We may earn a commission if you make a purchase through the links on our website.
What is Network Segmentation?
UPDATED: June 22, 2024
Understand the principles of network segmentation, and put them into action with the right tools.
By splitting a network into smaller, more controllable portions, network segmentation allows enterprises to mitigate the impact of potential security breaches. The process of splitting a network into smaller subnetworks, each with its own set of security policies and access controls, is known as network segmentation. Organizations can limit the breadth of potential security breaches, contain malware transmission, and prevent unauthorized access to vital assets by doing so.
Implementing network segmentation can be difficult, necessitating careful design and implementation. When developing a network segmentation strategy, organizations must carefully consider their network topology, the specific needs and requirements of their business, and the available tools and technologies.
Fortunately, numerous tools and methodologies are available to assist enterprises in properly implementing network segmentation. These technologies can help firms safeguard their important assets and enhance overall network performance by simplifying network design, monitoring, and security.
In this article, we will look at the fundamentals of network segmentation, such as the different types of segmentation, implementation methods, and the benefits of employing a network segmentation approach. We will also look at the SolarWinds Network Configuration Manager, a complete network configuration and security solution that can make network segmentation easier to adopt. Readers will have a greater grasp of network segmentation and its role in network security by the end of this essay, as well as the tools available to help them implement this strategy efficiently.
Understanding Network Segmentation
Network segmentation, as the name implies, is the process of breaking down a computer network into smaller subnetworks known as segments to improve security and performance. Network segmentation is an important strategy that assists organizations in improving their network security posture by establishing numerous layers of defense against intrusions.
The fundamental goal of network segmentation is to minimize the propagation of a cyberattack in the event of a breach. Attackers are prevented from moving laterally across a network by isolating distinct sections of the network. They are instead restricted to the part they have broken. This decreases the possibility of damage and data loss from a successful cyberattack.
Network segmentation also assists companies in optimizing network performance by ensuring that high-priority traffic receives the necessary bandwidth. Network administrators can divide a network into segments based on the kind of traffic, such as voice, video, data, and IoT devices, and ensure that each segment has enough bandwidth to accommodate the traffic types.
Compliance with regulatory standards is another critical feature of network segmentation. Many legal regulations, like the Payment Card Industry Data Security Standard (PCI DSS), demand network segmentation for handling sensitive data. Organizations can achieve these compliance standards and avoid hefty fines by segmenting their networks.
Implementing network segmentation necessitates meticulous planning and design. Organizations must identify the essential assets and data that must be safeguarded and devise the appropriate segmentation plan to fulfill their security and performance objectives. They must also ensure that the network segmentation strategy is consistent with their overall network architecture and business goals.
Thanks to network segmentation solutions like SolarWinds Network Configuration Manager, network segmentation has become more accessible and easier to implement. These technologies automate network segmentation, making it easier for network administrators to build and administer network segments, specify access control policies, and monitor network activities.
Types of Network Segmentation
Network segmentation is an important approach for enhancing network security and performance. Organizations can employ many types of network segmentation to safeguard their networks and optimize traffic flow.
- Physical Segmentation: The classic method of network segmentation is physical segmentation. Network components such as servers and switches are physically split into distinct network segments using firewalls or routers in this sort of segmentation. Physical segmentation enhances security by establishing a physical barrier between network portions. However, it can be costly and time-consuming to implement, and it might limit the network's flexibility and agility.
- Virtual Segmentation: Virtual segmentation, often known as network virtualization, is a software-based technique for constructing virtual networks on top of physical network infrastructure. Multiple virtual networks utilize the same physical network equipment but are segregated from one another using virtual firewalls or switches in this sort of segmentation. Because it can be established and adjusted fast and simply, virtual segmentation is less expensive and more versatile than physical segmentation. It also allows businesses to construct various virtual networks for different reasons, such as testing, development, and production, while still utilizing the same physical infrastructure.
- Logical Segmentation: Physical and virtual segmentation are combined in logical segmentation. Logical barriers are set between devices in this type of segmentation to restrict access to specific network resources. Access control lists (ACLs), VLANs, and software-defined networking (SDN) can all be used to create logical segmentation. Logical segmentation is more adaptable and agile than physical segmentation, since it can be quickly and readily implemented and modified. It is also less expensive than physical segmentation because no additional hardware is required.
- Network Micro-Segmentation: Network micro-segmentation is a more recent technique to network segmentation that enables granular security controls for specific applications or workloads. Network traffic is segregated at the application or workload level rather than the network level in this sort of segmentation. The use of software-defined policies that restrict traffic flow between distinct applications or workloads allows for network micro-segmentation. This sort of segmentation provides a high level of security by restricting lateral network mobility, but it requires careful planning and monitoring.
Implementing Network Segmentation
Implementing network segmentation necessitates careful planning and execution to guarantee that the organization's security and performance objectives are met. Here are some best practices for network segmentation implementation:
- Identify your security and performance objectives Before deploying network segmentation, you must first identify your security and performance objectives. What assets do you want to safeguard? What types of threats do you wish to protect yourself against? Which performance indicators do you want to improve? Defining your goals will assist you in selecting the appropriate type of segmentation and identifying the appropriate network resources to segment.
- Select the appropriate form of segmentation As stated in the previous section, there are various types of network segmentation, each with its own set of benefits and drawbacks. Choose the sort of segmentation that best satisfies your security and performance objectives while also being compatible with your network infrastructure and resources.
- Identify the network resources to segment Once you've defined your goals and selected the type of segmentation, you'll need to figure out which network resources to segment. Servers, workstations, network devices, and applications may be included. Determine which resources are vital to the operations of your firm and require the highest level of security and performance.
- Develop a segmentation plan Create a segmentation strategy that contains the scope of the segmentation, the segmentation technique, the segmentation tools and technologies, and the implementation timeframe. The roles and duties of the parties involved in the implementation should also be included in the plan.
- Test and validate the segmentation Test and validate the plan in a controlled environment before implementing the segmentation. This will assist in identifying any problems or gaps in the strategy and ensuring that the segmentation satisfies your security and performance objectives.
- Monitor and manage the segmentation Once the segmentation is in place, continue to monitor and manage it. Monitoring network traffic, spotting anomalies or threats, and changing segmentation as needed to maintain maximum security and performance are all part of this process.
It is critical to include all essential stakeholders, including IT personnel, security teams, and business leaders when establishing network segmentation. It's also critical to ensure that everyone knows the aims and benefits of network segmentation, as well as how it fits into the overall cybersecurity strategy of the organization.
Using a network segmentation tool can allow you to cut through a lot of the previously listed steps. These tools provide several convenient features that can assist with implementation, testing, and management.
SolarWinds Network Configuration Manager is one such product that can aid with network segmentation implementation. This program provides a single platform for setting and administering network devices such as firewalls and routers, which are essential for network segmentation implementation. It can also aid in the automation of network configuration activities as well as give real-time visibility into network performance and security. Organizations can execute network segmentation more efficiently and effectively using SolarWinds Network Configuration Manager, lowering the risk of security breaches and boosting network performance.
Benefits of Network Segmentation
We discussed briefly why you might look into implementing network segmentation, but let's expand on the kind of benefits that can be gained by implementing it into your network structure.
Network segmentation adds an important layer of security to enterprises. Organizations can better restrict access to important assets and reduce the risk of security breaches by splitting the network into smaller portions. If an attacker gains access to one segment, they will be unable to access other segments, restricting their ability to cause damage. Organizations can also apply different security policies to distinct segments based on the amount of risk and criticality of the assets in each section.
Network segmentation can also boost network performance by decreasing congestion and increasing network efficiency. Organizations can limit broadcast traffic, which can consume a large amount of network capacity, by segmenting the network into smaller subnets. This can increase network throughput and minimize latency, especially for low-latency applications like video conferencing or online gaming.
Network segmentation can also simplify and improve network management. IT workers may better focus on controlling each segment separately by separating the network into smaller parts, decreasing the complexity of network management. Because faults are restricted to certain segments, this can make troubleshooting network issues and identifying the source of problems easier.
Network segmentation can also assist enterprises in meeting regulatory obligations such as HIPAA and PCI-DSS. Organizations can reduce the risk of non-compliance and the associated penalties by using network segmentation, which keeps sensitive data separate from non-sensitive data.
Network segmentation can also save money by minimizing the need for costly security measures like firewalls across the entire network. Instead, enterprises can concentrate their efforts on safeguarding essential segments where the risk is greatest while relying on less expensive security solutions for less critical portions.
Network Configuration Management Tools
Implementing network segmentation may be a complex process, and various tools and technologies are available to assist organizations in planning, implementing, and managing network segmentation.
Network configuration management solutions, such as SolarWinds Network Configuration Manager, are critical components of network segmentation implementation. These technologies provide a consolidated platform for managing network configuration files, allowing IT workers to make changes to network configurations across various devices fast and easily.
Creating and managing configuration templates is one approach to implementing network segmentation with network configuration management technologies. Configuration templates give a consistent method to network segmentation, allowing IT workers to install new devices with the proper segmentation policies fast and efficiently. Organizations may ensure that all new network devices are correctly configured by establishing and managing configuration templates, lowering the risk of misconfiguration and boosting network security.
SolarWinds Network Configuration Manager
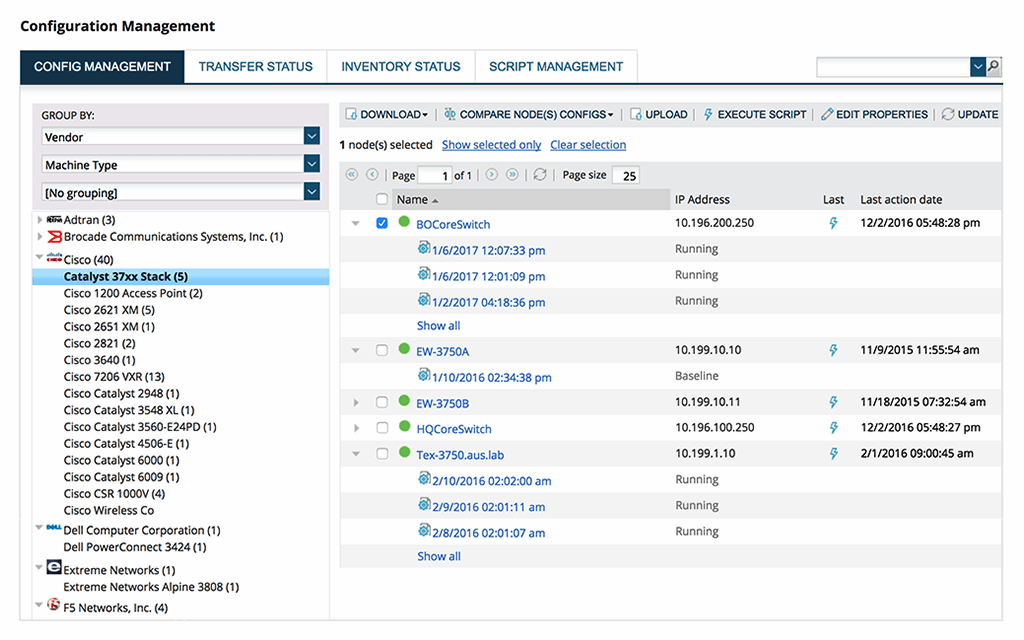
The SolarWinds Network Configuration Manager (NCM) is a robust network configuration management solution that offers a centralized platform for managing network configurations across numerous devices. IT workers may quickly and simply update network configurations and implement segmentation requirements with SolarWinds NCM. This tool can assist enterprises in improving network performance and security while lowering the chance of errors during network segmentation installation.
Key Features of SolarWinds NCM
- SolarWinds NCM provides a range of features that can help organizations implement network segmentation and improve network security.
- SolarWinds NCM can automate common processes such as network configuration backups, firmware upgrades, and configuration changes. This can save enterprises time and reduce the chance of errors during network segmentation implementation. The solution supports a wide range of network devices, including routers, switches, firewalls, and load balancers. IT personnel may utilize SolarWinds NCM to manage these devices' configurations from a single platform, maintaining consistency and lowering the chance of errors.
- SolarWinds NCM offers configuration templates, which provide a systematic method to network segmentation. Organizations may ensure that all new network devices are correctly configured by establishing and managing configuration templates, lowering the risk of misconfiguration and boosting network security. The product offers policy reporting, allowing IT employees to rapidly generate reports demonstrating network device compliance with segmentation regulations. These reports can assist enterprises in identifying noncompliant devices and taking corrective action to improve network security.
How does SolarWinds NCM help with network segmentation?
The practice of separating a network into smaller, more secure subnetworks is known as network segmentation. This can assist enterprises in improving network security by reducing attack surfaces and preventing unwanted access to sensitive data. IT workers must set up network devices with appropriate segmentation policies to implement network segmentation.
By offering a single platform for controlling network configurations, SolarWinds NCM may help with network segmentation. IT workers can use this application to generate and manage network device configuration templates, ensuring that all new devices are correctly configured with suitable segmentation policies. SolarWinds NCM also offers policy reporting, allowing IT employees to rapidly generate reports demonstrating network device compliance with segmentation regulations.
Conclusion
Network segmentation is an important strategy for improving network security and lowering the risk of cyber threats. Organizations can prevent unwanted access, isolate potential security breaches, and improve overall network performance by splitting down a network into smaller pieces and adopting suitable security measures.
There are numerous approaches and technologies available to assist enterprises with network segmentation implementation, each with its own set of features and benefits. When selecting a network segmentation tool or method, it is critical to carefully consider your organization's specific needs and requirements.
When done effectively, network segmentation can greatly improve an organization's security posture. Organizations can better safeguard their important assets and decrease the risk of data loss or downtime by lowering the attack surface, restricting the breadth of potential security breaches, and enabling granular control over network access. Network segmentation can have major benefits for network performance and management, in addition to boosting security. Organizations can increase network efficiency and reduce the risk of bottlenecks or downtime by enabling more granular control over network access and prioritizing vital traffic.
Overall, network segmentation is a critical step for any organization looking to improve network security and performance. Organizations can reap considerable benefits and better safeguard their important assets from potential cyber-attacks by carefully selecting a network segmentation tool or method and following best practices for implementation.