We may earn a commission if you make a purchase through the links on our website.
How To Protect Your USB Firmware From Viruses

UPDATED: October 30, 2023
An infected USB firmware can be a real threat. It can quickly install another version of the self-replicating virus and start sending malicious instructions to the computer. It could (not only infect the computer) but also open backdoors, install keyloggers and ransomware, steal data, and much more. To protect your USB firmware from viruses, you must take some precautions.
In this post, we’ll go through the various ways to protect your USB firmware from viruses. We’ll show you six different ways, including avoiding plugging and using unknown USBs, physical protection, using an updated antivirus, disabling autorun, using security-centric USB devices, and using device control software.
Why is it essential to protect USB firmware from viruses?
USB devices are usually built for a particular purpose; anything from storage, and wireless communications, to cold wallets that store cryptocurrency. USB devices have internally-stored firmware— a piece of software that controls the hardware at a low level and makes the device perform its specific task.
The bad news is that USB firmware is also the target of viruses, just like a standard OS would be. And even more bad news, an infected USB firmware is one of the easiest ways of propagating a virus.
An infected USB firmware transforms the regular USB into a self-replicating virus device. Hackers corrupt the USB firmware inside the device and convert it into a device designed to spread the virus; then, they trick the victim into plugging the device. Hackers usually leave an infected USB device lying around, hoping the victim falls into the trap. If the victim plugs the USB device (and autorun is on)… Voilà! Hackers could gain access to the network, steal data, spy on activities, or even destroy records.
This is precisely believed to be the method of how the infamous Stuxnet worm made its way into the Iranian nuclear facilities. First, it bypassed a major air gap, infected a computer inside the network, and slowly self-propagated across the network using USBs and other methods.
How to protect your system from malicious USB firmware
Learning how to protect your USB firmware from viruses is essential to improving your cybersecurity standpoint. You’ll improve not only the security of USB drives but also computers and entire networks.
Note: Keep in mind that infected USB firmware is not the only source of a self-replicated virus— a computer might be already infected by a virus that attaches and propagates via USBs. For instance, when you insert a clean USB drive into an infected computer, the USB drive infects you. So, to protect your systems and networks, you should also protect your USBs externally and your computers (that receive USBs) internally.
Now, let's go through six different ways to protect your USB firmware from viruses and your computers and networks from those self-replicating viruses.
1. Avoid lost and found USB devices
It is worth mentioning many times how unsafe it is to attach random, lost, or unprotected USB devices to a computer.
In 2016, researchers left about 300 unmarked USB flash drives around the campus at the University of Illinois. They observed that the people picked up about 98% of the drives and plugged almost half of them into a host device. But that was just an experiment; this happens in real life. Hackers use social engineering techniques to target specific networks.
As a network admin, inform and train users about the potential risks of using randomly lost & found USB devices. There is device control software (last section) that can help admins block USB ports and monitor their activity.
2. Use physical security measures
You can use physical security measures to help protect your USB firmware and computer from viruses. As a best practice, always avoid using your USB flash drive on an “untrusted” or “public” computer. But of course, there will be a time when you will need to use your USB device on another computer.
Many USB devices come with a write-protection hardware switch on the side. This switch changes the permissions of your USB device (and all files inside) into read-only (no execute and no write), which helps protect the device from data theft and virus infection. If you need to view the content of a USB device on another “untrusted” computer, always ensure that the USB’s Read-Only switch is enabled. If your USB device has this switch, move it into the lock position to keep it safe.
3. Use antivirus software
One way to protect your computer and network from USB-borne viruses is to use updated antivirus software with USB scanning capabilities. An antivirus program can be configured to automatically scan, detect and quarantine any malicious code that may be present on a USB device.
As a best practice for preventing unintended malware (such as self-replicating viruses), always scan your computer with updated antivirus software. Ensure your antivirus is reliable, up-to-date, and can scan autorun programs automatically. In addition, it is also a good practice to continuously check a USB drive before opening it or running any hosted program.
4. Disable Autorun
Windows Autorun is a utility that lets any removable media (such as USB) run automatically on your computer. Many USB firmware-based viruses exploit this valuable yet risky utility and run malicious programs on your system. One of the infamous examples of this type of malware is Conficker. This virus exploited the autorun utility of removable media and sent instructions to the computer to disable automatic backup settings, restore options, and open remote backdoor connections.
A best practice is then disabling Windows Autorun. Below are two known methods to disable Windows Autorun.
a. On an individual computer
Follow these steps to disable Autoplay (autorun) on a Windows computer.
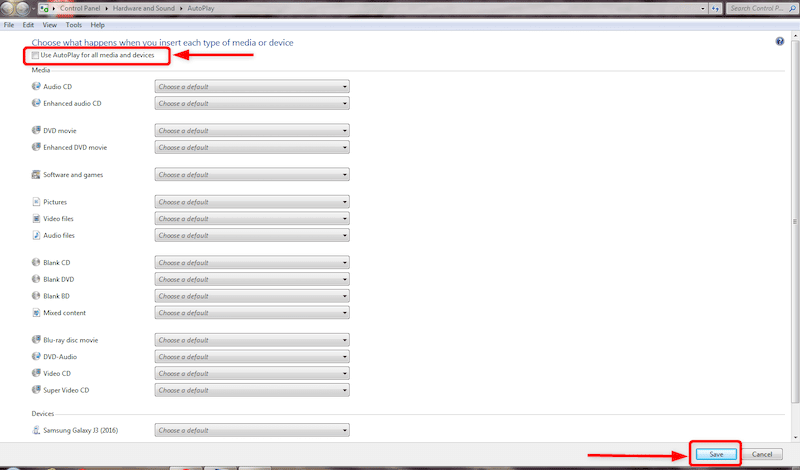
- Click on the Windows icon to open the Start menu. Then, type “Autoplay” in the search bar. Find and click on “Change default settings for media or devices”.
- In the “Autoplay Settings window,” Un-check (disable) the “Use AutoPlay for all media and devices” option.
- Click on Save to apply changes.
b. Via group policy objects (domain level)
As a network admin, you might want to disable autorun capabilities on all networked devices. If your Windows computers are within an Active Directory environment, you can use Group Policy Objects (GPO) to configure users’ and computer settings that belong to an AD domain.
- Open the Group Policy Management tool on the Windows Server running as Domain Controller (DC),
- On Group Policy Management > Forest (NAME) > Domains > Domain Controllers > Group Policy Objects. Right-click and choose “New”.
- Give it a name. Go back to Group Policy Objects, right-click on your new GPO and click on “Edit”.
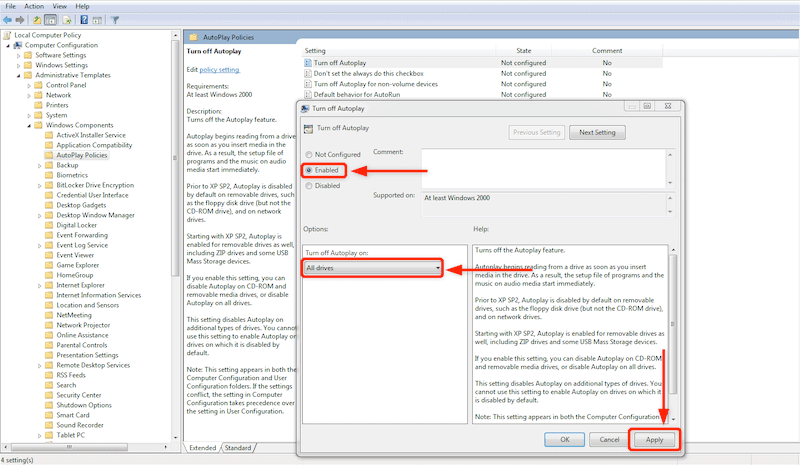
- On the Group Policy Editor window, open the “Computer Configuration” > “Administrative Templates” > “Windows Components” > “Autoplay Policies”.
- Double-click on “Turn off Autoplay” to open it. Click on “Enabled” and ensure “All drives” is selected from the “Turn off Autoplay on” dropdown. Click on Apply and Ok.
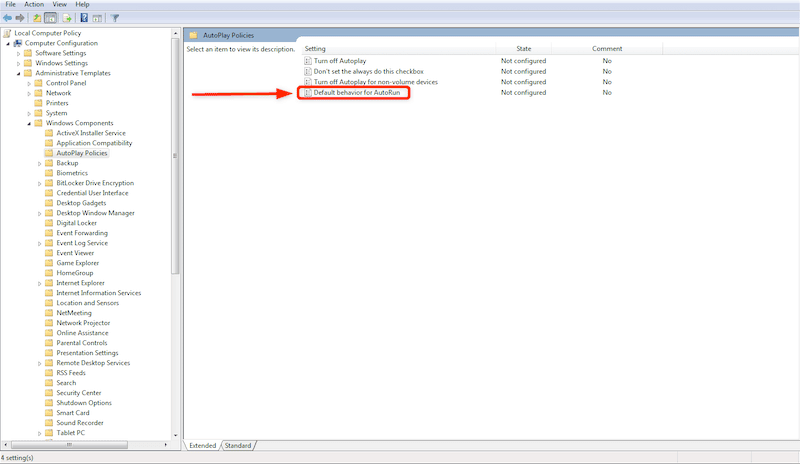
- Do the same for “Default behavior for AutoRun”. Open its editing tab and ensure the “Do not execute any autorun commands”.
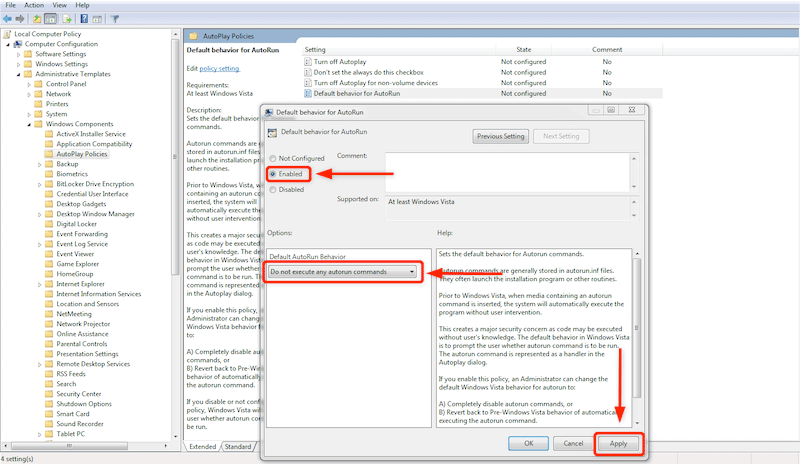
- Select “Do not execute any autorun commands” from the “Default AutoRun Behavior” options and ensure the policy is enabled. Click on Apply > Ok.
5. Use Security-Centric USB devices
There are some USB devices that you can find on the market which are explicitly designed with security in mind. Below, you'll find a list with a few of these security-centered USB devices.
a. Hardware-Encrypted devices
Hardware-based encrypted USB flash drives are highly efficient solutions to USB firmware-related security concerns. Some USB devices come with hardware-based encryption designed to protect highly sensitive data from government or corporate. No one can access or tamper with these USB devices; they work only on selected computers (the ones that hold the decryption key).
b. Write Protection
As already mentioned before, USB flash drives with the write protection switch can help avoid file transfer between a computer and a USB. The small switch (lock) on the side of the USB prohibits data transfer; it only allows users to view data. This helps protect the USB by preventing viruses or malware from writing into the firmware.
c. Keypad Flash Drives
Another hardware-based USB security method is the keypad flash drives. These flash drives come with a tiny keypad so that only the owner with the passcode can access the content. Thus, no one can inflict malicious malware on your USB device unless someone knows your passcode. Many keypad flash drives also come with encryption to double down on the security.
d. USB Firewalls
A USB firewall is a portable device that connects between a computer and the USB device, keeping any malicious USB firmware away from the computer (or vice versa). One end is plugged into the computer, and the other receives the USB device. These devices inspect all incoming and outgoing traffic to and from USB devices. It allows only the safety instructions to pass and blocks any suspicious or compromised file (or instructions) from penetrating the computer.
6. Device Control Software
Device Control Software is one of the most reliable methods to protect USB firmware from viruses in large networks. These types of software monitor and flags suspicious data transfers between networked endpoints and USB devices. Device Control Software lets admins control all the internal and external devices connected to a network.
The following are four of the best examples of Device Control Software. These solutions come with free trials and demos to help you get started, understand how they work, and test the products for a limited time.
- ManageEngine Device Control Plus – FREE TRIAL The best security solution for the industrial or technical sector. It provides full-fledged control over all external devices, such as USB flash drives. The solution also minimizes data theft by flagging unauthorized data transfers. Moreover, you can set up a list of trusted devices that can access your computer. Download a fully-featured 30-day free trial.
- Crowdstrike Falcon Device Control An award-winning endpoint security solution. It is a cloud-based security platform that monitors your data, identifies threats, and prevents attacks. It is perfect for small to large enterprises, scaling up to 1000 endpoints. Falcon Device Control is designed to protect USB devices. It provides granular control and insights on using USB devices and many more. Try Falcon Prevent (AV) for free for a limited time.
- CoSoSys Endpoint Protector A well-known Data Loss Prevention (DLP) software with a fantastic Device Control solution. It provides endpoint control, prevents data theft, and stops data leaks. Endpoint Protector can also help you protect your USB firmware from viruses by locking down USB ports, providing granular control, and automatically encrypting devices (and their data). Try a 30-day free trial.
- Ivanti Device Control A cloud-based security platform that allows admins to encrypt endpoints by enforcing security policies on removable media such as USBs and data. It is an outstanding solution for controlling USB devices, as it comes with USB lockdown capabilities so admins can “remotely” lockdown and regain control of devices.
Final Words
Despite their incredible benefits, USB devices pose a great risk to single computers and even entire networks. These devices are so portable and easy to plug in that they are frequently used by hacks and attacks. They are the target of some serious and nasty viruses out there.
As a network admin, you must take the proper cybersecurity measures to protect your network from USB-borne viruses. In this post, we discussed six ways to safeguard USB firmware from viruses. Avoid (and train users) unknown USB devices, physically protect computers and USBs, use antivirus, disable autorun, use the right security-centric USBs, and finally, use USB device control software.