We may earn a commission if you make a purchase through the links on our website.
The Complete SIEM Alerts Guide

UPDATED: June 8, 2023
SIEM solutions provide organizations with a centralized platform for monitoring, detecting, and responding to security incidents. But at the heart of SIEM systems are alerts. SIEM alerts play a vital role in identifying potential threats and enabling timely responses. They are the early warning systems of any solid security team.
In this article, we will delve into the world of SIEM alerts, exploring their importance, critical components, common types, and the tools and technologies available for effective SIEM alert management.
Table of Contents
- Understanding SIEM Systems and Alerts
- Why would anyone need SIEM alerts?
- Critical Components of SIEM Alerts
- What are Some Common Types of SIEM Alerts?
- Tools and Technologies for SIEM Alert Management
1. Understanding SIEM Systems and Alerts
SIEM (Security Information and Event Management) systems are integral components of modern cybersecurity infrastructure. They provide real-time analysis of potential security incidents.
SIEM systems are great for monitoring and analyzing data from different sources, including log files, system events, network traffic, and security devices. These systems allow you to collect, store, and analyze log and event data. They make it possible to detect and respond to security threats faster.
These systems immediately generate SIEM alerts when a specific security event or anomaly is detected. They can also be configured with pre-defined rules or conditions that, when met, trigger alerts and notify system admins.
If you run a business and are concerned about its security, consider SIEM alerts when setting up your security infrastructure. SIEM alerts provide immediate and valuable information, such as:
- Detecting suspicious activity
- Policy violations
- Abnormal user activity
- Network traffic anomalies
- Potential data and security breaches
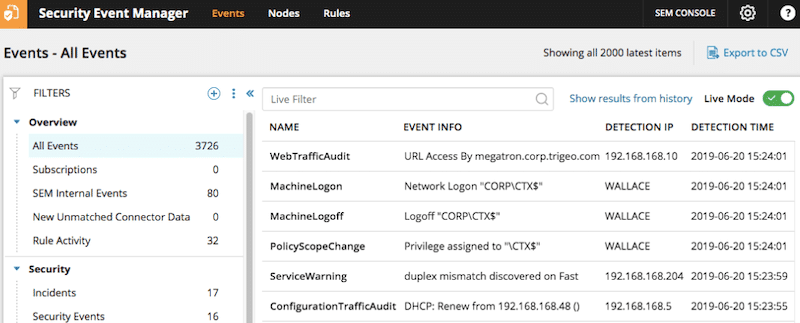
As you see from the screenshot above, SIEM alerts ‘usually' contain enough details about the event. They come with event type and info, source IP address (or detection IP), event detection time (timestamp), and any other information that provides the right context.
2. Why would anyone need SIEM alerts?
SIEM alerts are essential for building up your cybersecurity strength. They help reduce the time required to detect and respond to security incidents and improve your security posture. SIEM alerts allow security professionals to investigate and respond to security incidents quickly. They can help to reduce the potential impact of any attack or breach in your network.
Here are some reasons SIEM alerts are crucial:
- Early Detection of Security Threats SIEM alerts serve as early warning systems. They detect security threats early, helping security teams respond quickly and prevent damage. SIEM alerts will notify of events that need immediate attention, like failed login or unauthorized access attempts.
- Efficient Incident Response SIEM alerts can also introduce efficiency into the response system. They can provide critical and contextual information about the incident, including the time, location, and severity. This information can help security teams prioritize incidents and respond to them.
- Proactive Monitoring SIEM alerts can also help with proactive monitoring. They can proactively track and identify potential security threats before they can cause major damage.
- Compliance and Audit Requirements Many regulations and standards require organizations to have an effective security monitoring system. SIEM alerts can help these organizations meet these requirements
- Continuous Improvement SIEM alerts can help organizations identify areas where their security posture requires improvement. By analyzing SIEM alerts, they can pinpoint recurring security issues. They can later take steps to address them and improve their security posture.
3. Critical Components of SIEM Alerts
SIEM alerts rely on several key components, which help them detect and respond to security threats. You need to understand these components to leverage the full potential of SIEM systems. Understanding them, and knowing how to configure and fine-tune them, will give you the upper hand.
Let's explore the critical components of SIEM alerts:
- Event Correlation Event correlation is fundamental to SIEM alerts. It connects security events to help identify patterns or sequences that show potential threats. By correlating events from different sources, SIEM systems can identify complex attack scenarios. Without this, they would otherwise go unnoticed. This process helps understand the full context of an incident and determine the appropriate response.
- Rule-based Triggers Most of the time, SIEM alerts also rely on rule-based triggers. These triggers help identify specific events that meet predefined conditions. With rule-based triggers, security teams can define various rules based on different aspects. These triggers can be known attack patterns, indicators of compromise, or other suspicious activities. These rules act as filters, allowing the SIEM system to generate alerts when the observed events match the specified criteria.
- Threshold-based Triggers Like rule-based triggers, threshold-based triggers are also quite crucial for SIEM. These types of SIEM alerts involve setting specific thresholds or limits for certain events or metrics. When the threshold values surpass or fall below, the system generates the alert. Threshold-based triggers are quite helpful in identifying abnormal behavior or pattern deviations. For example, if there is a sudden peak in network traffic or many failed login attempts, the system will generate an alert.
- Anomaly Detection Anomaly detection is another key component of SIEM alerts. This ‘process’ helps identify deviations from expected behavior. This SIEM alert works by analyzing historical data and establishing baseline profiles for everyday activities. The SIEM system takes incoming events and compares them to these baseline profiles. It then flags any significant deviations as potential anomalies. Anomaly detection is effective because it can help detect previously unknown or zero-day attacks. It can also detect difficult-to-detect insider threats or unauthorized activities.
4. What are Some Common Types of SIEM Alerts?
SIEM alerts can cover different potential security incidents across different IT layers. There are three types of well-known SIEM alerts; these include network-based, system-based, and application-based.
Since there are a multitude of different sources generating traffic, there must be other ways to monitor them. SIEM systems are well suited to gather data from such sources, apply intelligence and generate alerts. It is important to configure SIEM systems to generate alerts based on these types of alerts.
Let's explore some common types of SIEM alerts:
- Unauthorized Access Attempts These are network-based alerts. They provide early warning signs of potential unauthorized access. They are triggered when SIEM systems detect failed login attempts or brute-force attacks.
- Network Intrusion Attempts Another popular network-based type of alert. These alerts happen when SIEM systems identify potential network intrusion attempts. This includes suspicious activities such as port scanning, IP address spoofing, or abnormal traffic patterns.
- Suspicious Network Traffic This is the third popular network-based type of alert. SIEM systems generate these alerts when network traffic exhibits unusual or suspicious behavior. It includes traffic patterns that deviate from normal baselines, large data transfers, or even unexpected destinations. It may also include traffic that matches known malicious signatures or indicators.
- Account Privilege Escalation This is a well-known system-based alert. They happen when SIEM detects user accounts gaining unauthorized privileges or access rights. This type of threat happens internally. These threats include user privileges elevation, administrative role changes, or unauthorized modifications to user permissions.
- Malware Detection SIEM systems can detect malware infections and raise this type of system-based alert. These alerts are triggered by malware-producing behaviors. When there is suspicious file activity, unexpected processes or services running on systems happen. Also, when there is communication with known malicious IP addresses or domains.
- Unusual System Activity Another type of system-based alert. Unusual or abnormal activities include unexpected system reboots, modifications to critical system files, unauthorized configuration changes, and more. SIEM systems must be prepared to identify these events.
- Unusual User Behavior This is an application-based type alert. They happen when users show abnormal behavior. Behavior that deviates from their typical patterns. Examples are multiple failed login attempts, access from unusual locations or devices, or unauthorized changes to application settings.
- Data Leakage Another application-based type alert. SIEM alerts can detect and alert potential data leakage or exfiltration incidents. Data leakage SIEM alerts include data transfers, access to sensitive data by unauthorized users, or access outside regular business hours.
- Suspicious Application Access SIEM systems can generate alerts when applications are accessed or used in a suspicious or unauthorized way. This includes attempts to exploit application vulnerabilities, unusual application usage patterns, or unauthorized access to sensitive application resources.
5. Tools and Technologies for SIEM Alert Management
There are no SIM alerts without a SIEM solution. To manage SIEM alerts effectively, you’ll need the right set of tools and technologies. Such will enhance the monitoring, analysis, and response capabilities of the system. In this section, we will explore those tools and technologies that will allow you to manage your SIEM alert effectively.
a. SIEM Platforms
The key to efficient SIEM alert management is using a good SIEM solution. We recommend a SIEM solution with the full features and capabilities to help you collect, analyze, and manage security event data. There are different SIEM solutions in the market. Each may have its own strengths and focus areas, so you might have to dig deeper to fulfill your particular organizational needs.
When looking for a SIEM platform, consider the following capabilities/features:
- Data Collection and Normalization The SIEM tool should collect and normalize data from different sources into a common format, removing inconsistencies and organizing it for analysis.
- Correlation and Analysis The tool should correlate data from various sources and use advanced analysis techniques and machine learning algorithms to identify patterns and anomalies that indicate security threats.
- Alerting and Notifications Real-time SIEM alerts and customizable notifications should be provided to detect and respond to potential security incidents promptly. Integration with other security tools and platforms is essential.
- Scalability and Flexibility The tool should scale seamlessly, accommodate increasing data volumes and new data sources, and support various deployment models.
- Integration and Compatibility The SIEM tool should integrate with different security tools and platforms, support various data sources, and use industry-standard protocols and formats.
- Reporting and Analytics Customizable dashboards, reports, and advanced analytics capabilities enable effective data analysis, pattern detection, and identification of trends.
- Ease of Use and Maintenance The SIEM tool should have an intuitive interface, automated maintenance features, and user-friendly documentation and training materials.
- Security and Compliance Robust security features, encryption, access controls, and compliance with relevant regulations ensure data protection and meet legal obligations.
- Support and Training Access to technical support resources, comprehensive training materials, and responsive customer support is essential.
SolarWinds Security Event Manager – FREE TRIAL
A SIEM tool that you can consider is SolarWinds Security Event Manager (SEM). SolarWinds SEM is a comprehensive SIEM solution designed to enhance the security posture and ensure regulatory compliance from organizations. It offers good coverage of SIEM features and capabilities. It includes centralized log collection and normalization, enabling monitoring and analyzing security events from multiple sources. SEM also stands out with its automated threat detection and response capabilities, leveraging advanced analytics and machine learning algorithms. It can swiftly identify anomalies like unauthorized access attempts, malware infections, and data exfiltration.
SEM supports flexible deployment options, allowing on-premises or cloud deployment to align with specific requirements.
When incidents are detected, SEM triggers incident response workflows, isolates affected systems, blocks malicious traffic, and notifies security teams. Compliance reporting tools are integrated, enabling the quick generation of reports for various frameworks like PCI DSS, HIPAA, and GDPR, along with customizable templates.
The SEM interface is intuitive, providing real-time visibility into the organization's security posture. It also offers file integrity monitoring (FIM) to track changes to critical files and folders, bolstering protection against unauthorized access and data tampering.
Pricing and Licensing: What sets SEM apart is its simple and affordable licensing model. It eliminates the need for expensive hardware or licensing fees. To get more information on pricing, get a quote.
Free trial: Download a fully functional 30-day free trial.
b. Other helpful solutions
If you are considering implementing efficient SIEM alert management and automation, consider the following additional tools and technologies.
- Automation and Orchestration Automation and orchestration are crucial in SIEM alert management. These tools can help streamline response efforts and reduce the workload on security teams. Some SIEM platforms offer automated response actions like IP blocking, system isolation, account resets, or incident ticket generation.
- Integration with Other Security Solutions Integrating SIEM with other security solutions can also help improve threat detection and response. Consider integration with Endpoint Detection and Response (EDR), Vulnerability Management, and Threat Intelligence Feeds.
Final Words
SIEM alerts are almost like the eyes and ears of an organization's security operations. They provide real-time insights into potential threats and vulnerabilities so that security teams can respond promptly.
In this article, we have explored the various components and types of SIEM alerts. We have also gone through the tools and technologies available to manage them efficiently. With tools like the SolarWinds Security Event Manager, you’ll have the right set of features and will be able to manage SIEM alerts in a centralized and efficient manner.