We may earn a commission if you make a purchase through the links on our website.
Security Testing: Techniques & Tools
UPDATED: October 24, 2022
There are many threats to businesses and the failure of IT assets is one of them. Left unprotected, your IT system is vulnerable to attack. This is particularly the case if you have an internet-facing or web-based infrastructure.
The first problem that you will face is not knowing what parts of your systems need to be protected. After tooling up with security systems to protect those vital components, you need to check that those cybersecurity measures are effective. So, there are many phases to security assessment. This isn’t a task that you can perform once and then forget about.
Recursive checks and continuous monitoring are the solutions to keeping your system guard up. This strategy can only be implemented by automated services. Let’s take a look at security strategies.
Here is our list of the five best security testing tools:
- ManageEngine Vulnerability Manager Plus – EDITOR'S CHOICE A system security bundle for on-premises resources that includes a vulnerability scanner and a patch manager. It runs on Windows and Windows Server. Start a 30-day free trial.
- Invicti Web Security Scanner This security testing system can be used by application developers and also by application users. It is particularly strong at testing web applications and it helps towards compliance with HIPAA and PCI DSS. It is available as a cloud service or for installation on Windows Server.
- Acunetix Web Vulnerability Scanner Software testing tools that are particularly useful for testing vulnerabilities in web applications. It is available for Windows, macOS, and Linux.
- Netwrix Auditor A great tool that supports security audits and also implements system security management functions, such as configuration management. It runs on Windows and Windows Server.
- LogicGate A cloud-based risk assessment and security auditing tool that can be tailored to the requirements of specific data security standards.
Application security strategies
Your security strategy will vary according to the degree of exposure your IT system has to the internet. A business that has in-house systems with no internet connection is very rare to find these days, even among small retailers that operate almost exclusively in the world of bricks and mortar. At the other extreme are businesses that operate a virtual office system with all services provided by SaaS systems from the cloud.
Enterprises that rely on remote systems for their back-office and conduct all of their business on the Web are extremely vulnerable to attack. Not only does that constant connection to the internet provide an always-open channel for hackers to get in but a system failure would end the viability of the operation.
We are going to focus on those connection-dependent businesses in this guide. The less connected your business is, the less dependent it is on cybersecurity. However, there will always be a need for some level of system protection for every business that uses a computer – which is all businesses.
The problem that connected businesses face is that they cannot completely withdraw from internet availability. They need to remain open while blocking certain activities.
In any business, the ultimate target for hackers is the endpoints – servers and desktop. This is where the valuable data is held and this is where hackers can sneak on malware. There are two types of threats that a business faces – from outsiders and from insiders.
System security strategies
Endpoint security testing can be conducted manually or automatically. There are two types of endpoint security testing strategies methodologies but there are procedural and reporting constraints to consider before you launch into testing,
- Risk assessment: Classifies all system components as Low, Medium, and High Risk. The risk assessment leads to the identification of key components that are a high priority for testing.
- Security auditing: An internal inspection of operating systems and software for security flaws. As with the risk assessment, the security audit should be performed in the context of prevailing security standards.
- Posture assessment: This is a form of a security audit that addresses manual procedures, conventions, workflows, and management responsibilities for data security.
- Penetration testing: Attempts by “white hat hackers” to break into a system and access sensitive data.
- Vulnerability scanning: Automated system probes from an outsider viewpoint, looking for incidences of known typical security weaknesses.
Read a little deeper into each of these topics below.
Risk assessment
Risk assessment directs security testing efforts towards the most important areas of the system. For example, sensitive data. On the topic of sensitive data, the definition of which types of information should be prioritized for protection is heavily influenced by the necessity to comply with specific data security standards, such as HIPAA and PCI DSS.
The issue of different data priorities shows that there is no “once size fits all” path for security testing. A risk assessment, conducted by a specialist consultancy with accreditation to the particular standards to which the business is subject, would provide a tailored direction in which security testing should progress.
Security auditing
Audits are requirements for security standards compliance. These will eventually be performed by external auditors. However, a business beginning the creation of a security testing process will need to create an internal audit, that should identify areas that need to be addressed in order to get the system up to standard compliance.
Posture assessment
The security “posture” of a business refers to its organizational security both in terms of working practices, management responsibilities, and system settings. Each aspect of the IT infrastructure will be the responsibility of a different specialist – for example, network administrator and database administrator. Each of the managers should be tasked with the responsibility of implementing system security tests for that specific set of resources. This will cover issues such as user account management, access rights management, device settings, and preventative maintenance schedules.
Penetration testing
Penetration testing is usually conducted by highly experienced cybersecurity technicians working for security consultancies. It is usual for a business to hire a penetration testing service to give a one-time assessment of a system. Penetration testing – also known as “pen testing” – results in a report of security weaknesses and recommendations for how those problems can be resolved.
The types of protection that companies usually implement in order to close down vulnerabilities include altering the settings of network devices, increasing control over user accounts, and installing recommended security software.
Vulnerability scanning
Vulnerability scanners, also known as vulnerability managers, perform periodic automated checks on a network. These services are launched from outside of the network from a remote location. They mimic the strategies implemented by hackers to try to break into a system. Some vulnerability management tools also include agent software that needs to be installed on an endpoint within the network. This checks for weaknesses that could be exploited by insiders.
After an initial sweep, a vulnerability scanning service will sweep a client’s system once a month. The weaknesses that the system searches for are compiled as a list by the vulnerability scanning service. When new exploits are discovered, that attack strategy is added to the list of problems that the next sweep should look for.
Web Application Security Testing
Web applications are vulnerable because they need to be accessible by any member of the public in order to fulfill their purposes. Hackers are part of the public. Web site owners want to enable easy access to Web servers without letting the bad visitors wreak havoc.
With websites and web services, the issue of vulnerabilities is different from the security measures needed for onsite resources.
With physical infrastructure, the main focus of security lies in access. With web-based systems, the issue that needs to be addressed is the ability to manipulate services to gain access to underlying resources, such as data.
Security testing methodologies
When approaching system security, devise your methodology for services to test onsite resources and separate procedures to check on website security. For onsite security, you should follow a methodology.
The methodology that suits your business will depend on the degree of connectivity your business model requires and the demands of any specific data security standards that you are expected to comply with.
Issues such as methodology will rise from the risk assessment, which should be the first phase in your security testing strategy.
Our methodology for selecting security testing tools:
We reviewed the market for security testing systems and analyzed tools based on the following criteria:
- Features for scanning, crawling, and exploiting vulnerabilities
- Examine various security testing techniques available, including penetration testing, vulnerability scanning, code review, security architecture review, and threat modeling
- Full coverage in terms of usage, scalability, and compatibility with your current systems and work
- Align with industry regulations and standards.
- Conduct trials or proofs of concept with selected tools.
- Upfront licensing fees, ongoing maintenance expenses, training costs, and any additional resources necessary
The best security testing tools
Given that there are many different business models, there are also many different testing strategies and required tools for the job. Penetration testing and vulnerability scanning are good tools for the job whether you are particularly concerned with protecting your physical resources or the services they support or website security. If you are primarily vulnerable through a website, there are further layers of security that you can deploy and these are closely bound with testing and monitoring.
You can read more about each of these systems in the following sections.
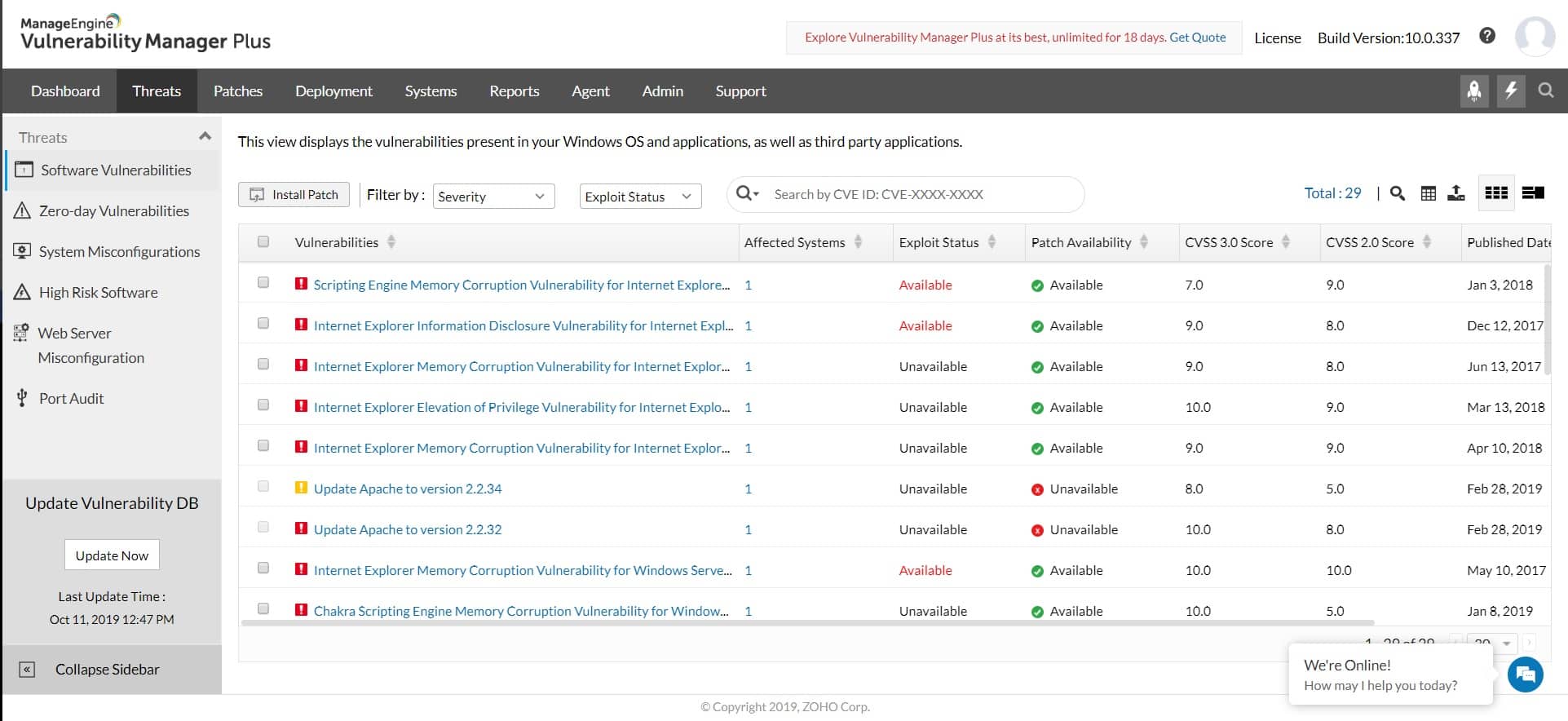
1. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus is a useful bundle of a vulnerability scanner and a patch manager. This neatly provides the tools to fix many of the security issues that get identified by the tests on system weaknesses. Out-of-date software is one of the top causes of vulnerabilities.
Key Features:
- Built-In Patching: Due to its built-in patching feature, it can easily detect vulnerabilities.
- Vulnerability Detection: Capability to instantly detect the vulnerability when it occurs.
- Vulnerability Scanning: Scans for all OS vulnerabilities and third-party vulnerabilities and ensure zero-day vulnerabilities.
- Remediation: Helps in deploying correlated patches to catch vulnerabilities and use alternative mitigation measures accordingly.
Why do we recommend it?
ManageEngine Vulnerability Manager Plus stands out with its advanced patching capabilities. Its built-in patching functionality ties patches directly with their associated vulnerabilities for instantaneous remediation across affected machines, while customizable deployment policies give you full control over when and how often patching should start and end. Furthermore, affected target systems are listed automatically for easy customization while you can retry failed target deployments and receive deployment status notifications on a regular basis – providing comprehensive vulnerability management.
If you are not reliant on web activity for your business, Vulnerability Manager Plus is probably going to be your best option on this list because it offers security auditing for physical and virtual resources based on site. Its scans focus on endpoints and network devices.
The vulnerability scanner launches every 90 minutes, checking all devices running Windows, Linux, and macOS. The scanner is able to discover all equipment over the network, so you don’t need to type in all of your device inventory in order to get it to work. Although this service is particularly strong at checking on-premises equipment and software, it is also able to check on internet communication security and the operations of websites.
Who is it recommended for?
ManageEngine Vulnerability Manager Plus is designed for cybersecurity specialists and IT professionals charged with protecting company networks. Using this tool quickly identifies vulnerabilities before prioritizing fixing them – saving both time and resources by automating tasks that decrease cyberattack risks quickly while freeing experts up to focus on other essential measures of defense against attacks – this tool ensures company networks remain safe.
Pros:
- Asset Discovery: Responsible for detecting and managing devices and endpoints across the network.
- Vulnerability Assessment: Conducts a vulnerability assessment, such as its impacts, and will prioritize according to age, severity, patch availability, exploit code, and other factors.
- Blind Spot Elimination: Includes automatically discovering the active endpoints, directories, and domains.
- Vulnerability Summary: Ranks the vulnerability based on the severity to get better visibility and solve the critical issues on first priority.
Cons:
- Slower Agent Scan: Some users recently reported that agent scan is comparatively slow when the computer is restarted. This eventually affected productivity and delayed vulnerability solving.
The software for Vulnerability Manager Plus runs on installs on a Windows Server host. The package is available in three editions: Free, Professional, and Enterprise. The Free plan will only monitor up to 25 endpoints. The Professional edition has no limits on the number of devices it can scan and the Enterprise edition is intended for use on WANs. You can get Vulnerability Manager Plus on a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Vulnerability Manager Plus is our go-to choice when it comes to top security testing tools due to its intelligent and comprehensive approach to vulnerability assessment. Constantly detecting vulnerabilities in real time helps prioritize areas requiring immediate attention, while its built-in patching capabilities provide instant remediation of identified vulnerabilities. Furthermore, its seamless integration with Active Directory domains and workgroup endpoints enables effortless scalability as new assets are added onto networks – making this one solution timesaving and efficient in managing cybersecurity risks.
Download: Download 30-Day Free Trial
Official Site: https://www.manageengine.com/vulnerability-management/
OS: Windows Server
2. Invicti Web Security Scanner
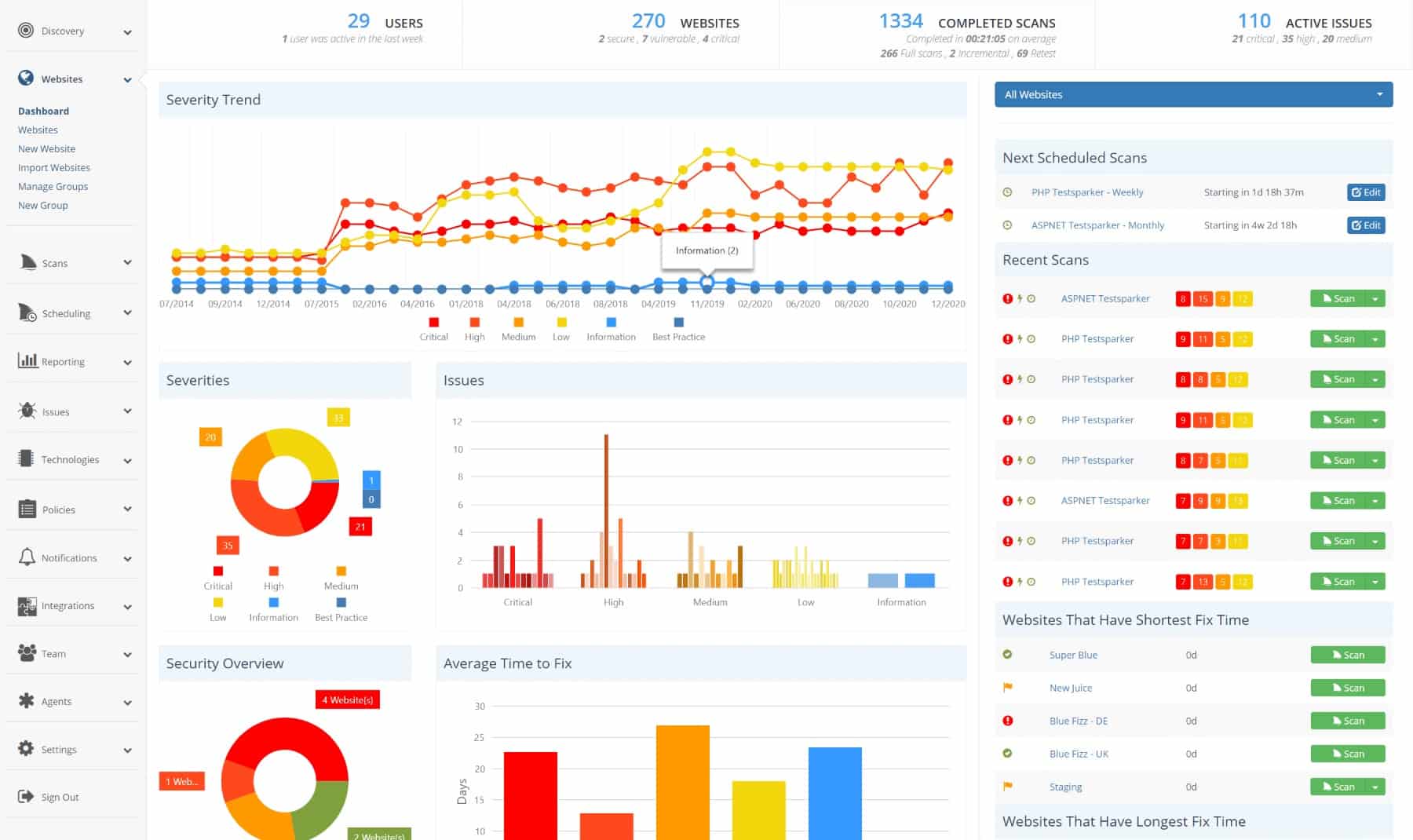
Invicti is an application security testing service that is, essentially, a vulnerability scanner for vulnerability websites. Web applications are becoming increasingly more complicated to track because they rely on Application Programming Interfaces (APIs). APIs give access to functions that are hosted elsewhere and it isn’t even possible to know exactly where those services are actually hosted or whether they, in turn, rely on other services hosted on other servers. So, there is a growing need for the services of Invicti so users of these services can be sure that they are secure.
Key Features:
- Automation Through SDLC: Helps automate security tasks and find the vulnerabilities that actually matter.
- Comprehensive App Visibility: Follows a dynamic and interactive approach and scans every corner of your app to keep risk at bay.
- Behavior-Based Testing: Uses signature and behavior-based testing to check the vulnerabilities with proven accuracy and false positives.
- Effective Risk Management: Allows you to combine security testing with your SDLC and manage permissions for unlimited users.
Why do we recommend it?
For various reasons, we highly recommend Invicti Web Security Scanner. Firstly, its artificial intelligence predicts risk levels in applications, making prioritizing fixes much simpler. Furthermore, its advanced search features can find all your web assets–even those you might have forgotten or created without permission–including ones other tools might miss; its scanning approach covers areas that other tools might miss, as well as seamless integration with issue tracking software so that you always know the status of security fixes; overall this tool provides powerful protection for web applications.
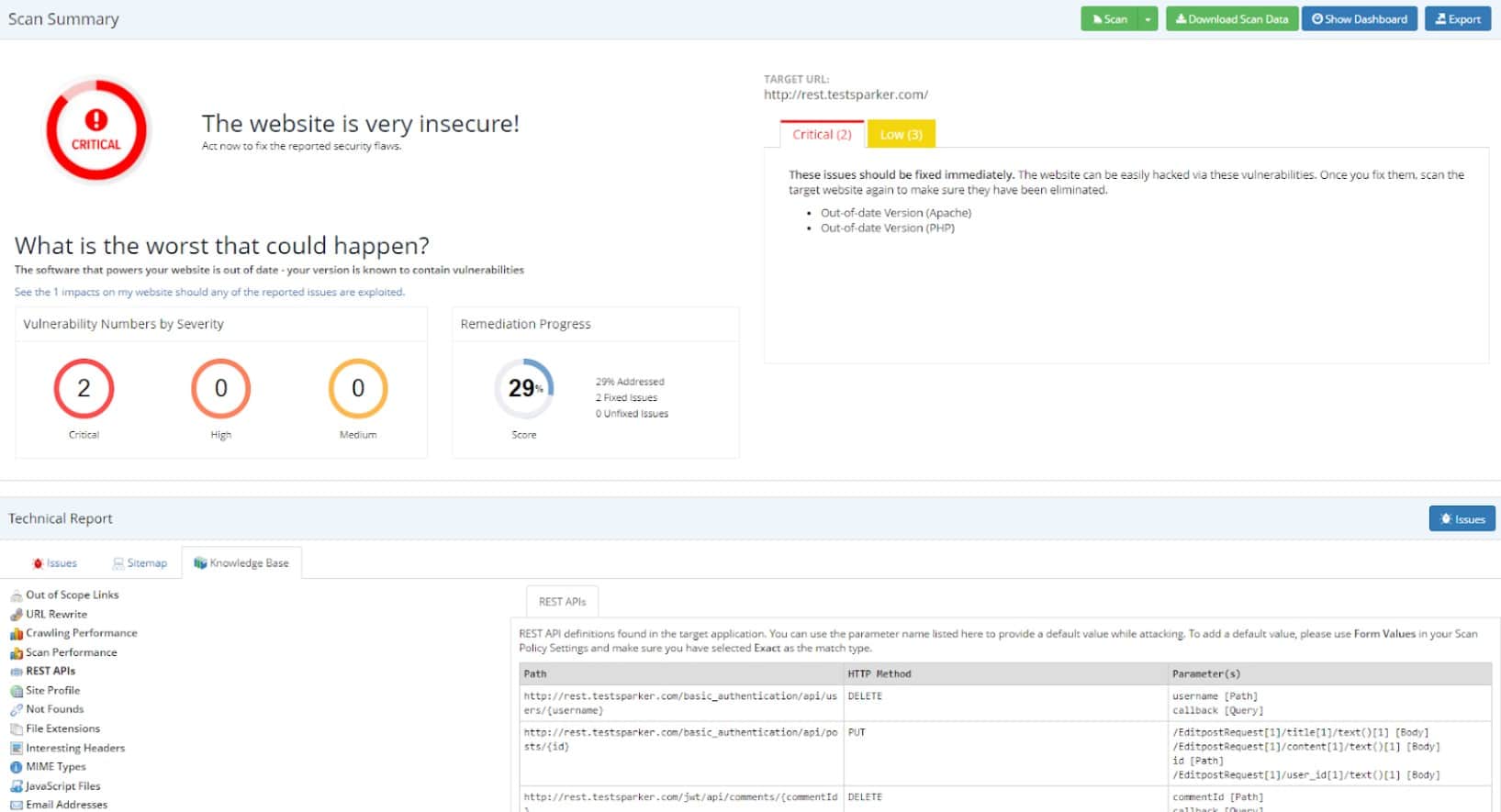
Invicti is offered in three editions, which are appropriate for different types of users. Companies that run websites developed by others don’t need all of the functions of the top edition, which is called Enterprise. This includes testing and verification tools that are needed for development and testing as well as the vulnerability scanning used for live websites. The Team version has similar capabilities but less capacity.
Both the Team and Enterprise editions are cloud services, though it is possible to get an on-premises version of Enterprise to install on Windows Server. The base package of Invicti is called Standard and that is only available for installation on Windows Server. This package doesn’t include the developer and acceptance testing penetration testing tools. It is largely a vulnerability scanner.
Who is it recommended for?
Invicti Web Security Scanner is ideal for anyone who needs to secure their websites or web applications from cyber threats, including website owners, developers, and IT professionals who are responsible for maintaining the security of web assets. From small business websites to enterprise ecommerce platforms and everything in between, Invicti can identify security vulnerabilities before hackers exploit them, providing valuable peace of mind and ensuring the safety and integrity of online presence.
Pros:
- Allows Secure Coding: Gives developers access to security feedback and code accordingly to prevent vulnerabilities.
- 50 Plus Integrations: Provides over more than 50 integrations so that it can be easily connected with your current system.
- High-Risk Vulnerability Detection: Supports DSAT, IAST, and API testing to find high-risk vulnerabilities.
- Use Open-Source Components: Security is uncompromised with open-source components and advanced manual scanning tools.
Cons:
- Longer Scanning Time: Users feel that it is expensive and takes longer scanning time when it's about scanning particular technologies or large websites.
Invicti is our top pick for a security testing tool because it is available for development teams as well as for testing in live environments. The Invicti system is able to enforce the requirements of data security standards, including HIPAA and PCI DSS. Invicti is ideal for those that want to perform security checks on websites and web services.
3. Acunetix Web Vulnerability Scanner
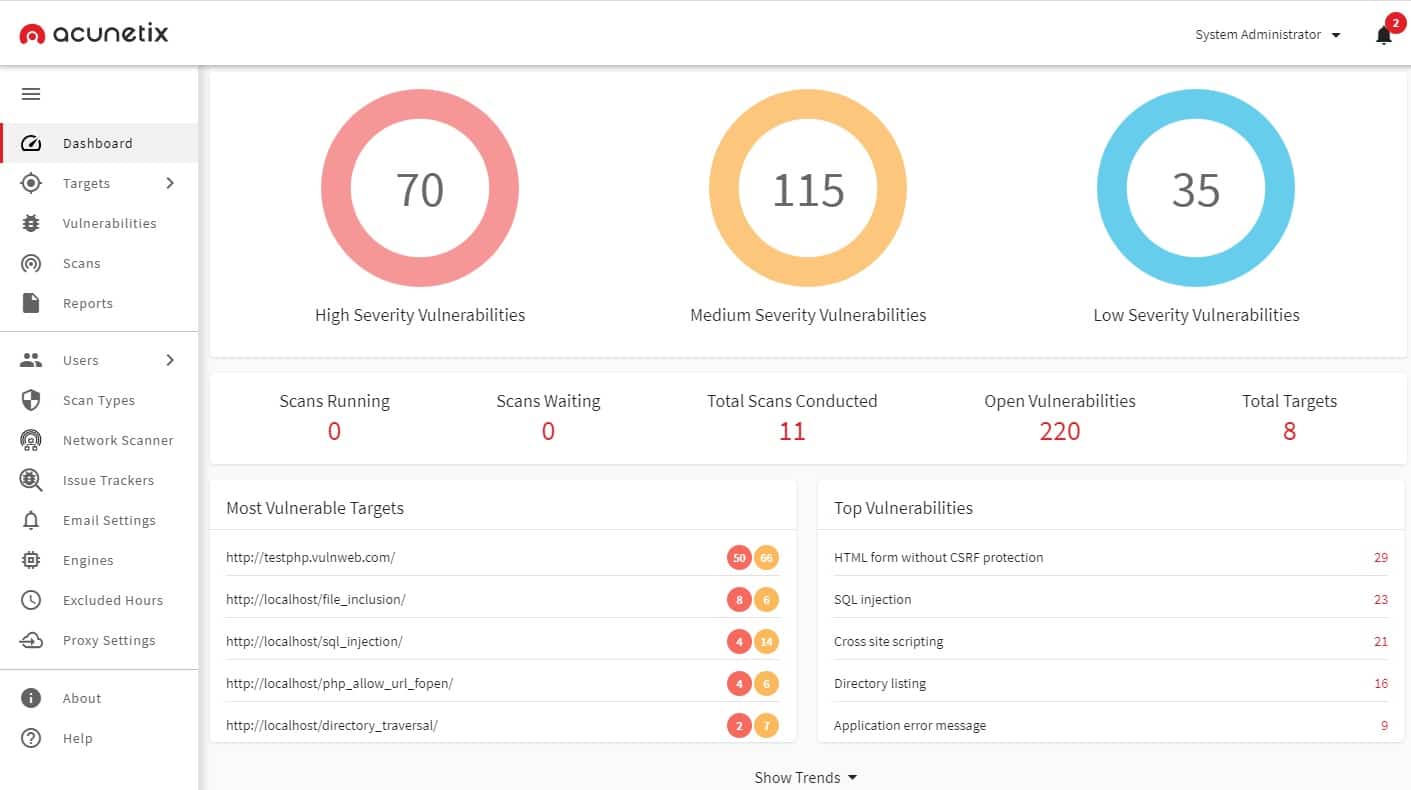
Acunetix is a vulnerability scanner for websites and web services. It is suitable for use both by developers of web applications and the owners of websites. The service scans for the presence of 6,500 known system weaknesses.
Key Features:
- Automate Vulnerability Management: Includes vulnerability tests to automate the integration and enhance easy remediation.
- Fastest Web Security Scanning Tool: Makes your complex scanning job easier and includes lots of javascript. It can find over 80% of the vulnerabilities.
- Network Security Scanner: Open-source tool that scans your open ports and IP address to identify vulnerabilities on specific network devices.
- Multiple Scanning Engines: Allows to use multiple scanning engines which can easily work on-premises and cloud.
Why do we recommend it?
We suggest you use Acunetix Web Vulnerability Scanner due to its best testing capabilities for the security of web applications. It's intuitively designed for easy use on its own or with other software, with built-in vulnerability assessment and management features that enable quick finding of security issues. Plus, Acunetix seamlessly integrates with popular software development tools for convenient development use – perfect for developers! By employing Acunetix, you can expand cybersecurity efforts while decreasing cyberattack risks without spending too many resources.
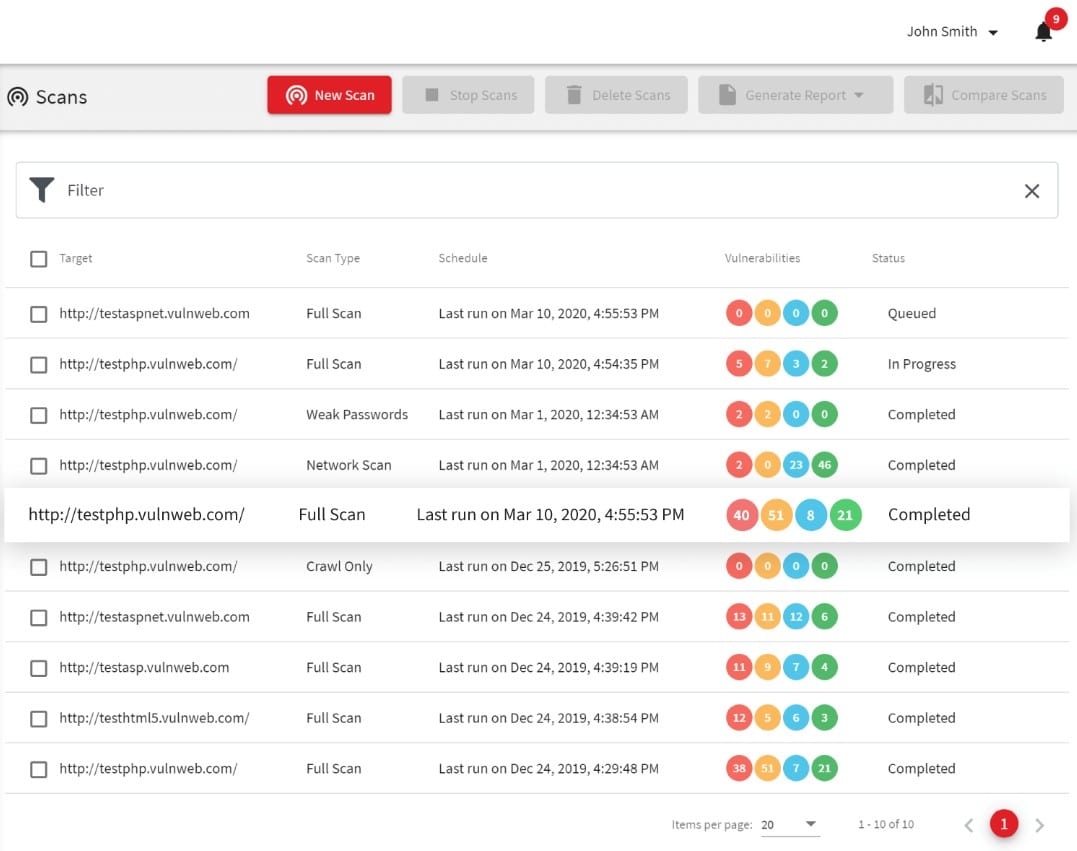
This is on-premises software and will render a full system auditing service. The package is offered in three editions: Standard, Premium, and 360. The base package is suitable for the operators of websites. Developers would need to opt for one of the two higher versions. These two versions integrate into development management systems to include vulnerability assessments in the development and testing phases of web applications and websites.
Who is it recommended for?
Acunetix Web Vulnerability Scanner is an excellent tool for anyone who needs help with website management or web application, from website administrators and developers to IT professionals seeking to protect their assets against cyber threats. From blogs to large e-commerce stores, Acunetix helps uncover security flaws quickly and efficiently, making it an indispensable solution for those focused on keeping their online presence safe.
Pros:
- Finds Other Web Security Threats: Also detects web security threats like SQL injections, XSS, and more.
- Low-False Positive Rates: Provides proof of exploits and vulnerabilities, which means low false positive rates.
- Has its Own API: Flexible API that can be easily connected to other third-party tools and security controls.
- Issue Trackers: Includes third-party issue trackers like Gitlab, jira, and much more to safely manage vulnerability.
Cons:
- Lacks in Scanning Options: Users reported that it has limited scanning options, and every scan impacts the system differently.
The software for Acunetix is available for Windows, macOS, and Linux. You can get a demo of the package so that you can try it for yourself.
4. Netwrix Auditor
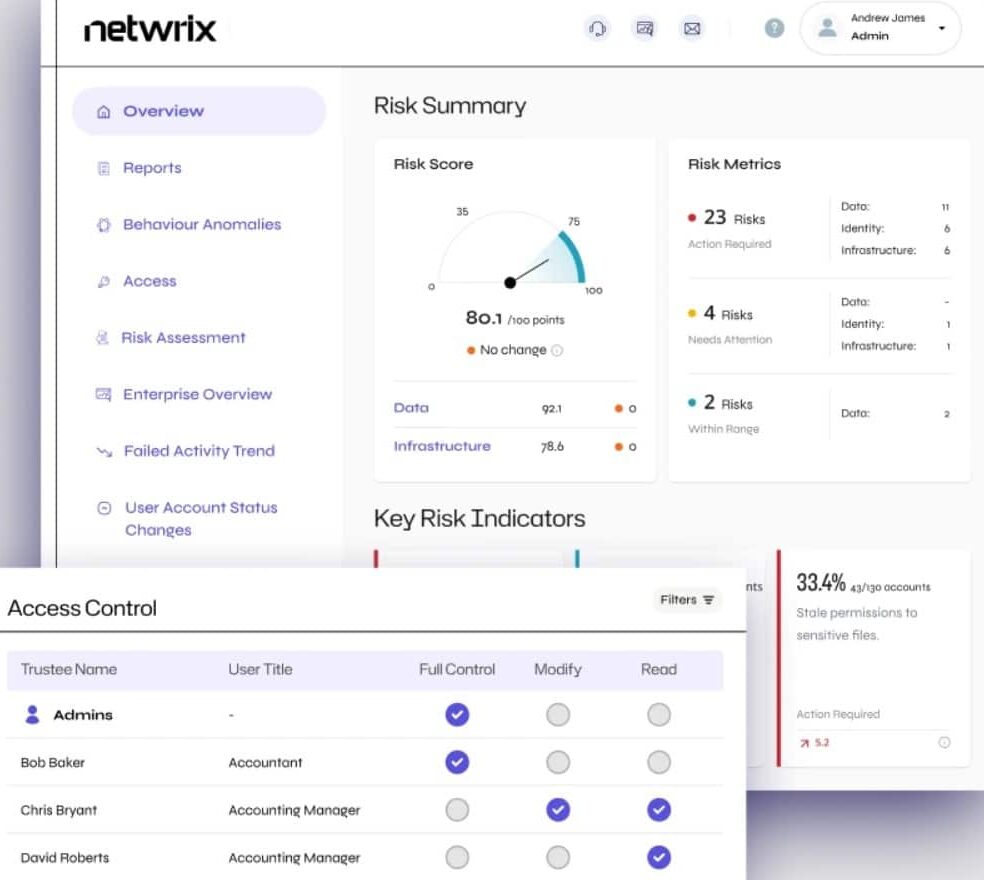
Netwrix Auditor is a system auditing tool that can be tailored to assess compliance to one of a list of data security standards. This list includes HIPAA, PCI DSS, SOX, GDPR, NIST, FERPA, GLBA, FISMA, CJIS, NERC CIP, and ISO/IEC 27001.
Key Features:
- Risk Assessment: Helps in identifying your top security and infrastructure gaps by monitoring critical assets.
- Auditing and Reporting: Collects all useful information from on-premises and cloud for audits and reporting.
- Sensitive Data Protection: Reviews sensitive data on a regular basis to maintain secure access.
- Threat Pattern Alerts: Monitors the threat patterns and send instant alerts in case of system failures and data breaches.
Why do we recommend it?
We recommend Netwrix Auditor because it benefits in keeping an organization's IT safe and compliant, helping detect security threats quickly, and demonstrating compliance with regulations. No matter if it's for small or large enterprise use, regular IT audits can strengthen security measures while meeting compliance requirements more easily – Netwrix Auditor makes the auditing process straightforward, making it an invaluable asset in improving overall cybersecurity posture and efficiency across an enterprise.
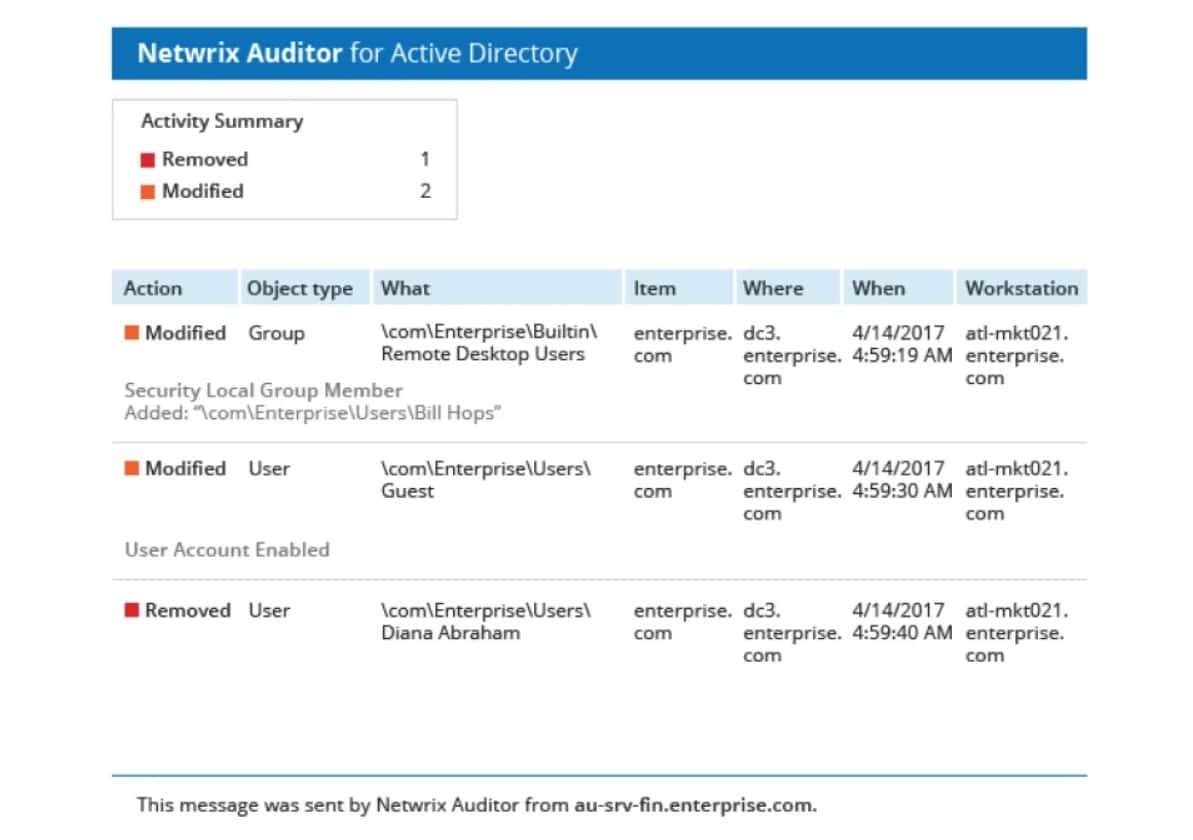
This package operates as a vulnerability scanner highlighting the weaknesses in protection for data and access to servers and the network. It interfaces with Active Directory to scan through user accounts, password security, and account activity. It also records all access events and particularly lists failed access attempts.
As well as querying the AD system, it helps secure Active Directory by managing backups and noting any changes in records. This monitoring is able to reverse unauthorized changes by restoring the last valid backup version. The reporting features of Netwrix Auditor are particularly strong. In fact, this is probably the main reason that you will buy this system. It automatically generates the reports you need in order to show standards compliance.
Who is it recommended for?
Netwrix Auditor is the best tool for anyone who needs to keep tabs on what's happening within their IT systems, be they business owners, IT administrators, or compliance officers. From monitoring Active Directory servers through to Windows Servers and Oracle Databases – while providing a centralized audit trail to help combat security threats while upholding compliance – Netwrix Auditor helps keep systems safe while upholding integrity overall.
Pros:
- Detects Insider Threats: Detailed visibility of insider users to spot malicious activity.
- User Access Reviews: You have the freedom to control user access and review, such as who can change and access the data.
- Weakness Mitigation: Focuses on reducing attacks and threats by mitigating the weak points across the network.
- Fast Search Function: Find accurate details about access events, sensitive files or any other unauthorized activity by searching with few clicks.
Cons:
- Some Plugins are Tough to Utilize: Some scans required specific plugins and the plugins were hard to use and lead to errors.
The Netwrix Auditor software package installs on Window Server or over Hyper-V and VMWare. This service is offered on a 20-day free trial.
5. LogicGate
LogicGate is a governance, risk management, and compliance (GRC) system. It will help you perform a risk assessment and posture assessment. The risk framework categorizes different parts of your system, earmarking those areas that are the most sensitive and in need of greater security. There are pre-set standards compliance configurations available that adjust the recommendations of the auditor according to GDPR, PCI-DSS, and SOX standards.
Key Features:
- Cyber Risk and Controls: Modifies cyber risk assessments, evidence, and other data by integrating cyber risk and business.
- Enterprise Risk Management: Helps to manage the whole enterprise by getting a clear view of connected risks and controls.
- Third-Party Risk Management: Helps to make vendor onboarding easier and improve security posture by measuring risk coming from third-party risk.
- Risk Quantification: Effectively plans and enhances your business risk strategy by understanding the financial terms and response strategies.
Why do we recommend it?
We highly recommend LogicGate as it provides an outstanding platform for Governance, Risk, and Compliance (GRC). With its user-friendly graph database and intuitive user interface, you can easily identify, assess, and address risks that impact regulatory compliance while simultaneously strengthening security for your organization. LogicGate gives comprehensive visibility into cybersecurity risks across your entire enterprise and makes audit preparation simpler; its Risk Cloud Controls Repository serves as a centralized source of truth to assess compliance across frameworks and regulations.
As well as risk assessment, LogicGate is a suitable tool to support system auditing. The system not only highlights security needs but offers a guide on steps that you should take in order to gain accreditation for a particular data protection standard. It offers a standard against which to run audits of your system.
Who is it recommended for?
LogicGate is an essential tool for professionals involved in governance, risk management, and compliance (GRC). It's ideal for compliance officers, risk managers, IT security professionals, and executives who are responsible for organizational security and regulatory adherence. Thanks to its great interface and cutting-edge features, LogicGate facilitates identifying risks, mitigating them efficiently, and ensuring regulatory adherence while creating resilient organizations – be they small businesses or large enterprises alike! LogicGate will strengthen security measures while meeting compliance standards.
Pros:
- Workflow and Process Customization: Allows you to customize the workflow and process according to the business and regulatory requirements.
- Effective Reporting Capabilities: Reports help to detect various third-party risks and other issues information in the vendor lifecycle.
- Intuitive Graph and Database: Anyone can easily use it to identify, evaluate, and mitigate risks because it uses a NO CODE interface.
- Real-Time Visibility: Due to its data-powered collaboration, you can reduce landscape risk and eliminate data silos and make better decisions.
Cons:
- Limited Reporting Capabilities: According to recent research, some users reported issues with limited reporting.
The LogicGate system is hosted, so you don’t need to install any software on your premises in order to operate the service.