We may earn a commission if you make a purchase through the links on our website.
The Best Next-Gen Firewalls

UPDATED: July 26, 2024
There are several important elements to consider while looking for the best next-generation firewalls. The security effectiveness of the firewall system comes first. Advanced threat detection and prevention capabilities, such as IPS, antivirus, anti-malware, and application control, should be provided by a robust NGFW. It should be capable of detecting and blocking known and unknown threats, such as zero-day attacks and Advanced Persistent Threats (APTs). To remain ahead of developing threats, look for NGFWs that use threat intelligence platforms and real-time updates.
Here is our list of the best Next-Gen Firewalls:
- Perimeter 81 FWaaS – FREE DEMO Offers advanced threat protection, network segmentation, and secure access controls. It provides centralized management, real-time monitoring, and scalable security for organizations of all sizes.
- Fortinet FortiGate Combines industry-leading security features with high-performance network capabilities. It offers advanced threat protection, SSL inspection, intrusion prevention, and application control, making it suitable for securing both small and large networks.
- Palo Alto Networks PA Series Known for its advanced security capabilities, including next-generation firewall features, threat intelligence, and integrated endpoint protection. It offers granular application visibility and control, along with protection against known and unknown threats.
- Check Point Next Generation Firewall Provides a comprehensive security solution that integrates firewall, intrusion prevention, application control, and threat prevention capabilities. It offers centralized management, advanced threat intelligence, and high-performance security for network protection.
- Cisco Firepower NGFW Combines advanced firewall capabilities with powerful threat intelligence and network visibility. It provides a Next-Generation Intrusion Prevention System (NGIPS), application control, and advanced malware protection to defend against sophisticated cyber threats.
- SonicWall NSa Series A range of next-generation firewalls that deliver robust security features, including deep packet inspection, network segmentation, and SSL/TLS decryption. It provides scalable solutions for small to enterprise-level networks.
Scalability and performance are also critical factors to consider. The NGFW should be able to handle your organization's network traffic volume without sacrificing performance. It should offer scalability options to handle future expansion and the increasing bandwidth requirements of modern networks. Look for NGFW solutions that are built on purpose-made hardware platforms and can scale as your company grows.
Another essential issue to consider is ease of use and management. A user-friendly interface and intuitive administration panel make firewall policy setup, configuration, and monitoring easier. Look for NGFWs with centralized management capabilities, which allow you to operate many firewalls from a single platform. This centralized solution simplifies policy management and guarantees consistent network security.
Integration with different security systems is an important factor to consider. NGFWs that can connect smoothly with other security technologies, including endpoint protection, SIEM systems, and threat intelligence platforms, provide a comprehensive and coordinated security ecosystem. Integration improves visibility, correlates security events, and streamlines incident response.
Consider the vendor's reputation and support services as well. Look for NGFW vendors who have a proven track record and favorable client feedback. Examine the vendor's pledge to provide frequent software updates, timely fixes, and quick technical assistance. A quality vendor will provide extensive documentation, training resources, and a dedicated support team to assist you with any issues or questions you may have.
Finally, the total cost of ownership of the NGFW solution must be assessed. Consider initial investment, license fees, continuing maintenance fees, and any extra features or services that may entail additional expenditures. To ensure that it aligns with your organization's budget and long-term security goals, evaluate the value supplied by the NGFW solution in terms of its security capabilities, scalability, performance, and simplicity of management.
The Best Next-Gen Firewalls
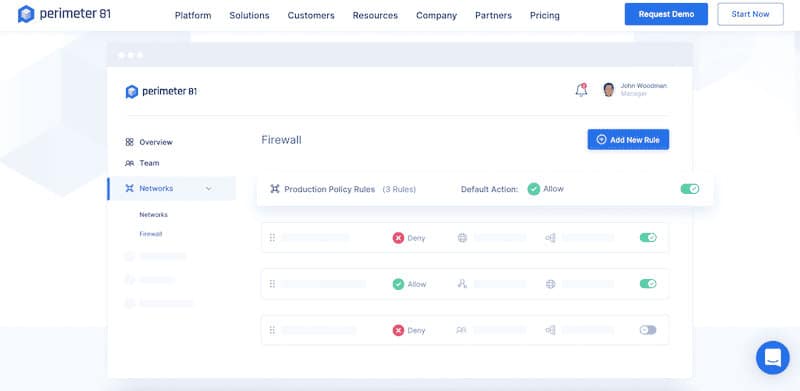
1. Perimeter 81 FWaaS – FREE DEMO
The cloud-based design of Perimeter 81 FWaaS is one of its primary differentiators, and the biggest draw for anyone wanting to invest in NGFW technology without having to consider hardware. This firewall solution eliminates the need for physical hardware appliances while providing the flexibility of scalable security by leveraging the power of the cloud. Businesses can easily extend their security perimeter to cloud settings, remote offices, and mobile devices with Perimeter 81 FWaaS, delivering consistent and robust protection throughout the whole network.
Another notable aspect of Perimeter 81 FWaaS is centralized management. The system includes a user-friendly web-based console that enables administrators to control and monitor network security from a single point of contact. This streamlined method makes it easier to manage security rules, rule sets, and user access controls across multiple locations and devices.
Perimeter 81 FWaaS features enhanced threat intelligence and defense technologies in addition to typical firewall capabilities. It detects and blocks known and new threats by utilizing machine learning techniques and real-time threat feeds. It can identify and mitigate potential security vulnerabilities by studying network traffic patterns and behavior, offering proactive defense against emerging threats.
The network segmentation capabilities of Perimeter 81 FWaaS are one of its distinguishing characteristics. Organizations can separate their network into isolated segments, each with its own security policies and access controls, using network segmentation. This ensures that even if one portion of the network is compromised, the rest of the network is safe. Perimeter 81 FWaaS streamlines the process of building and monitoring network segmentation, allowing enterprises to gain granular control over network traffic while mitigating the consequences of security breaches.
The emphasis on safe access controls is another significant distinction of Perimeter 81 FWaaS. With the proliferation of mobile devices and the rise of remote work, safeguarding access to corporate resources has become increasingly difficult. Perimeter 81 FWaaS tackles this issue by enabling secure remote access, letting employees connect to the business network from any location without jeopardizing security. To ensure that only authorized users have access to sensitive resources, it employs multi-factor authentication, encrypted tunnels, and granular access controls.
Perimeter 81 FWaaS also integrates well with other security products and services. Integration with threat intelligence platforms, SIEM systems, and identity and access management solutions is supported. This integration improves the organization's overall security posture by providing a comprehensive view of the network and enabling automatic response mechanisms to security issues. Register here for the free demo.
2. Fortinet FortiGate
Fortinet FortiGate is a market-leading NGFW with a plethora of strong features and functionalities that set it apart from other firewall systems. FortiGate delivers comprehensive protection for networks of all sizes thanks to its advanced security features and high-performance network functionalities.
Fortinet FortiGate's complete security suite is one of its most notable features. It includes a variety of security technologies such as a firewall, IPS, VPN, antivirus, online filtering, and application control. This multi-layered method ensures that firms have numerous layers of defense against diverse threats such as malware, ransomware, and network breaches.
Fortinet FortiGate offers superior performance, particularly in the high-end segment with its FortiGate 7000 series. These appliances are designed to meet the demands of large enterprises and service providers, providing exceptional throughput and scalability. The FortiGate 7000 series is equipped with purpose-built hardware and intelligent processing capabilities, allowing it to handle heavy traffic loads and deliver high-performance security without compromising network speed.
The solution’s sophisticated threat intelligence capabilities are another major differentiation. Fortinet's FortiGuard threat intelligence services, which provide real-time updates and protection against the most recent attacks, are integrated into the NGFW. This connection guarantees that enterprises have up-to-date threat intelligence and can defend against emerging threats, like zero-day attacks and complex malware campaigns, proactively.
The enhanced application control capabilities of FortiGate provide enterprises with granular control over network traffic. Administrators can design and enforce policies based on application categories, individual applications, and user groups. This level of management improves network security and assists enterprises in optimizing network performance by properly monitoring bandwidth utilization.
Fortinet FortiGate also has powerful VPN features, allowing for secure remote access to corporate resources. Organizations can provide encrypted connectivity for remote workers, branch offices, and business partners using built-in SSL and IPsec VPN technology. This secure remote access functionality protects critical data even when accessed from outside the corporate network.
Another important feature of Fortinet FortiGate is its scalability. FortiGate appliances, whether in the 7000 series or lower-end variants, can scale effortlessly to meet growing network demands. FortiGate's scalability makes it suited for companies of all sizes, from small businesses to huge enterprises with distributed networks.
Fortinet FortiGate's major strength is centralized management. The Fortinet Security Fabric provides a centralized management console through which administrators may configure, monitor, and control all FortiGate devices. This method of centralized management simplifies the effort of controlling many firewalls, lowers administrative overhead, and ensures that security settings are consistent across the network.
3. Palo Alto Networks PA Series

By providing granular application visibility and control, Palo Alto Networks PA Series goes beyond basic port and protocol inspection. Administrators can define particular policies to allow, prohibit, or limit access depending on application categories by detecting and categorizing apps on the network, decreasing the risk of unauthorized or harmful application usage.
In addition, the PA Series incorporates enhanced threat intelligence and prevention methods. Palo Alto Networks operates the WildFire cloud-based threat intelligence platform, which delivers real-time updates on emerging threats. The PA Series uses this data to detect and prevent known and undiscovered malware, including zero-day exploits. The PA Series can detect and neutralize threats in real-time by monitoring traffic patterns, behavior, and content, providing enterprises with excellent protection against the most recent attack vectors.
The PA Series' integrated endpoint protection is another notable feature. Palo Alto Networks provides Traps, a complete security suite that extends protection to endpoints like PCs, laptops, and mobile devices. This connection allows enterprises to implement consistent security policies and enforce endpoint protection mechanisms across the network, lowering the risk of breaches caused by weak endpoints.
Network segmentation is also supported by the Palo Alto Networks PA Series, allowing enterprises to build isolated network segments with their own security policies. This segmentation aids in the containment of potential breaches and the lateral flow of threats within the network. Organizations may ensure that even if one segment is compromised, the rest of the network remains secure by imposing independent security policies for each segment.
Furthermore, the PA Series offers centralized management via Palo Alto Networks' Panorama platform. Panorama enables administrators to operate numerous PA Series firewalls easily from a single interface. This approach to centralized management streamlines the deployment, implementation, and monitoring of firewall settings, guaranteeing consistent network security.
4. Check Point NGFW
Check Point NGFW combines firewall and IPS, antivirus, anti-bot, and sandboxing technologies. This multi-layered method protects against a wide range of threats, including malware, ransomware, zero-day attacks, and APTs.
Check Point NGFW makes use of Check Point ThreatCloud, an advanced threat intelligence platform. This cloud-based technology feeds real-time updates and threat intelligence to the firewall, allowing it to proactively identify and prevent incoming threats. Check Point NGFW can detect and block new and unknown attacks by using this intelligence, even before signatures or patches are available.
Granular application control capabilities are another notable feature. Administrators can use it to design and enforce policies based on application categories, individual applications, and user groups. This level of control enables enterprises to properly monitor and safeguard application usage, avoiding illegal or dangerous application access while ensuring business-critical apps are always available.
Check Point NGFW also supports comprehensive SSL/TLS inspection. It can decrypt and analyze SSL/TLS-encrypted traffic, allowing you to see what's going on behind the scenes. This functionality is critical as hackers employ encrypted communications to avoid detection. Check Point NGFW can discover and halt malicious actions disguised behind encrypted connections by analyzing SSL/TLS traffic, hence improving network security.
The solution also offers centralized management via its Security Management Portal. Administrators can use this web-based console to configure, monitor, and administer numerous firewalls from a single interface. This method of centralized administration simplifies policy management, saves administrative costs, and assures consistent network security.
Check Point NGFW also allows for seamless interaction with other security systems and services. It integrates with Check Point's Endpoint Security Suite, allowing businesses to extend their security protection to endpoints. Integration with Security Information and Event Management (SIEM) systems offers centralized security event monitoring and correlation, improving the overall security posture of the enterprise.
5. Cisco Firepower NGFW
Cisco Firepower NGFW distinguishes itself from other firewall options by delivering comprehensive network protection for businesses of all sizes. One of Cisco Firepower NGFW's primary differentiators is its integration with Cisco's Talos threat intelligence platform. Talos is a highly recognized threat intelligence agency that regularly monitors worldwide threats and delivers Firepower NGFW with real-time updates. This connectivity ensures that enterprises have access to the most recent security intelligence, allowing for proactive threat detection and response.
Cisco Firepower NGFW includes NGIPS features, which improve threat detection and prevention. It employs advanced heuristics, behavioral analysis, and machine learning algorithms to detect and eliminate known and undiscovered threats such as malware, ransomware, and APTs. Firepower NGFW can effectively defend against a wide range of complex assaults by combining signature-based and behavior-based detection algorithms.
The application-aware firewall functionality of Cisco Firepower NGFW is another noteworthy feature. It offers granular network traffic control based on application kinds, classifications, and user groups. With this level of application visibility and control, businesses may establish and enforce policies that meet their security and operational needs. It also aids in network performance optimization by monitoring bandwidth use and prioritizing vital applications.
Through its user-friendly administration panel, Cisco Firepower Administration Center (FMC), Cisco Firepower NGFW provides extensive network visibility. FMC acts as a centralized management platform for various Firepower NGFW devices, allowing administrators to configure, monitor, and analyze network security from a single interface. This method of centralized administration simplifies security policy management, simplifies device deployment, and improves overall network security.
Furthermore, Cisco Firepower NGFW enables decryption and inspection of SSL and TLS. It can discover and block dangers hidden within encrypted communications by decrypting and examining SSL/TLS-encrypted traffic. This capability enables enterprises to maintain a high level of security even while dealing with encrypted communications, which fraudsters are increasingly using to circumvent standard security controls.
6. SonicWall NSa Series
SonicWall NSa Series stands out among firewall systems due to its unique functions, providing enterprises with comprehensive network protection and threat avoidance. SonicWall NSa Series provides Deep Packet Inspection (DPI) technology, which allows the firewall to inspect and analyze network traffic at the application layer, providing granular control and visibility into application usage. SonicWall NSa Series provides enterprises with increased protection and control over network traffic by recognizing applications, users, and content, thereby preventing unauthorized access and virus distribution.
SonicWall NSa Series includes several security technologies that defend networks from a variety of threats. It combines standard firewall features with an IPS, antivirus, anti-malware, and web filtering. This multi-layered approach guarantees that companies are fully protected against both known and unknown dangers, such as APTs and zero-day assaults.
Another standout feature of SonicWall NSa Series is its secure remote access functionality. With the increasing trend of remote work, secure access to corporate resources is crucial. SonicWall NSa Series provides VPN capabilities, allowing remote workers to securely connect to the corporate network. By utilizing strong encryption and authentication protocols, SonicWall NSa Series ensures that remote access is protected and secure.
Through its SonicWall Network Security Manager (NSM) platform, the SonicWall NSa Series also provides centralized management. Administrators may configure, monitor, and control numerous SonicWall NSa firewalls using NSM's unified console. This method of centralized management simplifies policy administration, streamlines security operations, and gives a comprehensive picture of the network's security posture.
SonicWall NSa Series also offers enhanced threat intelligence and real-time updates via its SonicWall Capture Threat Network. This network receives and analyzes worldwide threat data, allowing SonicWall NSa firewalls to stay current on threats and provide proactive threat prevention. Organizations may effectively protect against emerging risks and zero-day assaults by employing threat information.