We may earn a commission if you make a purchase through the links on our website.
The Best Network Segmentation Tools

UPDATED: July 1, 2024
Secure and organize your network through these premium network segmentation tools.
By confining access to critical data and limiting the impact of any potential breaches, network segmentation is one effective strategy to protect against these risks. The process of splitting a network into smaller subnetworks, or segments, and implementing access control policies between them is known as network segmentation. This aids in the prevention of unwanted access to sensitive data and the containment of any potential security problems.
Here is our list of the best Network Segmentation Tools:
- ManageEngine Firewall Analyzer – EDITOR’S CHOICE This package lets you define security policies and implement them through firewalls around the network, including a set of coordinated access control lists to create zones of trust. Available for Windows Server, Linux, and AWS. Access a 30-day free trial.
- Tufin Orchestration Suite Provides a range of network segmentation capabilities, including automated policy management, risk analysis, and segmentation planning to help organizations control access to sensitive data and improve their overall security posture.
- SolarWinds Network Configuration Manager Offers network segmentation capabilities such as automated network device identification, configuration management, and compliance reporting.
- FireMon Security Manager Enables enterprises to enforce network segmentation policies and safeguard against cyber attacks by providing centralized management of firewall settings, risk assessment, and compliance reporting.
- Cisco TrustSec TrustSec offers policy-based access control, network segmentation, and network visibility to assist enterprises in enforcing network segmentation policies and protecting against cyber attacks.
- F5 Networks BIG-IP BIG-IP offers a variety of network segmentation capabilities, including application delivery, traffic management, and security features, to assist enterprises in enforcing network segmentation regulations and protecting themselves from cyber-attacks.
Implementing and administering network segmentation, on the other hand, can be a difficult process, particularly for enterprises with big and sophisticated networks. This is when network segmentation software comes in handy. Network segmentation tools are software solutions that aid in the management and enforcement of network segmentation policies. These solutions provide visibility into network traffic and user behavior, automate policy management, and notify users of potential security issues in real-time. They assist businesses in identifying and prioritizing security risks, allowing them to better deploy resources and respond to security crises.
Network Segmentation Tool Priorities
There are several important elements to consider when looking for a network segmentation tool. First and foremost, the solution should be simple to use and integrate with your current network architecture. It should have a simple user interface and be capable of automatically discovering and classifying all network assets. The tool should also support other network segmentation methods, such as virtual LAN (VLAN) and software-defined segmentation. This allows enterprises to select the optimal solution based on their specific needs and requirements.
Another critical consideration is the tool's capacity to automate policy management. The tool should be capable of enforcing network segmentation regulations across all devices and endpoints, such as firewalls, switches, routers, and servers. This lowers the possibility of human error and ensures that policies are followed consistently.
The tool should also enable real-time visibility into network traffic and user behavior. It should be able to monitor network activity, detect anomalies, and offer security alerts. This allows firms to respond to security problems promptly and mitigate the effect of any breaches. Finally, the technology should be scalable and adaptable to the needs of your firm. It should be able to support huge and complex networks while also being adaptable to changing security requirements.
The Best Network Segmentation Tools
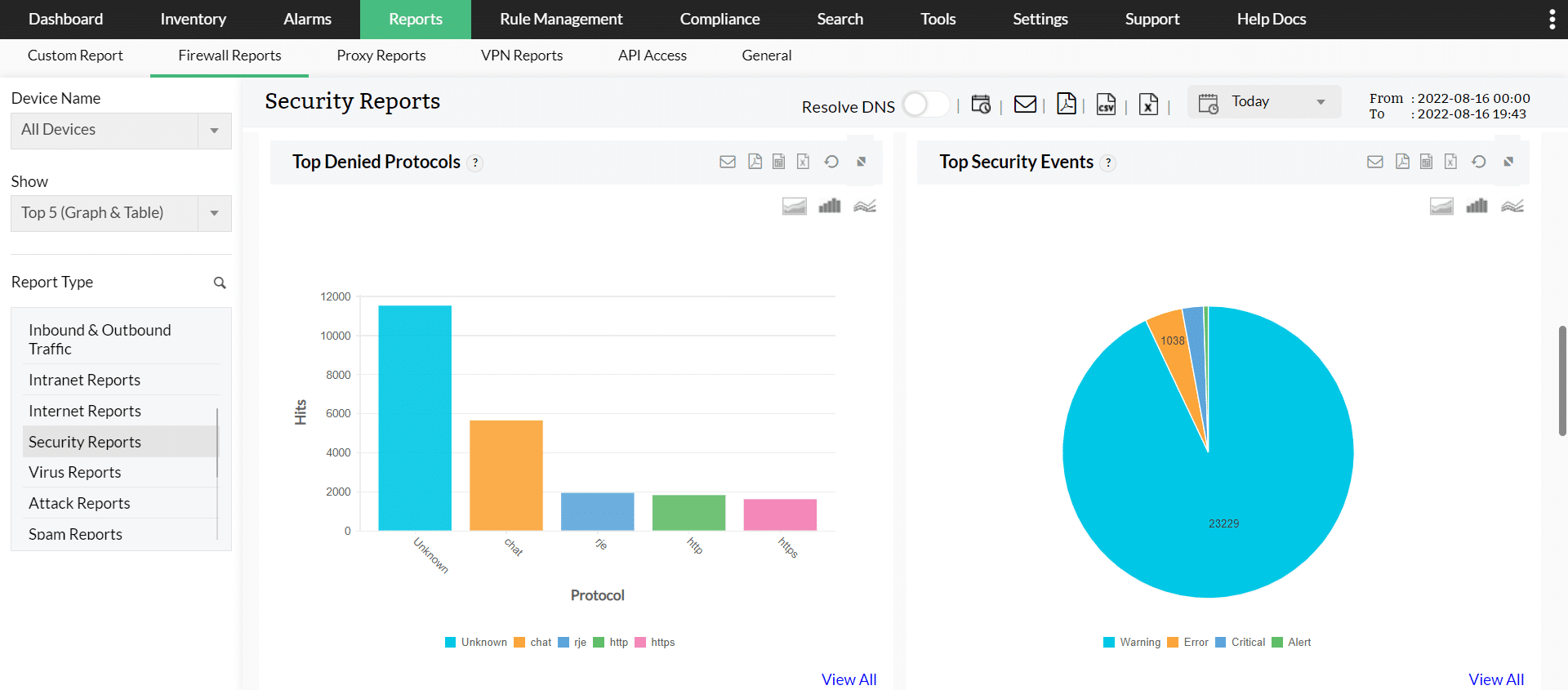
1. ManageEngine Firewall Analyzer – FREE TRIAL
ManageEngine Firewall Analyzer is a network security management application that provides real-time visibility into network traffic and security events. The software provides a wide range of features and capabilities that assist enterprises in more efficiently monitoring, analyzing, and managing their network security architecture.
One of Firewall Analyzer's primary advantages is its ability to provide real-time monitoring and alerting of network traffic. The software may monitor firewall logs and produce warnings based on established rules and policies, assisting IT teams in identifying possible security issues and taking corrective action promptly.
Another useful feature of Firewall Analyzer is the ability to generate thorough reports and analytics on network traffic and security events. The software may generate a variety of reports, such as firewall policy reports, traffic reports, bandwidth use data, and others. These reports assist enterprises in identifying network traffic trends, patterns, and anomalies, which may then be used to improve network security and optimize network performance.
ManageEngine Firewall Analyzer also provides some compliance management features that assist enterprises in meeting regulatory standards such as PCI-DSS, HIPAA, and GDPR. The platform generates automated compliance reports and dashboards, allowing IT teams to discover possible compliance concerns and take corrective action promptly.
The cost of Firewall Analyzer is determined by the number of firewalls monitored and the number of users who access the software. There are three editions: Standard, Professional, and Enterprise. The base package for the Standard and Professional editions caters to 60 devices and the Enterprise edition is intended for use on WANs and starts with a capacity of 1,200 devices.
A potential disadvantage is a lack of price flexibility. While Firewall Analyzer comes in three editions with varying levels of features and capabilities, the price is based on a set number of firewalls and users. As a result, enterprises may find it challenging to scale the software as their demands change over time.
Be sure to gain access to the 30-day free trial.
EDITOR'S CHOICE
ManageEngine Firewall Analyzer is our top pick for a network segment tool because it supports you through the complicated processes of formulating access control lists to enforce zones of trust across your network. The system provides insights into current traffic patterns through the firewall and shows how current controls are succeeding or failing. The package can plug into IDS and IPS tools that might be hosted on the same box as your firewall or integrated into it. This allows you to monitor any dynamic firewall rule creation activity and analyze the effectiveness of the automated security systems in which you invested. The Firewall Analyzer helps with compliance management for a range of standards including SOX and PCI DSS.
Download: Access a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/firewall/download.html
OS: Windows Server, Linux, and AWS
2. Tufin Orchestration Suite
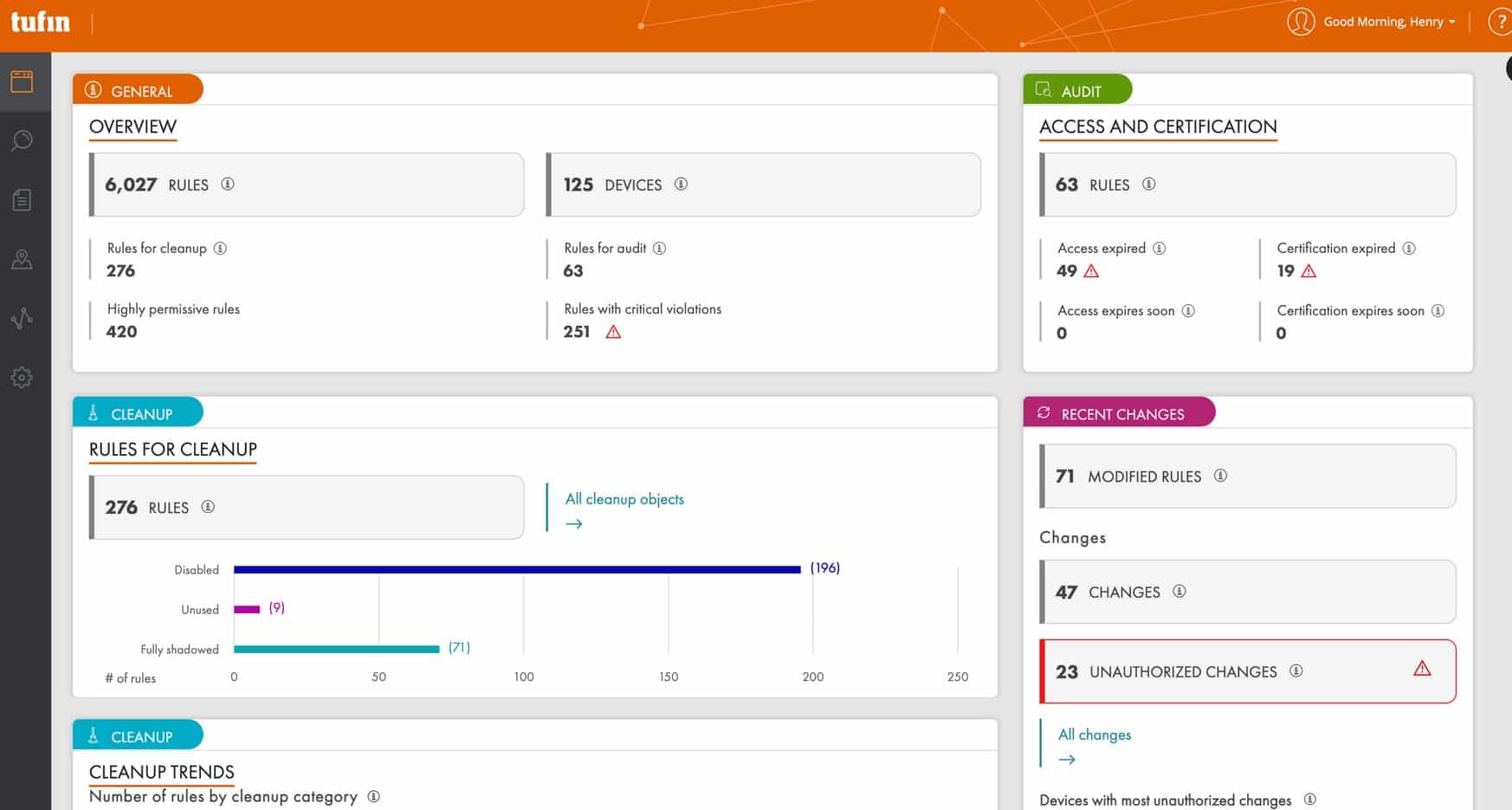
Tufin Orchestration Suite is a network security automation technology that provides organizations of all sizes with security and compliance capabilities. The platform includes various features, services, and connectors that help enterprises manage their network security infrastructure more efficiently and effectively. The Tufin Orchestration Suite is made up of numerous modules that can be purchased separately or as a package.
The ability to automate firewall rule management is a crucial feature of the Tufin Orchestration Suite. Tufin's policy-based automation engine analyzes the network traffic and creates and enforces firewall rules based on established policies. This reduces the risk of misconfigurations and guarantees that enterprises' networks are constantly in compliance with regulatory requirements.
Tufin Orchestration Suite also can provide end-to-end visibility and control over network security settings. Organizations can simply monitor and manage all of their security rules from a single spot thanks to its integrated policy management console. This makes it easier for IT teams to detect and address possible security problems before they harm.
One disadvantage of the Tufin Orchestration Suite is its complexity. The platform has a plethora of features and functionalities, which can be intimidating for enterprises unfamiliar with network security automation technologies. Furthermore, getting the platform up and running may necessitate a large investment in training and resources.
The product also contains a compliance management module that assists firms in meeting regulatory standards such as PCI-DSS, HIPAA, and GDPR. The module delivers automatic compliance reports, alerts, and dashboards to assist IT teams in identifying and correcting any compliance issues.
Tufin also integrates with a variety of additional security and networking products, including SIEMs, ITSMs, and CMDBs. Tufin's capabilities can thus be expanded and integrated with other security and networking solutions to create a more comprehensive security infrastructure.
The platform is normally offered through Tufin's network of approved resellers. However, the company does provide a free trial of its platform, which gives you access to all the Tufin Orchestration Suite modules for a short time. Customers can also ask Tufin's sales staff for a personalized estimate based on their individual needs. A major disadvantage is the lack of pricing transparency. While Tufin provides a free trial and tailored quotations, the lack of publicly available pricing information makes it difficult for enterprises to compare Tufin Orchestration Suite to other network security automation technologies on the market.
3. SolarWinds Network Configuration Manager
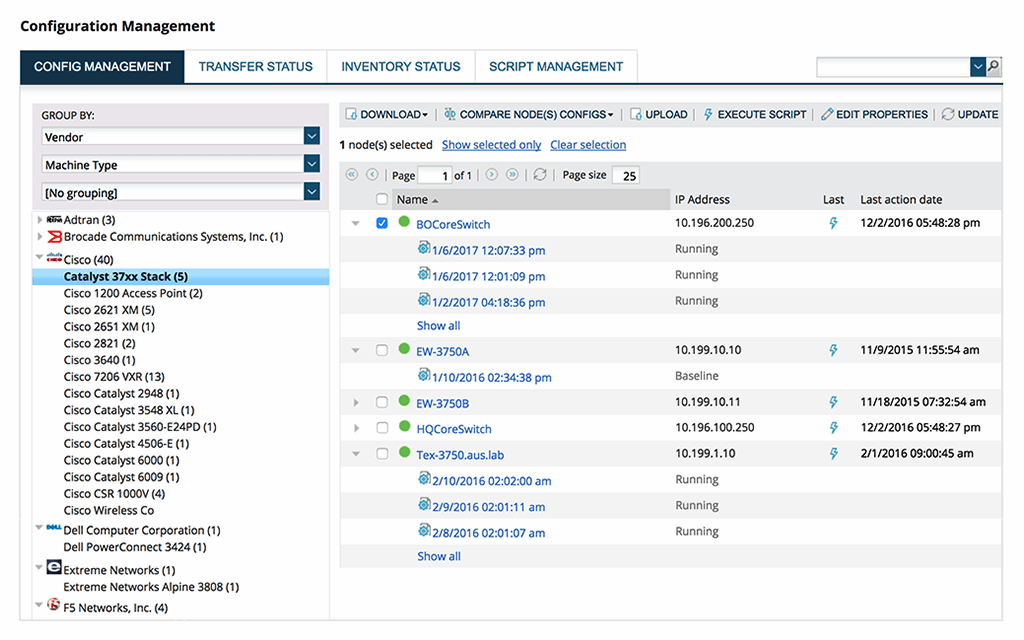
SolarWinds Network Configuration Manager is network configuration and change management software that is meant to assist IT teams in automating and reducing network device administration activities. The program includes a variety of features and capabilities that allow businesses to effortlessly manage their network infrastructure, reduce downtime, and increase network security.
The ability to automate network setup activities is a significant feature of Network Configuration Manager. The program may automate activities like configuration backup and restoration, firmware upgrades, and policy enforcement, allowing IT professionals to concentrate on more important responsibilities. Furthermore, the software offers a single store of network device configurations, making it simple to trace changes and return to earlier configurations as needed.
Another useful feature of Network Configuration Manager is the ability to monitor and notify network device configurations in real-time. The software can detect changes in device setups and produce alerts based on established rules and policies. This enables IT teams to spot possible security problems and take corrective action more rapidly.
Network Configuration Manager also contains reporting and analytics tools. The program may produce reports on device settings, change history, compliance, and other topics, assisting enterprises in identifying trends and patterns in network device management. This data can be utilized to improve network performance, decrease downtime, and increase network security.
The cost of Network Configuration Manager is determined by the number of nodes handled. There are three editions of the software available: Standard Edition, Professional Edition, and Enterprise Edition. The Standard Edition offers basic network setup and change management capabilities, while Professional and Enterprise Editions have more extensive features and capabilities.
4. FireMon Security Manager
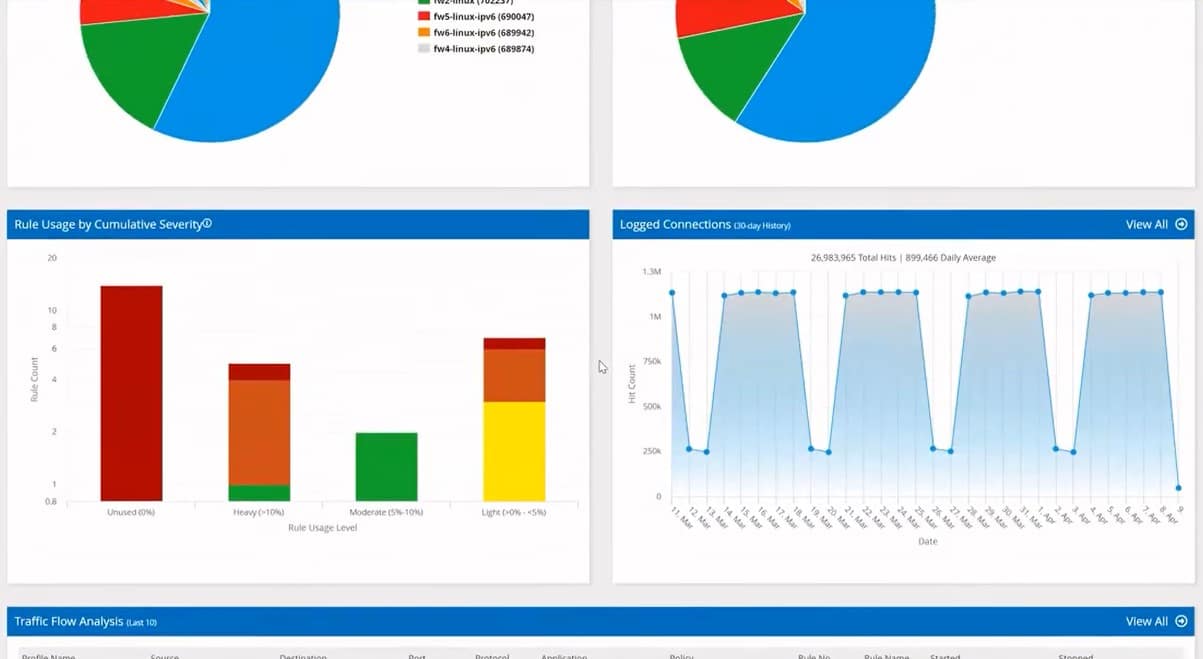
FireMon Security Manager is a network security management tool that assists enterprises in optimizing their security posture, reducing risk, and improving compliance. The program includes numerous features and capabilities that allow enterprises to monitor and manage their network security infrastructure in real-time.
One of FireMon Security Manager's primary advantages is its ability to provide centralized insight into network security infrastructure. The program can continuously monitor firewalls, routers, switches, and other security devices, offering a comprehensive picture of network security posture. This enables IT professionals to identify security weaknesses immediately and take corrective action to decrease risk.
The ability of FireMon Security Manager to automate security policy administration activities is another essential feature. Policy optimization, policy cleanup, and policy compliance verification can all be automated by the program, allowing IT professionals to focus on more important activities. Furthermore, the platform offers a unified library of security regulations, making it simple to track changes and ensure compliance.
FireMon Security Manager also has reporting and analytics features. The program may provide reports on network security posture, policy compliance, and other topics, assisting enterprises in identifying network security trends and patterns. This data can be utilized to improve network security, minimize risk, and increase compliance.
The cost of FireMon Security Manager is determined by the number of devices handled. There are three editions of the program available: the Basic Edition, the Standard Edition, and the Premium Edition. The Basic Edition provides fundamental network security management capabilities, whereas the Standard and Premium Editions give more advanced features and capabilities.
FireMon Security Manager is a robust network security management tool with numerous features and capabilities. While the software is sophisticated and may necessitate significant investment in training and resources, it can assist firms in optimizing their security posture, reducing risk, and improving compliance. FireMon Security Manager is a valuable solution for any organization trying to improve network security infrastructure management due to its centralized visibility, policy administration automation, and reporting and analytics capabilities.
5. Cisco TrustSec
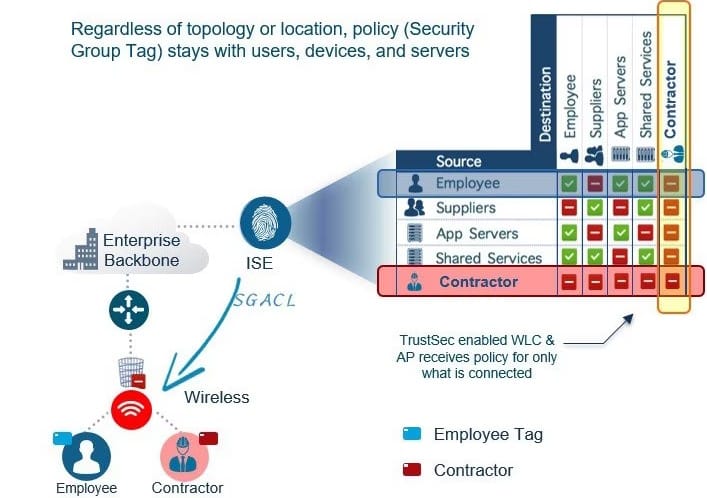
Cisco TrustSec is a network security solution that helps enterprises protect sensitive data by restricting network resource access. The program includes a number of features and capabilities that allow businesses to simply create and administer network security policies while also offering extensive visibility into network activities.
One of Cisco TrustSec's primary advantages is its ability to give secure access to network resources. identification-based access policies are used by the software to control resource access based on user identification, device type, and location. This ensures that only authorized users have access to important data and network resources, while simultaneously lowering the danger of unauthorized access.
The ability of Cisco TrustSec to automate security policy management is another essential feature. The software may automatically classify network resources and implement security measures based on their sensitivity. This enables IT professionals to administer network security policies quickly and effectively, while also guaranteeing that critical data is always safeguarded.
Cisco TrustSec additionally contains monitoring and reporting features. The software may monitor network activity in real-time and generate thorough reports on network activity, security incidents, and other topics. This data can be utilized to identify possible security problems promptly and take corrective action to mitigate risk.
Cisco TrustSec pricing varies depending on the size and complexity of the network environment. The software comes in several packages, including the Cisco TrustSec Starter Bundle, the Cisco TrustSec Foundation Bundle, and the Cisco TrustSec Advanced Bundle. Each bundle provides a unique collection of features and capabilities, allowing enterprises to choose the package that best matches their requirements.
One disadvantage of Cisco TrustSec is its complexity. The software has a plethora of capabilities and functions, which can be intimidating for enterprises unfamiliar with network security management solutions. Furthermore, getting the program up and running may necessitate a large investment in training and personnel.
6. F5 Networks BIG-IP
F5 Networks BIG-IP is a software-defined application delivery platform with advanced security and networking features such as network segmentation. The program allows enterprises to partition their networks by application, user, and device, while also providing advanced security features such as application firewall and DDoS protection.
BIG-IP's ability to provide flexible network segmentation is one of its primary characteristics. The program allows enterprises to divide their networks depending on certain applications, people, and devices, providing granular control over network resource access. This contributes to network security by restricting access to sensitive data and lowering the danger of unauthorized access.
BIG-IP also includes advanced security features like an application firewall and DDoS prevention. The program can detect and block harmful traffic in real-time, assisting in the prevention of cyber assaults and maintaining network uptime. Furthermore, the program can provide SSL/TLS offloading and encryption, allowing businesses to safely provide applications over the internet.
The program contains several management and monitoring features that enable enterprises to simply administer and monitor their network security rules. BIG-IP offers a centralized management console that enables IT teams to install and administer network security rules fast and efficiently, while also offering extensive visibility into network traffic. BIG-IP Advanced Firewall Manager, BIG-IP Local Traffic Manager, and BIG-IP Application Security Manager are among the software packages available. Each package has a unique collection of features and capabilities, allowing enterprises to choose the package that best matches their requirements.
BIG-IP from F5 Networks is a robust network security solution that offers a variety of features and capabilities for safeguarding network traffic and implementing network segmentation regulations. F5 Networks BIG-IP is a significant tool for any organization trying to better network security infrastructure management because of its flexible network segmentation capabilities, comprehensive security features, and management and monitoring capabilities. While the software is sophisticated and may necessitate significant investment in training and resources, it can assist enterprises in protecting sensitive data, reducing the danger of unwanted access, and improving network security posture.