our list of the best HIDS tools:
- ManageEngine Event Log Analyzer – EDITOR'S CHOICE This log manager also implements SIEM to look for compromised security in the IT system. Available in free and paid versions for installation on Windows Server or Linux. Start a 30-day free trial.
- ManageEngine Firewall Analyzer – FREE TRIAL A firewall log and policy analysis tool with multi-vendor support and real-time monitoring. Start a 30-day free trial.
- Open Source Security (OSSEC) A widely used, free host-based intrusion detection system that mines logs for indicators of unauthorized activity. Available for Windows, macOS, Linux, and Unix.
- Samhain A free host-based intrusion detection system that is implemented in two parts, clients to gather data from many endpoints, and a server to process that data centrally, looking for security incidences. Available for Linux and Unix and can run on Windows with Cygwin.
- Wazuh This tool is an alternative to OSSEC because it was developed from that code, which is open source and so freely available. Runs on Windows, macOS, Linux, and Unix.
- Advanced Intrusion Detection Environment (AIDE) An open-source host-based intrusion detection system that is free to use. This is a command-line utility for Linux, macOS, and Unix.
- SolarWinds Security Event Manager This log message collector and consolidator mines log data for signs of security breaches to form a SIEM. Runs on Windows Server.
- Tripwire This command line tool is a host-based intrusion detection system and it is free to use. Installs on Linux.
- IBM Security IDS / Maas360 An intrusion detection system that is offered from a platform of system security monitoring options. This is a cloud-based system.
- Lacework A cloud security intrusion detection system that looks for anomalies in activities. This is a SaaS platform.
- Security Onion A free, open-source package that bundles together a range of other open-source systems and includes a host-based intrusion detection system, which is actually Wazuh, detailed above. Runs on Linux.
These systems may not do anything to stop an intruder; they only sound alarms or let somebody know that there has been something unusual. But an alarm system can’t do anything to prevent the intruder, but your locks, gates, and security guards do.
In the telecommunications world, a HIDS is like your home alarm system. It lets you know when a hacker is attempting to attack your network or perimeter, it detects unusual behavior in the host and sends immediate alerts. The IPS (Intrusion Protection System) is like your locks, gates, and guards, which prevent intrusion.
What is a Host-Based Intrusion Detection System (HIDS)?
HIDS monitors the host computer where is installed by detecting unusual intrusions or misuse of resources. It logs all events and sends immediate notifications to a security administrator to take proper action. The HIDS keeps track of the traffic going and coming to the host computer, but not traffic in the network. It can also monitor crucial internal system files and detect any attempts to modify them. HIDS checks whether something or someone has violated any of the security policies.
HIDS is not:
A HIDS does not prevent intrusions or attacks, just as an IPS does. Although HIDS can be installed on network points such as routers or servers, they cannot monitor at the network level. A NID (Network Intrusion Detection), on the other hand, can be installed in network intersection points and monitor traffic. A HIDS does not filter incoming/outgoing traffic based on rules, the way a firewall does, or a Bandwidth monitor does. A HIDS is not designed to stop attacks, it is best, however, in detecting all kinds of attacks and delegating the “prevention” to someone else.
How does a HIDS work?
The dedicated intrusion detection system monitors traffic for malicious activity or policy violations. It detects known attacks by the specific actions they perform (signatures).
The HIDS analyzes traffic (much like a network traffic analyzer) and behavior that matches these signatures in real-time, in the host. It can also detect unusual usage patterns with anomaly detection methods. When the HIDS finds a match, it raises an alarm and notifies the administrator.
The HIDS is installed on the host, while the NIDS is placed inline. The HIDS protects the system at the source so that it can be deeper and more intense in its security. The HIDS can also monitor system files, executables, and log files in the host computer and look for attack signatures.
Functionalities of a HIDS include:
- Anomaly-based detection
- Signature attack detection
- Zero-day attacks
- Traffic monitoring at host
- File integrity monitoring
- Log analysis
- Compliance and auditing
- Notification and alerting system
The Best HIDS Tools & Software
Our methodology for selecting a host-based detection system tool
We reviewed the market for HIDS packages and analyzed options based on the following criteria:
- Log file collector
- Log consolidator and log file manager
- Log message sorting and searching for intrusion detection
- Data viewer for manual threat analysis
- Ability to exchange data with other security packages, such as SIEM tools
- Free trial for a no-risk assessment opportunity before buying or a free tool
- Value for money from a HIDS tool that provides competent detection measures or a free system that is thorough and worth using
With these selection criteria in mind, we identified a number of competent host-based intrusion detection tools, including many free packages.
1. ManageEngine Event Log Analyzer – FREE TRIAL
The Event Log Analyzer from ManageEngine is more than a HIDS; it is a log manager, auditing, and IT compliance solution. The tool can be used to perform network device audits, such as fire-wall audits, vulnerability scanning, and IDS/IPS reporting. It can also be used for file server and application auditing.
Key Features:
- Network Device Auditing: Gives instant alerts in case someone breaks your firewall security policies, rule changes, user logons, and logoffs.
- Application Log Analysis: Checks for critical changes, data theft, attacks, and downtime to maintain the confidentiality and integrity of the database.
- Web Server Log Management: Includes an IIS log analyzer, apache log analyzer, and DHCP log analyzer, which helps audit, track, and manage security errors and configuration changes.
Feature Distinction
This HIDS tool stands out for its seamless integration with other ManageEngine products. This makes log management and auditing easier while enhancing your overall security framework.
Why do we recommend it?
We recommend ManageEngine Event Log Analyzer because it helps protect your organization's sensitive data. Its file integrity monitoring feature tracks changes to files containing confidential data in real-time, detecting security incidents promptly and ensuring data integrity. This proactive approach helps prevent unauthorized access, modifications, and breaches, enhancing overall security.
The Event Log Analyzer’s SIEM capabilities allow you to monitor the integrity of your files in real time. This feature helps you protect sensitive information and meet compliance regulations. You can track changes in files and folders from a central location and receive real-time alerts when there’s been a violation.
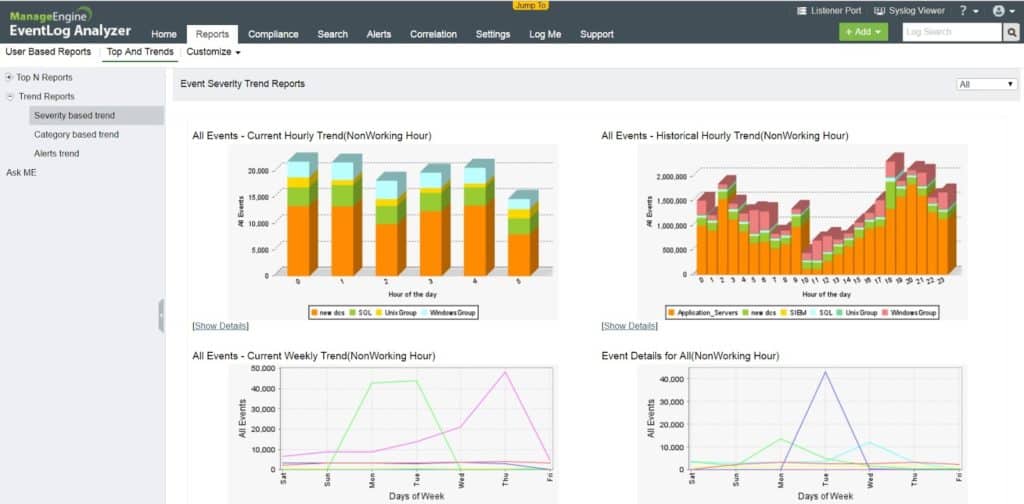
When it comes to log management, the Event Log Analyzer from ManageEngine is probably one of the most robust software out there. It can collect logs, add secure storage, normalize, analyze, and create reports and alerts. The tool also supports out-of-the-box IDS/IPS vendor logs, such as Cisco, Juniper, SonicWall, Barracuda, Fortinet, and more. The Event Log Analyzer automatically collects all these logs and stores them in a central location.
Benefits of IDS/IPS Reports:
- Attacks in real-time or history.
- Most targeted devices.
- Trendy attacks, and more.
Who is it recommended for?
EventLog Analyzer is recommended for companies of all sizes seeking efficient log data management, regulatory compliance, and network security. It's utilized by various experts, including IT administrators, compliance officers, and security professionals. Its customizable dashboard and compliance auditing capabilities make it suitable for addressing the requirements of PCI DSS, FISMA, HIPAA, and more.
Pros:
- Customizable Dashboards: Tailored dashboards are ideal for Network Operation Centers (NOCs), allowing for efficient monitoring and analysis of log data.
- Multiple Alert Channels: Alerts can be sent via SMS, email, or integrated with other applications, ensuring timely notifications to teams.
- Anomaly Detection: Utilizes anomaly detection to aid technicians in identifying irregularities and potential security threats in day-to-day operations.
- File Integrity Monitoring: Acts as an early warning system for various security concerns, including ransomware, data theft, and permission access issues.
Cons:
- Scalability Issue: Some users found issues with customization reports and correlation capabilities. It could have been made more user-friendly with the addition of AI-driven features and automation.
The software comes in three editions, Free, Premium, and Distributed. The Free edition is limited for a maximum of five log sources, while the Premium and Distributed editions can handle from 10 – 1000 log sources and 50 – unlimited. You can start off with a 30-day free trial.
Once the trial period is over, the software automatically reverts to the Free Edition of Event Log Analyzer and monitor a maximum of five log sources, perfect for a host-based environment. If at this stage you need the full functionality, you can purchase the software and activate all the features.
EDITOR'S CHOICE
ManageEngine EventLog Analyzer is our top pick for a host-based intrusion detection system because it provides comprehensive log management and security event monitoring, essential for detecting and preventing potential intrusions at the host level. HIDS focuses on identifying unauthorized activities within the system; EventLog Analyzer excels in collecting, analyzing, and correlating logs from servers, workstations, network devices, and security appliances to identify suspicious events. The core of EventLog Analyzer is its real-time log analysis capabilities, which enable IT teams to quickly detect anomalies indicative of possible intrusions. The system analyzes various event logs, including authentication attempts, access logs, file modifications, and configuration changes. Such actions look for patterns that suggest malicious activities. By applying correlation rules, the tool can highlight abnormal behavior, such as brute force attacks or privilege escalations, providing immediate alerts for quick response. EventLog Analyzer offers automated compliance reporting for standards such as PCI DSS, HIPAA, and GDPR, helping organizations ensure that their host-level security practices align with regulatory requirements. It also supports detailed forensic analysis, allowing teams to trace suspicious activities back to their source, aiding investigations and improving overall security posture.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/eventlog/download-free.html
OS: Windows Server and Linux
2. ManageEngine Firewall Analyzer – FREE TRIAL
ManageEngine Firewall Analyzer is a multi-vendor tool for firewall log and policy analysis. It centralizes visibility across 50+ security tools, including firewalls, HIDS, VPNs, and more. So it is perfect for helping you monitor configs, detect anomalies, and optimize rules.
Key Features:
- Broad Device Support: Works with 50+ firewalls, VPNs, IDS/IPS, and proxies.
- Agentless Log Collection: Fast root-cause search and forensic analysis.
- Smart Rule Management: Detects anomalies and cleans up.
- Real-Time Dashboards: Track VPNs, bandwidth, proxies, and sessions live.
- Compliance Automation: Generates reports for PCI DSS, ISO 27001, GDPR, HIPAA, and more.
- Config Change Tracking: Alerts on changes and keeps full history.
Why do we recommend it?
While a Host-based Intrusion Detection System (HIDS) monitors unauthorized activity and process anomalies, it only tells part of the story. To fully secure your environment, you also need visibility into the network perimeter. This is where traffic policies and firewall rules decide what gets in or out.
This is where ManageEngine Firewall Analyzer adds real value. It complements HIDS by analyzing firewall, VPN, IDS/IPS, and proxy logs, giving broader insight into external threats. It keeps firewall rules lean and effective and tracks VPN sessions and bandwidth spikes in real time. It also automates compliance reporting for standards like PCI-DSS, HIPAA, and GDPR while supporting forensic investigations.
When paired together, HIDS provides host-level depth while Firewall Analyzer delivers network-level breadth. The result is a stronger, two-layer security posture that reduces blind spots and speeds response.
Who is it recommended for?
Firewall Analyzer is perfect for enterprises and MSSPs managing many and different firewall fleets. Thanks to the software’s strong posture on compliance automation, the tool is also a strong fit for organizations in regulated sectors such as finance and healthcare. It is perfect for those requiring continuous compliance-ready reporting.
Pros:
- Multi-Vendor Coverage: Strong support with a centralized “single pane of glass.
- Real-Time Visibility: Custom dashboards and instant alerts speed response.
- Compliance Automation: Reduces manual reporting effort.
- Rule Optimization: Enhances firewall performance and security posture.
- Reliable Support: Responsive assistance and extensive documentation.
Cons:
- Performance Limits: Can lag under heavy log volumes without proper hardware.
- Complex Setup: Challenging for large or multi-site deployments.
- Dated Interface: Feels old-fashioned to some admins.
Start a 30-day free trial.
3. Open Source Security (OSSEC)
OSSEC (Open Source HIDS SECurity) is probably the best free, open-source, and multi-platform HIDS out there.
Key Features:
- Open Source: Allows customization to add custom rules, scripts, and other configurations.
- Multi-Platform Support: Compatible with Linux, Solaris, HP-UX, BSD, AIX, Windows, Mac, and VMware ESX and supports host-based intrusion detection.
- PCI Compliance: Monitors and informs you of illegal file system modifications and malicious behavior that may render you non-compliant.
Why do we recommend it?
We recommend OSSEC because it offers extra features like a Machine Learning System for free. It also includes things like real-time threat sharing, lots of new rules, and integration with the ELK stack. OSSEC+ gives added benefits at no cost, making it a great choice for security.
OSSEC provides the following functionalities:
- Log-based intrusion detection.
- File integrity monitoring.
- Compliance auditing.
- System inventorying.
- Windows registry monitoring.
- Rootkit and Malware detection.
- Centralized policy enforcement.
- Real-time alerting and active response.
The software comes with a robust correlation and analysis engine. It can monitor logs from multiple devices and formats and analyze their contents in real-time. You can also manage different systems with OSSEC’s centralized management platform.
OSSEC takes the usual HIDS functionalities further with their active response system. This system can respond to attacks and events in real-time using different mechanisms, such as firewall policies, integrations with third-party services, and self-healing actions.
This tool is compliant with the requirements of the Payment Card Industry Data Security Standard (PCI DSS). OSSEC detects and alerts file system modifications or behavior that are PCI non-compliant. OSSEC runs on most of the popular OS, like Linux, macOS, Windows, OpenBSD, FreeBSD, and Solaris.
Who is it recommended for?
The Atomic OSSEC system is recommended for security experts and IT professionals who need advanced threat detection and response capabilities. It offers thousands of enhanced rules, real-time file integrity monitoring, frequent updates, compliance tools, and expert support. It's a versatile security solution combining XDR and compliance features.
Pros:
- Active Community: The support community is easily accessible, so you can quickly get support, help, and configuration.
- File Integrity Monitoring: Monitors critical system files and directories for unauthorized changes. This helps to detect and mitigate the impact of malware and maintain system integrity.
- Centralized Management: You can manage everything through command-line tools to configure, monitor, and manage security policies across distributed environments from one central location.
Cons:
- Difficult Upgrades: Some users found that old rules disappeared, and the upgrade process took time and effort.
Get the latest stable version from the OSSEC official website.
4. Samhain
Samhain is another free and open-source HIDS tool. It can be used as a standalone solution to monitor a single host, or as a centralized logging and maintenance platform for multiple hosts running different operating systems.
Samhain is a multiplatform application that supports Unix, Linux, and Windows (through Cygwin). The software operates with a client/server architecture.
Key Features:
- File Integrity Monitoring (FIM): Checks for unauthorized changes, provides alerts when suspicious alterations occur, and protects against malware and unauthorized access.
- Log File Analysis: Scans log files to identify security events and anomalies and offers insights for potential threats or breaches.
- Tamper Resistance: Offers robust security with a PGP-signed database and supports stealth mode to ensure the security of configuration files.
- Web-Based Management Console: using a web-based console, you can monitor server and client activities, read client reports, and update baseline databases.
Why do we recommend it?
Samhain is an open-source tool and the perfect tool for analyzing multiple hosts with different operating systems. It offers centralized logging and maintenance across systems and can also be used as a standalone application on a single host. Plus, it's compatible with various POSIX systems, including Unix, Linux, and Cygwin/Windows.
Samhain provides:
- File integrity checking.
- Logfile monitoring and analysis.
- Port monitoring.
- Rootkit detection.
- Rogue SUID executables detection
- Hidden processes detection.
- Compliance with PCI DSS
The clients can export logs to a central repository, get client configurations, or update from a baseline database. Clients can also output data using Syslog, Email, or RDBMS.
But as mentioned above, the Samhain can be used only to monitor the host computer.
Who is it recommended for?
Cybersecurity experts and IT professionals who want robust host-based intrusion detection capabilities find this tool helpful. It offers file integrity checking, log file monitoring, rootkit detection, and more. Other than this, it supports multiple logging facilities, and you can customize it according to your security requirements.
Pros:
- File Integrity Monitoring: Offers robust file integrity monitoring, detecting unauthorized changes to system files and configurations and helping to prevent malware infections and unauthorized access.
- Log File Analysis: Provides comprehensive log file analysis, identifying security events and anomalies and aiding in the detection of potential threats or breaches.
- Open Source: Open-source software, allowing for transparency, community contributions, and customization to fit specific security needs.
- Efficient Resource Usage: Designed to be lightweight and efficient, minimizing resource usage while still providing robust security monitoring capabilities.
Cons:
- False Alerts: Users found getting the false positive alerts which creates confusion and leads users to investigate and validate security events manually.
Get the latest stable version of Samhain from its official website.
5. Wazuh
Wazuh, a fork of OSSEC, is a free and open-source HIDS. It comes with a centralized, cross-platform architecture that allows multiple systems to be monitored. It can detect intrusions for popular OSs like Linux, Windows, macOS, FreeBSD, OpenBSD, and Solaris.
Key Features:
- Host-Based Intrusion Detection (HIDS): Provides advanced host-based intrusion detection capabilities, offering real-time monitoring of system files, logs, and processes to detect and respond to security threats, enhancing overall system security.
- Scalable Architecture: Suitable for organizations of all sizes, allowing for centralized monitoring and management of security events across distributed environments, ensuring comprehensive threat detection and response.
- Intrusion Detection System (IDS): Acts as an intrusion detection system, detecting and alerting users to suspicious activities or unauthorized access attempts and bolstering network security.
Why do we recommend it?
Wazuh is a must-have if you are looking for a good free and open-source security platform. It offers transparency, flexibility, and constant improvement through community support. You can improve your engagement and collaboration with rapid capability development and comprehensive documentation.
Wazuh uses client/server architecture. The server uses an extensive database of signature attacks to identify intrusions and its detection engine to analyze log data. Its lightweight multi-platform agents (clients) scan the target systems looking for rootkits, malware, or any suspicious behavior. They can also detect hidden files, cloaked processes, or any incompatibilities with system calls.
Who is it recommended for?
Wazuh Cloud service is recommended for organizations of all sizes seeking managed and scalable security monitoring and endpoint protection. IT professionals, cybersecurity experts, and organizations looking for a hassle-free and effective security solution can benefit from Wazuh Cloud's ready-to-use and scalable cloud environments.
Pros:
- Open-Source Community Support: Easily collaborate and gain effective knowledge with community support to improve on knowledge gaps.
- Integrated Security Stack: Integrates with other security tools and platforms, providing a comprehensive security solution that enhances threat detection and response capabilities across the organization.
- Scalable Architecture: No matter what your business size, this tool can easily adapt to organizations of various sizes.
- Built-in Compliance Mapping: Includes built-in mappings to regulatory compliance standards such as PCI DSS, GDPR, and CIS benchmarks.
Cons:
- Issue with Computing Resources: Users find the computing resources time-consuming and don't make sense also.
Download the free Wazuh HIDS from the GitHub project.
6. Advanced Intrusion Detection Environment (AIDE)
Advanced Intrusion Detection Environment (AIDE) is a free and open-source HIDS. AIDE is designed only for checking the integrity of files. With this tool, you can craft rules that create a database of files that are protected from intrusion.
Key Features:
- Supported Message Digest Algorithms: Supports a wide range of message digest algorithms for file integrity checking, including md5, sha1, rmd160, tiger, sha256, sha512, whirlpool, and additional algorithms.
- Supported File Attributes: Monitors various file attributes for changes, including file type, permissions, inode, uid, gid, link name, size, block count, number of links, mtime, ctime, and atime.
- Support for Additional Attributes: Offers support for Posix ACL, SELinux, XAttrs, and extended file system attributes if support is compiled in, ensuring compatibility with diverse system configurations and security mechanisms.
- Plain Text Configuration Files and Database: Easily configure and manage the intrusion detection system without requiring specialized tools or expertise.
- Powerful Regular Expression Support: Selectively include or exclude files and directories from monitoring based on custom patterns, providing flexibility and granularity in defining monitoring criteria.
Why do we recommend it?
Advanced Intrusion Detection Environment is famous for its robust file integrity monitoring capabilities. By creating a database from configurable rules, AIDE efficiently verifies file integrity using multiple message digest algorithms and checks various file attributes for inconsistencies. It also ensures compatibility by reading databases from older or newer versions.
When you first run AIDE, you generate this baseline database, which is checked frequently against the system. The software will correlate and find differences between the database baseline and the filesystem.
Who is it recommended for?
Advanced Intrusion Detection Environment (AIDE) is recommended for IT professionals, cybersecurity experts, and organizations seeking robust file integrity monitoring. With powerful regular expression support, gzip database compression and standalone static binary, it caters to diverse monitoring needs, offering flexibility, efficiency, and ease of deployment in client/server configurations.
You can check the following file properties:
- File type
- Permissions
- Inode
- Modification time
- File contents
- Number of links
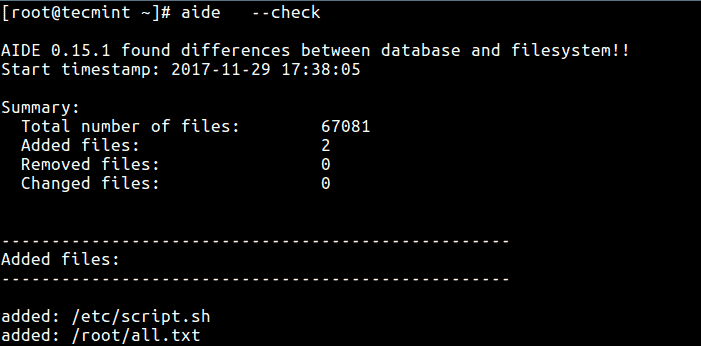
AIDE offers full flexibility when checking the integrity of files. It allows you to write customized expressions to include or exclude files and directories from the monitoring process.
The software only has robust file integrity checking; it does not perform other HIDS functionalities like log-analysis or rootkit/malware detection.
Pros:
- Comprehensive File Integrity Monitoring: Focuses on file integrity so you can monitor and detect unauthorized changes to system files, configurations, and attributes to check security threats promptly.
- Extensive File Attribute Monitoring: Includes permissions, timestamps, and inode to have granular visibility into file system changes.
- Flexible Configuration Options: Flexible configuration options; you can customize monitoring criteria and define alerting thresholds based on individual security needs.
Cons:
- Dependency on External Tools: Users find it relies on external tools and libraries for certain features, such as message digest algorithms or extended file attribute support.
Get the AIDE from the Github project.
7. SolarWinds Security Event Manager
The SolarWinds Security Event Manager (SEM) is a Security Information and Event Management (SIEM) software.
Key Features:
- On-Premises Package: Due to the on-premise package, you can securely control and deploy security event management solutions within the infrastructure.
- Log Collection and Consolidation: Allows easy collection and consolidation of logs from various sources across the network, including servers, endpoints, applications, and network devices.
- Event Correlation: Supports real-time log analysis and cross-event correlation to identify suspicious patterns and complex threats.
- Automated Threat Detection: By analyzing log data and applying predefined rules and behavioral analytics, SEM can automatically identify indicators of compromise, strange behavior, and suspicious activities.
Feature Distinction
What sets this tool apart from others is its root cause analysis (RCA) capability. This troubleshooting feature highlights issues and peels back the layers to reveal the core of security incidents.
Why do we recommend it?
We recommend SolarWinds Security Event Manager because it offers strong log file protection features. It encrypts log files during transit and storage and monitors folder and file checksums. You can forward log messages and easily backup or archive folders and files. Plus, it automatically scans log files without needing manual queries.
It can detect threats on a single host or the entire network. SEM comes with a cyber-threat intelligence framework to identify suspicious activities and take informed actions. SEM takes it beyond what a normal HIDS can do and provides some actionable capabilities.
The tool performs a powerful real-time event analysis, notifies you, or can respond actively. It can block IPs, modify privileges, block USBs, kill applications, and more. SEM can help you prove compliance for the following standards HIPAA, PCI DSS, SOX, and more.
It provides multiple out-of-the-box reporting templates to make auditing and compliance much more accessible.
Who is it recommended for?
This tool is recommended for anyone needing robust log management, from beginners to experts. Its virtual appliance deployment and user-friendly interface make it accessible for all skill levels. Plus, the licensing model based on log-emitting sources, not volume, ensures cost-effectiveness without sacrificing data collection.
Pros:
- Network Events Monitoring: Tracks USB device usage, system log entities, and login attempts like success and failure to detect unauthorized logins in the network.
- In-Depth Monitoring Capabilities: Useful to meet all the needs of an organization as it supports various types of breakdowns, filters, and rules.
- Stay Compliant with Security Requirements: Track changes and identify issues within switches and routers and also receive email notifications for critical events.
- Log Data Parsing: User-friendly dashboard that collects data. It instantly notices the activity when someone updates the system.
Cons:
- Poor Performance with Large Data Centers: Users have reported issues when handling large databases such as 10,000 plus elements.
8. Tripwire
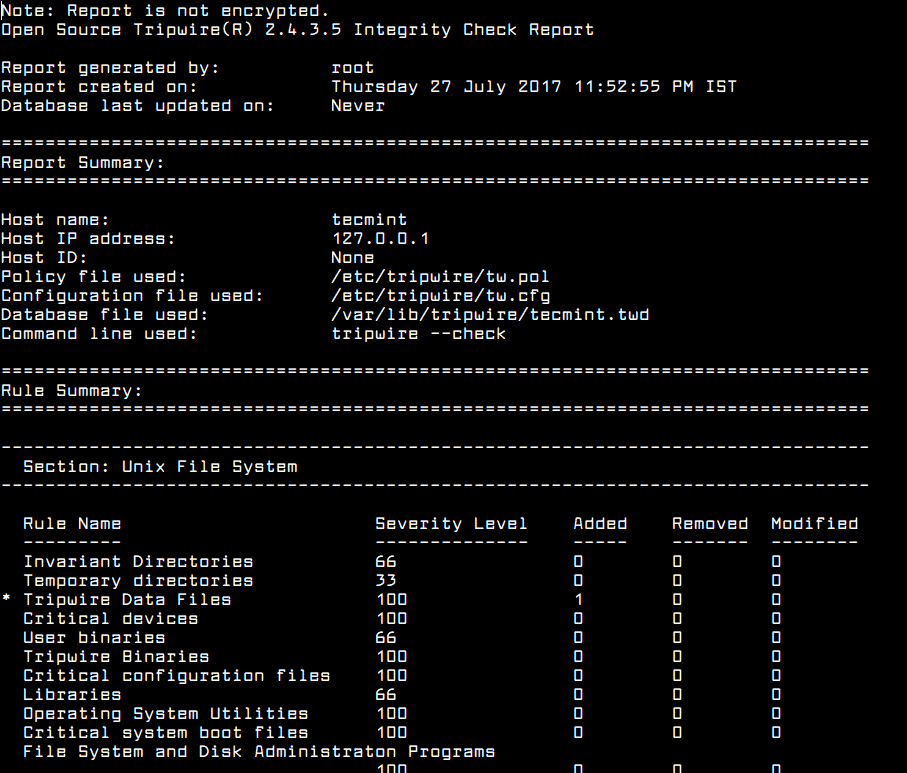
Tripwire develops a wide range of security and compliance software solutions. They offer a free and open-source HIDS that is capable of checking the integrity of files and send alerts when there's been file change.
Key Features:
- Real-Time Change Detection: Provides real-time monitoring of file systems and registries, detecting any unauthorized changes to files, configurations, or system settings instantly.
- Automated Compliance: Reduce penalties and fines by continuously monitoring systems and comparing their configurations to predefined policies.
- Extensive Integrations: Offers seamless integration with a wide range of security and IT management tools, including SIEMs, ticketing systems, and vulnerability scanners.
- Asset Discovery and Inventory: Gives information about the inventory of their IT and OT assets.
Why do we recommend it?
We recommend Tripwire for its real-time change intelligence and threat detection capabilities, offering proactive system hardening and automated compliance enforcement. With features like real-time change detection, automated compliance checks, and extensive integrations, Tripwire ensures enhanced security posture, reduced audit cycles, and cost savings for organizations.
When you start with Tripwire for the first time, you'll need to create a file baseline state by configuring a policy file. This policy file contains information about which files or folders to check and the attributes, such as permissions, type, hashes, etc.
The software will continuously compare the current filesystem state with this baseline. When it detects a difference in a filesystem, it will initiate an alert. You can also generate detailed reports that contain information about files, directories, devices, configuration, drivers, utilities, etc.
Who is it recommended for?
Tripwire is recommended for organizations with both IT and OT assets, allowing them to apply stringent cybersecurity controls across their entire environment. It is used by cybersecurity experts and professionals in industrial organizations to bridge the gap between IT and OT security, ensuring comprehensive monitoring and protection of assets.
Pros:
- Test Vulnerability of Network: Identify potential vulnerabilities and security weaknesses. By continuously monitoring and analyzing network configurations, file systems, and registries in real-time, Tripwire helps identify.
- Advanced Threat Intelligence: Advanced threat intelligence capabilities, leveraging threat feeds and analytics to provide proactive threat detection and response, enhancing overall security posture.
- Customizable Remediation Actions: Tripwire allows organizations to define customizable remediation actions for detected security incidents, enabling automated response or manual intervention based on specific requirements and policies.
Cons:
- Issue with Reporting System: Some users would like the data reporting to be more granular.
Free and open-source. Download Tripwire HIDS open-source from the Github’s project.
9. IBM Security IDS / Maas360
IBM is one of the oldest security providers in the market. It provides integrated security solutions to protect IT assets from threats. The IDS/IPS management module offers comprehensive monitoring, analysis, and management for your network.
The IBM IDS provides both HIDS and NIDS capabilities. The service can detect intrusion in the network and “extrusions” from the host. With this service, you can create and manage advanced policies to monitor threats efficiently.
Key Features:
- Threat Analysis: Useful for cyber security experts to provide comprehensive analysis and insights into emerging threats.
- Define IDS Policies: Defines specific policies for intrusion detection system (IDS) operations, including parameters for detecting attacks, scans, and network traffic anomalies.
- Intrusion Detection Events Page: Provides a centralized dashboard displaying real-time alerts and events generated by the intrusion detection system to react quickly to potential security incidents.
- Real-Time Intrusion and Extrusion Detection Notification: Offers immediate alerts and notifications in real-time upon detecting unauthorized intrusion attempts or data exfiltration activities.
Why do we recommend it?
We recommend IBM Security IDS / MaaS360 for its robust Threat Management capabilities. With MTM detecting and remedying malware from suspicious apps preemptively, it effectively mitigates security risks. Its built-in threat detection and response features prevent various threats, including phishing, man-in-the-middle, and crypto-jacking attacks, ensuring strong endpoint protection.
You can also collect logs from different IDS/IPS vendor devices and view them in the single portal. IBM IDS systems can detect different types of threats in a host or network, such as attacks, extrusions, scans, traffic regulation, and dynamic throttling.
IBM offers a variety of products that can detect intrusions at the host and network level. Their Security SaaS can help you detect threats at the cloud, and their Mainframe security product can help you detect intrusions on the on-premises.
One of the products that offer real-time threat detection, insights, and remediation for endpoints is IBM’s MaaS360. This product is an AI and cloud approach to unified endpoint management.
Who is it recommended for?
This tool is useful for risk management. It has advisors who provide insights into device and user risks. It has a risk score that is constantly updated, which helps IT Admins gain constant visibility on vulnerabilities and proposed solutions. If you need a high level of mobile device security posture, this tool is definitely a good choice.
Pros:
- Device Management Supported: Manage and secure your smartphones, tablets, and laptops from a centralized platform.
- Identity Management Supported: Involves managing user identities, access permissions, and authentication mechanisms, ensuring secure access to corporate resources.
- Policy Recommendation Engine: Provides recommendations to help organizations strengthen their security posture and compliance with industry regulations.
- Granular Patch Management: Easily deploy and manage software patches across their device fleet, ensuring devices are up-to-date and protected against known vulnerabilities.
Cons:
- Issue with Microsoft Computers: Users with Microsoft computers faced issues while downloading emails. Also, the graphics didn't look great on the PC.
Price: IBM MaaS360 comes in four different editions.
- Essentials ($4.00 per device/month)
- Deluxe ($5.00 per device/month)
- Premier ($6.25 per device/month)
- Enterprise ($9.00 per device/month)
Download: Get your free trial of IBM MaaS360 for 30 days!
10. Lacework
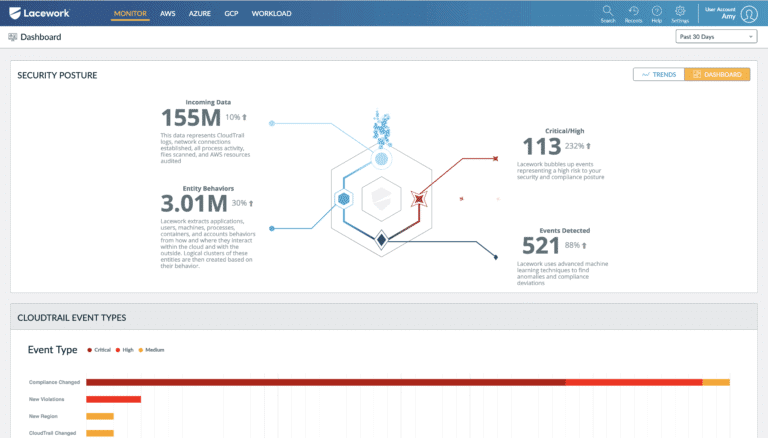
Laceworks develops advanced end-to-end cloud security solutions that allow you to view the risk across workloads on the cloud or containers.
One of their products if the anomaly-based Host Intrusion Detection System (HIDS). This solution can identify any unusual activity that is happening across workloads and accounts in the host.
Key Features:
- Interconnected Insights: Analyzes the relationships between different entities and connects the dots between various events to understand the threats and incidents.
- Behavior-Based Threat Detection: Monitors the behavior of users, applications, and resources in real time across the cloud infrastructure.
- Comprehensive Cloud Security: By providing a unified security solution for cloud workloads, containers, and serverless applications, Lacework helps organizations mitigate risks and maintain compliance with regulatory requirements.
Why do we recommend it?
We recommend Lacework because it offers behavior-based threat detection. Its Cloud Native Application Protection Platform (CNAPP) visualizes your cloud's relationships, tracks normal behavior, and alerts you to any suspicious changes automatically without needing complex configuration. This ensures proactive security monitoring and protection for your cloud environment.
The Lacework comes with an easy-to-navigate dashboard. It shows incidents at a high level of details. From this dashboard, you can visualize the interactions between cloud entities and search for events anywhere across the cloud.
With Lacework, you can detect abnormal changes in behavior and threats across your workloads, containers, and the cloud. Lacework can also help achieve compliance for regulations such as SO2 2, PCI DSS, HIPAA, and others.
Who is it recommended for?
It is recommended for organizations who need help with the development process. By providing tools like software composition analysis (SCA), static application security testing (SAST), and infrastructure as code (IaC) security, it helps developers to address risks before they reach production, enhancing code security and vulnerability management.
Pros:
- Critical Alerts: Alerts according to the seriousness of the issue so you can take action according to priority levels.
- Security Compliance: Works from a compliance perspective, which means it generates reports according to multiple compliance standards.
- Intrusion Detection Capabilities: You can set up an agent in cloud workloads, and it instantly creates tickets when malicious activities or anonymous behavior are detected.
Cons:
- Remediation: Users want improvement in remediation features. Also, it needs to work on integration with third-party SIEMs.
For more information on Lacework pricing, get a quote.
11. Security Onion
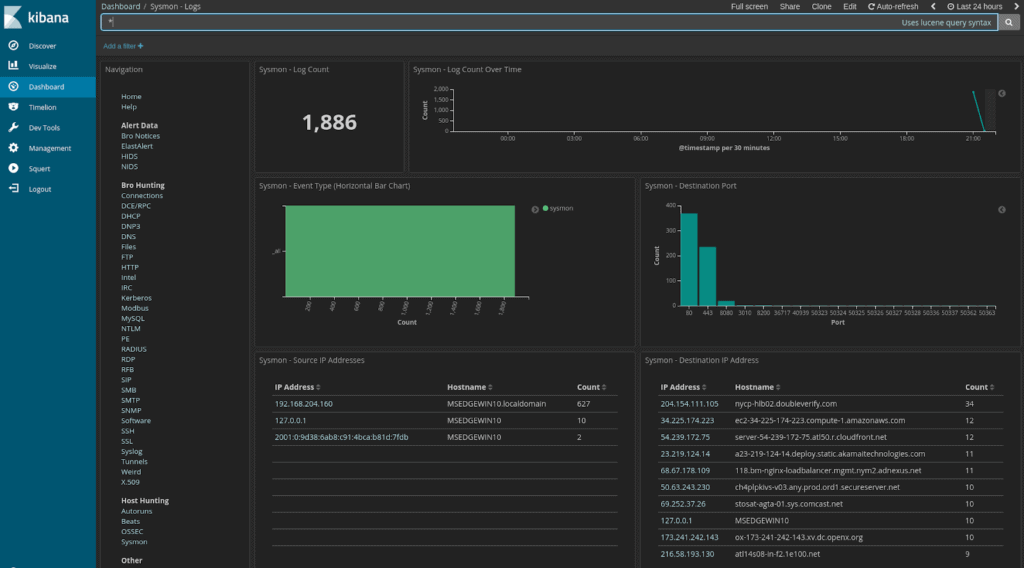
Security Onion is a free and open-source Linux distro for Network Security Monitoring (NSM), IDS, and log management solution. It contains a wide range of security tools, including HIDS functionalities. It integrates three core components, full packet capture, NIDS/HIDS, and analysis tools.
Key Features:
- Open Source and Extensible: Open-source platform with a vibrant developer and contributor community that can be adjusted and extended to meet specific security requirements.
- Collaborative Security Operations: Contains built-in collaboration tools like chat, notes, and case management to help with teamwork and communication.
- Packet Capture and Analysis: Helps identify security incidents, analyze network traffic patterns, and troubleshoot network issues.
- Threat Intelligence Integration: Stay up-to-date with information on known threats, vulnerabilities, and malicious IP addresses.
Why do we recommend it?
We recommend Security Onion for its ability to provide a comprehensive view of network traffic, facilitating quick threat identification and response. With its robust features for threat hunting, enterprise security monitoring, and log management, Security Onion stands as a powerful tool to safeguard your network infrastructure effectively.
With Security Onion, you can create and deploy multiple distributed sensors in your enterprise network. The sensors see and store as much information as possible from these security tools.
Security Onion integrates with other open-source security tools to achieve this high level of protection. Tools such as Snort, Suricata, Bro, Wazuh, OSSEC, Sguil, CyberChef, Squert, Kibana, NetworkMiner, Elasticsearch, Logstash, and more.
Tools that Integrate with Security Orion:
- HIDS alerts with Wazuh and OSSEC.
- NIDS alerts from Snort and Suricata.
- Full packet capture with netsniff-ng.
- Analysis-driven NIDS with Bro.
- Host data through Beats, Wazuh, syslog, and more.
- Session data with Bro.
- Visibility into the event data with Sguil.
- Deep data analysis with Kibana.
- Analyze and visualize NIDS/HIDS alerts with Squert.
Who is it recommended for?
Security Onion is recommended for cybersecurity experts and IT professionals who need advanced tools for analyzing and responding to security alerts. It offers valuable context for alerts, facilitates collaboration among team members, and enables the deployment of multiple sensors across enterprise networks to gather comprehensive security data.
Pros:
- Easily Learnable: Due to its easy UI, anyone can learn its functionalities and securely detect threats using monitoring capabilities.
- Vulnerability Assessment: Actively identify and remediate vulnerabilities, reducing the risk of potential exploits and data breaches.
Cons:
- Some Stability Issues: Users experienced some crashes while reporting, which could be made better with improvements in UI and graphical representation.
Free and open source. Security Onion from the GitHub project.
Conclusion
NIDS don’t have the advantage over HIDS. Although NIDS can look at incoming and outgoing traffic and detect intrusions at a network-level, they don’t have the grain-level security that HIDS can provide at the host.
HIDS can detect attacks that do not involve the network; they can monitor changes in critical system files, and even analyze what an application is doing. There are tons of security solutions, from SIEM, NIDS, HIDS, NIPS, etc.
Trying to select the appropriate software can be overwhelming. They all have the same goal of protecting your network and servers, but they do it differently. Nearly all of the best HIDS tools shown here are full HIDS tools, but there are some that fall into the SIEM category. They can do pretty much everything, including HIDS functionalities.
There are a variety of commercial, free-license, free trials, open-source HIDS tools. Most of them, like OSSEC, are open-source and free but more advanced software like SIEM that integrates everything comes with a price. You can start with ManageEngine Event Log Analyzer and SolarWinds Security Event Manager which are great SIEMs, and offer free license.
Host-Based Intrusion Detection Systems (HIDS) FAQs
What is an example of HIDS?
Some of the best host-based intrusion detection system (HIDS) tools are free to use. This category includes OSSEC, Advanced Intrusion Detection Environment (AIDE), and Samhain. There is a fine line between HIDS and SIEM because the Security Information Management part of Security Information and Event Management is based on the collection of log files, the same as HIDS. Thus some systems that are HIDS are also defined as SIEM, Wazuh is an example of this phenomenon. SolarWinds Security Event Manager and ManageEngine EventLog Analyzer are two examples of paid HIDS packages.
What does a HIDS do?
A host-based intrusion detection system (HIDS) searches through collected log messages for signs of unusual activity. This activity might indicate the presence of an intruder or software introduced onto the system by hackers to gather information and steal data.
Is antivirus a HIDS?
Antivirus and HIDS operate in different ways. An antivirus system operates on one endpoint and looks for harmful malware. This can be implemented through the identification of the files of malware by examining each file’s characteristics and comparing them against a signature database. Antivirus systems have recently evolved into Endpoint Detection and Response (EDR) systems, which look for anomalous behavior on an endpoint. An EDR acts like a HIDS but operates on just one endpoint. A HIDS collects log messages from all devices connected to a network, centralizes them, and consolidates them into a common format so that they can be held in a single database and searched for signs of anomalous behavior.