We may earn a commission if you make a purchase through the links on our website.
OSINT Tools & Software for Passive & Active Recon & Security!

UPDATED: January 2, 2024
“Spying has become just another business-travel tool, thanks to cheap, comprehensive technology, and to a soaring demand for dependable real-time information about day-to-day conditions in the world.” — Joe Sharkey, a New York Times columnist.
A few decades ago, the most significant intelligence agencies in the world with massive budgets couldn't do what you have in hand today, just with an Internet connection.
They had to use extreme spying methods, such as wiretapping, intercepting mail, and lots of social engineering, just to gather enough intel.
Here is our list of the 9 best OSINT tools:
- Recon-ng – EDITOR'S CHOICE This is a free tool from an open source project that enables the user to gather, collate, and correlate information for open source data sources. This system runs on Docker, so it is operating system independent and can be deployed on Windows, Linux, macOS, or Unix.
- Shodan A search engine that indexes everything on the internet other than websites, such as IoT devices, smart devices, vehicles, and routers. This is an online service and requires a subscription for access.
- Maltego This tool has many uses; it finds connections between data instances and creates a map. It will help you to find out who knows who by searching through social media profiles. Available in free and paid versions, this package installs on Windows, macOS, Linux.
- theHarvester This tool searches through a range of data sources on the internet to collect information on a given person, system, company, or event. Available for Linux.
- Recorded Future This is a cloud platform that gives access to threat intelligence sources and allows the user to extract possible hacker activity.
- Metagoofil This is a free passive reconnaissance tool that uses Google to locate files that have metadata related to a target, downloads them, and then indexes them for the relevant information. Runs on Linux.
- GHDB The Google Hacking Database is a free online searchable database of tricky Google search strings that can extract important information about a target system with a Google search.
- SpiderFoot A free tool that performs “fingerprinting” on a topic by linking together different discoveries about a given target. Runs on Windows and Linux.
- OSINT Framework A free online system that presents a collection of investigative tools that link together to discover and present information about a target.
We take it for granted, but today we have the kind of technology that intelligence agencies, two to three decades ago, would have only dreamt of.
Like hi-resolution satellite images of the entire world, the street-view showing how a place looks physically, access to “dark web” where criminals roam, people posting updates and pictures on social media, and a lot more.
This new type of open-source intelligence gave investigators an easier way to solve their cases, they started to refer to it as OSINT.
OSINT in Cyber-security
Wikipedia describes OSINT as “data collected from publicly available sources to be used in an intelligence context.”
OSINT is a practice that anyone with Internet access can do— if you are reading this, then you can also do it.
But that is the scary thing, even not-so-innocent black hat hackers, script kiddies, or hacktivists investigate and gather enough intel to perform attacks.
The amount of information that people can find available online is mind-boggling and if they know how to connect the dots, they can figure out lots of things.
A hacker usually starts an attack from a passive reconnaissance phase.
Their first step is to get to know the target systems (or users) by gathering enough information (without actively engaging with them).
They will want to see the type of public-facing assets; they’ll go to postings on social media to know about the insides of the organization, and some would even gather information from satellite and street-view images to know more about the premises.

OSINT tools can help you identify that open-source information of your organization that is publicly available on the Internet before hackers do.
Three Categories of OSINT Tools:
- Finding a Company’s Assets Information
- Discovering Sensitive Information Outside the Perimeter
- Aggregating Information
Finding a Company’s Assets Information
Today, most organizations have public internet-facing infrastructure information, from cloud-assets, hosting services, domain names, and more.
The OSINT tools can help you discover that internal/external asset information and give you a detailed report.
These tools passively explore the Internet to find information publicly available about the assets of the organization.
Keep in mind that finding information does not mean active reconnaissance— in other words, these tools do not directly interact with the systems.
Discovering Sensitive Information Outside the Perimeter
The company's employees might post sensitive information on social media.
For example, an IT manager could post something on his Twitter account like, “We finally finished our long day of Apache HTTP server updates, the new version 2.4 doesn't look so bad.
Time for those drinks!”. This post is gold for hackers.
OSINT tools can look for sensitive information outside the perimeters of your network, such as social media posts or domains that do not belong to your organization.
Aggregating Information
After gathering and discovering information on public sources, the OSINT tool can aggregate all data and provide actionable insights.
It is like the “Sherlock Holmes” of the recon tools.
These tools can't only gather information, but they can also put all the pieces of the puzzle together.
They can help you determine the who, what, when, where, and why.
Best OSINT Tools and Software
The available OSINT is vast. There are tons of sources that hackers can use to gather information.
What should you look for in open source intelligence systems?
We reviewed the market for OSINT systems and analyzed the options based on the following criteria:
- Automated utilities that can perform worldwide scans in minutes
- Adaptable tools that can filter out irrelevant results through search criteria
- Systems that ways to query IoT device data as well as computers
- Investigative tools that find relevant intelligence that is related to a core search subject
- Tools that hackers are known to use
- A free tool or a no-cost assessment period
- Valuable free tools or paid tools that offer value for money
With these selection criteria in mind, we have found a good range of tools that you can use in combination for effective intelligence gathering.
Before a hacker finds that sensitive information about your assets, employees, or facilities, an OSINT tool can lead you in the same direction (as a hacker would) so you can remove or deal with all that information from public sources.
1. Recon-ng
Recon-ng is a web reconnaissance and OSINT framework written in Python.
It can automate the process of information-gathering by thoroughly and quickly exploring the open-source information on the web.
Key Features:
- Open source OSINT framework
- Interactive, module-based CLI
- Similar interface to Metasploit
- Linux-compatible, Python 2.0
Why do we recommend it?
Recon-ng is recommended for its efficient, module-based approach to gathering open-source intelligence, offering a user-friendly interface similar to Metasploit, making it accessible for various users.
Once it finds valuable data, it will aggregate it and present it in an integrated and easy-to-read format.
The tool comes with an interactive command-line interface that is based on modules. The independent modules are recon, reporting, import, exploitation, and discovery.
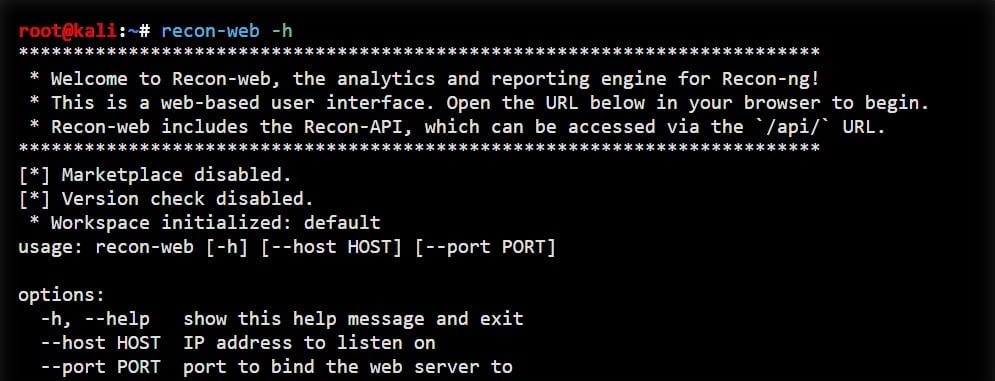
The interface looks a lot like the popular Metasploit Framework used for exploiting systems. The interface also comes with helpful features like command completion, database interaction, contextual help, API key management, and standardized outputs.
Recon-ng only works on Linux and requires Python 2.0 for its installation.
Who is it recommended for?
This tool is ideal for cybersecurity professionals and researchers who require a comprehensive, Linux-based OSINT solution that emphasizes an interactive, modular approach.
Pros:
- Open source, completely free
- Strong community, one of the most popular OSINT tools
- Great interface – looks and feels like Metaspoit
Cons:
- Highly detailed, takes time to fully explore and use all features within the tool
EDITOR'S CHOICE
Recon-ng is our top pick for an OSINT tool because not only does it help you mine open source information sources, it is an open source project as well. This package provides you with guidance through a framework for intelligence gathering. Services in the tool help you to consolidate data from different sources and identify links between data instances. As it is an open source tool, it is free to use.
Download: 100% FREE - Visit GitHub
Official Site: https://github.com/lanmaster53/recon-ng
OS: Docker over any operating system
2. Shodan
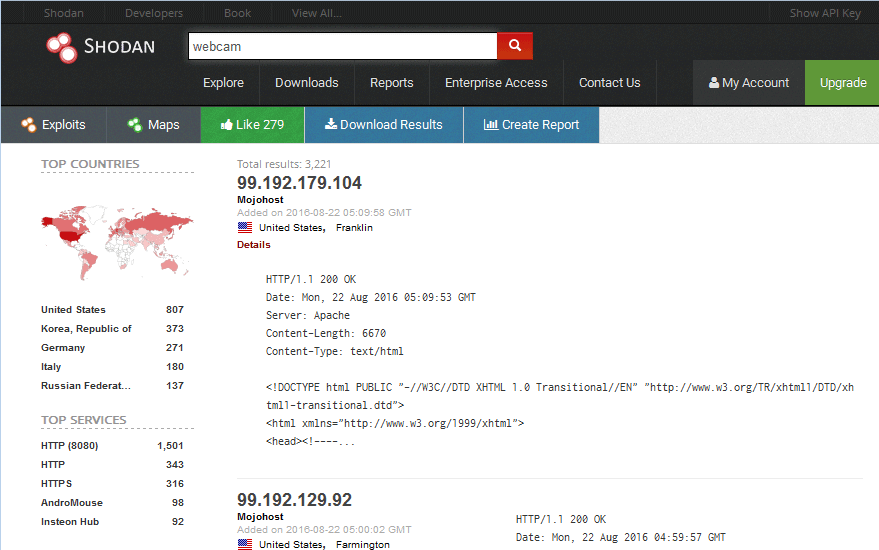
Shodan is the first search engine for interconnected or IoT devices. While Google indexes the web, Shodan indexes everything else on the Internet. It can find webcams, servers, routers, surveillance, traffic lights, smart TVs, fridges, vehicles, anything that is connected to the Internet.
Key Features:
- IoT device search engine
- Operational technology discovery
- User-friendly interface with maps
Why do we recommend it?
Shodan stands out for its unique ability to index IoT and operational technology, providing invaluable insights for cybersecurity efforts in industrial contexts.
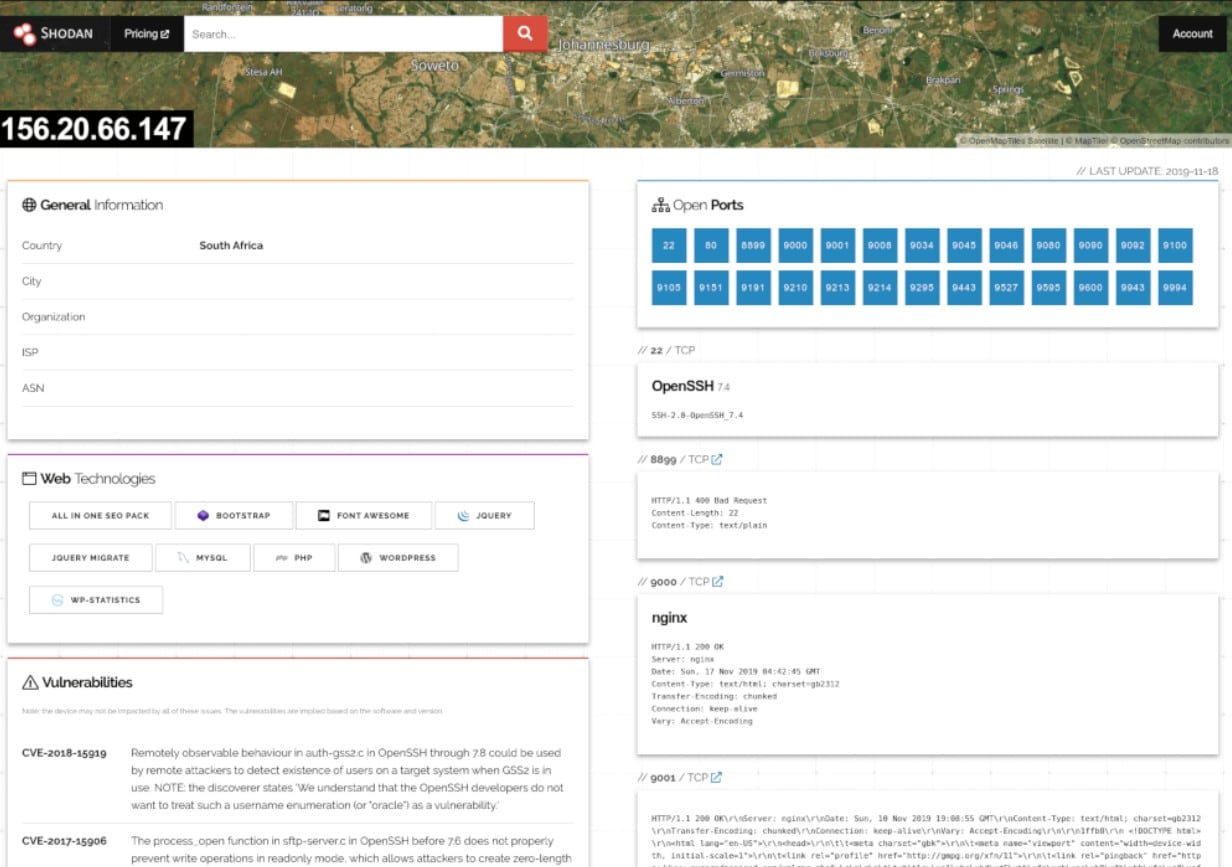
These IoT devices are often not searchable, but Shodan devised a way to find information on them and included their open ports and vulnerabilities. This search engine is one of the only ones that can discover operational technology found in industrial control systems. This makes Shodan, a critical tool for cybersecurity in the Industry. Aside from discovering IoT devices, Shodan can also be used to monitor databases to see if they have data leaks on public sites, and it can even find hidden video game servers within corporate networks.
Who is it recommended for?
Shodan is recommended for cybersecurity experts and industry professionals needing a specialized search engine for IoT and interconnected devices.
Pros:
- Very user friendly, even for non-technical users
- Great user interface, displays metrics alongside a geographical map
- Can export results and build reports from inside the tool
Cons:
- Shodan is a paid tool, starting at $59
- Shodan is offered as a service, much like Google you cannot tinker with its inner workings
Price: Shodan is offered in three different editions, Freelancer ($59 /month), Small Business ($299/month), Corporate ($899/month).
Download: No downloads. Just sign up for their service and choose a plan.
3. Maltego
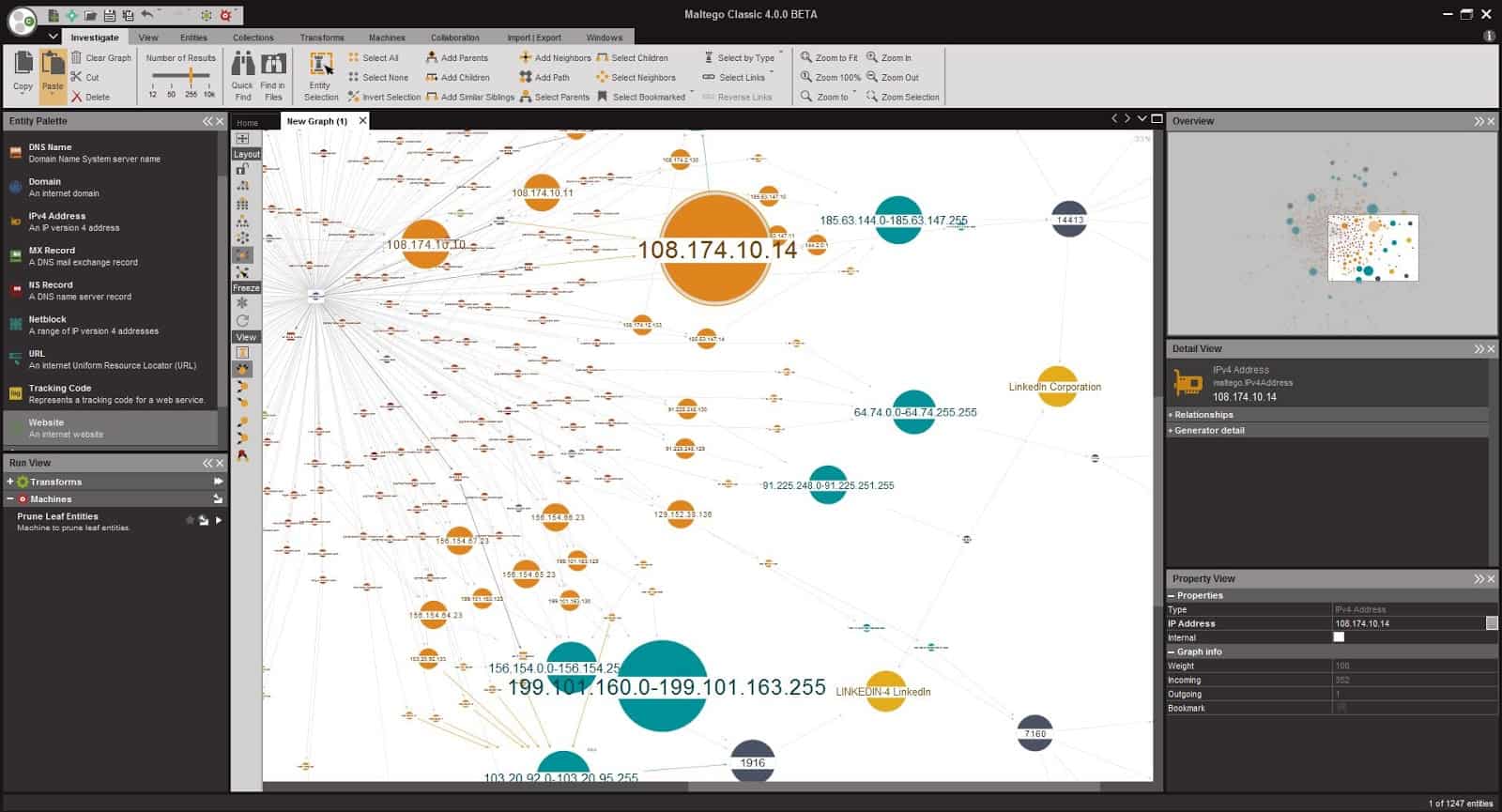
Maltego is an OSINT and computer forensics tool. It provides interactive data mining with rich visualizations that allow efficient analysis of links. The software is used for online investigations of the relationships between data from different sources on the internet.
Key Features:
- Data mining with visualizations
- Links analysis between data points
- Extensible via API
Why do we recommend it?
Maltego is recommended for its sophisticated data mining capabilities, particularly its graphical representation of complex networks and relationships.
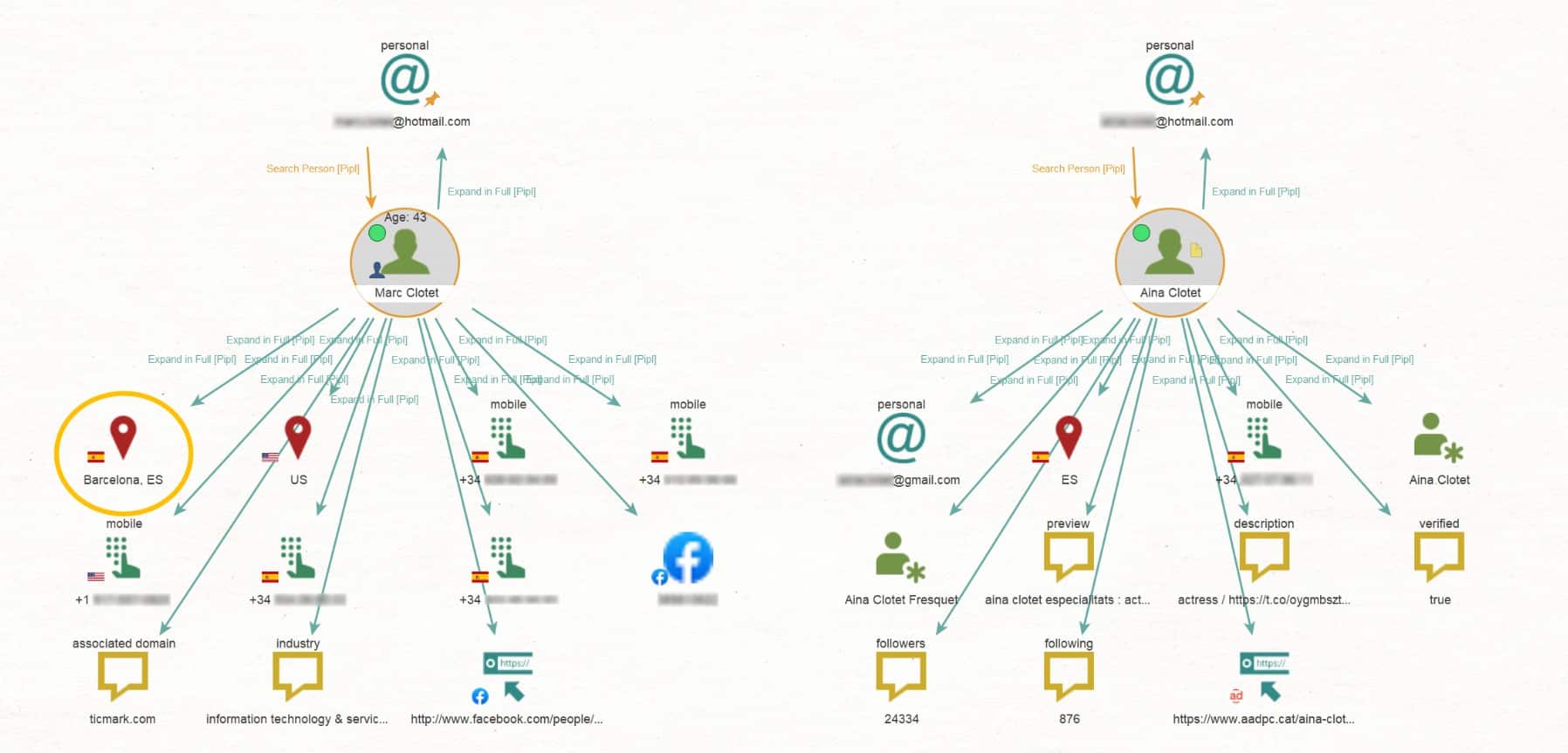
It can discover relationships between people and companies and find publicly accessible information. For example, Maltego can find links between emails, usernames, companies, websites, and more. It takes this information and renders a graph showing all connections and data points.
Maltego is based on a library of transforms that allow discovery from several public sources. By default, Maltego comes with a complete list of transforms, but you can extend it by running the API from other public information sources. The software runs in Java, and it can be installed on Windows, macOS, and Linux.
Who is it recommended for?
Ideal for cybersecurity analysts and digital forensics experts who require in-depth analysis of relationships and links across various internet data sources.
Pros:
- Highly visual, great for mapping complex networks and relationships
- The interface is very detailed but easy to learn
- Highlights relationships between datapoints natively – new sources can be added via API
Cons:
- The paid versions can be cost-prohibitive to smaller organizations
Price: Maltego comes in a variety of editions. Maltego CE is the free community edition.
Maltego Classic ($999 for the initial cost) and Maltego XL ($1999 for the initial price).
The software is also available for large-scale server installations, and the price starts from $40,000, including training.
Download: Get the free community edition Maltego CE by registering on their website.
4. theHarvester
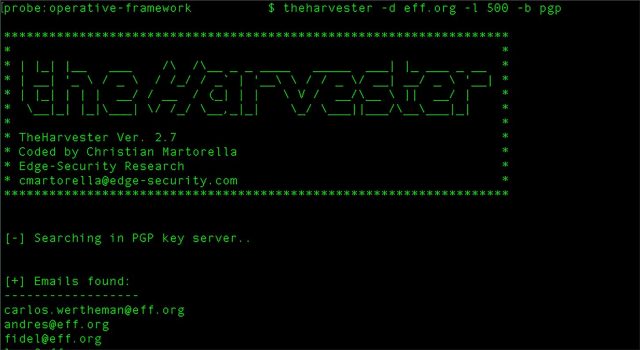
theHarvester is an OSINT passive reconnaissance simple tool written in Python. It was designed for information gathering from different public sources like search engines, the SHODAN database of internet-connected devices, or PGP key servers.
Key Features:
- Passive reconnaissance tool
- Python-based, open-source
- Subdomains, URLs, IP discovery
Why do we recommend it?
theHarvester is a versatile tool for gathering external organizational data, making it a top choice for passive reconnaissance.
The tool is terrific for finding information lying outside the perimeters of an organization, but it can also find public-facing assets inside the perimeters. It can discover information about subdomains, URLs, IPs, email accounts, employee names, and more.
theHarvester is relatively easy to use. Some of the most public sources like Google, Hunter, and Baidu, are included for passive reconnaissance. You can install some modules with an API key, such as bingapi, gitHub, and more.
Who is it recommended for?
Recommended for security professionals and pen-testers seeking a straightforward, effective tool for external information gathering.
Pros:
- Lightweight tool written in Python
- 100% free and open source
- Supported by a large community
Cons:
- No data visualization
Price: Open source and 100% free.
Download: From theHarvester for free from the GitHub repository.
5. Recorded Future
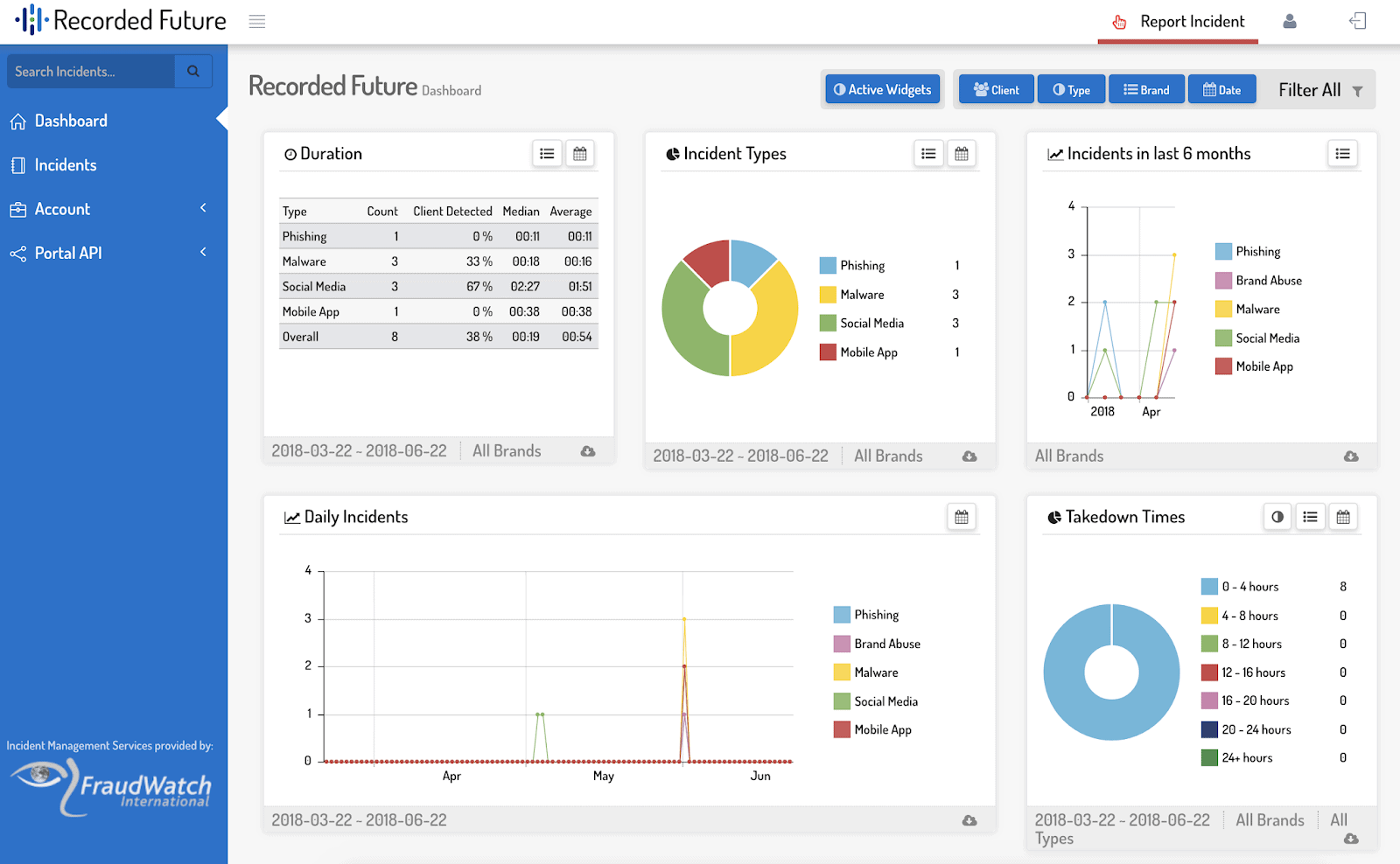
Recorded Future is an integrated threat intelligence solution. The software can gather and analyze large amounts of threat data in real-time. It converts all data into valuable insights with the help of ML (Machine Learning), AI (Artificial Intelligence), and NLP (Natural Language Processing).
Key Features:
- Threat intelligence with real-time alerts
- Uses ML, AI, and NLP
- Passive reconnaissance capabilities
Why do we recommend it?
Recorded Future is exemplary for its advanced, AI-driven approach to threat intelligence, offering real-time insights and alerts.
Among its many functionalities, Recorded Future can perform passive reconnaissance with the help of the Threat Intelligence Platform (TIP). Leveraging ML, AI, and NLP, Recorded Future can collect and aggregate data from publicly available sources, such as domain registrations, social media profiles, third-party websites, and more.
It works automatically and sends real-time alerts when it finds data leaks, such as credentials, typosquat domains, code leaks, bank identification numbers, brand-talk in the dark web, and more.
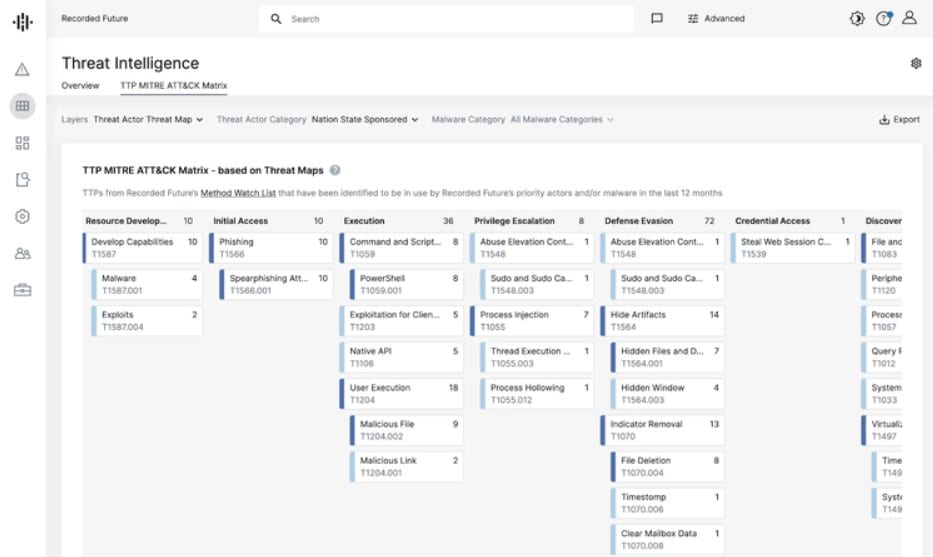
Who is it recommended for?
Suitable for organizations and security teams needing a comprehensive, AI-powered platform for threat intelligence and data analysis.
Pros:
- Simple yet intuitive user interface
- Modular widgets allow for easy dashboard customization
- Can analyze collected threat data or publicly available information online
Cons:
- Must contact for pricing
- Steeper learning curve due to their use of machine learning
Price: Recorded Future comes in three different editions, Express, Core, and Advanced. To learn more pricing, contact them.
Download: Request a demo.
6. Metagoofil
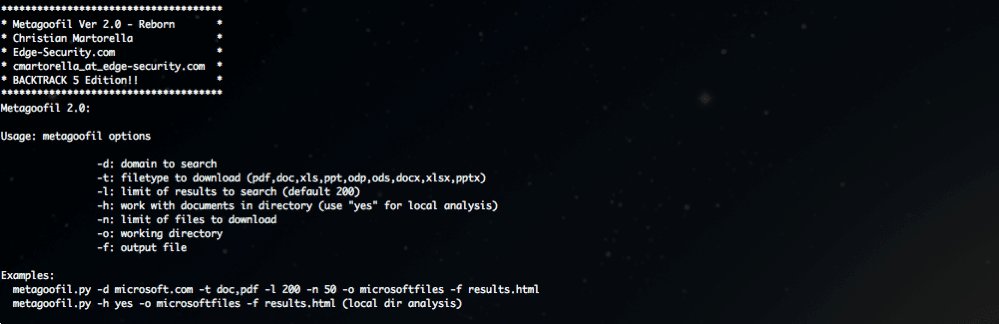
Metagoofil is a free passive recon metadata collector, written in Python. It is used for extracting information from documents like pdf, doc, Xls, ppt, ODP, and ods that are found on the target’s webpage or any other public site.
Key Features:
- Metadata extraction from documents
- Google-based document discovery
- Sensitive information identification
Why do we recommend it?
Metagoofil is adept at extracting and analyzing metadata from public documents, providing crucial insights into sensitive information exposure.
The tool uses Google to find the documents, then downloads them to the local disk, and extracts all metadata. Metagoofil analyzes the metadata of these documents and collects a good amount of information.
It can find sensitive information like usernames, real-names, software versions, emails, paths/servers. Hackers can use Metagoofil to gather username information and perform easier brute-force attacks. It can also show a hacker the file paths that can reveal OS, network names, shared resources, and more.
Who is it recommended for?
Recommended for security analysts and pen-testers focusing on uncovering sensitive data and potential vulnerabilities from public documents.
Pros:
- Exports reports in several file types, including PDF
- Can automatically find public text documents within a domain and download them
- Filters can be applied to scrape usernames, emails, and passwords
- Free and open source
Cons:
- Data visualization is very rudimentary
- Could use more documentation to help newer users
Price: Free and open-source.
Download:Metagoofil for free from the GitHub repository.
7. GHDB
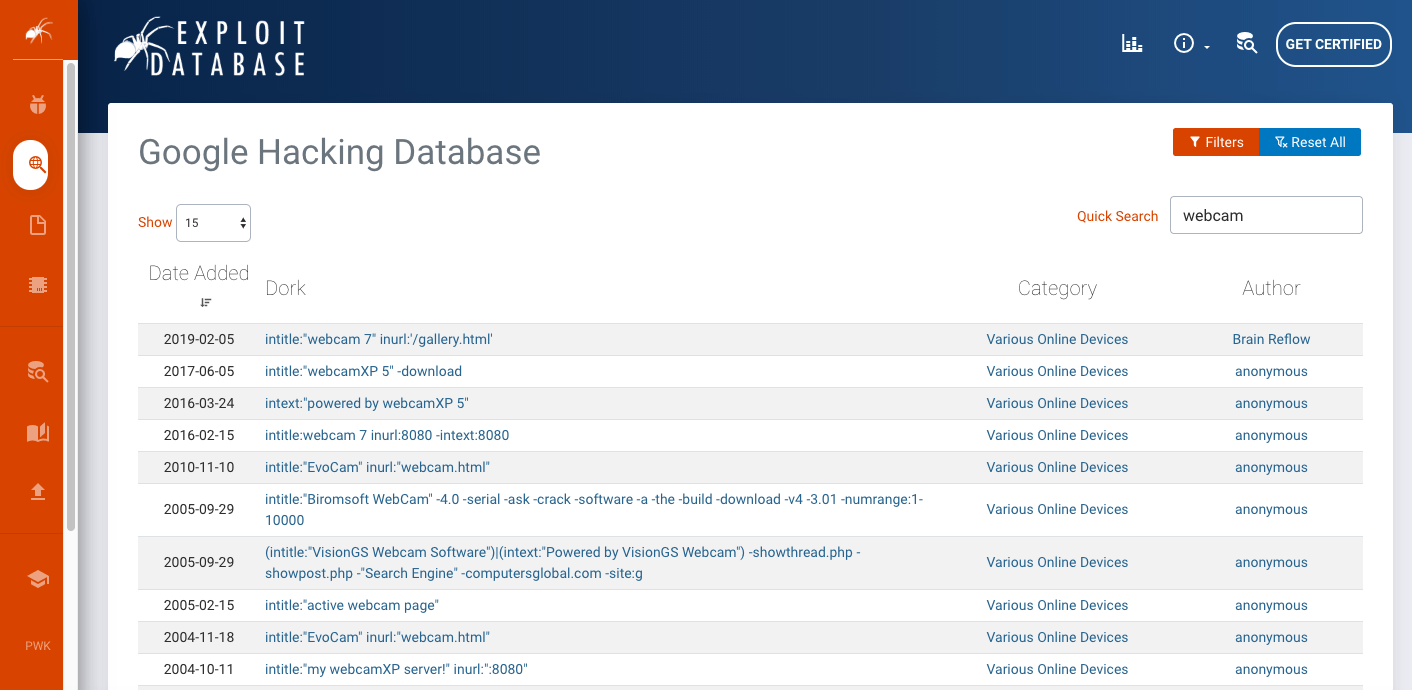
GHDB (Google Hacking Database) or often referred to as Google Dorks, is a database of search queries for Google that aims to find publicly available information.
The victims accidentally post sensitive information on the web, such as web consoles without security, open ports, login portals, sensitive directories, open webcams, files containing username information, and anything that is unintentionally exposed on the Internet.
Key Features:
- Google-based vulnerability search
- Community-driven query database
- Finds exposed sensitive information
Why do we recommend it?
GHDB is a unique, community-driven resource for finding exposed sensitive information and potential vulnerabilities through Google queries.
The community in Google Dorks posts a series of advanced Google search strings every day. An example of a Google dork query can be “intitle:index.of “users.db” that exposes files with users, or “intitle: “webcamXP 5″ -download” that shows all webcams with brand XP5 that are open for viewing.
GHDB is intended for pen-testers at the information-gathering phase or OSINT. If a pen-tester knows how to craft sophisticated queries in Google or can find the right one in GHDB he/she can find security holes in the configuration or coding of about anything.
Who is it recommended for?
This tool is best suited for pen-testers and cybersecurity researchers aiming to uncover and exploit vulnerabilities in publicly available information.
Pros:
- Powered by a large community of researchers
- Is continuously updated to reflect the latest vulnerability trends
- Uses simple search operators to identify vulnerable assets
Cons:
- Pages marked as “noindex” will not show up – offering an incomplete picture of the true scale of an attack surface
Price: Free
Download: It is a database of queries; there is nothing to download.
8. SpiderFoot
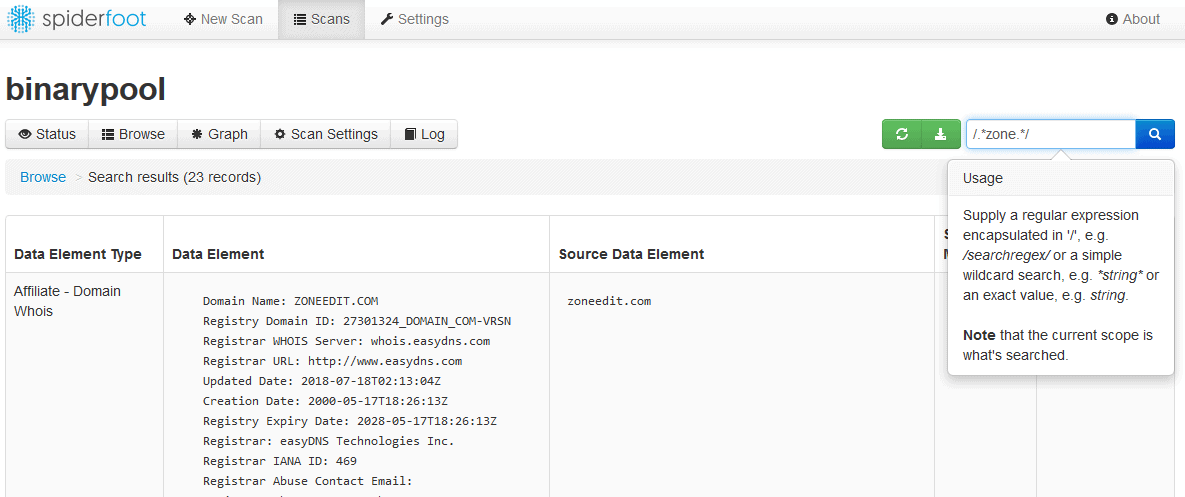
SpiderFoot is an open-source reconnaissance tool. It is often called the fingerprinting with the most extensive OSINT collection. The tool can automatically send queries to more than 100 public sources and collect intelligence on IP addresses, domain names, web servers, email addresses, and more. The software is written in Python.
Key Features:
- Extensive OSINT collection tool
- Queries over 100 public sources
- Windows and Linux compatible
Why do we recommend it?
SpiderFoot's extensive data collection capabilities from numerous public sources make it a standout choice for comprehensive reconnaissance.
To start with SpiderFoot, specify the target and choose among the hundreds of different fingerprinting modules. Examples of the SpiderFoot modules can be “sfp_arin.py” that queries ARIN registry for contact information or “sfp_crt.py” which gathers hostnames from historical certificates in crt.sh. Once you choose the modules, SpiderFoot will automatically collect information and build a report.
SpiderFoot is available for Windows and Linux.
Who is it recommended for?
Recommended for cybersecurity experts and researchers needing a robust tool for in-depth data collection and analysis from a wide range of sources.
Pros:
- Simple minimalistic interface
- Queries a bulk of public resources – great for extensive data collection
- New modules offers additional sources for data collection
- Completely free
Cons:
- No Mac Version
Price: Free and open-source
Download: Download from the Spider official site or from the Github Repository.
9. OSINT Framework
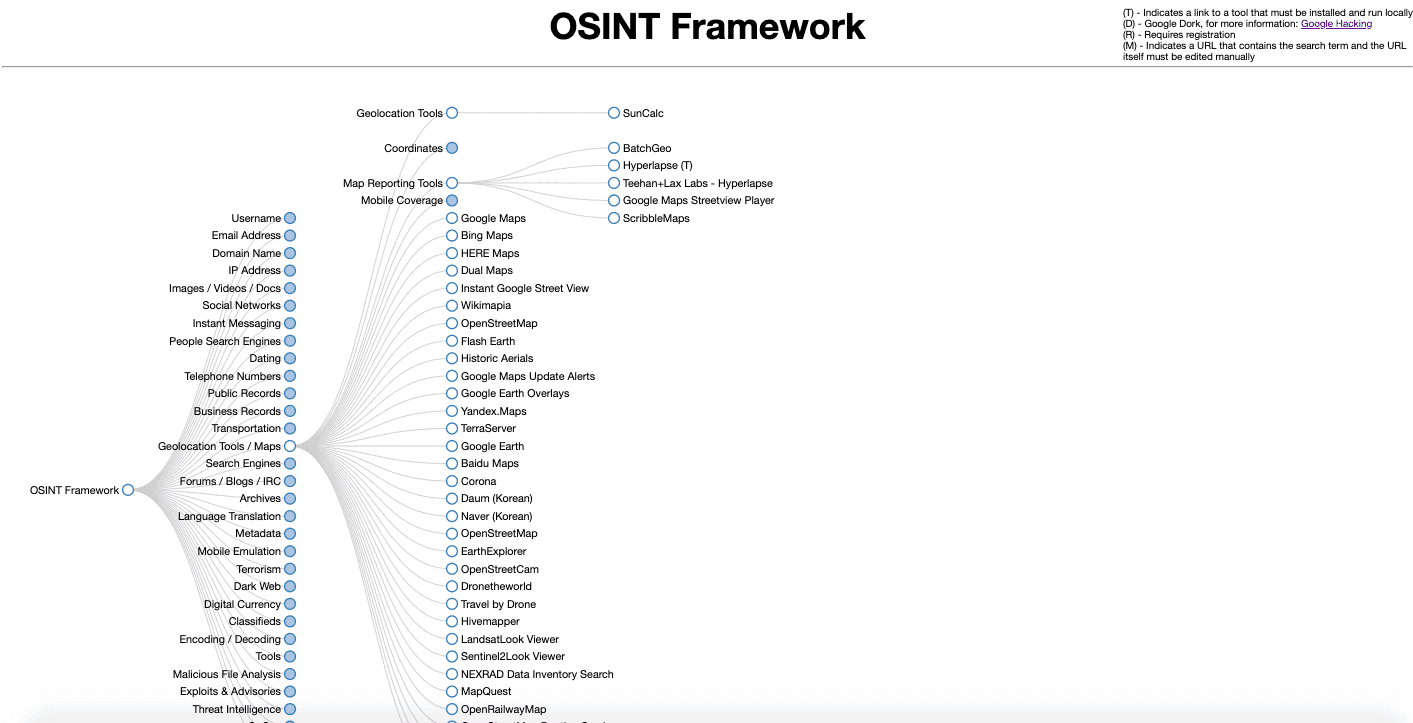
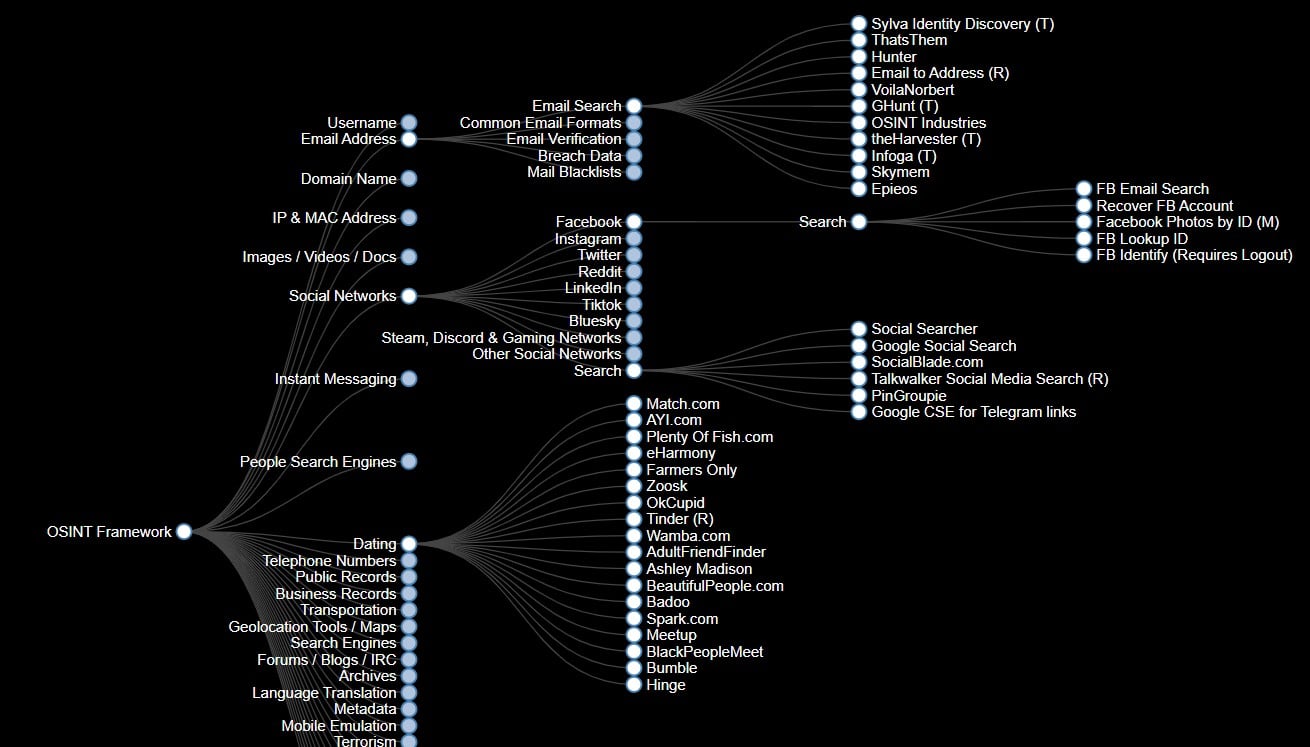
Last but not least is the OSINT Framework. If you haven’t found your perfect OSINT tool yet (or if it is not here on this list), the OSINT Framework will guide you in the right direction. The OSINT framework is not specifically software, but a collection of tools that make your OSINT tasks much easier.
Key Features:
- Centralized OSINT tools collection
- Category-based tool sorting
- Interactive mind map interface
Why do we recommend it?
The OSINT Framework is an invaluable resource for navigating the vast landscape of OSINT tools, offering a well-organized and comprehensive directory.
The OSINT Framework presents the information in a web-based interactive mind map that organizes the information visually. The framework is popular among pen-testers and cyber-security researchers that are looking for tools on specific areas of information-gathering and reconnaissance.
With this framework, you can browse through different OSINT tools which are filtered by categories. For example, some categories are the username, email address, geolocation/maps, dark web, search engines, transportation, public records, and a lot more.
Who is it recommended for?
Ideal for cybersecurity professionals, pen-testers, and researchers seeking a centralized repository of OSINT tools for various investigative needs.
Pros:
- The leading framework in the OSINT community
- Great place to find new tools for data collection
- Can sort tools by category
- Completely free
Cons:
- Can be overwhelming for new users who aren’t familiar with OSINT
Price: Free.
Download: It is a free web-based framework. There is nothing to download.
Final Words & Conclusion
OSINT does not only help you enforce the cyber-security standpoint of an organization but It can also help secure any area, from the company premises perimeter, improve anonymity on the web, remain safe from social engineering tricks, and even avoid terrorism.
If you know how to use Google Earth, its historical satellite imagery, and street views, you are already using open-source intelligence.
Knowing what information is available on public sources that can put you or your organization in risk is the key to block that critical passive recon phase and avoid an attack altogether.
Using OSINT tools and software shown here, take it a step forward, and automatically scan the publicly available information for you.
And even aggregate data and generate reports!!!
Happy Monitoring!