We may earn a commission if you make a purchase through the links on our website.
How to Query FSMO Roles in AD Quickly

UPDATED: August 30, 2024
Active Directory is a database and set of services that store information about users and their respective computers. Also, it helps create a connection between users and various Windows domain networks. To authenticate all users and computers connected with the Windows domain network, there are Domain Controllers, a server running Active Directory. There are multiple Domain Controllers (DC) and directory services in an Active Directory Environment. Each directory has a Domain Controller. Thus, any change made to the directory can be processed by any domain controller (DC) regardless it is linked or not to the network.
Active Directory allows changes to the domain controller, but it can also create conflicts or problems if data replication occurs to the rest of the enterprise. One way is to discard all the changes made to other DCs, which is acceptable only in some cases. The other method is to follow the single-master model, under which only one DC from the entire directory will process and perform updates to specific objects. AD, however, extended this old model by adding multiple roles and responsibilities to the Domain Controllers in the enterprise. A single DC makes domain changes, and the rest will follow the same. Also, if a DC fails, the other DC will take its place and perform updates.
As the roles in the Active Directory do not restrict to a single DC, it's referred to as Flexible Single Master Operation or FSMO roles. Mainly, there are five FSMO roles, including:
- Schema Master
- Domain Naming Master
- Infrastructure Master
- PDC or Primary Domain Controller Emulator
- RID or Relative ID Master
The ones restricted to enterprise-level are Domain Naming Masters and Schema Masters (one per forest). The other three FSMO roles – Infrastructure Master, Primary Domain Controller Emulator (PDC), Relative ID Master (RID) are restricted to domain level (one per domain).
Let's discuss in detail more about these separate roles and how they collectively complete an AD system.
The Five FSMO Roles of Active Directory
1. Schema Master
The Schema Master is the enterprise-level FSMO role that has the authority of modifying forest schema and raising the functional level of the domain controllers operating system. This FSMO role comprises a writable schema partition and stores AD classes and attributes. Make sure to create a backup before making changes to the schema. Once changes are made in the schema master, data replication from the server to the rest domain controllers begins.
2. Domain Naming Master
The Domain Naming Master is the other enterprise-level FSMO role in an Active Directory Forest. Only the domain naming expert can add or delete existing domains and application partitions. Without it, you cannot access or create a new domain. The Domain Naming Master also ensures similar domain names must not be made in the same forest. Keep in mind if the DC owner does not return online, the roles can be seized.
3. Infrastructure Master
In an Active Directory Forest, the Infrastructure Master comes under the domain-level role. This role manages phantom objects created in the cross-reference objects and verifies the clients’ authorizations. The objective of Phantom objects is to track deleted objects' local domain references and as things attribute in other domains. Every single part is assigned only one Infrastructure Master role that updates Distinguished Names (DNs), Security Identifiers (SIDs), and Globally Unique Identifiers (GUIDs) between domains controller roles. Only the Domain controller must manage this role. Remember, no user will be notified if you lose the original domain controller.
4. Primary Domain Controller Emulator
The Primary Domain Controller is a domain-level role that reverts to authentication requests, manages Group Policy Objects, and changes passwords in an AD forest. This role is essential for the following tasks, such as:
- Backward Compatibility The role owners’ job is to address back-compatibility issues in the directories by registering as a target domain controller for legacy applications. They have similar properties (writable operations) like the single master role.
- Distributed File System The default Distributed File System occasionally requires updated DFS namespace data from the primary domain controller, resulting in resource overcrowding.
- Password Update Processing The primary domain controller emulator receives a duplicate copy of the updated retreat as a non-primary domain controller resets PC and passwords. He also processes account lockouts.
- Time Synchronization Each PDCE synchronizes its clock with the domain forest root, whereas the non-PDCE synchronize its clock with the domain’s PDCE.
- Group Policy Updates The domain PDCE receives all updates on the essential policies, such as simultaneous modifications done by two domain controllers to avoid conflicts.
5. Relative ID Master
Another domain-level role whose purpose is to assign Security Identifiers (SID) blocks to domain controllers in each domain. It interacts with an active Relative ID Pool that contains unique RIDs used to create a new object's Security Identifier (SID). To avoid conflicts related to similar SIDs for multiple objects, the role owner assigns unique SIDs and provides access to add or remove objects from the domain. If the Relative ID pool of the domain controller fails, you can demand an extra Relative ID with the Domain's Relative ID Master.
How to Query FSMO roles in AD Quickly
There are two ways to query FSMO roles in Active Directory
1. Using Netdom Query FSMO Command-line Tool
The Netdom is a Windows command-line tool used to manage Active Directory domains, trust and check the FSMO roles.
To check the FSMO roles in AD, follow the below steps:
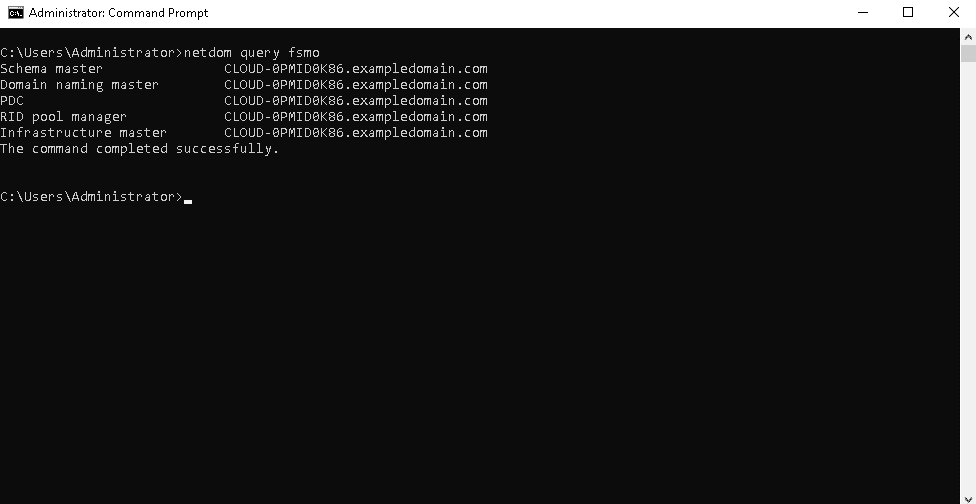
Step 1 Open a Windows command prompt and run the following command:
netdom query fsmo
This will return with five FSMO roles with Domain Controller.
Schema master CLOUD-0PMID0K86.exampledomain.com Domain naming master CLOUD-0PMID0K86.exampledomain.com PDC CLOUD-0PMID0K86.exampledomain.com RID pool manager CLOUD-0PMID0K86.exampledomain.com Infrastructure master CLOUD-0PMID0K86.exampledomain.com The command was completed successfully.
2. Using Powershell
You can also check the FSMO roles in Windows Active Directory via PowerShell.
Follow the below steps to check the FSMO roles:
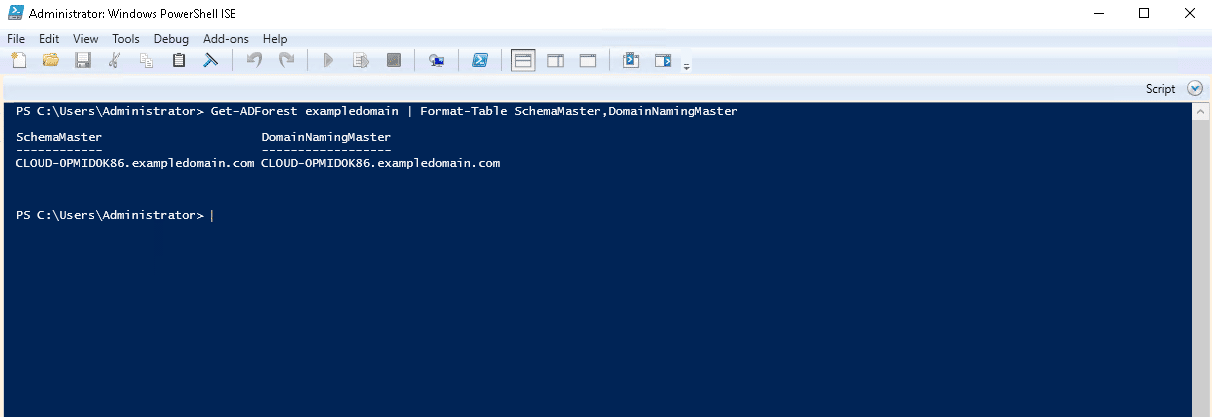
Step 1 Open the Windows PowerShell and run the following command to check the forest FSMO roles:
Get-ADForest exampledomain | Format-Table SchemaMaster, DomainNamingMaster
You should see the forest roles in the following output:
SchemaMaster DomainNamingMaster ------------ ------------------ CLOUD-0PMID0K86.exampledomain.com CLOUD-0PMID0K86.exampledomain.com
Step 2 To check the domain FSMO roles, run the following command:
Get-ADDomain exampledomain | format-table
You should see the following output:
AllowedDNSSuffixes ChildDomains ComputersContainer DeletedObjectsContainer DistinguishedName DNSRoot Domai
nCont
rolle
rsCon
taine
r
------------------ ------------ ------------------ ----------------------- ----------------- ------- -----
{} {} CN=Computers,DC=exampledomain,DC=com CN=Deleted Objects,DC=exampledomain,DC=com DC=exampledomain,DC=com exampledomain.com OU...
Use a Third-Party Tool
ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine produces a tool for exploiting the data in Active Directory and that system, called ADAudit Plus, includes a tool to query FSMO role changes.
Steps to Query FSMO Roles in AD with ManageEngine ADAudit Plus:
Log in to ADAudit Plus:
- Open your web browser and log in to the ManageEngine ADAudit Plus console with your credentials.
Navigate to the Reports Section:
- Once logged in, navigate to the left-hand pane of the dashboard where you’ll find various categories for AD audit reports.
- Click on “Reports” to access the different types of reports available within ADAudit Plus.
Access FSMO Role Change Reports:
- Within the Reports section, locate the “Configuration Changes” category.
- Under this category, click on “FSMO Role Changes”. This report will provide you with detailed information about any changes made to the FSMO roles in your Active Directory.
View FSMO Role Information:
- The FSMO Role Changes report will display information such as the role holder name, the old and new role owners, change time, and the user who made the change.
- You can use filters to narrow down the results based on time range, domain, or specific roles.
Generate and Export Reports:
- You can generate reports on FSMO role changes over a specified period. ADAudit Plus also allows you to export these reports in various formats (PDF, CSV, etc.) for further analysis or compliance reporting.
- Click on the “Export” button to save the report in your desired format.
Schedule FSMO Role Change Reports:
- To stay updated on FSMO role changes, you can schedule these reports to be generated and sent to your email automatically. Go to the “Schedule Reports” section, set up your schedule, and select the FSMO Role Changes report.
Set Up Alerts (Optional):
- If you want to receive real-time alerts whenever an FSMO role change occurs, navigate to the “Alerts” section and configure an alert for FSMO role changes. This feature ensures that any critical changes are promptly communicated to the relevant stakeholders.
Benefits of Using ADAudit Plus for FSMO Role Monitoring:
- Real-Time monitoring: Real-time tracking of FSMO role changes, ensuring that any unauthorized or unexpected changes are detected immediately.
- Comprehensive reporting: Detailed reports give you a clear view of who made changes to FSMO roles, when, and from where, helping in audits and ensuring compliance.
- Automated alerts: Setting up alerts for FSMO role changes helps in proactive management and quick response to critical changes in your AD environment.
By following these steps, you can effectively query and monitor FSMO roles in Active Directory using ManageEngine ADAudit Plus, ensuring better oversight and control of your AD infrastructure. You can get started by registering for a 30-day free trial.
Conclusion
Microsoft Active Directory's primary purpose is to connect users with Windows domain networks to help further create objects, install and update software, enforce security policies, store users' credentials, and more. However, authority to make changes to the domain controller can create conflicts. Thus, various roles were assigned, later referred to as Flexible Single Master Operation or FSMO roles as they do not limit to a single DC. The Schema Master, Domain Naming Master, Infrastructure Master, Primary Domain Controller Emulator, Relative ID Master are the prominent five roles in an Active Directory Forest classified into enterprise and domain-level roles.
If, due to any technical or other issues, the FSMO roles crash, you have the power to seize these roles to other domain controllers, fix and bring them back online. Use Management Console or PowerShell to transfer the FSMO role actively.
How to Query FSMO Roles in AD Quickly FAQs
What are FSMO (Flexible Single Master Operations) roles in Active Directory?
FSMO roles are a set of special operations master roles in Active Directory that are responsible for specific tasks, such as creating and deleting objects, updating the schema, and handling naming conflicts. There are five FSMO roles in Active Directory:
- Schema Master: Responsible for updating the schema of the directory.
- Domain Naming Master: Responsible for adding and removing domains from the forest.
- PDC Emulator: Responsible for handling password changes and authentication requests.
- RID Master: Responsible for allocating RIDs (Relative Identifiers) to domain controllers.
- Infrastructure Master: Responsible for updating object information between domains.
How do I query the FSMO roles in Active Directory?
You can query the FSMO roles in Active Directory using the following methods:
- Using the Active Directory Administrative Center: Open the Active Directory Administrative Center, right-click on the domain and select "Operations Masters." This will show you the FSMO roles for the domain.
- Using the command line: Open a Command Prompt window and type "netdom query fsmo" to see the FSMO roles for the forest.
Why is it important to know the FSMO role holders in Active Directory?
It is important to know the FSMO role holders in Active Directory because these roles are critical for the proper functioning of the directory. Knowing the FSMO role holders helps you to understand the structure of the directory and to identify potential bottlenecks or points of failure in the directory.
What are the consequences of losing a FSMO role in Active Directory?
Losing an FSMO role in Active Directory can cause various problems, depending on which role is lost. For example, losing the RID Master role can cause domain controllers to run out of RIDs, causing new objects not to be created. Losing the Infrastructure Master role can cause incorrect information to be displayed in the directory.
How do I transfer a FSMO role in Active Directory?
To transfer an FSMO role in Active Directory, follow these steps:
- Open the Active Directory Users and Computers console.
- Right-click on the domain and select "Operations Masters."
- Select the role you want to transfer and click "Change."
- Select the target domain controller and click "OK."
- Confirm the transfer and restart the target domain controller.
- How do I seize a FSMO role in Active Directory?
- To seize a FSMO role in Active Directory, follow these steps:
- Open a Command Prompt window.
- Type "ntdsutil" to open the NTDS Utility.
- Type "roles" to enter the FSMO maintenance mode.
- Type "connections" to enter the server connection mode.
- Type "connect to server <server_name>" to connect to the target server.
- Type "quit" to return to the FSMO maintenance mode.
- Type "seize <role_name>" to seize the FSMO role.
Note: Seizing a FSMO role should only be done as a last resort, as it can cause serious problems in the directory.